2014-07-09 - FIESTA EK FROM 64.202.116[.]156 - GPOISON[.]IN[.]UA
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 64.202.116[.]156 - gpoison[.]in[.]ua - Fiesta EK
- 5.149.248[.]153 - report.a3k793w7931ws31s9ei[.]com - Post-infection traffic
- 79.142.66[.]239 - update.74knli1n7ctr61[.]com and report.a3k793w7931ws31s9ei[.]com - Post-infection traffic
FIESTA EK:
- 23:54:10 UTC - 64.202.116[.]156 - gpoison[.]in[.]ua - GET /d9gj8h5/2
- 23:54:12 UTC - 64.202.116[.]156 - gpoison[.]in[.]ua - GET /d9gj8h5/5be2605ccb74a5cc5c070909040b0751025a5109025205580051075652050154
- 23:54:12 UTC - 64.202.116[.]156 - gpoison[.]in[.]ua - GET /d9gj8h5/1a76467ec4de90654216510d060d05570659030d0054075e0452555250030352;112202;228
- 23:54:20 UTC - 64.202.116[.]156 - gpoison[.]in[.]ua - GET /d9gj8h5/5fdb77861a072673460a1259050c0a04025e50590355080d0055060653020c01;4060129
- 23:54:21 UTC - 64.202.116[.]156 - gpoison[.]in[.]ua - GET /d9gj8h5/6597b243d87e8b315545520c50090601010d0d0c5650040803065b530607000a;4
- 23:54:28 UTC - 64.202.116[.]156 - gpoison[.]in[.]ua - GET /d9gj8h5/6597b243d87e8b315545520c50090601010d0d0c5650040803065b530607000a;4;1
- 23:54:30 UTC - 64.202.116[.]156 - gpoison[.]in[.]ua - GET /d9gj8h5/6098c8929c7856505742580351030b0001080d03575a090903035b5c070d0d05
- 23:54:30 UTC - 64.202.116[.]156 - gpoison[.]in[.]ua - GET /d9gj8h5/283a6c803fc6a6365148585a04580a020500075a0201080b070b510552560c07;5
- 23:54:37 UTC - 64.202.116[.]156 - gpoison[.]in[.]ua - GET /d9gj8h5/283a6c803fc6a6365148585a04580a020500075a0201080b070b510552560c07;5;1
- 23:54:38 UTC - 64.202.116[.]156 - gpoison[.]in[.]ua - GET /d9gj8h5/12c844ae3fc6a63652420803060f5357060a57030056515e0401015c50015552;6
- 23:54:45 UTC - 64.202.116[.]156 - gpoison[.]in[.]ua - GET /d9gj8h5/12c844ae3fc6a63652420803060f5357060a57030056515e0401015c50015552;6;1
- 23:54:46 UTC - 64.202.116[.]156 - gpoison[.]in[.]ua - GET /d9gj8h5/666d1bbbf4cd9990554e535f03595050010e025f050052590305540055575655;1;2
- 23:54:52 UTC - 64.202.116[.]156 - gpoison[.]in[.]ua - GET /d9gj8h5/666d1bbbf4cd9990554e535f03595050010e025f050052590305540055575655;1;2;1
POST-INFECTION TRAFFIC FROM SANDBOX ANALYSIS:
- 00:11:57 UTC - 79.142.66[.]239:80 - report.a3k793w7931ws31s9ei[.]com - GET /?3179w31=%96%9D%A2%A0%[long string of characters]
- 00:11:57 UTC - 5.149.248[.]153:80 - report.a3k793w7931ws31s9ei[.]com - POST /
- 00:11:57 UTC - 5.149.248[.]153:80 - update.74knli1n7ctr61[.]com - GET /?14=ka2ilZmly5Romc2j0ZmVnm2b1tWX[long string of characters]
- 00:11:58 UTC - 79.142.66[.]239:80 - report.a3k793w7931ws31s9ei[.]com - GET /?SK9y43=%96%9D%A2%A0%[long string of characters]
- 00:11:58 UTC - 79.142.66[.]239:80 - report.a3k793w7931ws31s9ei[.]com - GET /?9c17u20=%96%9D%A2%A0%[long string of characters]
- 00:11:58 UTC - 79.142.66[.]239:80 - report.a3k793w7931ws31s9ei[.]com - GET /?e1aAAA17=%96%9D%A2%A0%[long string of characters]
