2014-07-28 - ANGLER EK FROM 66.96.246[.]143 - 02S.YLUKODORSAIEAQL[.]ORG
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Typical traffic for Angler EK.
- The Windows 7 sandbox analysis of the malware payload didn't reveal much.
- The Windows XP sandbox analysis triggered alerts for a Trojan.Win32.Qadars variant, and a bitcoin miner was installed on the sandbox VM.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 66.96.246[.]143 - 02s.ylukodorsaieaql[.]org - Angler EK
- 24.122.103[.]218 - beckcomelith[.]biz - Callback traffic by Trojan.Win32.Qadars variant
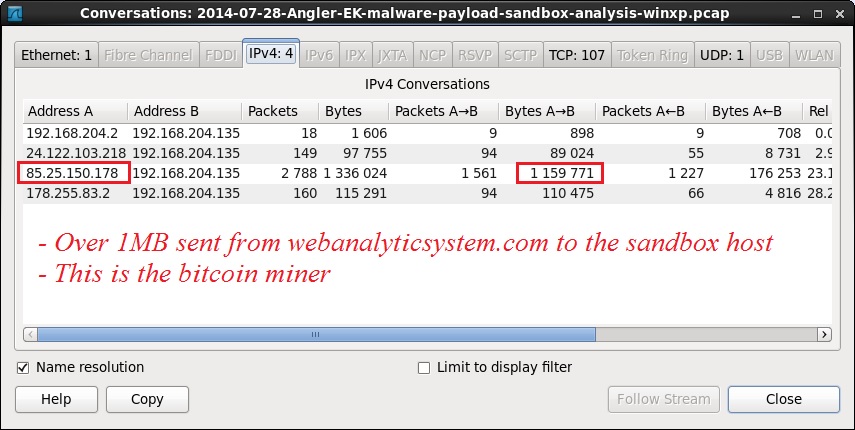
- 85.25.150[.]178 - webanalyticsystem[.]com - Bitcoin miner follow-up malware sent over HTTPS
- Other domains were noted in DNS queries from the sandbox traffic (see below)
ANGLER EK:
- 23:42:33 UTC - 66.96.246[.]143:80 - 02s.ylukodorsaieaql[.]org - GET /zqhpxe2aeu
- 23:42:38 UTC - 66.96.246[.]143:80 - 02s.ylukodorsaieaql[.]org - GET /rUKdFDCKBkdyJ7sw1_KPIrOlxi4b4rx84Ask17gZtsGh2mcaW4nMzFmSmbAk0H1v
- 23:42:58 UTC - 66.96.246[.]143:80 - 02s.ylukodorsaieaql[.]org - GET /fUIwdUHc8VxQJtK7qKO1KOZ5VMRETnAh-8iSUKuJrwx53M6JsxKY5YWuwVg5POpN
- 23:43:02 UTC - 66.96.246[.]143:80 - 02s.ylukodorsaieaql[.]org - GET /rk7_CLg1kxlkEy4JXIL3hYXEvrIl0e05SQQS7RnGU2fMiCUGk4JHAx-Nf67dfCb0
- 23:43:02 UTC - 66.96.246[.]143:80 - 02s.ylukodorsaieaql[.]org - GET /rk7_CLg1kxlkEy4JXIL3hYXEvrIl0e05SQQS7RnGU2fMiCUGk4JHAx-Nf67dfCb0
- 23:43:04 UTC - 66.96.246[.]143:80 - 02s.ylukodorsaieaql[.]org - GET /_bfe-SACNHpI7RFq5-ZnxPLG6EkrQ8aLlCx13deXPcXRONQeTVF9HGBQvWHjQKuG
TRAFFIC FROM SANDBOX ANALYSIS USING WINDOWS 7:
- [local host]:53 - DNS query for beckcomelith[.]biz - resolves: 128.100.217.137
- 128.100.217[.]137:80 - Attempted TCP connections, but 3 way handshake not established (RST by the client, see below)
- [local host]:53 - DNS query for file.bouwprofs[.]com - response: No such name
- [local host]:53 - DNS query for file.stellarquest[.]us - response: No such name
- [local host]:53 - DNS query for beckcomelith[.]biz - response: 140.184.196[.]114
- 128.100.217[.]137:80 - More attempted TCP connections to 128.100.217[.]137, but 3 way handshake not established
NOTE: In the Windows 7 sandbox analysis, all TCP connection reset by the client (not the server). For example:
- 128.100.217[.]137:80 - [SYN] Seq=0 Win=65535 Len=0 MSS=1460 SACK_PERM=1
- 128.100.217[.]137:80 - [SYN, ACK] Seq=0 Ack=1 Win=65535 Len=0 MSS=1366 SACK_PERM=1
- 128.100.217[.]137:80 - [RST] Seq=1 Win=0 Len=0
POST-INFECTION TRAFFIC FROM SANDBOX ANALYSIS USING WINDOWS XP:
- 24.122.103[.]218:80 - beckcomelith[.]biz POST /scans.php
- 24.122.103[.]218:80 - beckcomelith[.]biz POST /scans.php
- 24.122.103[.]218:80 - beckcomelith[.]biz POST /scans.php
- 24.122.103[.]218:80 - beckcomelith[.]biz POST /scans.php
- 24.122.103[.]218:80 - beckcomelith[.]biz POST /scans.php
- 85.25.150[.]178:443 - HTTPS traffic to webanalyticsystem[.]com
- 178.255.83[.]2:80 - crt.comodoca[.]com GET /EssentialSSLCA_2.crt
- 178.255.83[.]2:80 - crt.comodoca[.]com GET /ComodoUTNSGCCA.crt
- 178.255.83[.]2:80 - crl.comodoca[.]com GET /UTN-DATACorpSGC.crl
- 178.255.83[.]2:80 - crl.comodoca[.]com GET /COMODOCertificationAuthority.crl
- 178.255.83[.]2:80 - crl.comodoca[.]com GET /EssentialSSLCA.crl
- 85.25.150[.]178:443 - more than 1 MB HTTPS traffic with webanalyticsystem.com sending a bitcoin miner
- Also saw a DNS query to infowarsoft[.]biz that did not resolve.
