2014-07-10 - NUCLEAR EK FROM 93.189.40[.]229 - GUMENO.YAHOOAPLE[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- I first discovered www.mirneboskrebov[.]ru was compromised on 2014-06-02 ( link ).
- Today, that site generated a redirect to Nuclear EK traffic in the same manner as shown in my previous blog entry.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 5.9.141[.]183 - www.mirneboskrebov[.]ru - Compromised website
- 188.226.208[.]231 - gosinaj.cynthiamartinez[.]com[.]ar - Redirect
- 93.189.40[.]229 - gumeno.yahooaple[.]com - Nuclear EK
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 16:21:37 UTC - 5.9.141[.]183:80 - www.mirneboskrebov[.]ru - GET /category/arxitektory/
- 16:21:37 UTC - 5.9.141[.]183:80 - www.mirneboskrebov[.]ru - GET /wp-content/plugins/featured-content-gallery/scripts/mootools.v1.11.js
- 16:21:39 UTC - 188.226.208[.]231:80 - gosinaj.cynthiamartinez[.]com[.]ar - GET /link15.hotbox
NUCLEAR EK:
- 16:21:40 UTC - 93.189.40[.]229:80 - gumeno.yahooaple[.]com - GET /a40c4046ht2.html
- 16:21:53 UTC - 93.189.40[.]229:80 - gumeno.yahooaple[.]com - GET /3827605767/1/1404988500.jar
- 16:21:54 UTC - 93.189.40[.]229:80 - gumeno.yahooaple[.]com - GET /f/1/1404988500/3827605767/2
- 16:21:55 UTC - 93.189.40[.]229:80 - gumeno.yahooaple[.]com - GET /f/1/1404988500/3827605767/2/2
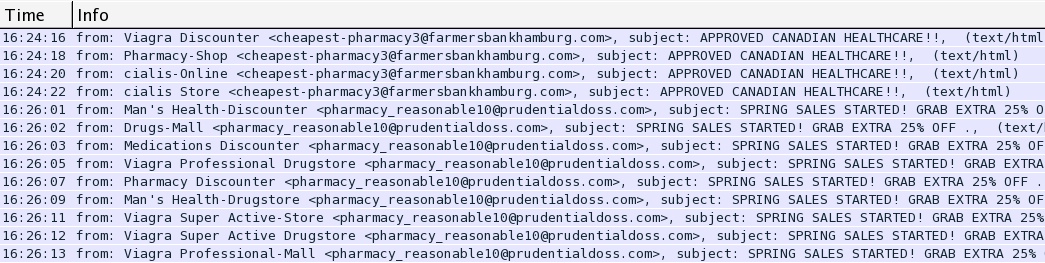
POST-INFECTION TRAFFIC:
- Google connectivity check by the malware
- SMTP pharmacy spam on TCP port 25
PRELIMINARY MALWARE ANALYSIS
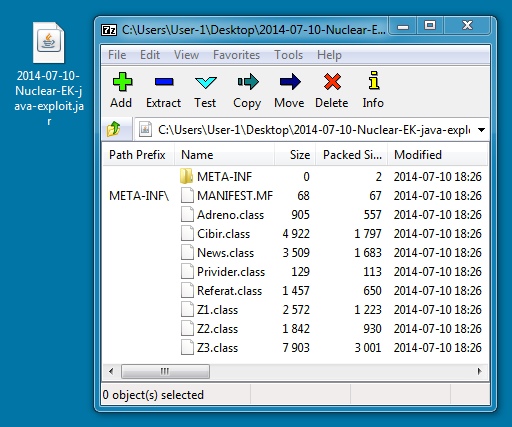
JAVA EXPLOIT:
File name: 2014-07-10-Nuclear-EK-java-exploit.jar
File size: 11,199 bytes
MD5 hash: 5fe052dc0f01e3d4c75fafe6ef5d8e2e
Detection ratio: 1 / 54
First submission: 2014-07-10 20:51:26 UTC
VirusTotal link: https://www.virustotal.com/en/file/35121c1a3996baf8110215b8046a68f70e03dee0e60879a95501b70421e1d686/analysis/
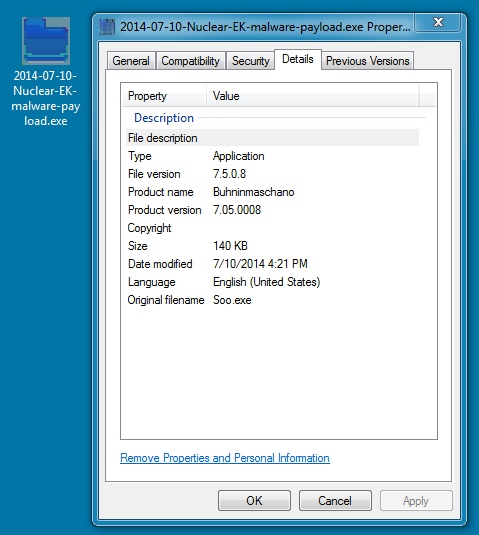
MALWARE PAYLOAD:
File name: 2014-07-10-Nuclear-EK-malware-payload.exe
File size: 143,360 bytes
MD5 hash: f31d2d8bdc00fa7a39d7558ea4bbf08b
Detection ratio: 4 / 47
First submission: 2014-07-10 15:25:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/8463ba7986419ef4a0afeb8e33fa26ed529975a668b1f31e12a0ac0f8e714646/analysis/
Click here to return to the main page.