2014-06-28 - SWEET ORANGE EK FROM 94.185.80[.]43 PORT 8590 - NULAPTRA.INDOLOCKER[.]COM - TYJALOS.TORNADO-365[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 83.166.234[.]103 - zamcheck[.]org - ad traffic with malicious javascript
- 94.185.80[.]43 - nulaptra.indolocker[.]com and tyjalos.tornado-365[.]com - Sweet Orange EK on TCP port 8590
- 217.23.10[.]132 - callback traffic using DNS over UDP port 53 - from infected VM and Malwr sandbox analysis
- 50.77.231[.]183 - additional IP address noted in callback traffic using DNS over UDP port 53 - from Malwr sandbox analysis
AD-BASED REDIRECT:
- 16:34:00 UTC - 83.166.234[.]103:80 - zamcheck[.]org - GET /300x250/int.php?eh=51312
SWEET ORANGE EK:
- 16:34:03 UTC - 94.185.80[.]43:8590 - nulaptra.indolocker[.]com:8590 - GET /includes/config.php?wifi=69
- 16:34:06 UTC - 94.185.80[.]43:8590 - nulaptra.indolocker[.]com:8590 - GET /includes/CIUhYc [Flash exploit]
- 16:34:13 UTC - 94.185.80[.]43:8590 - tyjalos.tornado-365[.]com:8590 - GET /stars.php?click=469 [malware payload]
- 16:35:01 UTC - 94.185.80[.]43:8590 - nulaptra.indolocker[.]com:8590 - GET /includes/gRHfAMJC.jar
- 16:35:01 UTC - 94.185.80[.]43:8590 - nulaptra.indolocker[.]com:8590 - GET /includes/HIwdF.jar
- 16:35:01 UTC - 94.185.80[.]43:8590 - nulaptra.indolocker[.]com:8590 - GET /includes/gRHfAMJC.jar
- 16:35:02 UTC - 94.185.80[.]43:8590 - nulaptra.indolocker[.]com:8590 - GET /includes/gRHfAMJC.jar
- 16:35:02 UTC - 94.185.80[.]43:8590 - nulaptra.indolocker[.]com:8590 - GET /includes/gRHfAMJC.jar
- 16:35:06 UTC - 94.185.80[.]43:8590 - nulaptra.indolocker[.]com:8590 - GET /includes/gRHfAMJC.jar
NOTE: The requests for .jar files all returned a 404 Not Found response.
POST-INFECTION TRAFFIC (FROM INFECTED VM):
- 16:34:46 - 217.23.10[.]132:53 - Standard query ANY 5020.eea1d2de3883b2c4e0cbe303be43d075f43529d7577d7ef4a2.search.google[.]com
- 16:34:46 - 217.23.10[.]132:53 - Standard query response A 0.0.0[.]0 TXT (539 bytes)
- 16:34:46 - 217.23.10[.]132:53 - Standard query TXT 0.6932.images.google[.]com
- 16:34:46 - 217.23.10[.]132:53 - Standard query response TXT (317 bytes)
- 16:34:46 - 217.23.10[.]132:53 - Standard query TXT 1.6932.images.google[.]com
- 16:34:46 - 217.23.10[.]132:53 - Standard query response TXT (317 bytes)
- 16:34:46 - 217.23.10[.]132:53 - Standard query TXT 2.6932.images.google[.]com
- 16:34:47 - 217.23.10[.]132:53 - Standard query response TXT (317 bytes)
- 16:34:47 - 217.23.10[.]132:53 - Standard query TXT 3.6932.images.google[.]com
- 16:34:47 - 217.23.10[.]132:53 - Standard query response TXT (317 bytes)
- 16:34:47 - 217.23.10[.]132:53 - Standard query TXT 4.6932.images.google[.]com
- 16:34:47 - 217.23.10[.]132:53 - Standard query response TXT (317 bytes)
- 16:34:47 - 217.23.10[.]132:53 - Standard query TXT 5.6932.images.google[.]com
- 16:34:47 - 217.23.10[.]132:53 - Standard query response TXT (317 bytes)
- 16:34:47 - 217.23.10[.]132:53 - Standard query TXT 6.6932.images.google[.]com
- 16:34:47 - 217.23.10[.]132:53 - Standard query response TXT (317 bytes)
