2014-07-04 - NUCLEAR EK ON 5.135.211[.]48 - EDC.VIRTUALTRAVELEVENTS[.]NET
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 54.86.234[.]106 - www.likemagicbox[.]com - First redirect (don't know who the original referer was)
- 162.247.12[.]165 - coaches.toasthousemarket[.]com - Second redirect
- 5.135.211[.]48 - edc.virtualtravelevents[.]net - Nuclear EK
- Various IP addresses - various domains - Post-infection traffic from sandbox analysis
REDIRECT CHAIN LEADING TO NUCLEAR EK:
- 00:58:48 UTC - 54.86.234[.]106:80 - www.likemagicbox[.]com - GET /fusionx/www/delivery/afr.php?zoneid=603&cb=34531279210
- 00:58:48 UTC - 162.247.12[.]165:80 - coaches.toasthousemarket[.]com - GET /assets/js/jquery-1.3.1.min.js?ver=3.75.8698
NUCLEAR EK:
- 00:58:49 UTC - 5.135.211[.]48:80 - edc.virtualtravelevents[.]net - GET /58c92896mv39x6.html
- 00:59:00 UTC - 5.135.211[.]48:80 - edc.virtualtravelevents[.]net - GET /3020225639/3/1404414600.jar
- 00:59:01 UTC - 5.135.211[.]48:80 - edc.virtualtravelevents[.]net - GET /f/3/1404414600/3020225639/2
- 00:59:02 UTC - 5.135.211[.]48:80 - edc.virtualtravelevents[.]net - GET /f/3/1404414600/3020225639/2/2
PCAP FROM SANDBOX ANALYSIS OF THE MALWARE:
- 01:11:08 UTC - 134.249.9[.]253:80 - lare-funer[.]com - GET /b/shoe/1480
- 01:11:08 UTC - 134.249.9[.]253:80 - lare-funer[.]com - GET /b/shoe/1480
- 01:11:10 UTC - 68.45.64[.]5:80 - arrival-tuer[.]com - GET /mod_articles-78.34/jquery/
- 01:12:20 UTC - 50.46.181[.]179:80 - arrival-tuer[.]com - GET /mod_jshopping-12.32/soft32.dll
- 01:12:26 UTC - 99.238.33[.]1:80 - vision-vaper[.]su - GET /b/eve/b2679c30b956c3c5301871dd
- 01:13:25 UTC - 99.238.33[.]1:80 - vision-vaper[.]su POST /b/opt/394E49754B7EF459404FABAC
- 01:13:26 UTC - 99.238.33[.]1:80 - vision-vaper[.]su - GET /b/letr/B8B05C930D24C00306159FF6
- 01:13:27 UTC - 31.192.209[.]243:8080 - 31.192.209[.]243:8080 - POST /b/opt/99076BD6C7D87019CCE92FEC
- 01:13:28 UTC - 31.192.209[.]243:8080 - 31.192.209[.]243:8080 - GET /b/letr/3A5E7D65AB927416A0A32BE3
- 01:13:28 UTC - 194.38.104[.]218:443 - POST /b/opt/2174CE4ED7882393DCB97C66
- 01:13:28 UTC - 194.38.104[.]218:443 - POST /b/req/F92E8B58573E4A535C0F15A6
PRELIMINARY MALWARE ANALYSIS
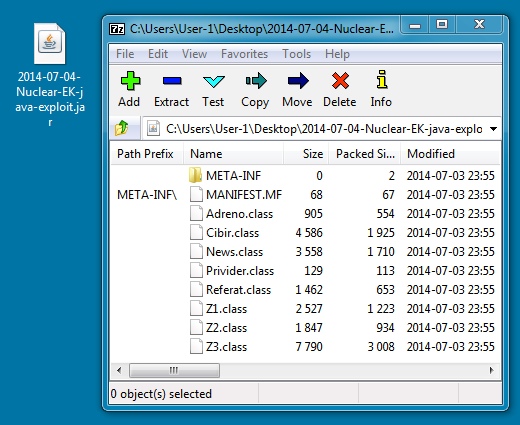
JAVA EXPLOIT
File name: 2014-07-04-Nuclear-EK-java-exploit.jar
File size: 11,365 bytes
MD5 hash: 3bbf5967da5b854ae3103722e69f5437
Detection ratio: 2 / 54
First submission: 2014-07-04 01:08:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/d57f9b53c89bfa09272eb92e7a6d238a9b35c6db8910195d82dc5604b348f2fe/analysis/
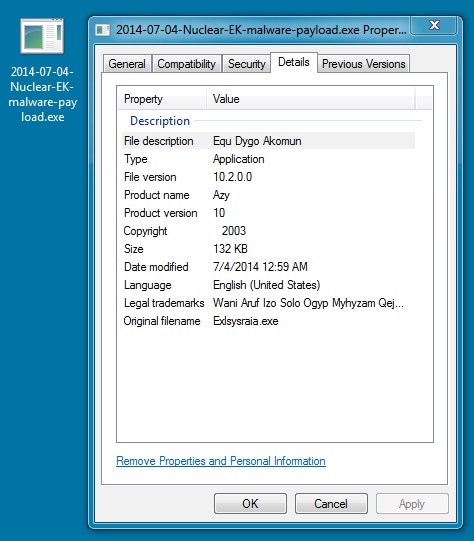
MALWARE PAYLOAD
File name: 2014-07-04-Nuclear-EK-malware-payload.exe
File size: 135,680 bytes
MD5 hash: bf523d17c9ee2fffd0dae1431a729927
Detection ratio: 3 / 54
First submission: 2014-07-04 01:08:47 UTC
VirusTotal link: https://www.virustotal.com/en/file/e2adbf56f9aee4711b296eb0ce62afda1e97235ae95fb16d511e8629d6850b8e/analysis/
FOLLOW-UP MALWARE
File name: 2014-07-04-Nuclear-EK-post-infection-malware.exe
File size: 168,968 bytes
MD5 hash: 0bdf4a4c27fe59b370e4cce0db3bb502
Detection ratio: 10 / 54
First submission: 2014-07-04 01:28:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/e14f03337a7d9963a56d5f3ca7dca15cb8d149c96da03f8707b400a1a4ee8220/analysis/
ALERTS FROM THE INITIAL INFECTION
