2014-07-11 - MALWARE INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
TODAY'S EMAILS
SCREENSHOTS:
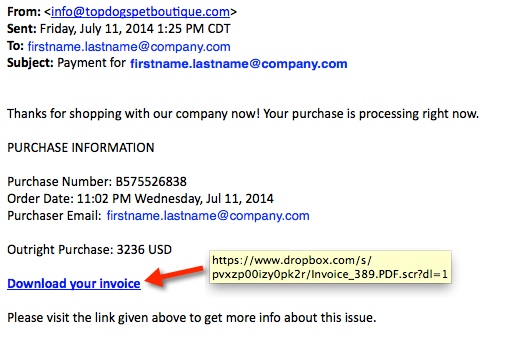
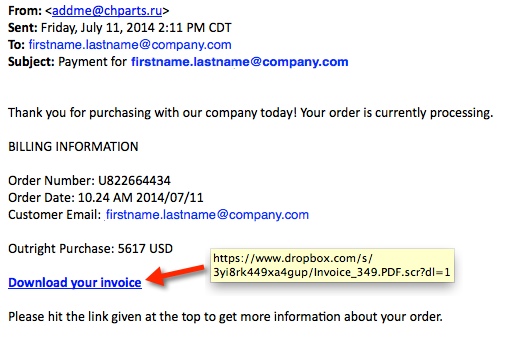
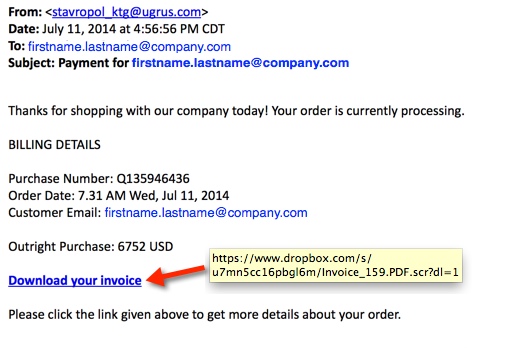
SUBJECT LINE:
Payment for [recipient's email address]
EXAMPLE OF THE MESSAGE TEXT:
Thanks for shopping with our company today! Your order is currently processing.
BILLING DETAILS
Purchase Number: Q135946436
Order Date: 7.31 AM Wed, Jul 11, 2014
Customer Email: [redacted]
Outright Purchase: 6752 USD
Download your invoice
Please click the link given above to get more details about your order.
LINKS FROM THE EMAILS TO THE MALWARE:
- www.dropbox[.]com/s/pvxzp00izy0pk2r/Invoice_389.PDF.scr?dl=1
- www.dropbox[.]com/s/3yi8rk449xa4gup/Invoice_349.PDF.scr?dl=1
- www.dropbox[.]com/s/u7mn5cc16pbgl6m/Invoice_159.PDF.scr?dl=1
NOTE: I aquired a copy of the malware from the first link. By the time I checked the other links, Dropbox had removed the malware.
TRAFFIC FROM SANDBOX ANALYSIS
IP ADDRESSES AND DOMAINS CALLED BY THE MALWARE:
- 49.50.8[.]51 - tikalikainterior[.]com
- 60.191.21[.]141 - tour-cn[.]com
- 78.129.153[.]11 - no domain, used port 8080
- 82.194.88[.]23 - manuelhuertasabogados[.]com
- 88.198.99[.]60 - hondazoomer[.]com
- 109.228.1[.]86 - www.energizerecruitment[.]co[.]uk
- 149.3.144[.]37 - zadropress[.]it
- 149.62.168[.]234 - piscinasalhaurin[.]es
- 173.201.216[.]13 - peterreh[.]com
- 193.227.16[.]94 - www.ies.alexu[.]edu[.]eg
- 199.204.44[.]252 - messina-and-messina[.]com
HTTP TRAFFIC FROM THE PCAP:
NOTE: [!] shows where more malware was returned.
- 21:54:16 UTC - 78.129.153[.]11:8080 - 78.129.153[.]11:8080 - POST /warez/cloacla.php
- 21:54:20 UTC - 149.62.168[.]234:80 - piscinasalhaurin[.]es - GET /modules/mod_modules/res.exe [!]
