2014-06-10 - FLASHPACK EK FROM 192.71.151[.]14 - 3JF9S456U0RQV91RNO5PMFM.APTEKA-EREKCJA[.]PL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Tried to get the CVE-2014-0515 Flash exploit, but got CVE-2014-0497 instead.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 198.71.51[.]226 - insideevs[.]com - Compromised website
- 192.71.151[.]14 - vl65q7njutvgbgbq6n127pw.arcadehaven[.]co[.]uk and vl65q7njutvgbgbq6n127pw713453cf631795a54788823369999e837.arcadehaven[.]co[.]uk - Redirect
- 192.71.151[.]14 - 3jf9s456u0rqv91rno5pmfm.apteka-erekcja[.]pl - FlashPack EK
- 62.146.57[.]194 - no domain name - Glupteba callback traffic on TCP port 32136
- 192.71.151[.]14 - vl65q7njutvgbgbq6n127pw.arcadehaven[.]co[.]uk - Post-infection callback for follow-up malware
TRAFFIC:
- 02:46:55 UTC - insideevs[.]com - GET /tesla-announces-85-kwh-model-s-service-loaner-program-end-of-forced-600-annual-fee-expanded-battery-coverage/
- 02:46:57 UTC - vl65q7njutvgbgbq6n127pw.arcadehaven[.]co[.]uk - GET /index.php?i=YnNpeHl5anY9dmpoZXFwdiZ0aW1lPTE0MD[long string of characters]
- 02:46:59 UTC - vl65q7njutvgbgbq6n127pw713453cf631795a54788823369999e837.arcadehaven[.]co[.]uk - GET /index2.php
- 02:47:00 UTC - vl65q7njutvgbgbq6n127pw713453cf631795a54788823369999e837.arcadehaven[.]co[.]uk - GET /favicon.ico
- 02:47:02 UTC - 3jf9s456u0rqv91rno5pmfm.apteka-erekcja[.]pl - GET /fortunez/vokutred/allow.php
- 02:47:02 UTC - 3jf9s456u0rqv91rno5pmfm.apteka-erekcja[.]pl - GET /fortunez/vokutred/js/pd.php?id=766c363571376e6[long string of characters]
- 02:47:08 UTC - 3jf9s456u0rqv91rno5pmfm.apteka-erekcja[.]pl - POST /fortunez/vokutred/json.php
- 02:47:09 UTC - 3jf9s456u0rqv91rno5pmfm.apteka-erekcja[.]pl - GET /fortunez/vokutred/javadb.php
- 02:47:09 UTC - 3jf9s456u0rqv91rno5pmfm.apteka-erekcja[.]pl - GET /fortunez/vokutred/flash2014.php
- 02:47:09 UTC - 3jf9s456u0rqv91rno5pmfm.apteka-erekcja[.]pl - GET /fortunez/vokutred/flash0515.php
- 02:47:10 UTC - 3jf9s456u0rqv91rno5pmfm.apteka-erekcja[.]pl - GET /fortunez/vokutred/include/f763a.swf
- 02:47:18 UTC - 3jf9s456u0rqv91rno5pmfm.apteka-erekcja[.]pl - GET /fortunez/vokutred/include/0a12c6384b19c8444147bc8eedc41e2f.jar
