2014-07-20 - FIESTA EK FROM 62.212.73[.]198 - WGXJVD.MYFTP[.]BIZ
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
INFECTION TRAFFIC
FIESTA EK:
- 01:45:12 UTC - 62.212.73[.]198 - wgxjvd.myftp[.]biz - GET /wjrywszhceyf5pfckpy4wzaeilo7hf
- 01:45:14 UTC - 62.212.73[.]198 - wgxjvd.myftp[.]biz - GET /q4vprom/35f47e35b6d20d044042000f035e040102015e0f0307030e060605560600570c;112202;228
- 01:45:14 UTC - 62.212.73[.]198 - wgxjvd.myftp[.]biz - GET /q4vprom/2133d247b97838ad5b545f085009030303050b085050040c070250515557500e
- 01:45:22 UTC - 62.212.73[.]198 - wgxjvd.myftp[.]biz - GET /q4vprom/74e5c5c7680bbb124458130e570e540306005d0e5757530c020706575250070e;4060129
- 01:45:23 UTC - 62.212.73[.]198 - wgxjvd.myftp[.]biz - GET /q4vprom/6861cbbdc67483bd55485d0a57595550070c0e0a5700525f030b555352070607;4
- 01:45:25 UTC - 62.212.73[.]198 - wgxjvd.myftp[.]biz - GET /q4vprom/6861cbbdc67483bd55485d0a57595550070c0e0a5700525f030b555352070607;4;1
- 01:45:26 UTC - 62.212.73[.]198 - wgxjvd.myftp[.]biz - GET /q4vprom/3fc9cc924dca3b575016080257580e0602525b02570109090655005b52065d0b;5
- 01:45:28 UTC - 62.212.73[.]198 - wgxjvd.myftp[.]biz - GET /q4vprom/3fc9cc924dca3b575016080257580e0602525b02570109090655005b52065d0b;5;1
- 01:45:29 UTC - 62.212.73[.]198 - wgxjvd.myftp[.]biz - GET /q4vprom/7d764a96ee74cb315616560d005a0e0206500f0d0003090d0257545405045d0f
- 01:45:29 UTC - 62.212.73[.]198 - wgxjvd.myftp[.]biz - GET /q4vprom/50257eb84dca3b575640590e035e550c04040a0e030752030003515706000601;6
- 01:45:31 UTC - 62.212.73[.]198 - wgxjvd.myftp[.]biz - GET /q4vprom/50257eb84dca3b575640590e035e550c04040a0e030752030003515706000601;6;1
- 01:45:32 UTC - 62.212.73[.]198 - wgxjvd.myftp[.]biz - GET /q4vprom/6e40eaf986c104f1551d510b515a510d07510c0b510356020356575254040200;1;2
- 01:45:34 UTC - 62.212.73[.]198 - wgxjvd.myftp[.]biz - GET /q4vprom/6e40eaf986c104f1551d510b515a510d07510c0b510356020356575254040200;1;2;1
POST INFECTION TRAFFIC ON THE VM:
- 01:45:25 UTC - 78.27.159[.]112 - enjoy-hot[.]com - GET /b/shoe/54608
Above line repeats several times with different source ports - 01:46:03 UTC - 91.209.64[.]134 - star-ffee[.]com - GET /mod_articles-qa9843/jquery/
Above line repeats several times with different source ports
SANDBOX ANALYSIS TRAFFIC GENERATED BY THE MALWARE PAYLOAD:
- 02:08:02 UTC - 81.22.142[.]183:80 - enjoy-hot[.]com - GET /b/shoe/54608
- 02:08:03 UTC - 81.22.142[.]183:80 - enjoy-hot[.]com - GET /b/shoe/54608
- 02:08:06 UTC - 217.12.122[.]58:80 - star-ffee[.]com - GET /mod_articles-qa9843/jquery/
- 02:08:56 UTC - 142.197.52[.]24:80 - star-ffee[.]com - GET /mod_jshopping-php6574/soft32.dll
- 02:09:17 UTC - 37.229.143[.]37:80 - vision-vaper[.]su - GET /b/eve/c3082889c839777ca71a35bb
- 02:10:14 UTC - 37.229.143[.]37:80 - vision-vaper[.]su - POST /b/opt/51F4EFE2E469F6EAEF58A91F
- 02:10:15 UTC - 37.229.143[.]37:80 - vision-vaper[.]su - GET /b/letr/9677BCC2573A70675C0B2F92
- 02:10:15 UTC - 63.247.95[.]50:8080 - 63.247.95[.]50:8080 - POST /b/opt/F3EB66FCAAE15CD5A1D00320
