2014-03-17 - ZUPONCIC EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
This is the first time I've run across Zuponcic. Here are some good blog posts about this exploit kit and the associated malware:
- https://blog.fox-it.com/2013/12/19/not-quite-the-average-exploit-kit-zuponcic/
- https://malwageddon.blogspot.com/2013/08/zuponcic-is-it-bird-is-it-plane-no-its.html>
- https://c-apt-ure.blogspot.com/2013/12/ponmocup-hunter-is-re-tired.html
As the Fox-it blog post states, the malware payload is encrypted using an RC4 hash, and I was unable to decrypted the malware payload. The fox-it blog post also states if Java is disabled on the browser, the EK sends an archive for you to download. When I tried this, I was sent a 1.2 MB JAR file by the EK, which I've included in the ZIP file of today's malware.
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 217.76.156[.]117 - www.silvergrey[.]es - Compromised website
- 31.210.96[.]157 - ambalanchery.drdekloet[.]com - Redirect
- 178.33.192[.]35 - ga.instylecuts[.]net - Zuponcic EK
- 93.115.88[.]220 - 93.115.88[.]220 - First post-infection callback
- 66.254.123[.]33 - www.sanctionedmedia[.]com - Second post-infection callback
INFECTION CHAIN OF EVENTS
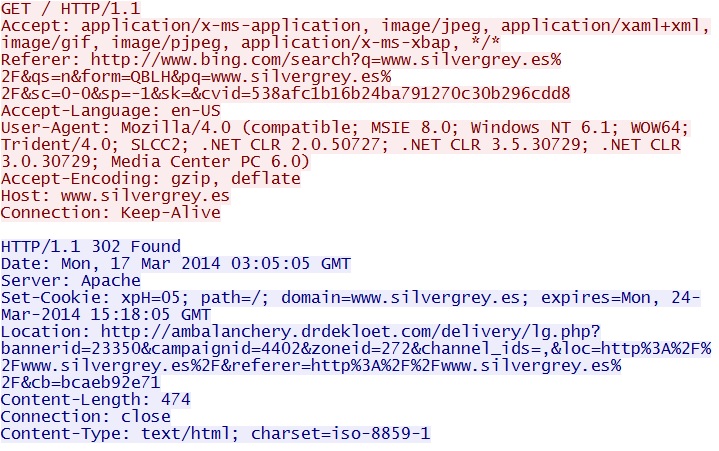
- 03:05:05 UTC - 217.76.156[.]117:80 - www.silvergrey[.]es - GET /
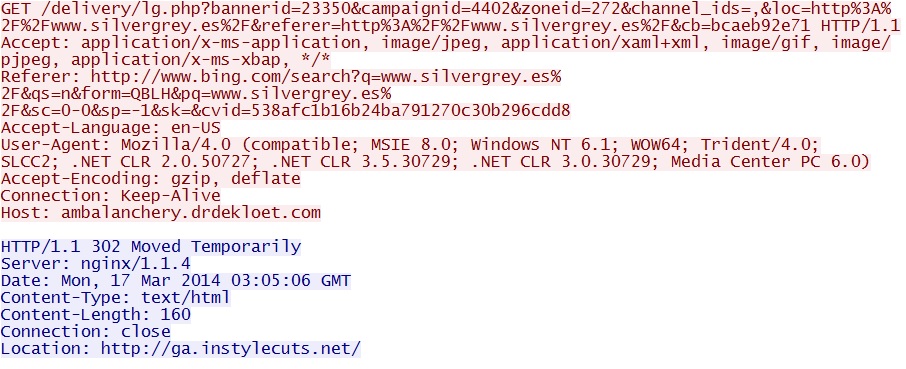
- 03:05:06 UTC - 31.210.96[.]157:80 - ambalanchery.drdekloet[.]com - GET /delivery/lg.php?
