2014-07-11 - ANGLER EK FROM 192.154.110[.]237 - 41N.DEGOODYX[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 192.154.110[.]237 - 41n.degowodyx[.]com - Angler EK
ANGLER EK:
- 02:23:50 UTC - 41n.degowodyx[.]com - GET /lwq6kymc7s
- 02:23:52 UTC - 41n.degowodyx[.]com - GET /l_vmLhIT5qHoXVuVY4nAJ-BHKgZyW48YIIdnu27x3X_rMYhL0lU70rGs6mVJNZRw
- 02:23:54 UTC - 41n.degowodyx[.]com - GET /3pDKqBoUNBqRLPnu_ED5jdoza-Bqb9pgn5WbXXLIu4j7QHRrddr_9giMZT2OnuDr
- 02:24:14 UTC - 41n.degowodyx[.]com - GET /MFzaD0NzpHe8o6Uj1yAwPk5mMiAqdgKg-mCpdTfv_5MphhFy3LIpxAi87E4mSsKq
- 02:24:16 UTC - 41n.degowodyx[.]com - GET /ui8SOuhx56hsSkLLwzUJIbSmoUjjvSqGIxaSdp9CqgRLEe5CX4qZw3trIzL_XNFa
- 02:24:17 UTC - 41n.degowodyx[.]com - GET /UO1KG0XZQJvHfQYndRt3asGEdIyAMSsHZ6d99vR8RV-PifsJGrHDHkFgAyyY6Zg4
POST-INFECTION TRAFFIC FROM THE SANDBOX ANALYSIS:
- DNS query for ns6.figaina5[.]net - resolved to 15.206.174[.]69 but no followup traffic to that IP address
- TCP traffic over port 53 to 85.17.139[.]17
PRELIMINARY MALWARE ANALYSIS
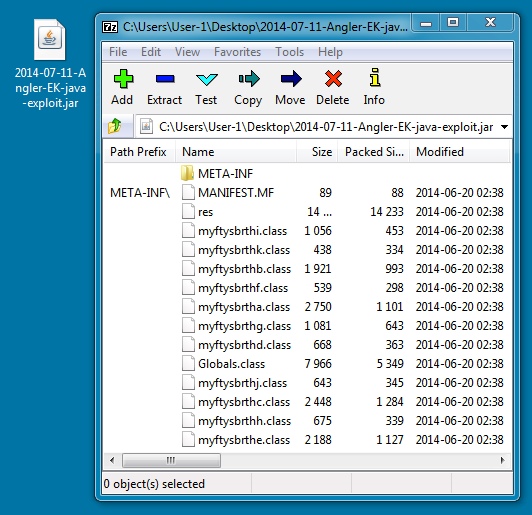
JAVA EXPLOIT:
File name: 2014-07-11-Angler-EK-java-exploit.jar
File size: 28,721 bytes
MD5 hash: d9905f9daf40cc3ea7c0f4cf69eeb716
Detection ratio: 17 / 53
First submission: 2014-06-20 12:38:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/959d3ff72d416c2130cfa38e036909c7eb3154f3fcd57bce9b9f1e0522999c07/analysis/
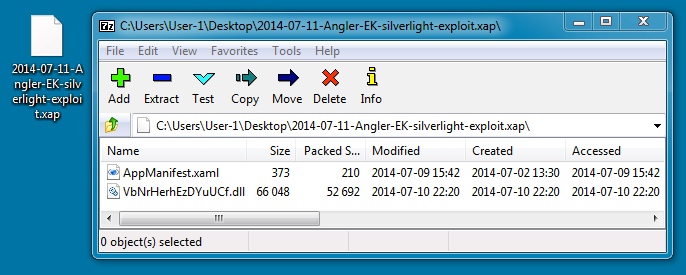
SILVERLIGHT EXPLOIT:
File name: 2014-07-11-Angler-EK-silverlight-exploit.xap
File size: 53,220 bytes
MD5 hash: 70ac580aab2d6e93a0cef61e16fcdbaa
Detection ratio: 0 / 53
First submission: 2014-07-12 00:24:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/196f88d93e4fe11d19467b5d947da82ea1505637da3b5498d82942519f4e4112/analysis/
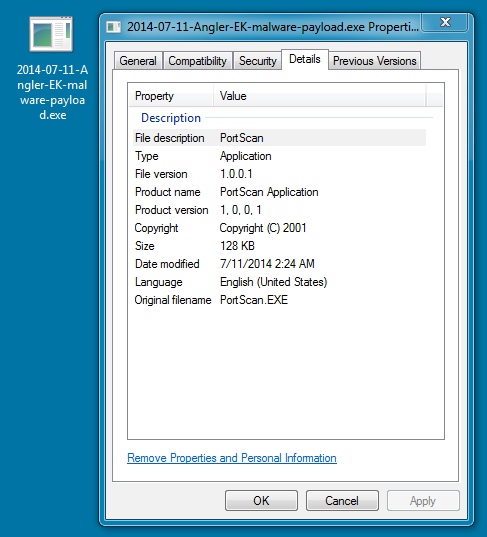
MALWARE PAYLOAD:
File name: 2014-07-11-Angler-EK-malware-payload.exe
File size: 131,072 bytes
MD5 hash: 0e886370029b1b54ef2f66244852ac96
Detection ratio: 2 / 51
First submission: 2014-07-11 03:01:47 UTC
VirusTotal link: https://www.virustotal.com/en/file/1c7f8bde68f7f24d2bdfce0a88ea1dd52aafff150776b51292a3e009a44cd8cb/analysis/
SNORT EVENTS
Sourcefire VRT ruleset from Snort 2.9.6.0 running on Ubuntu 14.04 LTS:
- 2014-07-11 02:23:51 UTC - 192.154.110[.]237:80 - [1:21037:5] INDICATOR-OBFUSCATION randomized javascript encodings detected
- 2014-07-11 02:23:51 UTC - 192.154.110[.]237:80 - [1:19867:4] INDICATOR-OBFUSCATION randomized javascript encodings detected
- 2014-07-11 02:23:53 UTC - 192.154.110[.]237:80 - [1:31331:1] EXPLOIT-KIT Angler exploit kit encrypted binary download
- 2014-07-11 02:23:55 UTC - 192.154.110[.]237:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download
- 2014-07-11 02:23:55 UTC - 192.154.110[.]237:80 - [1:17276:15] FILE-OTHER Multiple vendor Antivirus magic byte detection evasion attempt
- 2014-07-11 02:23:55 UTC - 192.154.110[.]237:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download
Click here to return to the main page.