2014-07-19 - NUCLEAR EK FROM 79.133.219[.]121 - 141320960-6.EASYPOTENT[.]CO[.]VU
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- I ran the malware payload through the Malwr sandbox analysis twice, because I couldn't extract the follow-up Rerdom malware from the first pcap.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 79.133.219[.]121 - 141320960-6.easypotent[.]co[.]vu and c659714ddr8i.easypotent[.]co[.]vu - Nuclear EK
- Various IP addresses - various domains - Post-infection traffic (see below)
NUCLEAR EK:
- 2014-07-19 00:02:27 UTC - 79.133.219[.]121:80 - c659714ddr8i.easypotent[.]co[.]vu - GET /
- 2014-07-19 00:02:31 UTC - 79.133.219[.]121:80 - 141320960-6.easypotent[.]co[.]vu - GET /1405706160.swf
- 2014-07-19 00:02:38 UTC - 79.133.219[.]121:80 - 141320960-6.easypotent[.]co[.]vu - GET /1405706160.jar
- 2014-07-19 00:02:39 UTC - 79.133.219[.]121:80 - 141320960-6.easypotent[.]co[.]vu - GET /f/1405706160/2
- 2014-07-19 00:02:40 UTC - 79.133.219[.]121:80 - 141320960-6.easypotent[.]co[.]vu - GET /f/1405706160/2/2
POST-INFECTION TRAFFIC FROM THE VM:
- 2014-07-19 00:02:41 UTC - 178.150.136[.]252:80 - enjoy-hot[.]com - GET /b/shoe/75412
- 2014-07-19 00:02:42 UTC - 178.150.136[.]252:80 - enjoy-hot[.]com - GET /b/shoe/75412
- 2014-07-19 00:02:50 UTC - 178.150.136[.]252:80 - enjoy-hot[.]com - GET /b/shoe/75412
- 2014-07-19 00:02:51 UTC - 178.150.136[.]252:80 - enjoy-hot[.]com - GET /b/shoe/75412
- 2014-07-19 00:02:58 UTC - 178.150.136[.]252:80 - enjoy-hot[.]com - GET /b/shoe/75412
- 2014-07-19 00:03:04 UTC - 178.150.136[.]252:80 - enjoy-hot[.]com - GET /b/shoe/75412
- 2014-07-19 00:04:13 UTC - 178.150.136[.]252:80 - enjoy-hot[.]com - GET /b/shoe/75412
- 2014-07-19 00:04:15 UTC - 178.150.136[.]252:80 - enjoy-hot[.]com - GET /b/shoe/75412
- 2014-07-19 00:04:22 UTC - 178.150.136[.]252:80 - enjoy-hot[.]com - GET /b/shoe/75412
- 2014-07-19 00:04:42 UTC - 178.150.136[.]252:80 - enjoy-hot[.]com - GET /b/shoe/75412
- 2014-07-19 00:04:43 UTC - 188.190.5[.]162:80 - star-ffee[.]com - GET /mod_articles-qa/jquery/
- 2014-07-19 00:04:58 UTC - 188.190.5[.]162:80 - star-ffee[.]com - GET /mod_articles-qa/jquery/
- 2014-07-19 00:05:03 UTC - 188.190.5[.]162:80 - star-ffee[.]com - GET /mod_articles-qa/jquery/
POST-INFECTION TRAFFIC FROM SANDBOX ANALYSIS:
- 00:45:33 UTC - 46.172.192[.]38:80 - enjoy-hot[.]com - GET /b/shoe/75412
- 00:45:34 UTC - 46.172.192[.]38:80 - enjoy-hot[.]com - GET /b/shoe/75412
- 00:45:35 UTC - 134.249.3[.]254:80 - star-ffee[.]com - GET /mod_articles-qa/jquery/
- 00:46:09 UTC - 109.254.81[.]175:80 - star-ffee[.]com - GET /mod_jshopping-php/soft32.dll