- 16:34:47 - 217.23.10[.]132:53 - Standard query TXT 7.6932.images.google[.]com
- 16:34:48 - 217.23.10[.]132:53 - Standard query response TXT (317 bytes)
- 16:34:48 - 217.23.10[.]132:53 - Standard query TXT 8.6932.images.google[.]com
- 16:34:48 - 217.23.10[.]132:53 - Standard query response TXT (317 bytes)
- 16:34:48 - 217.23.10[.]132:53 - Standard query TXT 9.6932.images.google[.]com
- 16:34:48 - 217.23.10[.]132:53 - Standard query response TXT (317 bytes)
- 16:34:48 - 217.23.10[.]132:53 - Standard query TXT 10.6932.images.google[.]com
- 16:34:48 - 217.23.10[.]132:53 - Standard query response TXT (318 bytes)
- 16:34:48 - 217.23.10[.]132:53 - Standard query TXT 11.6932.images.google[.]com
- 16:34:48 - 217.23.10[.]132:53 - Standard query response TXT (318 bytes)
- 16:34:48 - 217.23.10[.]132:53 - Standard query TXT 12.6932.images.google[.]com
- 16:34:49 - 217.23.10[.]132:53 - Standard query response TXT (318 bytes)
- 16:34:49 - 217.23.10[.]132:53 - Standard query TXT 13.6932.images.google[.]com
- 16:34:49 - 217.23.10[.]132:53 - Standard query response TXT (318 bytes)
- 16:34:49 - 217.23.10[.]132:53 - Standard query TXT 14.6932.images.google[.]com
- 16:34:49 - 217.23.10[.]132:53 - Standard query response TXT (318 bytes)
- 16:34:49 - 217.23.10[.]132:53 - Standard query TXT 15.6932.images.google[.]com
- 16:34:49 - 217.23.10[.]132:53 - Standard query response TXT (318 bytes)
- 16:34:49 - 217.23.10[.]132:53 - Standard query TXT 16.6932.images.google[.]com
- 16:34:49 - 217.23.10[.]132:53 - Standard query response TXT (318 bytes)
- 16:34:49 - 217.23.10[.]132:53 - Standard query TXT 17.6932.images.google[.]com
- 16:34:50 - 217.23.10[.]132:53 - Standard query response TXT (318 bytes)
- 16:34:51 - 217.23.10[.]132:53 - Standard query TXT 18.6932.images.google[.]com
- 16:34:51 - 217.23.10[.]132:53 - Standard query response TXT (318 bytes)
- 16:34:51 - 217.23.10[.]132:53 - Standard query TXT 19.6932.images.google[.]com
- 16:34:51 - 217.23.10[.]132:53 - Standard query response TXT (318 bytes)
- Continues throughout pcap of traffic from infected VM.
POST-INFECTION TRAFFIC (FROM MALWR SANDBOX ANALYSIS OF MALWARE):
- 02:35:24 - 217.23.10[.]132:53 - Standard query ANY 5020.51ab1a6978ac5fec63139d96c6ed6f1c0fed1a40b6ed52203f.search.google[.]com
- 02:35:24 - 217.23.10[.]132:53 - Standard query response A 0.0.0[.]0 TXT (547 bytes)
- 02:35:24 - 50.77.231[.]183:53 - Standard query TXT 0.4565.images.horoshoza[.]com
- 02:35:24 - 50.77.231[.]183:53 - Standard query response TXT (320 bytes)
- 02:35:24 - 50.77.231[.]183:53 - Standard query TXT 1.4565.images.horoshoza[.]com
- 02:35:25 - 50.77.231[.]183:53 - Standard query response TXT (320 bytes)
- 02:35:25 - 50.77.231[.]183:53 - Standard query TXT 2.4565.images.horoshoza[.]com
- 02:35:25 - 50.77.231[.]183:53 - Standard query response TXT (320 bytes)
- 02:35:25 - 50.77.231[.]183:53 - Standard query TXT 3.4565.images.horoshoza[.]com
- 02:35:26 - 50.77.231[.]183:53 - Standard query response TXT (320 bytes)
