2014-08-01 - NUCLEAR EK FROM 85.159.213[.]246 - PARALETAS.PATMOS-STAR[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 95.85.17[.]107 - cucnaterafos.amtranexperts[.]com - Malicious redirect
- 85.159.213[.]246 - paraletas.patmos-star[.]com - Nuclear EK
- Various IP addresses - Post-infection traffic (see below)
REDIRECT (REPEATED):
- 2014-08-01 00:52:30 UTC - 95.85.17[.]107:80 - cucnaterafos.amtranexperts[.]com - GET /roriskajetas15.html
- 2014-08-01 00:52:30 UTC - 95.85.17[.]107:80 - cucnaterafos.amtranexperts[.]com - GET /roriskajetas15.html
- 2014-08-01 00:52:30 UTC - 95.85.17[.]107:80 - cucnaterafos.amtranexperts[.]com - GET /roriskajetas15.html
- 2014-08-01 00:52:30 UTC - 95.85.17[.]107:80 - cucnaterafos.amtranexperts[.]com - GET /roriskajetas15.html
- 2014-08-01 00:52:30 UTC - 95.85.17[.]107:80 - cucnaterafos.amtranexperts[.]com - GET /roriskajetas15.html
NUCLEAR EK:
- 2014-08-01 00:52:30 UTC - 85.159.213[.]246:80 - paraletas.patmos-star[.]com - GET /32af58c4ga4.html
- 2014-08-01 00:52:30 UTC - 85.159.213[.]246:80 - paraletas.patmos-star[.]com - GET /32af58c4ga4.html
- 2014-08-01 00:52:30 UTC - 85.159.213[.]246:80 - paraletas.patmos-star[.]com - GET /32af58c4ga4.html
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - paraletas.patmos-star[.]com - GET /3597476258/1/1406832420.jar
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - paraletas.patmos-star[.]com - GET /3597476258/1/1406832420.jar
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - paraletas.patmos-star[.]com - GET /3597476258/1/1406832420.jar
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - paraletas.patmos-star[.]com - GET /f/1/1406832420/3597476258/2
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - paraletas.patmos-star[.]com - GET /f/1/1406832420/3597476258/2
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - paraletas.patmos-star[.]com - GET /f/1/1406832420/3597476258/2
- 2014-08-01 00:52:42 UTC - 85.159.213[.]246:80 - paraletas.patmos-star[.]com - GET /f/1/1406832420/3597476258/2/2
- 2014-08-01 00:52:42 UTC - 85.159.213[.]246:80 - paraletas.patmos-star[.]com - GET /f/1/1406832420/3597476258/2/2
- 2014-08-01 00:52:42 UTC - 85.159.213[.]246:80 - paraletas.patmos-star[.]com - GET /f/1/1406832420/3597476258/2/2
POST-INFECTION TRAFFIC:
- 2014-08-01 00:53:32 UTC - 74.125.228[.]49:80 - www.google[.]com - GET /
- Numerous attempts to connect with different mail servers over port 25
Also saw encrypted TCP streams to the following IP addresses:
- 2014-08-01 00:52:56 UTC - 111.121.193[.]238:443
- 2014-08-01 00:53:27 UTC - 77.120.107[.]90:44510
- 2014-08-01 00:53:31 UTC - 103.15.107[.]118:12510
- 2014-08-01 00:53:31 UTC - 174.138.165[.]90:12510
- 2014-08-01 00:53:31 UTC - 188.190.114[.]109:12510
- 2014-08-01 00:53:31 UTC - 85.114.141[.]62:12510
- 2014-08-01 00:54:01 UTC - 77.120.107[.]90:44510
- 2014-08-01 00:55:04 UTC - 77.120.107[.]90:44510
- 2014-08-01 00:55:37 UTC - 77.120.107[.]90:44510
Information on these callback IP addresses:
- 77.120.107[.]90 - Ukraine, Kiev - Kyivski Telekomunikatsiyni Merezhi, LLC - Viola DC
- 85.114.141[.]62 - Germany, Dusseldorf - Fast IT Colocation
- 103.15.107[.]118 - Hong Kong - Hong Kong IDC (Gigabit hosting)
- 111.121.193[.]238 - China, Guiyang - China Telecom
- 174.138.165[.]90 - United States, Phoenix AZ - Webquest,Inc
- 188.190.114[.]109 - Ukraine, Kharkiv - Infium LLC
PRELIMINARY MALWARE ANALYSIS
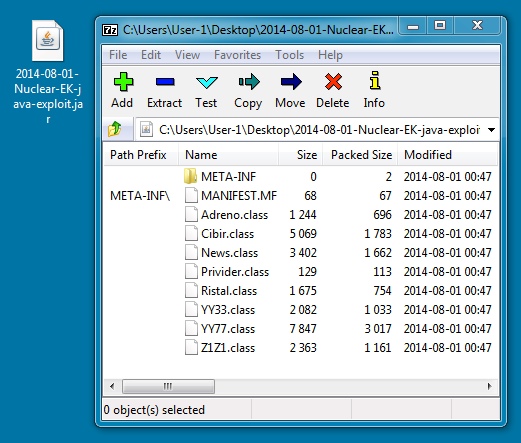
JAVA EXPLOIT:
File name: 2014-08-01-Nuclear-EK-java-exploit.jar
