2014-06-30 - INFINITY EK FROM 188.65.113[.]171 - D7HOSTING[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
INFINITY EK:
- 02:46:03 UTC - 188.65.113[.]171:80 - d7hosting[.]com - GET /slide/rarscanner.html
- 02:46:24 UTC - 188.65.113[.]171:80 - d7hosting[.]com - GET /6468.swf
- 02:46:24 UTC - 188.65.113[.]171:80 - d7hosting[.]com - GET /1581.xap
- 02:46:40 UTC - 188.65.113[.]171:80 - d7hosting[.]com - GET /55.mp3?rnd=26518
- 02:46:55 UTC - 188.65.113[.]171:80 - d7hosting[.]com - GET /55.mp3?rnd=69155
- 02:47:14 UTC - 188.65.113[.]171:80 - d7hosting[.]com - GET /37521495.mp3?rnd=43805
POST-INFECTION TRAFFIC:
- 02:47:21 UTC - 185.4.64[.]84:443 - HTTPS traffic to fargocrafts2[.]com
- 02:47:25 UTC - 185.4.64[.]84:443 - HTTPS traffic to fargocrafts2[.]com
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-06-30-Infinity-EK-flash-exploit.swf
File size: 4,084 bytes
MD5 hash: 368bf49f08111c32fed060a61ba87bac
Detection ratio: 0 / 54
First submission: 2014-06-11 17:05:02 UTC
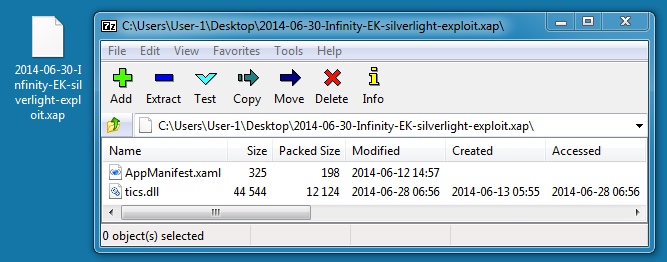
SILVERLIGHT EXPLOIT
File name: 2014-06-30-Infinity-EK-silverlight-exploit.xap
File size: 12,580 bytes
MD5 hash: 13110267b2764269c5e064cab95dca0c
Detection ratio: 0 / 54
First submission: 2014-06-28 13:21:02 UTC
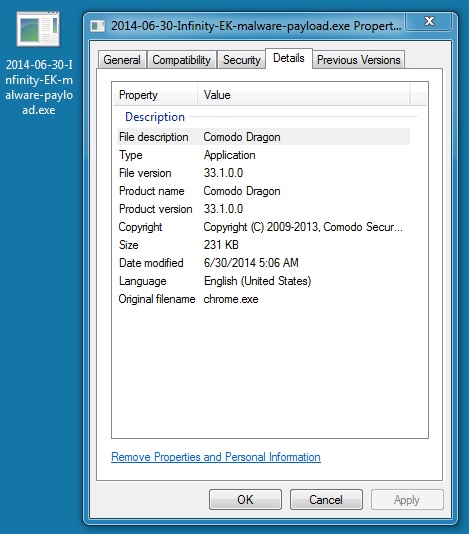
MALWARE PAYLOAD
File name: 2014-06-30-Infinity-EK-malware-payload.exe
File size: 237,332 bytes
MD5 hash: 42fa88a8a004de2edeb088f2713b78e5
Detection ratio: 3 / 54
First submission: 2014-06-30 03:07:25 UTC
ALERTS
These Snort events were taken from Sguil on Security Onion using the default Emerging Threats rule set. This list does not include the ET INFO or ET POLICY rules.
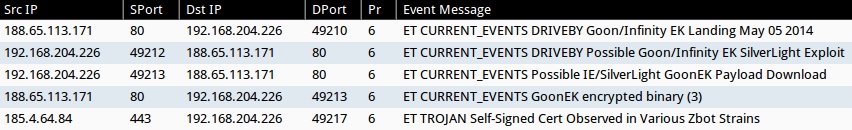
- 188.65.113[.]171:80 - ET CURRENT_EVENTS DRIVEBY Goon/Infinity EK Landing May 05 2014 (sid:2018440)
- 188.65.113[.]171:80 - ET CURRENT_EVENTS DRIVEBY Possible Goon/Infinity EK SilverLight Exploit (sid:2018402)
- 188.65.113[.]171:80 - ET CURRENT_EVENTS Possible IE/SilverLight GoonEK Payload Download (sid:2017998)
- 188.65.113[.]171:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3) (sid:2018297)
- 185.4.64[.]84:443 - ET TROJAN Self-Signed Cert Observed in Various Zbot Strains (sid:2018284)
Click here to return to the main page.