- 02:35:26 - 50.77.231[.]183:53 - Standard query TXT 4.4565.images.horoshoza[.]com
- 02:35:26 - 50.77.231[.]183:53 - Standard query response TXT (320 bytes)
- 02:35:26 - 50.77.231[.]183:53 - Standard query TXT 5.4565.images.horoshoza[.]com
- 02:35:26 - 50.77.231[.]183:53 - Standard query response TXT (320 bytes)
- 02:35:26 - 50.77.231[.]183:53 - Standard query TXT 6.4565.images.horoshoza[.]com
- 02:35:27 - 50.77.231[.]183:53 - Standard query response TXT (320 bytes)
- 02:35:27 - 50.77.231[.]183:53 - Standard query TXT 7.4565.images.horoshoza[.]com
- 02:35:28 - 50.77.231[.]183:53 - Standard query response TXT (320 bytes)
- 02:35:28 - 50.77.231[.]183:53 - Standard query TXT 8.4565.images.horoshoza[.]com
- 02:35:28 - 50.77.231[.]183:53 - Standard query response TXT (320 bytes)
- 02:35:28 - 50.77.231[.]183:53 - Standard query TXT 9.4565.images.horoshoza[.]com
- 02:35:28 - 50.77.231[.]183:53 - Standard query response TXT (320 bytes)
- 02:35:28 - 50.77.231[.]183:53 - Standard query TXT 10.4565.images.horoshoza[.]com
- 02:35:29 - 50.77.231[.]183:53 - Standard query response TXT (321 bytes)
- 02:35:29 - 50.77.231[.]183:53 - Standard query TXT 11.4565.images.horoshoza[.]com
- 02:35:29 - 50.77.231[.]183:53 - Standard query response TXT (321 bytes)
- 02:35:29 - 50.77.231[.]183:53 - Standard query TXT 12.4565.images.horoshoza[.]com
- 02:35:30 - 50.77.231[.]183:53 - Standard query response TXT (321 bytes)
- 02:35:30 - 50.77.231[.]183:53 - Standard query TXT 13.4565.images.horoshoza[.]com
- 02:35:30 - 50.77.231[.]183:53 - Standard query response TXT (321 bytes)
- 02:35:30 - 50.77.231[.]183:53 - Standard query TXT 14.4565.images.horoshoza[.]com
- 02:35:30 - 50.77.231[.]183:53 - Standard query response TXT (321 bytes)
- 02:35:30 - 50.77.231[.]183:53 - Standard query TXT 15.4565.images.horoshoza[.]com
- 02:35:31 - 50.77.231[.]183:53 - Standard query response TXT (321 bytes)
- 02:35:31 - 50.77.231[.]183:53 - Standard query TXT 16.4565.images.horoshoza[.]com
- 02:35:31 - 50.77.231[.]183:53 - Standard query response TXT (321 bytes)
- 02:35:33 - 50.77.231[.]183:53 - Standard query TXT 17.4565.images.horoshoza[.]com
- 02:35:34 - 50.77.231[.]183:53 - Standard query response TXT (321 bytes)
- Continues throughout pcap from Malwr sandbox analysis of the malware.
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-06-28-Sweet-Orange-EK-flash-exploit.swf
File size: 4,337 bytes
MD5 hash: ad63d2543428a9dbde3b4d9d905e8733
Detection ratio: 2 / 49
First submission: 2014-06-27 08:27:22 UTC
VirusTotal link: https://www.virustotal.com/en/file/ebfa23acd2e6c2f315f322640ec279788efe97b9580568af9b9b60c4d1eafbc7/analysis/
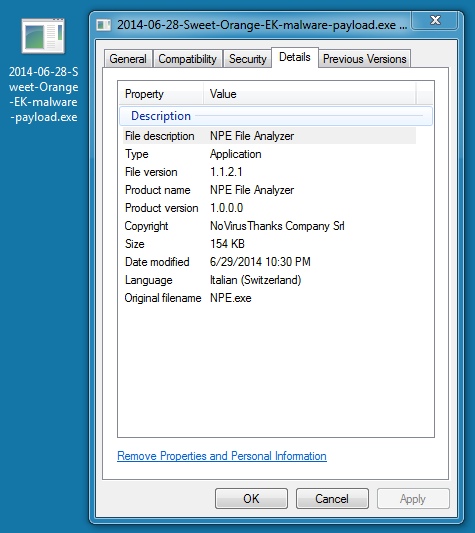
MALWARE PAYLOAD
File name: 2014-06-28-Sweet-Orange-EK-malware-payload.exe
File size: 158,208 bytes
MD5 hash: 41026646f5a0bab6f5bc0d118359b71a
Detection ratio: 28 / 54
First submission: 2014-06-28 13:57:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/255b5f2c8434eafd41a03cedaec29e45a46077cf464ea1c35bd54e58087c6a31/analysis/
Click here to return to the main page.