- 21:54:24 UTC - 78.129.153[.]11:8080 - 78.129.153[.]11:8080 - POST /warez/cloacla.php
- 21:54:25 UTC - 199.204.44[.]252:80 - messina-and-messina[.]com - GET /modules/mod_modules/p.exe [!]
- 21:54:29 UTC - 78.129.153[.]11:8080 - 78.129.153[.]11:8080 - POST /warez/cloacla.php
- 21:55:06 UTC - 88.198.99[.]60:80 - hondazoomer[.]com - POST /testosteron/gate.php
- 21:55:08 UTC - 82.194.88[.]23:80 - manuelhuertasabogados[.]com - GET /administrator/svp.exe
- 21:55:09 UTC - 199.204.44[.]252:80 - messina-and-messina[.]com - GET /administrator/svp.exe
- 21:55:10 UTC - 149.62.168[.]234:80 - piscinasalhaurin[.]es - GET /_virus2/svp.exe
- 21:55:10 UTC - 109.228.1[.]86:80 - www.energizerecruitment[.]co[.]uk - GET /cv/svp.exe
- 21:55:11 UTC - 173.201.216[.]13:80 - peterreh[.]com - GET /wp-admin/svp.exe
- 21:55:13 UTC - 193.227.16[.]94:80 - www.ies.alexu[.]edu[.]eg - GET /administrator/svp.exe
- 21:55:14 UTC - 60.191.21[.]141:80 - tour-cn[.]com - GET /bbs/uc_server/svp.exe
- 21:55:15 UTC - 149.3.144[.]37:80 - zadropress[.]it - GET /administrator/svp.exe
- 21:55:16 UTC - 49.50.8[.]51:80 - tikalikainterior[.]com - GET /about/svp.exe
- 21:55:17 UTC - 49.50.8[.]51:80 - tikalikainterior[.]com - GET /about/svp.exe/
- 21:55:34 UTC - 88.198.99[.]60:80 - hondazoomer[.]com - POST /testosteron/gate.php
PRELIMINARY MALWARE ANALYSIS
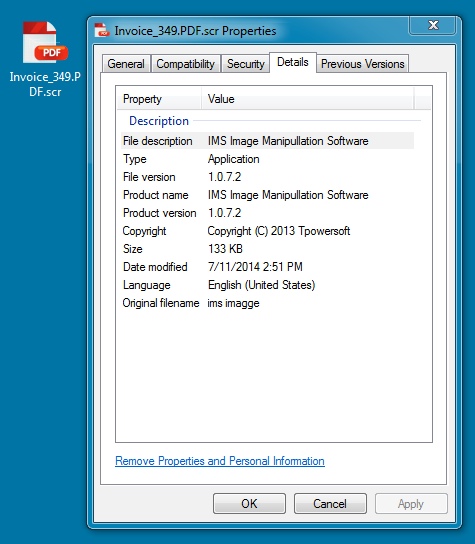
MALWARE FROM PHISHING EMAIL LINK:
File name: Invoice_349.PDF.scr
File size: 137,042 bytes
MD5 hash: a2929c03164efd23e7007b05a3de8da4
Detection ratio: 1 / 54
First submission: 2014-07-11 21:46:43 UTC
VirusTotal link: https://www.virustotal.com/en/file/28e8e70a068e49062b7eb028cf97b18eece72573ca7ae644995f3f692cfa7cc5/analysis/
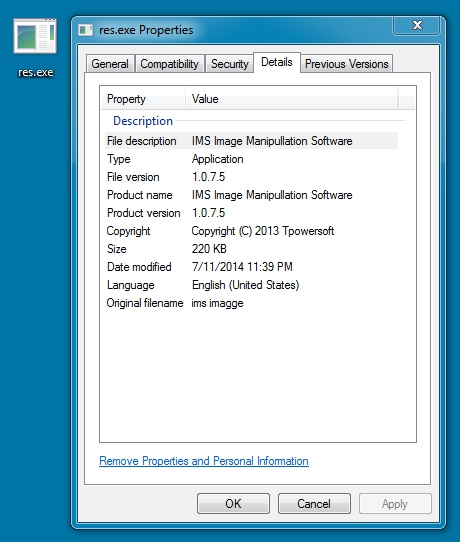
FOLLOW-UP MALWARE 1 OF 2:
File name: res.exe
File size: 225,792 bytes
MD5 hash: 0c55c1a7e7c14c239b7535039a922150
Detection ratio: 2 / 54
First submission: 2014-07-11 23:41:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/a1e9af4632ff0eb5b3eb21285f5909ad8e28c326d71489707e7ea2f76e28e34b/analysis/
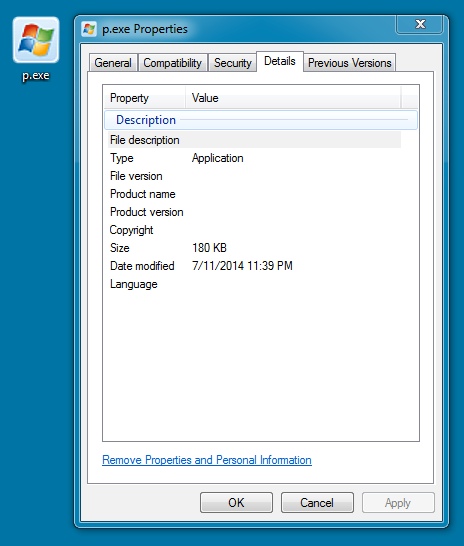
FOLLOW-UP MALWARE 2 OF 2:
File name: p.exe
File size: 184,320 bytes
MD5 hash: c24ead56a5532bfc8840d9b602aebbe2
Detection ratio: 2 / 54
First submission: 2014-07-11 21:23:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/e7e70c62c8741f9394edf394554d46a2fc41ca8fb51a6a5141f042eaf50cb956/analysis/
