2014-06-29 - MAGNITUDE EK FROM 64.187.226[.]183 - 751.895A24.1C7872.05A3.4D.2DAFCA.A1E.C2.QGZOCPAL.SLIPTRIED[.]IN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS:
ASSOCIATED DOMAINS:
- 64.187.226[.]183 - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - Magnitude EK
- various IP addresses - various domains - Post-infection traffic (see below)
MAGNITUDE EK:
- 22:30:04 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /
- 22:30:12 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /ef89c4d318f7454b6dbad22254636ab7/30cb99adc78b03e3d3b264f6b9a96649
- 22:30:23 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /ef89c4d318f7454b6dbad22254636ab7/6dac6469b8d3b598be4adc5badc6356b
- 22:30:23 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /ef89c4d318f7454b6dbad22254636ab7/380bed34792a9c7125f56e1d793349cb
- 22:30:24 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /ef89c4d318f7454b6dbad22254636ab7/380bed34792a9c7125f56e1d793349cb
- 22:30:24 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /ef89c4d318f7454b6dbad22254636ab7/c7b000aed0739d2c7a5ac5da28e000fd
- 22:30:24 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /ef89c4d318f7454b6dbad22254636ab7/c7b000aed0739d2c7a5ac5da28e000fd
- 22:30:25 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /ef89c4d318f7454b6dbad22254636ab7/380bed34792a9c7125f56e1d793349cb
- 22:30:26 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /ef89c4d318f7454b6dbad22254636ab7/0 [!]
- 22:30:28 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /ef89c4d318f7454b6dbad22254636ab7/380bed34792a9c7125f56e1d793349cb
- 22:30:28 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /ef89c4d318f7454b6dbad22254636ab7/uzkr.class
- 22:30:28 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /ef89c4d318f7454b6dbad22254636ab7/1
- 22:30:29 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /ef89c4d318f7454b6dbad22254636ab7/uzkr.class
- 22:30:30 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /ef89c4d318f7454b6dbad22254636ab7/2
- 22:30:32 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /ef89c4d318f7454b6dbad22254636ab7/3 [!]
- 22:30:36 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /ef89c4d318f7454b6dbad22254636ab7/4 [!]
- 22:30:40 UTC - 751.895a24.1c7872.05a3.4d.2dafca.a1e.c2.qgzocpal.sliptried[.]in - GET /ef89c4d318f7454b6dbad22254636ab7/5 [!]
[!] indicates a malware payload was sent.
POST-INFECTION TRAFFIC:
- 22:30:32 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /p5lfp3baq3qe
- 22:30:37 UTC - 91.244.131.188:80 - carbiginer[.]com - GET /b/shoe/749634
- 22:30:40 UTC - 99.238.33[.]1:80 - goccefy[.]com - GET /mod_articles_news-96-789/jquery/
- 22:30:41 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /v32hoarl04
- 22:30:44 UTC - 31.184.192.202:80 - cd5c5c[.]com - POST /q
- 22:30:48 UTC - 31.184.192.202:80 - cd5c5c[.]com - POST /q
- 22:30:49 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /d3g77sn097k8g
- 22:30:49 UTC - 31.184.192.202:80 - cd5c5c[.]com - POST /q
- 22:30:50 UTC - 31.184.192.202:80 - cd5c5c[.]com - GET /dll
- 22:30:50 UTC - 31.184.192.202:80 - cd5c5c[.]com - POST /q
- 22:31:01 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /aevgwrkqzx8iji
- 22:32:04 UTC - 2.22.48.33 :80 - www.msftncsi[.]com - GET /ncsi.txt
- 22:32:08 UTC - 94.244.161.54:80 - goccefy[.]com - GET /mod_jshopping_filters-74-984/soft64.dll
- 22:32:24 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /ht095539kk2b