- 00:46:15 UTC - 178.236.143[.]163:80 - vision-vaper[.]su - GET /b/eve/43a7e6ea4896b91f3c6e439c
- 00:47:13 UTC - 178.236.143[.]163:80 - vision-vaper[.]su - POST /b/opt/CD2EF2264695AD334DA4F2C6
- 00:47:13 UTC - 178.236.143[.]163:80 - vision-vaper[.]su - GET /b/letr/1138EB488BC5A39780F4FC62
- 00:47:15 UTC - 65.254.49[.]118:8080 - 65.254.49[.]118:8080 - POST /b/opt/44203100FBB2BE7AF083E18F
- 00:47:32 UTC - 65.254.49[.]118:8080 - 65.254.49[.]118:8080 - POST /b/req/E5E308C3893C898C820DD679
- 00:47:53 UTC - 65.254.49[.]118:8080 - 65.254.49[.]118:8080 - POST /b/req/D1F2146112BF5CD3198E0326
- 00:47:14 UTC - 50.57.228[.]220:443 - POST /b/opt/F2BEA10A7635E6DA7D04B92F
- 00:47:14 UTC - 50.57.228[.]220:443 - GET /b/letr/F0399A3C51DDC6665AEC9993
- 00:48:14 UTC - 65.254.49[.]118:8080 - 65.254.49[.]118:8080 - POST /b/opt/384EA98A1A43CABD11729548
- 00:47:55 UTC - 192.162.19.34:80 - lereve-search[.]com - GET /
- 00:47:56 UTC - 192.162.19.34:80 - resorts-search[.]com - GET /
- followed by other fake search engine click-faud traffic (see 2014-07-19-Nuclear-EK-malware-payload-sandbox-analysis-01.pcap for details)
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-07-19-Nuclear-EK-flash-exploit.swf
File size: 5,897 bytes
MD5 hash: 765f1c63fb0747125e8391392c0e078e
Detection ratio: 4 / 53
First submission: 2014-07-19 00:44:55 UTC
VirusTotal link: https://www.virustotal.com/en/file/0c7ea628113061150d1277afce771ace591c57f7721e11f78a8c606cf6cbbe94/analysis/
JAVA EXPLOIT:
File name: 2014-07-19-Nuclear-EK-java-exploit.jar
File size: 11,367 bytes
MD5 hash: b21c14530f4ac483258642d29baa806f
Detection ratio: 1 / 53
First submission: 2014-07-18 20:06:39 UTC
VirusTotal link: https://www.virustotal.com/en/file/d6d69158e1bebf5fd202ea40c2d70dea6a0c033843df04d9d04d417d62769504/analysis/
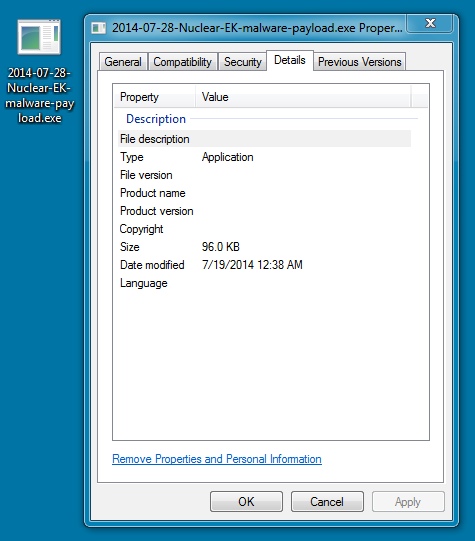
MALWARE PAYLOAD:
File name: 2014-07-19-Nuclear-EK-malware-payload.exe
File size: 98,312 bytes
MD5 hash: 3cbc20e8ce4b4fb47da3cc1c963d41b3
Detection ratio: 1 / 52
First submission: 2014-07-19 00:43:53 UTC
VirusTotal link: https://www.virustotal.com/en/file/957a25e2023721a17fa86d8db8f6985f2817e48bb3fb0dd8efb052c40424aa9a/analysis/
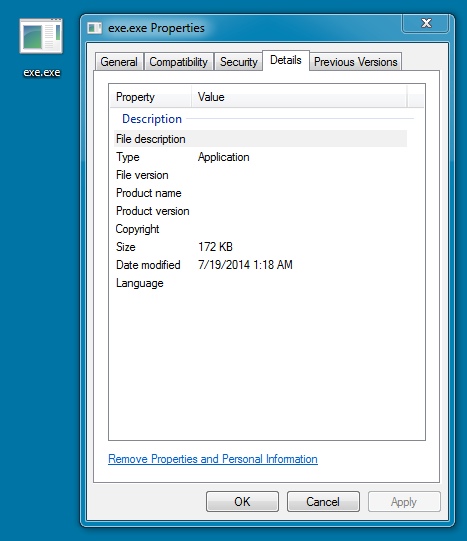
FOLLOW-UP MALWARE FROM SANDBOX ANALYSIS:
File name: exe.exe
File size: 176,128 bytes
MD5 hash: 72353b5bd718a4abd964b2612e3dd01d
Detection ratio: 2 / 53
First submission: 2014-07-19 01:28:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/e5ad7bec18337e46f45cb67a62f853b5bc31af86ef950c0715d476a9cd7489e4/analysis/
NOTE: This is Rerdom, normally saved to the infected computer as UpdateFlashPlayer_[something].exe in the user's AppData\Local\Temp directory.
