2014-07-14 - RIG EK FROM 46.182.27[.]166 - ABSTRACKT.THOMASARTA[.]COM - ALSO FROM 178.132.203[.]218 - GRIZZL.THEWELL-BEINGCOMPANY[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- The first attempt sent Flash and Silverlight exploits, along with a malware payload.
- The second attempt sent a Java exploit, but I didn't get malware payload that time.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 46.182.27[.]166 - abstrakt.thomasarta[.]com - Rig EK (first attempt)
- 178.132.203[.]218 - grizzl.thewell-beingcompany[.]com - Rig EK (second attempt)
RIG EK - FIRST ATTEMPT WITH FLASH AND SILVERLIGHT EXPLOITS:
- 14:09:01 UTC - 46.182.27[.]166:80 - abstrakt.thomasarta[.]com - GET /?PHPSSESID=njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6
JVg|ZjhkZGIyNGM3ZjllMGNkZGY4ZTJjMjdkZmJlNzY3OWM - 14:09:08 UTC - 46.182.27[.]166:80 - abstrakt.thomasarta[.]com - GET /index.php?req=swf&num=6026&PHPSSESID=njrMNruDMh7HApzB
Kv7cTKZNKU7YHVnYmMzMhe6JVg|ZjhkZGIyNGM3ZjllMGNkZGY4ZTJjMjdkZmJlNzY3OWM - 14:09:08 UTC - 46.182.27[.]166:80 - abstrakt.thomasarta[.]com - GET /index.php?req=xap&PHPSSESID=njrMNruDMh7HApzBKv7cTKZNK
U7YHVnYmMzMhe6JVg|ZjhkZGIyNGM3ZjllMGNkZGY4ZTJjMjdkZmJlNzY3OWM - 14:09:19 UTC - 46.182.27[.]166:80 - abstrakt.thomasarta[.]com - GET /index.php?req=mp3&num=97896410&PHPSSESID=njrMNruDMh7H
ApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CZjhkZGIyNGM3ZjllMGNkZGY4ZTJjMjdkZmJlNzY3OWM&dop=0884
RIG EK - SECOND ATTEMPT WITH JAVA EXPLOIT:
- 23:56:38 UTC - 178.132.203[.]218:80 - grizzl.thewell-beingcompany[.]com - GET /?PHPSSESID=njrMNruDMh7HApzBKv7cTKZNKU7YHVn
YmMzMhe6JVg|MDlhOTU0MDhmNDYxYmNlY2Q3OTRhZmFhMThmOWJkMTQ - 23:57:06 UTC - 178.132.203[.]218:80 - grizzl.thewell-beingcompany[.]com - GET /index.php?req=xml&num=8323&PHPSSESID=njrMNruD
Mh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|MDlhOTU0MDhmNDYxYmNlY2Q3OTRhZmFhMThmOWJkMTQ - 23:57:08 UTC - 178.132.203[.]218:80 - grizzl.thewell-beingcompany[.]com - GET /index.php?req=jar&num=7399&PHPSSESID=njrMNruD
Mh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CMDlhOTU0MDhmNDYxYmNlY2Q3OTRhZmFhMThmOWJkMTQ - 23:57:14 UTC - 178.132.203[.]218:80 - grizzl.thewell-beingcompany[.]com - GET /META-INF/services/javax.xml.datatype.DatatypeFactory
- 23:57:24 UTC - 178.132.203[.]218:80 - grizzl.thewell-beingcompany[.]com - GET /index.php?req=mp3&num=441832&PHPSSESID=njrMN
ruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CMDlhOTU0MDhmNDYxYmNlY2Q3OTRhZmFhMThmOWJkMTQ
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-07-14-Rig-EK-flash-exploit.swf
File size: 4,153 bytes
MD5 hash: b0e9d5ac051d1606652e74e2c66bed22
Detection ratio: 0 / 53
First submission: 2014-07-09 07:46:29 UTC
VirusTotal link: https://www.virustotal.com/en/file/d4fce22526e1aec3f04400179b3bb4267c4f8c1818dd621fa250a39a03420024/analysis/
JAVA EXPLOIT
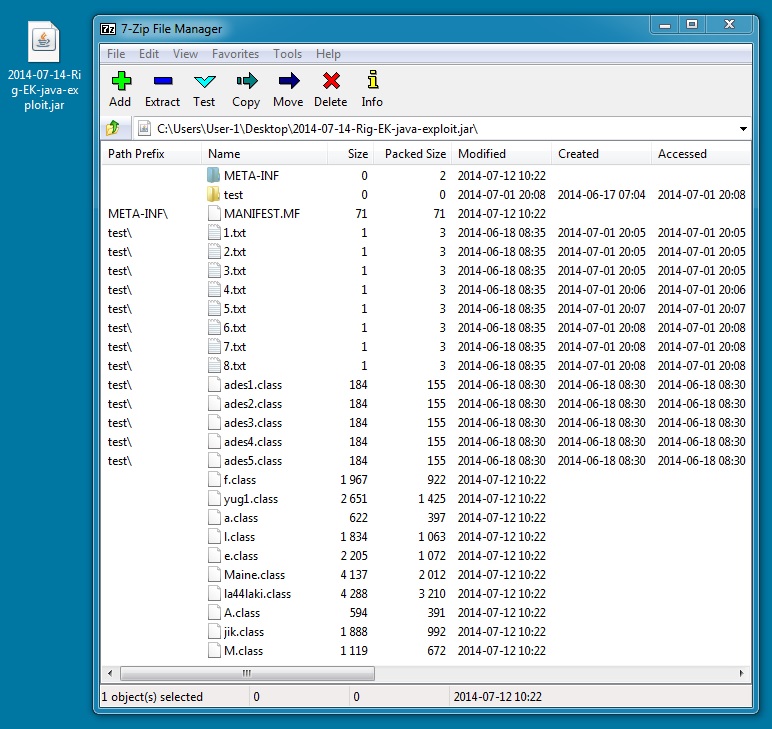
File name: 2014-07-14-Rig-EK-java-exploit.jar
File size: 16,161 bytes
MD5 hash: 83798d39dde98babb3b07e243f7aa1c5
Detection ratio: 3 / 54
First submission: 2014-07-15 01:34:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/6391eb18d40344a6bd2dce1cfb0f2a5009267d1b16dc27491744e08bc5920bbb/analysis/
SILVERLIGHT EXPLOIT
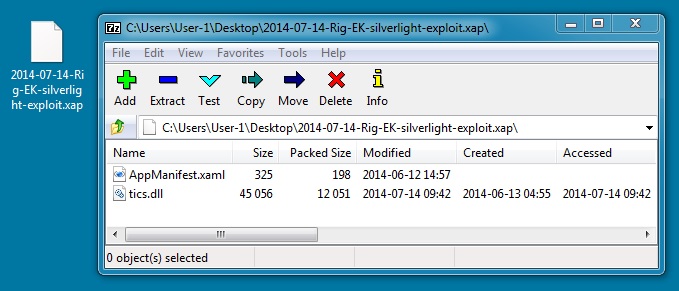
File name: 2014-07-14-Rig-EK-silverlight-exploit.xap
File size: 12,507 bytes
MD5 hash: af634212316b3908fee5c3ff1029a678
Detection ratio: 4 / 53
First submission: 2014-07-14 14:44:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/8f6581fabe61ec3e8fefab4a9c9a9da6d99db518791ae8e48b80dfa0912fec68/analysis/
MALWARE PAYLOAD
File name: 2014-07-14-Rig-EK-malware-payload.exe
File size: 745,472 bytes
MD5 hash: 01f4b1d9b2aafb86d5ccfa00e277fb9d
Detection ratio: 5 / 54
First submission: 2014-07-15 01:35:20 UTC
VirusTotal link: https://www.virustotal.com/en/file/29f932227fc489ffb0cec82a02869a6c96a568b7fb94f35e3eb4393cdd37efe0/analysis/
ALERTS FROM FIRST PCAP (FLASH AND SILVERLIGHT EXPLOITS)

Emerging Threats and ETPRO rulesets from Sguil on Security Onion:
- 2014-07-14 14:09:08 UTC - 46.182.27[.]166:80 - ET POLICY Outdated Windows Flash Version IE (sid:2014726)
- 2014-07-14 14:09:08 UTC - 46.182.27[.]166:80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2104 (sid:2018441)
- 2014-07-14 14:09:09 UTC - 46.182.27[.]166:80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2104 (sid:2018441)
- 2014-07-14 14:09:24 UTC - 46.182.27[.]166:80 - ET CURRENT_EVENTS Goon EK encrypted binary (3) (sid:2018297)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-07-14 14:09:08 UTC - 46.182.27[.]166:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 2014-07-14 14:09:08 UTC - 46.182.27[.]166:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 2014-07-14 14:09:09 UTC - 46.182.27[.]166:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download