- 02:10:16 UTC - 63.247.95[.]50:8080 - 63.247.95[.]50:8080 - GET /b/letr/CFBA92B2CD028F38C633D0CD
- 02:10:17 UTC - 178.18.18[.]30:443 - POST /b/opt/025CC390419704794AA65B8C
- 02:10:18 UTC - 178.18.18[.]30:443 - POST /b/opt/D4864C15B00F2017BB3E7FE2
- 02:10:35 UTC - 178.18.18[.]30:443 - POST /b/req/8E59C14B6F92439B64A31C6E
- 02:10:56 UTC - 178.18.18[.]30:443 - POST /b/req/C4474BB1B929D1D1B2188E24
- 02:10:59 UTC - 192.162.19[.]34:80 - report-search[.]com - GET /
- 02:10:59 UTC - 192.162.19[.]34:80 - report-search[.]com - GET /style.css
- 02:11:00 UTC - 192.162.19[.]34:80 - forest-search[.]com - GET /
- 02:11:00 UTC - 192.162.19[.]34:80 - report-search[.]com - GET /btn_search.png
- 02:11:00 UTC - 192.162.19[.]34:80 - forest-search[.]com - GET /style.css
- 02:11:00 UTC - 192.162.19[.]34:80 - report-search[.]com - GET /logo.png
- 02:11:00 UTC - 192.162.19[.]34:80 - report-search[.]com - GET /icon_serch.png
- 02:11:00 UTC - 192.162.19[.]34:80 - forest-search[.]com - GET /btn_search.png
- 02:11:00 UTC - 192.162.19[.]34:80 - forest-search[.]com - GET /icon_serch.png
- 02:11:00 UTC - 192.162.19[.]34:80 - forest-search[.]com - GET /logo.png
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-07-20-Fiesta-EK-flash-exploit.swf
File size: 10,150 bytes
MD5 hash: cfb54a37495bb73b8bf7022d5700d0bf
Detection ratio: 0 / 53
First submission: 2014-07-20 02:40:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/a77793947db764072f734b2e2168f45e14adffb99b72c9d2c92f9822d7f34159/analysis/
JAVA EXPLOIT:
File name: 2014-07-20-Fiesta-EK-java-exploit.jar
File size: 4,914 bytes
MD5 hash: 1cd0537fbde21b9a53559f4efd4274f1
Detection ratio: 3 / 52
First submission: 2014-07-17 14:46:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/8911369a40910c004261a63532d6e2dfed91c8a8772124039ee88217f818d18c/analysis/
SILVERLIGHT EXPLOIT:
File name: 2014-07-20-Fiesta-EK-silverlight-exploit.xap
File size: 11,777 bytes
MD5 hash: 648cc2a876d6028194332af0ac9fcdf6
Detection ratio: 3 / 53
First submission: 2014-07-17 18:43:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/7f0188ee01229741f8703f83b06464a8b97cfd73c047cd21ed090efe617c3f44/analysis/
MALWARE PAYLOAD:
File name: 2014-07-20-Fiesta-EK-malware-payload.exe
File size: 102,408 bytes
MD5 hash: 464c76e11266b8259ae3ac2b4dc8ae7b
Detection ratio: 1 / 53
First submission: 2014-07-20 02:05:20 UTC
VirusTotal link: https://www.virustotal.com/en/file/3c592ffcfe519c5346fc97848c18851cce0b8451f6f48971491c4451416da2bc/analysis/
FOLLOW-UP MALWARE FROM SANDBOX ANALYSIS PCAP:
File name: exe.exe
File size: 176,128 bytes
MD5 hash: 885609e439b2d6dba029a572f36f66ea
Detection ratio: 12 / 53
First submission: 2014-07-19 21:41:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/4eac236d1d0fb9351800f61a0f8713576f393adf6b0b7e876d1cdc9bc534edf0/analysis/
NOTE: This is Rerdom, normally saved to the infected computer as UpdateFlashPlayer_[something].exe in the user's AppData\Local\Temp directory.