ALERTS FROM THE VM INFECTION TRAFFIC
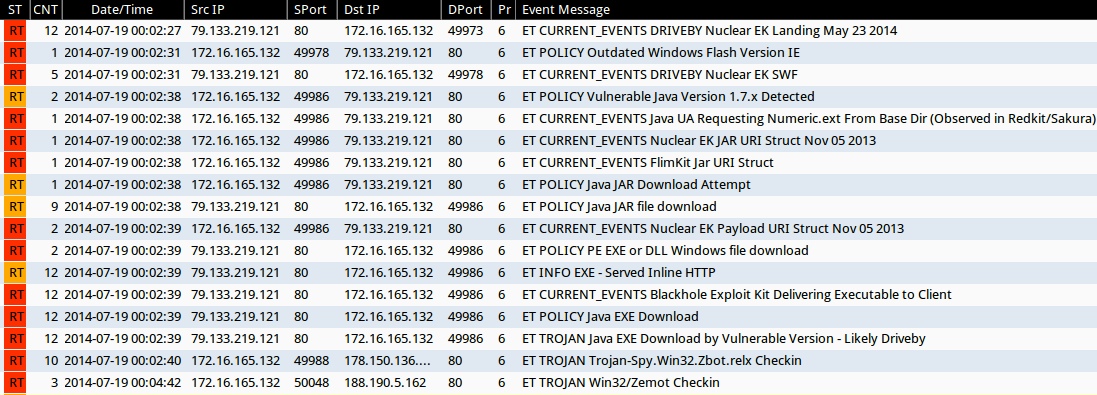
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not counting ET INFO or ET POLICY signatures):
- 2014-07-19 00:02:27 UTC - 79.133.219[.]121:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing May 23 2014 (sid:2018595)
- 2014-07-19 00:02:31 UTC - 79.133.219[.]121:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2018362)
- 2014-07-19 00:02:38 UTC - 79.133.219[.]121:80 - ET CURRENT_EVENTS Java UA Requesting Numeric.ext From Base Dir (Observed in Redkit/Sakura) (sid:2017199)
- 2014-07-19 00:02:38 UTC - 79.133.219[.]121:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013 (sid:2017666)
- 2014-07-19 00:02:38 UTC - 79.133.219[.]121:80 - ET CURRENT_EVENTS FlimKit Jar URI Struct (sid:2017152)
- 2014-07-19 00:02:39 UTC - 79.133.219[.]121:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 2014-07-19 00:02:39 UTC - 79.133.219[.]121:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:2013962)
- 2014-07-19 00:02:39 UTC - 79.133.219[.]121:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby (sid:2013036)
- 2014-07-19 00:02:40 UTC - 178.150.136[.]252:80 - ET TROJAN Trojan-Spy.Win32.Zbot.relx Checkin (sid:2018643)
- 2014-07-19 00:04:42 UTC - 188.190.5[.]162:80 - ET TROJAN Win32/Zemot Checkin (sid:2018644)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-07-19 00:02:31 UTC - 79.133.219[.]121:80 - [1:31237:1] EXPLOIT-KIT Nuclear exploit kit outbound swf request
- 2014-07-19 00:02:38 UTC - 79.133.219[.]121:80 - [1:30219:2] EXPLOIT-KIT Nuclear exploit kit outbound jar request
- 2014-07-19 00:02:38 UTC - 79.133.219[.]121:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt
- 2014-07-19 00:02:39 UTC - 79.133.219[.]121:80 - [1:30220:2] EXPLOIT-KIT Nuclear exploit kit outbound payload request
- 2014-07-19 00:02:39 UTC - 79.133.219[.]121:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-07-19 00:02:39 UTC - 79.133.219[.]121:80 - [1:25042:3] EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit
- 2014-07-19 00:02:39 UTC - 79.133.219[.]121:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 2014-07-19 00:02:39 UTC - 79.133.219[.]121:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
- 2014-07-19 00:02:39 UTC - 79.133.219[.]121:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-19 00:02:40 UTC - 79.133.219[.]121:80 - [1:30220:2] EXPLOIT-KIT Nuclear exploit kit outbound payload request
- 2014-07-19 00:02:40 UTC - 79.133.219[.]121:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
Click here to return to the main page.