2014-07-03 - NUCLEAR EK SENDS CRYPTOWALL RANSOMWARE FROM 23.29.118[.]27 - 758672626-6.DRIVCELLENT[.]UNI[.]ME
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- The bitcoin address used by this particular CryptoWall ransomware is: 1M4pN4rH4LfXuTaJCL5tpnXJkbVRC35saU
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 23.29.118[.]27 - f9182c03z9mgj8.drivcellent[.]uni[.]me - Nuclear EK landing page
- 23.29.118[.]27 - 758672626-6.drivcellent[.]uni[.]me - Nuclear EK
- 194.58.101[.]96 - vivatsaultppc[.]com - post-infection HTTP CryptoWall ransomware traffic
- 94.156.77[.]26 - kpai7ycr7jxqkilp.enter2tor[.]com - post-infection HTTPS CryptoWall ransomware traffic
NUCLEAR EK:
- 00:43:21 UTC - 23.29.118[.]27:80 - f9182c03z9mgj8.drivcellent[.]uni[.]me - GET /
- 00:43:24 UTC - 23.29.118[.]27:80 - 758672626-6.drivcellent[.]uni[.]me - GET /1404327300.swf
- 00:43:31 UTC - 23.29.118[.]27:80 - 758672626-6.drivcellent[.]uni[.]me - GET /f/1404327300/7
- 00:43:33 UTC - 23.29.118[.]27:80 - 758672626-6.drivcellent[.]uni[.]me - GET /1404327300.htm
- 00:43:33 UTC - 23.29.118[.]27:80 - 758672626-6.drivcellent[.]uni[.]me - GET /1404327300.jar
- 00:43:35 UTC - 23.29.118[.]27:80 - 758672626-6.drivcellent[.]uni[.]me - GET /f/1404327300/5/x00e520804090407000700080150050f030
4045106565601;1;5 - 00:44:00 UTC - 23.29.118[.]27:80 - 758672626-6.drivcellent[.]uni[.]me - GET /1404327300.jar
- 00:44:01 UTC - 23.29.118[.]27:80 - 758672626-6.drivcellent[.]uni[.]me - GET /f/1404327300/2
- 00:44:04 UTC - 23.29.118[.]27:80 - 758672626-6.drivcellent[.]uni[.]me - GET /f/1404327300/2/2
POST-INFECTION TRAFFIC:
- 00:43:36 UTC - 194.58.101[.]96:80 - vivatsaultppc[.]com - POST /x1vm3508h0wn
- 00:43:38 UTC - [local host]:53 - DNS query for: domainsfullkolls[.]biz
- 00:43:38 UTC - [local host]:53 - UTC - DNS response for domainsfullkolls[.]biz as: 94.242.216[.]61 [no follow-up traffic noted]
- 00:43:39 UTC - 194.58.101[.]96:80 - vivatsaultppc[.]com - POST /3srclktnmtcu27c
- 00:44:00 UTC - 194.58.101[.]96:80 - vivatsaultppc[.]com - POST /qbzcvgwqkzr8zw
- 00:44:01 UTC - 94.156.77[.]26:443 - HTTPS traffic to kpai7ycr7jxqkilp.enter2tor[.]com