- 00:11:58 UTC - 79.142.66[.]239:80 - report.a3k793w7931ws31s9ei[.]com - GET /?55gM558=%96%9D%A2%A0%[long string of characters]
- 00:11:58 UTC - 79.142.66[.]239:80 - report.a3k793w7931ws31s9ei[.]com - GET /?79e17k355=%96%9D%A2%A0%[long string of characters]
- 00:12:03 UTC - 79.142.66[.]239:80 - report.a3k793w7931ws31s9ei[.]com - GET /?17mY116=%96%9D%A2%A0%[long string of characters]
- 00:12:14 UTC - 79.142.66[.]239:80 - report.a3k793w7931ws31s9ei[.]com - GET /?3y7cEI709=%96%9D%A2%A0%[long string of characters]
- 00:12:24 UTC - 204.79.197[.]200:80 - www.bing[.]com - GET /chrome/report.html?1u9m1=%9B%EE%EDk%D9%[long string of characters]
- 00:12:25 UTC - 79.142.66[.]239:80 - report.a3k793w7931ws31s9ei[.]com - GET /?Y7cE25=%96%9D%A2%A0%[long string of characters]
- 00:12:25 UTC - 79.142.66[.]239:80 - report.a3k793w7931ws31s9ei[.]com - GET /?17g3iQG57=%96%9D%A2%A0%[long string of characters]
- 00:12:25 UTC - 79.142.66[.]239:80 - report.a3k793w7931ws31s9ei[.]com - GET /?17o317i63=%96%9D%A2%A0%[long string of characters]
- 00:12:26 UTC - 79.142.66[.]239:80 - report.a3k793w7931ws31s9ei[.]com - GET /?17931sK18=%96%9D%A2%A0%[long string of characters]
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-07-09-Fiesta-EK-flash-exploit.swf
File size: 10,039 bytes
MD5 hash: a893630ee0690b9823a7411a4b15949e
Detection ratio: 0 / 53
First submission: 2014-07-09 13:53:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/8dc95e2b5c98e355dceec09c683362bdb453f14d171e99d0422a278d0b012cc9/analysis/
File name: 2014-07-09-Fiesta-EK-flash-exploit-uncompressed.swf
File size: 15,668 bytes
MD5 hash: 6756e1563fcb97234cb129acb2a201fa
Detection ratio: 0 / 54
First submission: 2014-07-10 00:16:54 UTC
VirusTotal link: https://www.virustotal.com/en/file/2fcb4eb223c733eb388c4cec50ad16723d3ccce5ef3fcbf38aea63ac04ebf241/analysis/
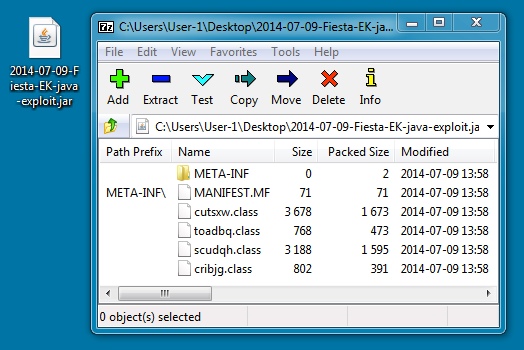
JAVA EXPLOIT
File name: 2014-07-09-Fiesta-EK-java-exploit.jar
File size: 4,941 bytes
MD5 hash: 7526d3bebafefe3a219236ab3c29ea3b
Detection ratio: 2 / 54
First submission: 2014-07-10 00:17:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/839a6beb74ffdd94eaeb0cd403515edff3ac18b0cfe37da439d5393f7933c678/analysis/
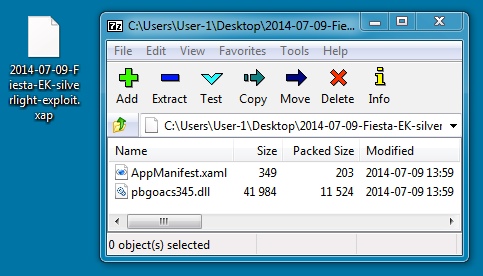
SILVERLIGHT EXPLOIT
File name: 2014-07-09-Fiesta-EK-silverlight-exploit.xap
File size: 11,961 bytes
MD5 hash: cb8fe8f15d1f8e320d7050640919e77e
Detection ratio: 1 / 54
First submission: 2014-07-10 00:17:35 UTC
VirusTotal link: https://www.virustotal.com/en/file/fda83f0b8c42f823a735ec3f37e9768ee330c6006c6105edfb6e8e053e2dba5f/analysis/
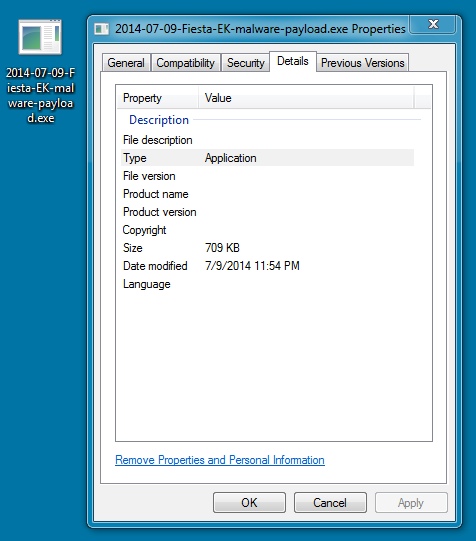
MALWARE PAYLOAD
File name: 2014-07-09-Fiesta-EK-malware-payload.exe
File size: 726,528 bytes
MD5 hash: 575f8b8b898472b381e99cb1686d4ade
Detection ratio: 7 / 53
First submission: 2014-07-10 00:05:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/48e263d42ffd3b8c994acce5f5e6c8cd1dda5d2a858435a28b17b98117dd42df/analysis/
Click here to return to the main page.