- 02:47:18 UTC - 3jf9s456u0rqv91rno5pmfm.apteka-erekcja[.]pl - GET /fortunez/vokutred/include/0a12c6384b19c8444147bc8eedc41e2f.jar
- 02:48:20 UTC - 3jf9s456u0rqv91rno5pmfm.apteka-erekcja[.]pl - GET /fortunez/vokutred/loaddb.php?id=4
- 02:48:41 UTC - 62.146.57[.]194:32136 - GET /stat?uid=100&downlink=1111&uplink=1111&id=0008FBBC&statpass=bpass&[long string of characters]
- 02:49:59 UTC - vl65q7njutvgbgbq6n127pw.arcadehaven[.]co[.]uk - GET /software.php?06100250381139797
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-06-10-FlashPack-EK-flash-exploit.swf
File size: 15,807 bytes
MD5 hash: 0535f214023fb455a36afe6782ba96ac
Detection ratio: 0 / 45
First submission: 2014-06-10 04:40:32 UTC
VirusTotal link: https://www.virustotal.com/en/file/cdd7e502ddf9e3f74660da3157a5ece7cf277e3ce4eb65928ce682bd0f6de55e/analysis/
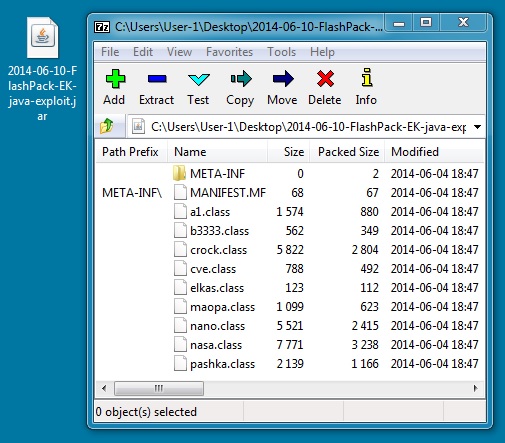
JAVA EXPLOIT
File name: 2014-06-10-FlashPack-EK-java-exploit.jar
File size: 13,434 bytes
MD5 hash: 97925d90f5340be2aabf833d91f9f917
Detection ratio: 8 / 52
First submission: 2014-06-10 03:32:55 UTC
VirusTotal link: https://www.virustotal.com/en/file/ace5fabcb614564f13bd9493a7f91ecc13694a9b294d94148b9579a1bef27152/analysis/
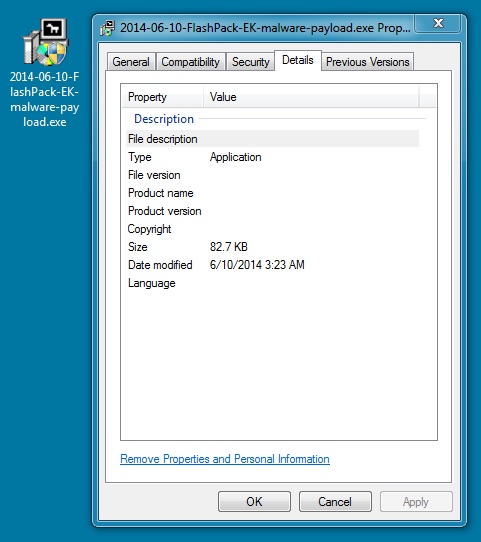
MALWARE PAYLOAD
File name: 2014-06-10-FlashPack-EK-malware-payload.exe
File size: 84,745 bytes
MD5 hash: 1255d6345b7d29113bd540c2db4bbdfb
Detection ratio: 31 / 53
First submission: 2014-06-10 04:41:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/ec5a1f379ad579697acbcdac073c14d6284185ba0c293c41f699e413d3f9acc0/analysis/
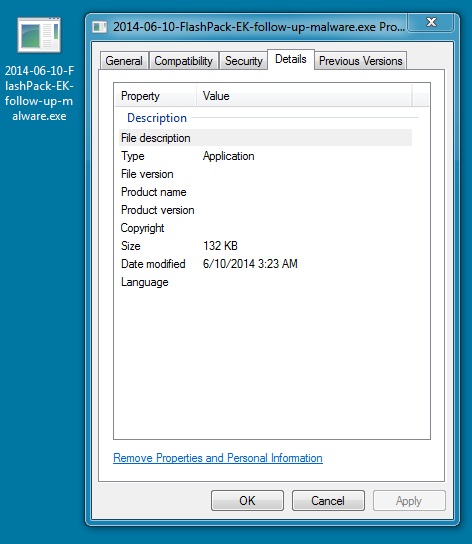
FOLLOW-UP MALWARE
File name: 2014-06-10-FlashPack-EK-follow-up-malware.exe
File size: 135,692 bytes
MD5 hash: 785c2dbd22431fe669f480ad050c1f43
Detection ratio: 23 / 53
First submission: 2014-06-10 04:41:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/6f4c499ae13e823bb7fa1cb744b2f2784977d1f1c621fc40e48ef113e42f673e/analysis/
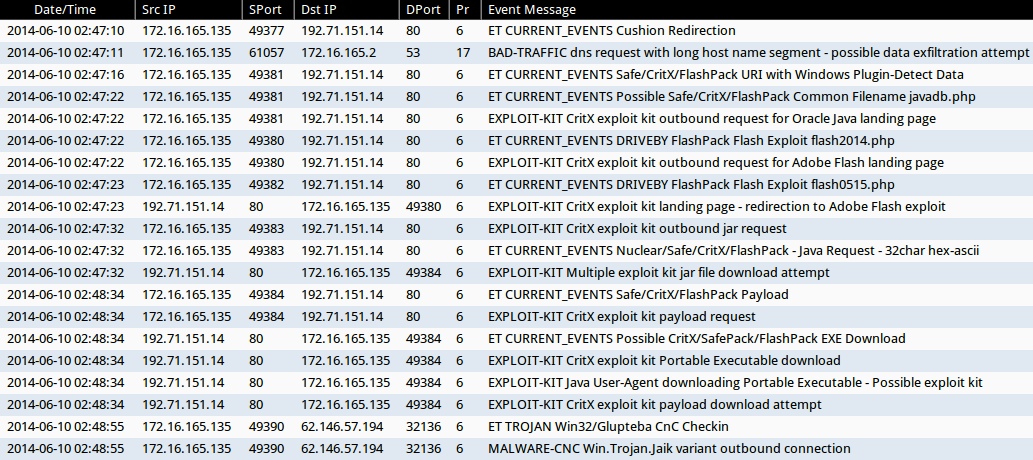
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
Emerging Threats and ETPRO rulesets:
- 2014-06-10 02:47:10 UTC - 192.71.151[.]14:80 - ET CURRENT_EVENTS Cushion Redirection (sid:2017552)
- 2014-06-10 02:47:16 UTC - 192.71.151[.]14:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack URI with Windows Plugin-Detect Data (sid:2017812)