ALERTS
Sourcefire VRT ruleset from Snort 2.9.6.0 running on Ubuntu 14.04 LTS:
- 2014-07-11 21:54:20 UTC - 8.8.4[.]4:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority
- 2014-07-11 21:54:20 UTC - 149.62.168[.]234:80 - 172.16.165.133:1033 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-07-11 21:54:20 UTC - 149.62.168[.]234:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-11 21:54:26 UTC - 199.204.44[.]252:80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP
- 2014-07-11 21:54:25 UTC - 199.204.44[.]252:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-11 21:54:26 UTC - 199.204.44[.]252:80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP
- 2014-07-11 21:54:26 UTC - 199.204.44[.]252:80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP
- 2014-07-11 21:54:26 UTC - 199.204.44[.]252:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-07-11 21:55:06 UTC - 88.198.99[.]60:80 - [1:27919:3] MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration
- 2014-07-11 21:55:08 UTC - 82.194.88[.]23:80 - [1:27918:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection
- 2014-07-11 21:55:09 UTC - 199.204.44[.]252:80 - [1:27918:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection
- 2014-07-11 21:55:10 UTC - [local host]:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority
- 2014-07-11 21:55:10 UTC - 149.62.168[.]234:80 - [1:27918:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection
- 2014-07-11 21:55:10 UTC - 109.228.1[.]86:80 - [1:27918:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection
- 2014-07-11 21:55:11 UTC - 173.201.216[.]13:80 - [1:27918:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection
- 2014-07-11 21:55:13 UTC - 193.227.16[.]94:80 - [1:27918:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection
- 2014-07-11 21:55:14 UTC - 60.191.21[.]141:80 - [1:27918:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection
- 2014-07-11 21:55:15 UTC - 149.3.144[.]37:80 - [1:27918:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection
- 2014-07-11 21:55:16 UTC - 49.50.8[.]51:80 - [1:27918:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection
- 2014-07-11 21:55:34 UTC - 88.198.99[.]60:80 - [1:27919:3] MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration
Click here to return to the main page.