- 22:32:29 UTC - 85.29.190[.]85:80 - vision-vaper[.]su - GET /b/eve/d692eb926343190301a31d47
- 22:32:31 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /5fbsoqv8sy2
- 22:32:37 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /kfym4jy3o390n4s
- 22:32:45 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /x3q9pbxbul81
- 22:32:51 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /vrhucndzzn9ixq0
- 22:32:57 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /5pw55ccs7o75q
- 22:33:04 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /axen1mtnm2e4wr
- 22:33:13 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /8r9c5n0y4z4yww
- 22:33:23 UTC - 85.29.190[.]85:80 - vision-vaper[.]su - POST /b/opt/57CE7001706186F8C5B07469
- 22:33:23 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /wxi3wflyuq6
- 22:33:26 UTC - 85.29.190[.]85:80 - vision-vaper[.]su - GET /b/letr/535D4FBB3776BCC982A74E58
- 22:33:30 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /my73e15b4h0363
- 22:33:31 UTC - 178.18.18[.]30:443 - 178.18.18[.]30:443 - POST /b/opt/90B875CA010D5B84B4DCA915
- 22:33:38 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /2zdd02afds
- 22:33:45 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /xzsgbht0uok00
- 22:33:50 UTC - 178.18.18[.]30:443 - 178.18.18[.]30:443 - POST /b/req/1B1B401D6DE70EA8D836FC39
- 22:33:51 UTC - 178.18.18[.]30:443 - 178.18.18[.]30:443 - GET /b/eve/0adda4d9bf0c564818fce4cc
- 22:33:52 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /rd86wfz0a7
- 22:34:00 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /yh4eitdqw7j3w
- 22:34:08 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /sy620v2es9tv0h
- 22:34:15 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /ucj37drryo82shy
- 22:34:24 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /g5yx1yl7r27
- 22:34:30 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /348pba0mze
- 22:34:37 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /ghs51z3xwlffvgz
- 22:34:49 UTC - 178.18.18[.]30:443 - 178.18.18[.]30:443 - POST /b/req/F7D327685841B98CED904B1D
- 22:34:45 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /1r9cjlnw9l4d1
- 22:34:53 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /8d4o4ys5854x0iv
- 22:35:01 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /l10r95b108
- 22:35:05 UTC - 195.242.81[.]52:80 - vision-vaper[.]su - GET /b/eve/39aae2078c7b10961564c867
- 22:35:10 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /2sik115itnsur
- 22:35:19 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /8uncvu2s2ll
- 22:35:32 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /nql8fcbbjhy
- 22:35:40 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /3bkzspv486
- 22:35:47 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /ncaomai3ka
- 22:35:59 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /n47ase6z79w
- 22:36:02 UTC - 208.76.172[.]96:8080 - 208.76.172[.]96:8080 - POST /b/opt/BF2871B154B2ADBEE1635F2F
- 22:36:08 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /4sfpkxpy1zp3
- 22:36:16 UTC - 199.127.225[.]232:80 - vivatsaultppc[.]com - POST /ur0q3g6hd9449f
- 22:36:19 UTC - 208.76.172[.]96:8080 - 208.76.172[.]96:8080 - POST /b/req/B9CDD8ACEE8DEBE65B5C1977
- 22:36:21 UTC - 192.162.19.34:80 - resorts-search[.]com - GET /
- 22:36:21 UTC - 192.162.19.34:80 - aquariums-search[.]com - GET /
- 22:36:21 UTC - 192.162.19.34:80 - grand-search[.]com - GET /
- 22:36:21 UTC - 192.162.19.34:80 - victory-search[.]com - GET /
