2014-06-12 - CVE-2014-0515 EXPLOIT FROM SWEET ORANGE EK - 82.118.17[.]172 PORT 16122 - IMG.BLUEPRINT-LEGAL[.]COM:16122
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Sweet Orange EK now has the CVE-2014-0515 Flash exploit.
- My infected VM was running IE 11, Flash 13.0.0.182, and Java 7u51
- According to Virus Total, Kaspersky has identified this Flash exploit as: Exploit.SWF.CVE-2014-0515.d
CHAIN OF EVENTS
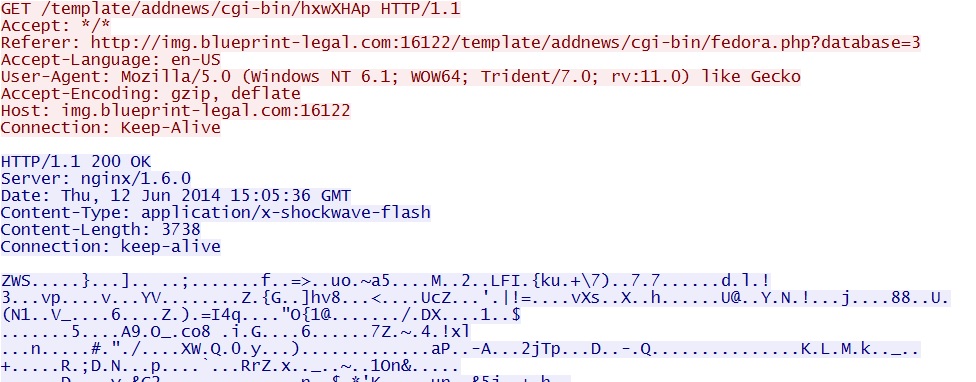
- 15:05:33 UTC - 82.118.17[.]172 - img.blueprint-legal[.]com:16122 - GET /template/addnews/cgi-bin/fedora.php?database=3
- 15:05:35 UTC - 82.118.17[.]172 - img.blueprint-legal[.]com:16122 - GET /template/addnews/cgi-bin/hxwXHAp [CVE-2014-0515 Flash exploit]
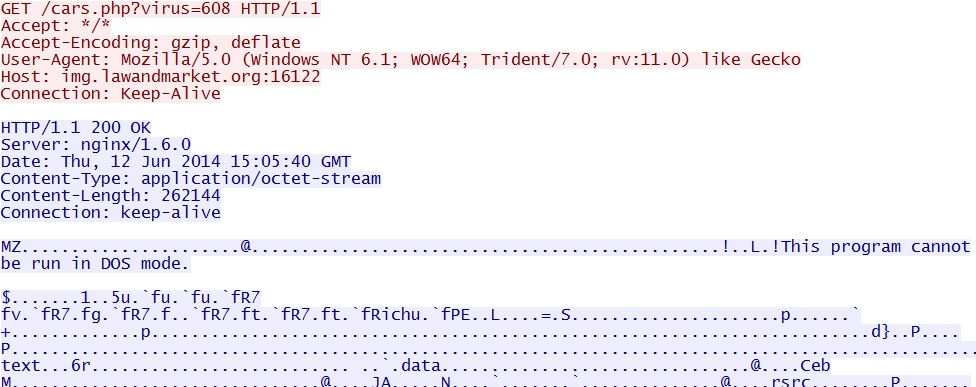
- 15:05:40 UTC - 82.118.17[.]172 - img.lawandmarket[.]org:16122 - GET /cars.php?virus=608 [malware payload]
- 15:06:00 UTC - 82.118.17[.]172 - img.blueprint-legal[.]com:16122 - GET /template/addnews/cgi-bin/Fqxzdh.jar
- 15:06:00 UTC - 82.118.17[.]172 - img.blueprint-legal[.]com:16122 - GET /template/addnews/cgi-bin/cnJzjx.jar
- 15:06:00 UTC - 82.118.17[.]172 - img.blueprint-legal[.]com:16122 - GET /template/addnews/cgi-bin/Fqxzdh.jar
- 15:06:00 UTC - 82.118.17[.]172 - img.blueprint-legal[.]com:16122 - GET /template/addnews/cgi-bin/Fqxzdh.jar
- 15:06:01 UTC - 82.118.17[.]172 - img.blueprint-legal[.]com:16122 - GET /template/addnews/cgi-bin/Fqxzdh.jar
- 15:06:01 UTC - 82.118.17[.]172 - img.blueprint-legal[.]com:16122 - GET /template/addnews/cgi-bin/Fqxzdh.jar
NOTE: No java exploits were sent in response to the requests for a JAR file.
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-06-12-Sweet-Orange-EK-flash-exploit.swf
File size: 3,738 bytes
MD5 hash: 4e2a9652c42f52c369204dc8818eb434
Detection ratio: 1 / 54
First submission: 2014-06-13 06:35:53 UTC
VirusTotal link: https://www.virustotal.com/en/file/d2bc28e651184a2f251b0cb799f5a10ab2cf5030ebd33bd535898e23b58da694/analysis/
MALWARE PAYLOAD
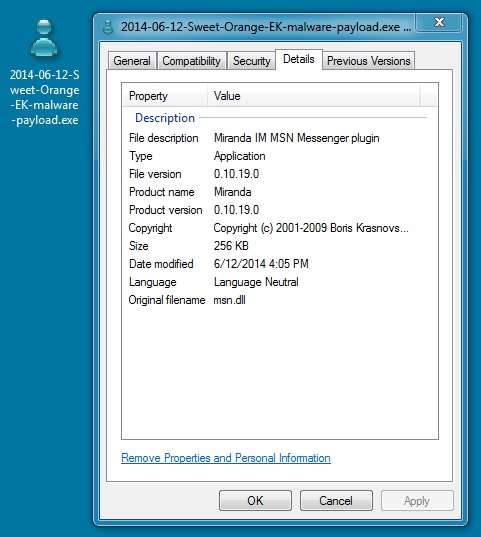
File name: 2014-06-12-Sweet-Orange-EK-malware-payload.exe
File size: 262,144 bytes
MD5 hash: 280f0c567eaaef776b95c53dede9e934
Detection ratio: 23 / 53
First submission: 2014-06-11 20:58:39 UTC
VirusTotal link: https://www.virustotal.com/en/file/b47b52fa525cd43ddfbdec9b5c7cb911352d339a44662e6c2ada1a8db04db1a7/analysis/
ALERTS
No alerts were noted, since this traffic took place on a non-standard port for HTTP traffic.
HIGHLIGHTS FROM THE TRAFFIC
Sweet Orange EK delivers CVE-2014-0515 Flash exploit:
Payload delivered after successful CVE-2014-0515 exploit:
Click here to return to the main page.