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT:
File name: 2014-07-28-Angler-EK-java-exploit.jar
File size: 29,896 bytes
MD5 hash: 7a0eba050245fbb3f9d1985686a39ba8
Detection ratio: 14 / 54
First submission: 2014-07-29 02:44:26 UTC
VirusTotal link: https://www.virustotal.com/en/file/a5f9012fd513c4210a189df9924516b086dd5b264b976c3aa61c30d1c7568faf/analysis/
SILVERLIGHT EXPLOIT:
File name: 2014-07-28-Angler-EK-silverlight-exploit.xap
File size: 53,280 bytes
MD5 hash: e0950b06e7f01ffcd6a56b809cc68f28
Detection ratio: 0 / 53
First submission: 2014-07-29 02:44:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/002a5f7b5ee8d1fc983fee2b320843acecab411ce7b9588ebbc44695ee276846/analysis/
MALWARE PAYLOAD:
File name: 2014-07-28-Angler-EK-malware-payload.exe
File size: 657,920 bytes
MD5 hash: c0d1f083cb7e6b0cf501e11f5454bd05
Detection ratio: 4 / 53
First submission: 2014-07-28 23:02:44 UTC
VirusTotal link: https://www.virustotal.com/en/file/edbea251a734530925697f4e364810e87b1fd7d1a26d35f2d032e43e8ffce5e1/analysis/
FOLLOWUP MALWARE (BITCOIN MINER) FROM WINDOWS XP SANDBOX ANALYSIS:
File name: 9152a9aaed2e492bf7a4f74121e6233f.exe
File size: 1,026,588 bytes
MD5 hash: 9152a9aaed2e492bf7a4f74121e6233f
Detection ratio: 21 / 54
First submission: 2014-07-19 13:18:47 UTC
VirusTotal link: https://www.virustotal.com/en/file/561ec353ddac01d67968660c023768ba337321dd355f3b54a8498cd878a6a98b/analysis/
In the sandbox analysis, this file was saved as: C:\Documents and Settings\Username\Local Settings\Temp\6.tmp
ALERTS
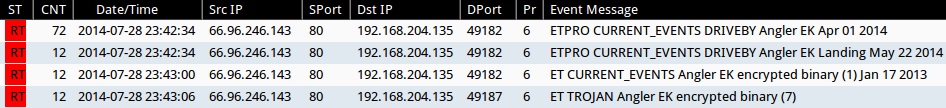
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-07-28 23:42:34 UTC - 66.96.246[.]143:80 - ETPRO CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2807913)
- 2014-07-28 23:42:34 UTC - 66.96.246[.]143:80 - ETPRO CURRENT_EVENTS DRIVEBY Angler EK Landing May 22 2014 (sid:2808076)
- 2014-07-28 23:43:00 UTC - 66.96.246[.]143:80 - ET CURRENT_EVENTS Angler EK encrypted binary (1) Jan 17 2013 (sid:2017984)
- 2014-07-28 23:43:06 UTC - 66.96.246[.]143:80 - ET TROJAN Angler EK encrypted binary (7) (sid:2018511)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-07-28 23:42:34 UTC - 66.96.246[.]143:80 - [1:31370:1] EXPLOIT-KIT Angler exploit kit redirection page
- 2014-07-28 23:42:39 UTC - 66.96.246[.]143:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download
- 2014-07-28 23:42:39 UTC - 66.96.246[.]143:80 - [1:17276:15] FILE-OTHER Multiple vendor Antivirus magic byte detection evasion attempt
- 2014-07-28 23:42:43 UTC - 66.96.246[.]143:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download
NOTE: From the Windows XP sandbox analysis, I saw multiple events for Trojan.Win32.Qadars from the ET PRO and Sourcefire VRT rulesets:
- 24.122.103[.]218:80 - ETPRO TROJAN Trojan.Win32.Qadars Checkin (sid:2807110)
- 24.122.103[.]218:80 - [1:30235:3] MALWARE-CNC Win.Trojan.Qadars variant outbound connection
Click here to return to the main page.