2014-07-09 - KULUOZ INFECTION FROM LINK IN ASPROX BOTNET EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-07-09-Kuluoz-infection-from-Asprox-botnet-emails-3-pcaps.zip
- 2014-07-09-Kuluoz-malware-example.zip
TODAY'S EMAILS
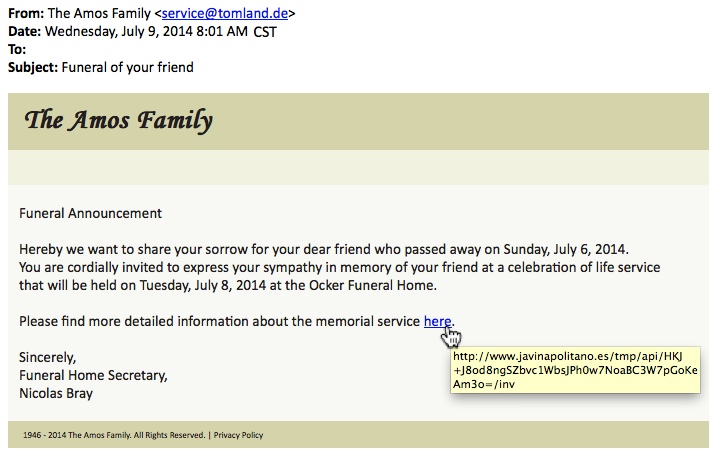
SCREENSHOTS:
SUBJECT LINE:
Funeral of your friend
MESSAGE:
Funeral Announcement
Hereby we want to share your sorrow for your dear friend who passed away on Sunday, July 6, 2014.
You are cordially invited to express your sympathy in memory of your friend at a celebration of life service
that will be held on Tuesday, July 8, 2014 at the Ocker Funeral Home.
Please find more detailed information about the memorial service here.
Sincerely,
Funeral Home Secretary,
[different names used]
LINKS FROM THE EMAILS TO THE MALWARE:
- 64.90.54[.]129 - www.ifim[.]com[.]br/components/api/YdBbXBf/a5jNAQKCBj3rVKcFxhEKfTL50hMnzF4BxI0=/inv
- 192.55.193[.]162 - www.javinapolitano[.]es/tmp/api/HKJ+J8od8ngSZbvc1WbsJPh0w7NoaBC3W7pGoKeAm3o=/inv
NOTE: The link above for www.javinapolitano[.]es did not work for me.
PRELIMINARY MALWARE ANALYSIS
DOWNLOADED ZIP ARCHIVE:
File name: FuneralInvitation_San_Antonio.zip
File size: 80,391 bytes
MD5 hash: 5eb4150af5a153241b2aee1bd78e8033
Detection ratio: 3 / 54
First submission: 2014-07-09 18:17:19 UTC
VirusTotal link: https://www.virustotal.com/en/file/7ca5f69099a9f002255cbfe12b378818b7daae087d85e38098d1069919e6daa8/analysis/
EXTRACTED FILE:
File name: FuneralInvitation_San_Antonio.exe
File size: 120,832 bytes
MD5 hash: f389a95e7cb672c37501143e9d418def
Detection ratio: 4 / 54
First submission: 2014-07-09 18:17:33 UTC
VirusTotal link: https://www.virustotal.com/en/file/3405743613d8393f430bde91070b690c04a03dcbe64cee79c56ad001f2a6a468/analysis/
TRAFFIC FROM SANDBOX ANALYSIS OF MALWARE
Malwr sandbox analysis:
- 18:19:39 UTC - 142.4.60[.]242:443 - POST /460326245047F2B6E405E92260B09AA0E35D7CA2B1
Other sandbox analysis on the same malware earlier in the day:
- 16:30:56 UTC - 92.240.232[.]232:443 - POST /BBFC8F9EDEB972DE1BE5401CED593A5ABB33E12DA8
- 16:31:02 UTC - 188.165.192[.]116:8080 - POST /BBFC8F9EDEB972DE1BE5401CED593A5ABB33E12DA8
- 16:31:02 UTC - 113.53.247[.]147:443 - POST /BBFC8F9EDEB972DE1BE5401CED593A5ABB33E12DA8
- 16:31:08 UTC - 94.32.67[.]214:8080 - POST /BBFC8F9EDEB972DE1BE5401CED593A5ABB33E12DA8
- 16:31:11 UTC - 50.57.139[.]41:8080 - POST /BBFC8F9EDEB972DE1BE5401CED593A5ABB33E12DA8
- 16:31:14 UTC - 203.157.142[.]2:8080 - POST /BBFC8F9EDEB972DE1BE5401CED593A5ABB33E12DA8
- 16:31:17 UTC - 212.45.17[.]15:8080 - POST /BBFC8F9EDEB972DE1BE5401CED593A5ABB33E12DA8
Click here to return to the main page.