bannerid=23350&campaignid=4402&zoneid=272&channel_ids=,&loc=http%3A%2F%2Fwww.silvergrey[.]es%2F&
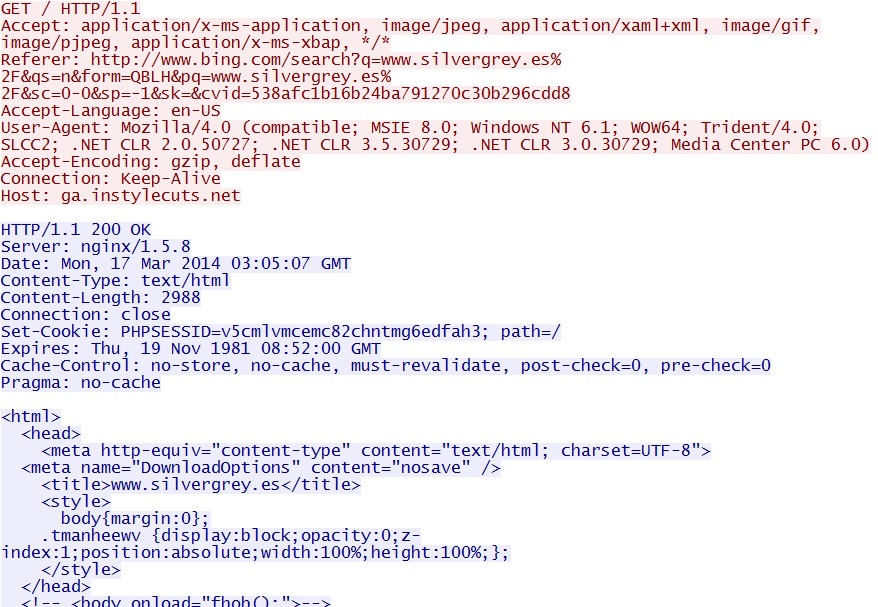
referer=http%3A%2F%2Fwww.silvergrey[.]es%2F&cb=bcaeb92e71 - 03:05:07 UTC - 178.33.192[.]35:80 - ga.instylecuts[.]net - GET /
- 03:05:07 UTC - 178.33.192[.]35:80 - ga.instylecuts[.]net - GET /js/java.js
- 03:05:07 UTC - 178.33.192[.]35:80 - ga.instylecuts[.]net - GET /tr.gif
- 03:05:08 UTC - 178.33.192[.]35:80 - ga.instylecuts[.]net - GET /favicon.ico
- 03:05:08 UTC - 173.194.115[.]51:80 - www.google[.]com - GET /
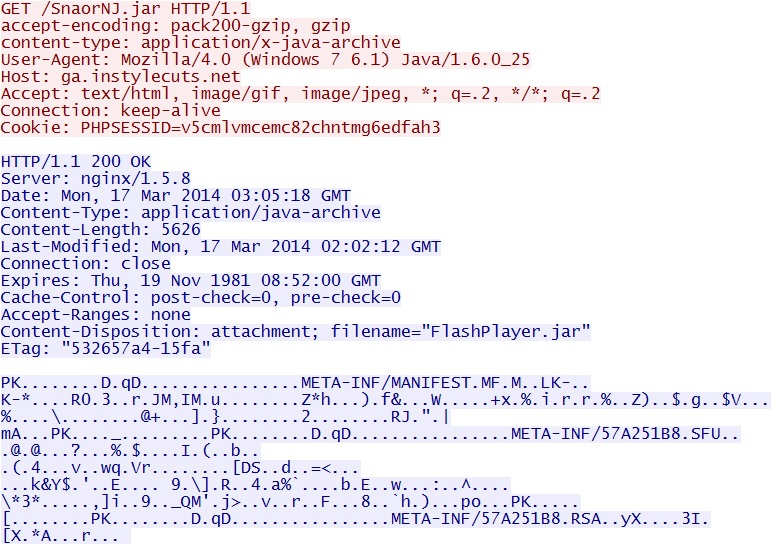
- 03:05:18 UTC - 178.33.192[.]35:80 - ga.instylecuts[.]net - GET /SnaorNJ.jar
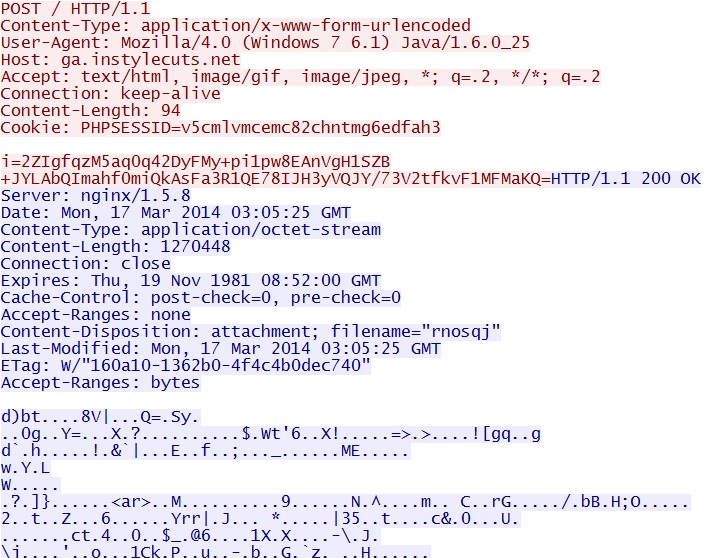
- 03:05:24 UTC - 178.33.192[.]35:80 - ga.instylecuts[.]net - POST /
POST-INFECTION CALLBACK TRAFFIC
- 03:05:34 UTC - 93.115.88[.]220:80 - 93.115.88[.]220 - GET /redir/article/home
- 03:05:36 UTC - 93.115.88[.]220:80 - 93.115.88[.]220 - GET /redir/article/home
- 03:05:41 UTC - 66.254.123[.]33:80 - www.sanctionedmedia[.]com - GET /version2.XML
- 03:05:46 UTC - 66.254.123[.]33:80 - www.sanctionedmedia[.]com - POST /smfeed2.php
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
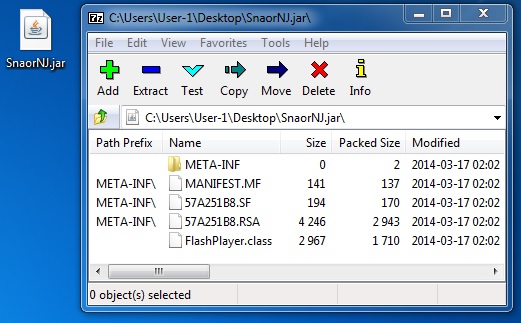
File name: SnaorNJ.jar
