2014-07-25 - RIG EK FROM 194.58.101[.]49 - WELCOME.SHOPSTHATGIVEA[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 194.58.101[.]49 - welcome.shopsthatgivea[.]com - Rig EK
- 188.241.116[.]231 - shared.wdc0[.]com and hosted.wdc01[.]com - Post-infection traffic using HTTPS (port 443)
RIG EK:
- 20:56:00 UTC - 194.58.101[.]49:80 - welcome.shopsthatgivea[.]com - GET /?PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|NzE1OTllYTUyNTM4MTcxYjI0YmZiYzIzMGUxNzk5OGQ - 20:56:08 UTC - 194.58.101[.]49:80 - welcome.shopsthatgivea[.]com - GET /index.php?req=swf&num=2888&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|NzE1OTllYTUyNTM4MTcxYjI0YmZiYzIzMGUxNzk5OGQ - 20:56:08 UTC - 194.58.101[.]49:80 - welcome.shopsthatgivea[.]com - GET /index.php?req=xap&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|NzE1OTllYTUyNTM4MTcxYjI0YmZiYzIzMGUxNzk5OGQ - 20:56:15 UTC - 194.58.101[.]49:80 - welcome.shopsthatgivea[.]com - GET /index.php?req=mp3&num=54285120&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CNzE1OTllYTUyNTM4MTcxYjI0YmZiYzIzMGUxNzk5OGQ&dop=0
POST-INFECTION TRAFFIC:
- 20:58:20 UTC - 188.241.116[.]231:443 - HTTPS traffic to shared.wdc0[.]com
- 20:58:21 UTC - 188.241.116[.]231:443 - HTTPS traffic to shared.wdc0[.]com
- 21:00:25 UTC - 188.241.116[.]231:443 - HTTPS traffic to hosted.wdc01[.]com
- 21:00:26 UTC - 188.241.116[.]231:443 - HTTPS traffic to hosted.wdc01[.]com
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-07-25-Rig-EK-flash-exploit.swf
File size: 4,453 bytes
MD5 hash: 3d7e96bd371bfbac440864dc651a0ddf
Detection ratio: 0 / 53
First submission: 2014-07-25 19:39:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/48272657d2347f7dfca47f8c99822264c1ac7df44a37fbd3b555e40bed99d3dd/analysis/
SILVERLIGHT EXPLOIT:
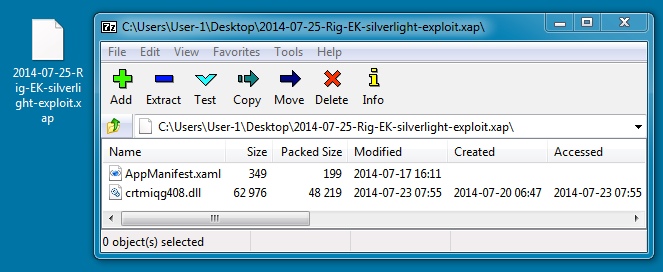
File name: 2014-07-25-Rig-EK-silverlight-exploit.xap
File size: 48,688 bytes
MD5 hash: 1699d8065bb7e9ae66491d6e52cc6981
Detection ratio: 9 / 52
First submission: 2014-07-23 10:46:54 UTC
VirusTotal link: https://www.virustotal.com/en/file/d6928f1c8680059cddb757a3d219717f0ed5ca42ae0cd9f8bbfeaf3602cee5c5/analysis/
MALWARE PAYLOAD:
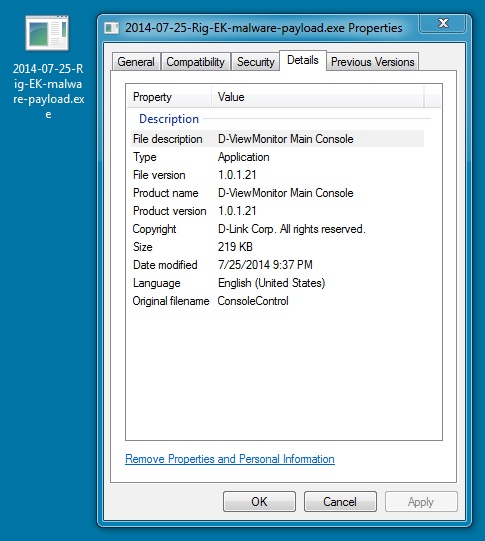
File name: 2014-07-25-Rig-EK-malware-payload.exe
File size: 224,768 bytes
MD5 hash: 7ef60352e4076902e4817115125ab72f
Detection ratio: 2 / 53
First submission: 2014-07-25 18:45:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/78c076664d94fbb6fecfc16e08e5155ffee947a5a8867f1bc2268be9e2c97faf/analysis/
ALERTS
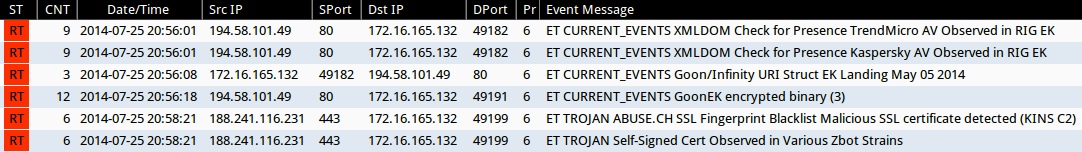
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY events):
- 20:56:01 UTC - 194.58.101[.]49:80 - ET CURRENT_EVENTS XMLDOM Check for Presence TrendMicro AV Observed in RIG EK (sid:2018757)
- 20:56:01 UTC - 194.58.101[.]49:80 - ET CURRENT_EVENTS XMLDOM Check for Presence Kaspersky AV Observed in RIG EK (sid:2018756)
- 20:56:08 UTC - 194.58.101[.]49:80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (sid:2018441)
- 20:56:18 UTC - 194.58.101[.]49:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3) (sid:2018297)
- 20:58:21 UTC - 188.241.116[.]231:443 - ET TROJAN ABUSE.CH SSL Fingerprint Blacklist Malicious SSL certificate detected (KINS C2) (sid:2018725)
- 20:58:21 UTC - 188.241.116[.]231:443 - ET TROJAN Self-Signed Cert Observed in Various Zbot Strains (sid:2018284)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 20:56:08 UTC - 194.58.101[.]49:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 20:56:08 UTC - 194.58.101[.]49:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 20:56:09 UTC - 194.58.101[.]49:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download
- 20:56:09 UTC - 194.58.101[.]49:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download
- 20:56:15 UTC - [local host]:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority
- 20:56:15 UTC - 194.58.101[.]49:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 20:56:18 UTC - 194.58.101[.]49:80 - [1:30934:2] EXPLOIT-KIT Goon/Infinity/Rig exploit kit encrypted binary download
- 20:58:20 UTC - [local host]:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority
- 21:00:25 UTC - [local host]:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority
Click here to return to the main page.