- 22:36:21 UTC - 192.162.19.34:80 - recommendation-search[.]com - GET /
- 22:36:21 UTC - 192.162.19.34:80 - sultan-search[.]com - GET /
- 22:36:21 UTC - 192.162.19.34:80 - ecored-search[.]com - GET /
- 22:36:21 UTC - 192.162.19.34:80 - sheikh-search[.]com - GET /
- 22:36:21 UTC - 192.162.19.34:80 - submission-search[.]com - GET /
- 22:36:21 UTC - 192.162.19.34:80 - country-search[.]com - GET /
- 22:36:21 UTC - 192.162.19.34:80 - cleopatra-search[.]com - GET /
- 22:36:21 UTC - 192.162.19.34:80 - available-search[.]com - GET /
- 22:36:21 UTC - 192.162.19.34:80 - calimera-search[.]com - GET /
- 22:36:21 UTC - 192.162.19.34:80 - aquariums-search[.]com - GET /
- 22:36:21 UTC - 192.162.19.34:80 - grand-search[.]com - GET /
- 22:36:22 UTC - 192.162.19.34:80 - lereve-search[.]com - GET /
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT:
File name: 2014-06-29-Magnitude-EK-java-exploit.jar
File size: 13,830 bytes
MD5 hash: 4ab8409d83b845f39f787ac0ba087811
Detection ratio: 2 / 54
First submission: 2014-06-30 21:53:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/8edf0aab22d5c16d4e1ea5f438a9ecb461bfbfc7a6db364cdba9fd434dec211b/analysis/
MALWARE TAKEN FROM THE VM:
- 2014-06-29-Magnitude-EK-malware-payload-1-of-4.exe - MD5: e59bb202d56f9f603d735fd34a66ad9f - 186,368 bytes - Virus Total link
- 2014-06-29-Magnitude-EK-malware-payload-2-of-4.exe - MD5: 08c6abc9d618b66b87a425d820f81350 - 92,688 bytes - Virus Total link
- 2014-06-29-Magnitude-EK-malware-payload-3-of-4.exe - MD5: 52d8656b13807412f92128dc95b57823 - 24,424 bytes - Virus Total link
- UpdateFlashPlayer_602e5b93.exe - MD5: b9a6a7b595d6d00424fabe037df305ec - 168,968 bytes - Virus Total link
NOTE: The malware payloads in the pcap are obfuscated with more than a simple XOR, so I couldn't decrypt them. I also couldn't find the last malware payload (4 of 4) on the infected VM, so it's not included here.
ALERTS
These alerts were generated using Sguil on Security Onion using the default Emerging Threats rule set. This list does not include the ET INFO or ET POLICY rules.
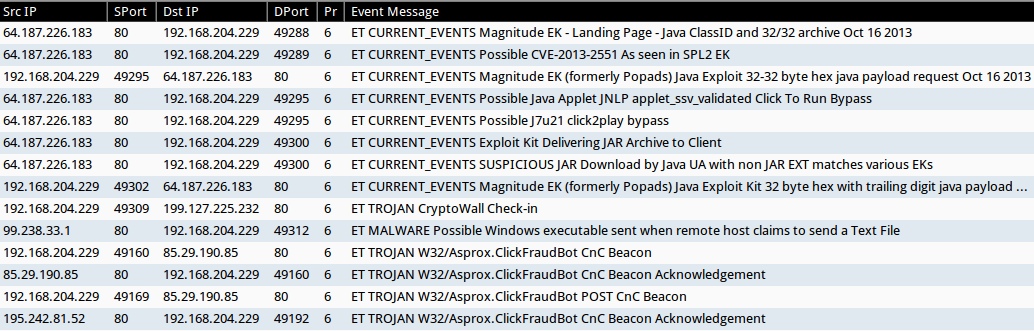
- 64.187.226[.]183:80 - ET CURRENT_EVENTS Magnitude EK - Landing Page - Java ClassID and 32/32 archive Oct 16 2013 (sid:2017602)
- 64.187.226[.]183:80 - ET CURRENT_EVENTS Possible CVE-2013-2551 As seen in SPL2 EK (sid:2017849)
- 64.187.226[.]183:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit 32-32 byte hex java payload request Oct 16 2013 (sid:2017603)
- 64.187.226[.]183:80 - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass (sid:2016797)
- 64.187.226[.]183:80 - ET CURRENT_EVENTS Possible J7u21 click2play bypass (sid:2017509)
- 64.187.226[.]183:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client (sid:2014526)
- 64.187.226[.]183:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs (sid:2016540)
- 64.187.226[.]183:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit Kit 32 byte hex with trailing digit java payload request (sid:2015888)
- 199.127.225[.]232:80 - ET TROJAN CryptoWall Check-in (sid:2018452)
- 99.238.33[.]1:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 85.29.190[.]85:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- 85.29.190[.]85:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 85.29.190[.]85:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
- 195.242.81[.]52:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
Click here to return to the main page.