File size: 5,626 bytes
MD5 hash: f9185a43f34132752fd16e4470c0a6b4
Detection ratio: 12 / 50
First submission: 2014-03-17 05:04:02 UTC
VirusTotal link: https://www.virustotal.com/en/file/67fd420d33936733816bcb38926da3edef8996f2011807b206c3e23d55f168c5/analysis/
ONE OF THE PIECES OF MALWARE DROPPED AFTER THE EXPLOIT
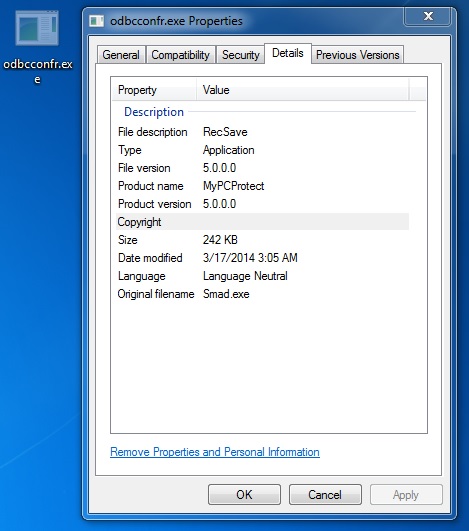
File name: odbcconfr.exe
File size: 248,320 bytes
MD5 hash: c3cd820083d508131eec3697d941a5fa
Detection ratio: 36 / 50
First submission: 2014-03-17 03:38:02 UTC
VirusTotal link: https://www.virustotal.com/en/file/35b1f5f0969d9d2ad7e96c2e80752fea19b4319129362d983d061f346dcee01b/analysis/
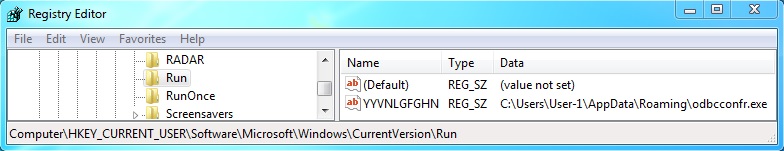
Associated registry key for this malware:
ARCHIVE SENT FROM ZUPONCIC EK DOMAIN WHEN JAVA WAS DISABLED ON THE BROWSER
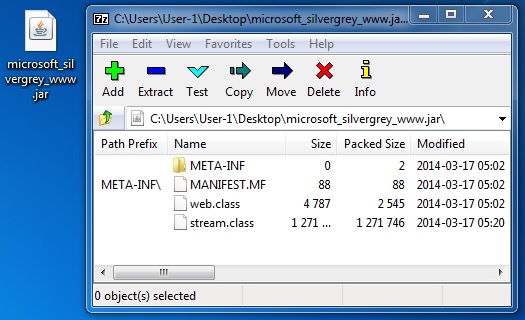
File name: microsoft_silvergrey_www.jar
File size: 1,274,879 bytes
MD5 hash: 1c8d8765fa6908c2da297110c2d0bdb3
Detection ratio: 6 / 50
First submission: 2014-03-17 05:31:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/cf16a8a61ca1b1eb7bc87c5aac00e3ea8f0a2d32828c818a7e6a2a0f72b60409/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
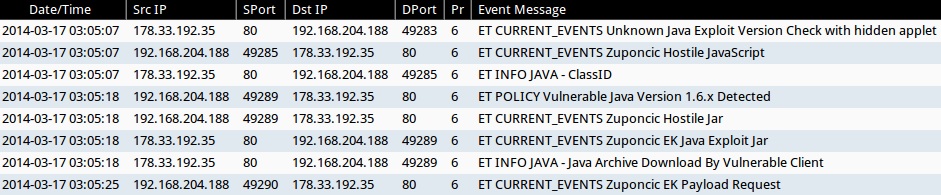