- 2014-07-14 14:09:19 UTC - 46.182.27[.]166:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 2014-07-14 14:09:24 UTC - 46.182.27[.]166:80 - [1:30934:2] EXPLOIT-KIT Goon/Infinity/Rig exploit kit encrypted binary download
ALERTS FROM SECOND PCAP (JAVA EXPLOIT)
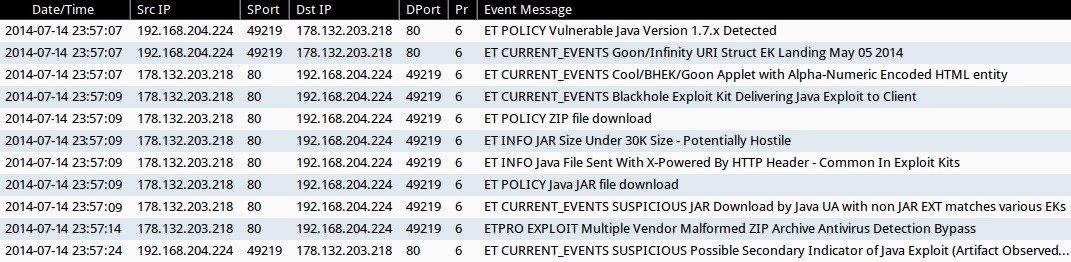
Emerging Threats and ETPRO rulesets from Sguil on Security Onion:
- 2014-07-14 23:57:07 UTC - 178.132.203[.]218:80 - ET POLICY Vulnerable Java Version 1.7.x Detected (sid:2014297)
- 2014-07-14 23:57:07 UTC - 178.132.203[.]218:80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (sid:2018441)
- 2014-07-14 23:57:07 UTC - 178.132.203[.]218:80 - ET CURRENT_EVENTS Cool/BHEK/Goon Applet with Alpha-Numeric Encoded HTML entity (sid:2017064)
- 2014-07-14 23:57:09 UTC - 178.132.203[.]218:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Java Exploit to Client (sid:2013961)
- 2014-07-14 23:57:09 UTC - 178.132.203[.]218:80 - ET POLICY ZIP file download (sid:2000428)
- 2014-07-14 23:57:09 UTC - 178.132.203[.]218:80 - ET INFO JAR Size Under 30K Size - Potentially Hostile (sid:2017639)
- 2014-07-14 23:57:09 UTC - 178.132.203[.]218:80 - ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits (sid:2017637)
- 2014-07-14 23:57:09 UTC - 178.132.203[.]218:80 - ET POLICY Java JAR file download (sid:2011854)
- 2014-07-14 23:57:09 UTC - 178.132.203[.]218:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs (sid:2016540)
- 2014-07-14 23:57:14 UTC - 178.132.203[.]218:80 - ETPRO EXPLOIT Multiple Vendor Malformed ZIP Archive Antivirus Detection Bypass (sid:2800029)
- 2014-07-14 23:57:24 UTC - 178.132.203[.]218:80 - ET CURRENT_EVENTS SUSPICIOUS Possible Secondary Indicator of Java Exploit (Artifact Observed mostly in EKs/a few mis-configured apps) (sid:2017579)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-07-14 23:57:06 UTC - 178.132.203[.]218:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 2014-07-14 23:57:08 UTC - 178.132.203[.]218:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 2014-07-14 23:57:10 UTC - 178.132.203[.]218:80 - [1:25562:4] FILE-JAVA Oracle Java obfuscated jar file download attempt
- 2014-07-14 23:57:10 UTC - 178.132.203[.]218:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt
- 2014-07-14 23:57:24 UTC - 178.132.203[.]218:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
Click here to return to the main page.