ALERTS
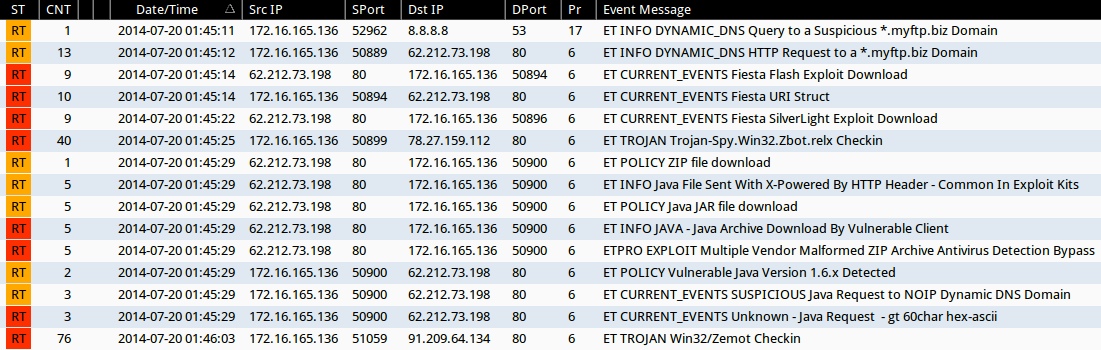
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO and ET POLICY rules):
- 2014-07-20 01:45:14 UTC - 62.212.73[.]198:80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- 2014-07-20 01:45:14 UTC - 62.212.73[.]198:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 2014-07-20 01:45:22 UTC - 62.212.73[.]198:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- 2014-07-20 01:45:25 UTC - 78.27.159[.]112:80 - ET TROJAN Trojan-Spy.Win32.Zbot.relx Checkin (sid:2018643)
- 2014-07-20 01:45:29 UTC - 62.212.73[.]198:80 - ETPRO EXPLOIT Multiple Vendor Malformed ZIP Archive Antivirus Detection Bypass (sid:2800029)
- 2014-07-20 01:45:29 UTC - 62.212.73[.]198:80 - ET CURRENT_EVENTS SUSPICIOUS Java Request to NOIP Dynamic DNS Domain (sid:2016582)
- 2014-07-20 01:45:29 UTC - 62.212.73[.]198:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
- 2014-07-20 01:46:03 UTC - 91.209.64[.]134:80 - ET TROJAN Win32/Zemot Checkin (sid:2018644)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-07-20 01:45:14 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-20 01:45:14 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-20 01:45:22 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-20 01:45:23 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-20 01:45:25 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-20 01:45:26 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-20 01:45:28 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-07-20 01:45:29 UTC - 62.212.73[.]198:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
ALERTS FROM SANDBOX ANALYSIS
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-07-20 02:08:07 UTC - 217.12.122[.]58:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 2014-07-20 02:08:07 UTC - 217.12.122[.]58:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-20 02:09:16 UTC - [local host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-07-20 02:09:17 UTC - 37.229.143[.]37:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-20 02:10:14 UTC - 37.229.143[.]37:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-20 02:10:15 UTC - 37.229.143[.]37:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-20 02:10:15 UTC - 63.247.95[.]50:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-20 02:10:16 UTC - 63.247.95[.]50:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
Click here to return to the main page.