File size: 11,474 bytes
MD5 hash: 8851958384b1cbb376e6c4c25aced05a
Detection ratio: 0 / 54
First submission: 2014-08-01 02:29:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/c737abdecbf3b7856a5eebda668af46b95a469ea4c8987e9fa2304cade48d121/analysis/
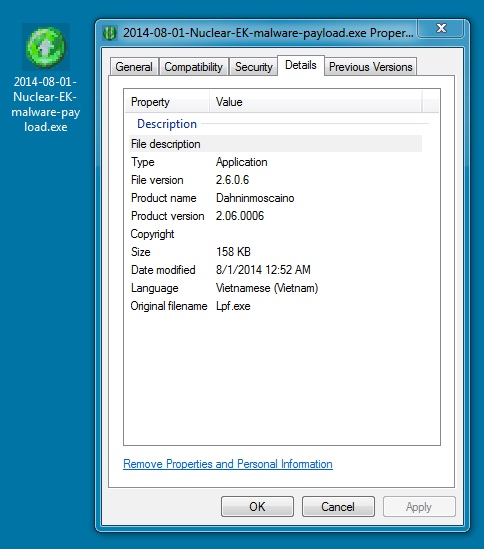
MALWARE PAYLOAD:
File name: 2014-08-01-Nuclear-EK-malware-payload.exe
File size: 162,744 bytes
MD5 hash: 0e2a570edd577f27ba711afd9557f718
Detection ratio: 3 / 53
First submission: 2014-08-01 02:30:06 UTC
VirusTotal link: https://www.virustotal.com/en/file/a9dd22ce9baf671e1a2b07203e237fdbb21f9f8d509b3c1157f350b445e7dd47/analysis/
ALERTS
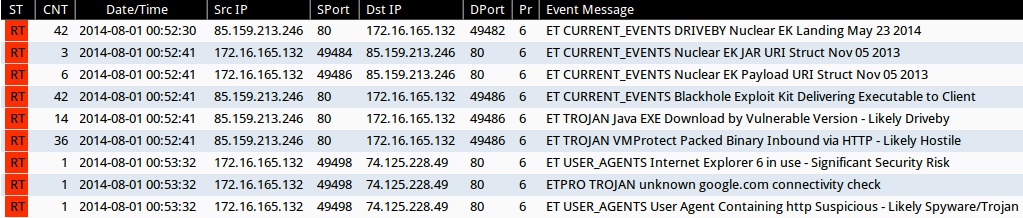
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-08-01 00:52:30 UTC - 85.159.213[.]246:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing May 23 2014 (sid:2018595)
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013 (sid:2017666)
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:2013962)
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby (sid:2013036)
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - ET TROJAN VMProtect Packed Binary Inbound via HTTP - Likely Hostile (sid:2009080)
- 2014-08-01 00:53:32 UTC - 74.125.228[.]49:80 - ET USER_AGENTS Internet Explorer 6 in use - Significant Security Risk (sid:2010706)
- 2014-08-01 00:53:32 UTC - 74.125.228[.]49:80 - ETPRO TROJAN unknown google.com connectivity check (sid:2808012)
- 2014-08-01 00:53:32 UTC - 74.125.228[.]49:80 - ET USER_AGENTS User Agent Containing http Suspicious - Likely Spyware/Trojan (sid:2003394)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Ubuntu 14.04 LTS:
- [local host]:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority (numerous times throughout pcap)
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:30219:2] EXPLOIT-KIT Nuclear exploit kit outbound jar request
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:30219:2] EXPLOIT-KIT Nuclear exploit kit outbound jar request
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:30219:2] EXPLOIT-KIT Nuclear exploit kit outbound jar request
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:30220:2] EXPLOIT-KIT Nuclear exploit kit outbound payload request
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:30220:2] EXPLOIT-KIT Nuclear exploit kit outbound payload request
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:30220:2] EXPLOIT-KIT Nuclear exploit kit outbound payload request
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:25042:3] EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:25042:3] EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:25042:3] EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
- 2014-08-01 00:52:41 UTC - 85.159.213[.]246:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-08-01 00:52:42 UTC - 85.159.213[.]246:80 - [1:30220:2] EXPLOIT-KIT Nuclear exploit kit outbound payload request
- 2014-08-01 00:52:42 UTC - 85.159.213[.]246:80 - [1:30220:2] EXPLOIT-KIT Nuclear exploit kit outbound payload request
- 2014-08-01 00:52:42 UTC - 85.159.213[.]246:80 - [1:30220:2] EXPLOIT-KIT Nuclear exploit kit outbound payload request
- 2014-08-01 00:52:42 UTC - 85.159.213[.]246:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
- 2014-08-01 00:52:42 UTC - 85.159.213[.]246:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
- 2014-08-01 00:52:42 UTC - 85.159.213[.]246:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
Click here to return to the main page.