- 03:05:07 UTC - 178.33.192[.]35:80 - ET CURRENT_EVENTS Unknown Java Exploit Version Check with hidden applet
- 03:05:07 UTC - 178.33.192[.]35:80 - ET CURRENT_EVENTS Zuponcic Hostile JavaScript
- 03:05:07 UTC - 178.33.192[.]35:80 - ET INFO JAVA - ClassID
- 03:05:18 UTC - 178.33.192[.]35:80 - ET POLICY Vulnerable Java Version 1.6.x Detected
- 03:05:18 UTC - 178.33.192[.]35:80 - ET CURRENT_EVENTS Zuponcic Hostile Jar
- 03:05:18 UTC - 178.33.192[.]35:80 - ET CURRENT_EVENTS Zuponcic EK Java Exploit Jar
- 03:05:18 UTC - 178.33.192[.]35:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 03:05:25 UTC - 178.33.192[.]35:80 - ET CURRENT_EVENTS Zuponcic EK Payload Request
HIGHLIGHTS FROM THE TRAFFIC
Redirect when reaching the server from a Bing search (probably an .htaccess style redirect) - www.silvergrey[.]es
Second redirect - ambalanchery.drdekloet[.]com/delivery/lg.php?bannerid=23350&campaignid=4402&zoneid=272&
channel_ids=,&loc=http%3A%2F%2Fwww.silvergrey[.]es%2F&referer=http%3A%2F%2Fwww.silvergrey[.]es%2F&cb=bcaeb92e71
Zuponcic EK landing page - ga.instylecuts[.]net/
Zuponcic EK delivers Java exploit - ga.instylecuts[.]net/SnaorNJ.jar
Malware payload retrieved (encrypted with RC4 hash) - ga.instylecuts[.]net/
Click here to return to the main page.