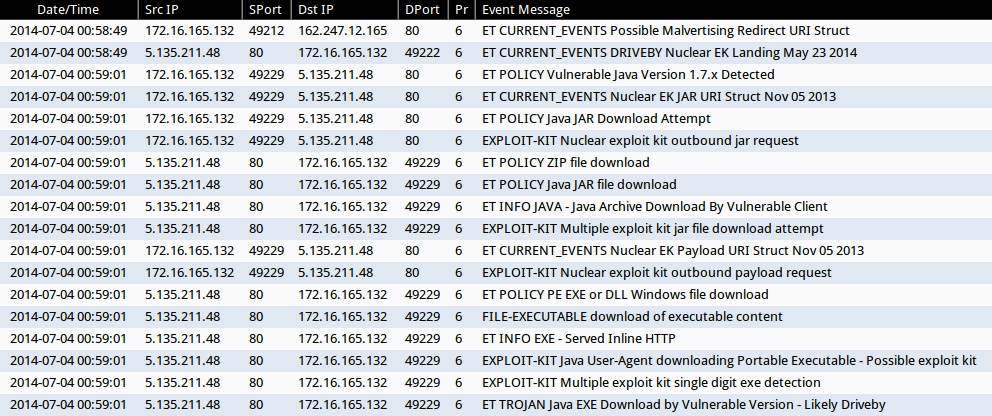
Emerging Threats and ETPRO rulesets (not including ET INFO or ET POLICY signatures):
- 162.247.12[.]165:80 - ET CURRENT_EVENTS Possible Malvertising Redirect URI Struct (sid:2018454)
- 5.135.211[.]48:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing May 23 2014 (sid:2018595)
- 5.135.211[.]48:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 5.135.211[.]48:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013 (sid:2017666)
- 5.135.211[.]48:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby (sid:2013036)
Sourcefire VRT ruleset:
- 5.135.211[.]48:80 - EXPLOIT-KIT Multiple exploit kit jar file download attempt (sid:27816)
- 5.135.211[.]48:80 - EXPLOIT-KIT Nuclear exploit kit outbound payload request (sid:30220)
- 5.135.211[.]48:80 - FILE-EXECUTABLE download of executable content (sid:11192)
- 5.135.211[.]48:80 - EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit (sid:25042)
- 5.135.211[.]48:80 - EXPLOIT-KIT Multiple exploit kit single digit exe detection (sid:28423)
- 5.135.211[.]48:80 - EXPLOIT-KIT Nuclear exploit kit outbound jar request (sid:30219)
NOTE: These Snort events were taken from Sguil on Security Onion
ALERTS FROM SANDBOX ANALYSIS OF THE MALWARE
Emerging Threats and ETPRO rulesets (not including ET INFO or ET POLICY signatures):
- 2014-07-04 00:11:08 UTC - 134.249.9[.]253:80 - [1:2807742:1] ETPRO TROJAN Trojan-Spy.Win32.Zbot.relx Checkin
- 2014-07-04 00:11:08 UTC - 134.249.9[.]253:80 - [1:2807742:1] ETPRO TROJAN Trojan-Spy.Win32.Zbot.relx Checkin
- 2014-07-04 00:11:11 UTC - 68.45.64[.]5:80 - [1:2008438:7] ET MALWARE Possible Windows executable sent when remote host claims to send a Text File
- 2014-07-04 00:12:20 UTC - 50.46.181[.]179:80 - [1:2010706:6] ET USER_AGENTS Internet Explorer 6 in use - Significant Security Risk
- 2014-07-04 00:12:26 UTC - 99.238.33[.]1:80 - [1:2018096:1] ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon
- 2014-07-04 00:12:27 UTC - 99.238.33[.]1:80 - [1:2018097:1] ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement
- 2014-07-04 00:13:25 UTC - 99.238.33[.]1:80 - [1:2018098:2] ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon
- 2014-07-04 00:13:27 UTC - 31.192.209[.]243:8080 - [1:2018098:2] ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon
Sourcefire VRT ruleset:
- 2014-07-04 00:11:11 UTC - 68.45.64[.]5:80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP
- 2014-07-04 00:11:11 UTC - 68.45.64[.]5:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 2014-07-04 00:11:11 UTC - 68.45.64[.]5:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-04 00:11:11 UTC - 68.45.64[.]5:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-07-04 00:12:24 UTC - [local host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-07-04 00:12:26 UTC - 99.238.33[.]1:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-04 00:13:25 UTC - 99.238.33[.]1:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-04 00:13:26 UTC - 99.238.33[.]1:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-04 00:13:27 UTC - 31.192.209[.]243:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-04 00:13:28 UTC - 31.192.209[.]243:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
Click here to return to the main page.