- 2014-06-10 02:47:22 UTC - 192.71.151[.]14:80 - ET CURRENT_EVENTS Possible Safe/CritX/FlashPack Common Filename javadb.php (sid:2018238)
- 2014-06-10 02:47:22 UTC - 192.71.151[.]14:80 - ET CURRENT_EVENTS DRIVEBY FlashPack Flash Exploit flash2014.php (sid:2018471)
- 2014-06-10 02:47:23 UTC - 192.71.151[.]14:80 - ET CURRENT_EVENTS DRIVEBY FlashPack Flash Exploit flash0515.php (sid:2018540)
- 2014-06-10 02:47:32 UTC - 192.71.151[.]14:80 - ET CURRENT_EVENTS Nuclear/Safe/CritX/FlashPack - Java Request - 32char hex-ascii (sid:2014751)
- 2014-06-10 02:48:34 UTC - 192.71.151[.]14:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack Payload (sid:2017813)
- 2014-06-10 02:48:34 UTC - 192.71.151[.]14:80 - ET CURRENT_EVENTS Possible CritX/SafePack/FlashPack EXE Download (sid:2017297)
- 2014-06-10 02:48:55 UTC - 62.146.57[.]194:32136 - ET TROJAN Win32/Glupteba CnC Checkin (sid:2013293)
Sourcefire VRT ruleset:
- 2014-06-10 02:47:22 UTC - 192.71.151[.]14:80 - EXPLOIT-KIT CritX exploit kit outbound request for Oracle Java landing page (sid:30971)
- 2014-06-10 02:47:22 UTC - 192.71.151[.]14:80 - EXPLOIT-KIT CritX exploit kit outbound request for Adobe Flash landing page (sid:30970)
- 2014-06-10 02:47:23 UTC - 192.71.151[.]14:80 - EXPLOIT-KIT CritX exploit kit landing page - redirection to Adobe Flash exploit (sid:30967)
- 2014-06-10 02:47:32 UTC - 192.71.151[.]14:80 - EXPLOIT-KIT CritX exploit kit outbound jar request (sid:29165)
- 2014-06-10 02:47:32 UTC - 192.71.151[.]14:80 - EXPLOIT-KIT Multiple exploit kit jar file download attempt (sid:27816)
- 2014-06-10 02:48:34 UTC - 192.71.151[.]14:80 - EXPLOIT-KIT CritX exploit kit payload request (sid:30973)
- 2014-06-10 02:48:34 UTC - 192.71.151[.]14:80 - EXPLOIT-KIT CritX exploit kit Portable Executable download (sid:24791)
- 2014-06-10 02:48:34 UTC - 192.71.151[.]14:80 - EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit (sid:25042)
- 2014-06-10 02:48:34 UTC - 192.71.151[.]14:80 - EXPLOIT-KIT CritX exploit kit payload download attempt (sid:29167)
- 2014-06-10 02:48:55 UTC - 62.146.57[.]194:32136 - MALWARE-CNC Win.Trojan.Jaik variant outbound connection (sid:30977)
Click here to return to the main page.