- 00:44:06 UTC - 194.58.101[.]96:80 - vivatsaultppc[.]com - POST /w5bt74v22rlpfhx
- 00:44:06 UTC - 94.156.77[.]26:443 - HTTPS traffic to kpai7ycr7jxqkilp.enter2tor[.]com
- 00:44:06 UTC - 94.156.77[.]26:443 - HTTPS traffic to kpai7ycr7jxqkilp.enter2tor[.]com
- 00:44:06 UTC - 94.156.77[.]26:443 - HTTPS traffic to kpai7ycr7jxqkilp.enter2tor[.]com
- 00:44:06 UTC - 94.156.77[.]26:443 - HTTPS traffic to kpai7ycr7jxqkilp.enter2tor[.]com
- 00:44:06 UTC - 94.156.77[.]26:443 - HTTPS traffic to kpai7ycr7jxqkilp.enter2tor[.]com
- 00:44:09 UTC - 194.58.101[.]96:80 - vivatsaultppc[.]com - POST /3640m0hzrz4i
- 00:44:13 UTC - 194.58.101[.]96:80 - vivatsaultppc[.]com - POST /4z824ft4kum
- 00:44:13 UTC - 94.156.77[.]26:443 - HTTPS traffic to kpai7ycr7jxqkilp.enter2tor[.]com
- 00:44:20 UTC - 94.156.77[.]26:443 - HTTPS traffic to kpai7ycr7jxqkilp.enter2tor[.]com
- 00:44:20 UTC - 94.156.77[.]26:443 - HTTPS traffic to kpai7ycr7jxqkilp.enter2tor[.]com
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-07-03-Nuclear-EK-flash-exploit.swf
File size: 4,309 bytes
MD5 hash: d008e2d6f73f7eb816ee176fa5df62b2
Detection ratio: 1 / 53
First submission: 2014-07-02 20:02:06 UTC
VirusTotal link: https://www.virustotal.com/en/file/e63667e4eab40e3caca83e4d5ba8c0eb3e94c3806147f43223aa442632353c15/analysis/
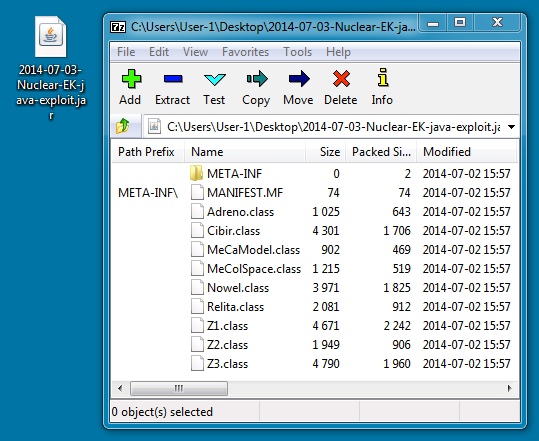
JAVA EXPLOIT
File name: 2014-07-03-Nuclear-EK-java-exploit.jar
File size: 12,560 bytes
MD5 hash: a885718f803c09c0649523bdb6df13b1
Detection ratio: 4 / 53
First submission: 2014-07-02 12:40:01 UTC
VirusTotal link: https://www.virustotal.com/en/file/9cf2368f097f9e270a695b24450b98857f4da48c5418ff4c5effda005228dab6/analysis/
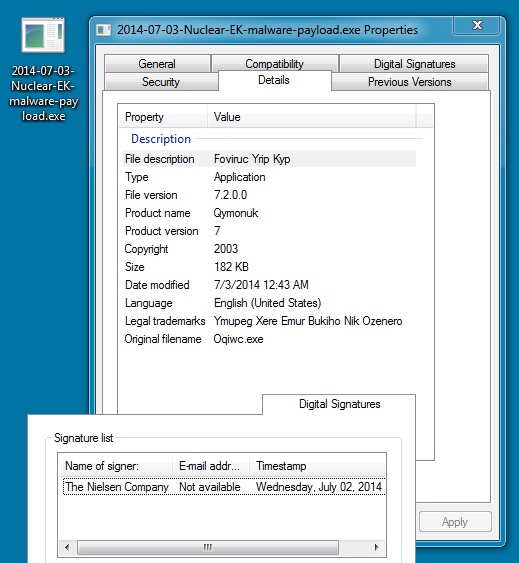
MALWARE PAYLOAD
File name: 2014-07-03-Nuclear-EK-malware-payload.exe
File size: 186,488 bytes
MD5 hash: 1625fd5912a2d620c4a423227d59b241
Detection ratio: 4 / 54
First submission: 2014-07-03 01:42:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/968d47391cddb4ff7ca360d805409365799e0b3fadd74feef07505213db64ba2/analysis/
Click here to return to the main page.