2014-08-06 - NUCLEAR EK FROM 94.229.64[.]227 - IBIZ.COUNSELINGMOMENTS[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
REDIRECT THAT LED TO NUCLEAR EK:
- ports.changeyourschools[.]com/p/h/d/0.32.2/external.min.js?ver=1.40.4319
NUCLEAR EK:
- 22:31:57 UTC - 94.229.64[.]227:80 - ibiz.counselingmoments[.]com - GET /63c81e76vfy8.html
- 22:32:08 UTC - 94.229.64[.]227:80 - ibiz.counselingmoments[.]com - GET /746074750/3/1407342360.jar
- 22:32:09 UTC - 94.229.64[.]227:80 - ibiz.counselingmoments[.]com - GET /f/3/1407342360/746074750/2
- 22:32:11 UTC - 94.229.64[.]227:80 - ibiz.counselingmoments[.]com - GET /f/3/1407342360/746074750/2/2
POST-INFECTION TRAFFIC:
- 22:32:14 UTC - 31.202.203[.]170:80 - icepower[.]su - GET /b/shoe/1480
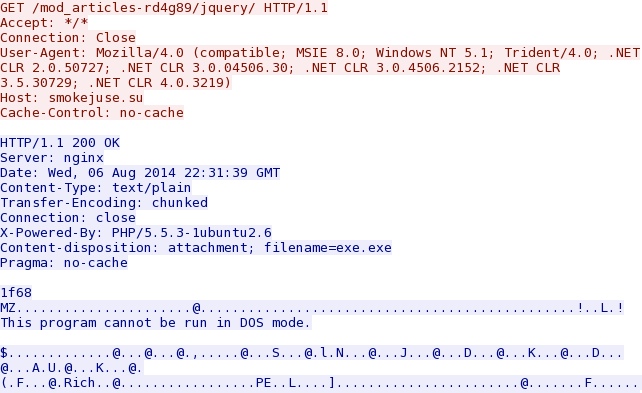
- 22:32:22 UTC - 37.229.104[.]171:80 - smokejuse[.]su - GET /mod_articles-rd4g89/jquery/
- 22:32:30 UTC - 37.229.104[.]171:80 - smokejuse[.]su - GET /mod_articles-rd4g89/jquery/
- 22:33:14 UTC - 188.230.15[.]191:80 - smokejuse[.]su - GET /mod_jshopping-re1k67/soft64.dll
- 22:33:16 UTC - 176.120.47[.]28:80 - vision-vaper[.]su - GET /b/eve/7a5684aab544793d37f05a96
- 22:34:14 UTC - 31.202.203[.]170:80 - vision-vaper[.]su - POST /b/opt/A495069680AF592C4FBDA4BB
- 22:34:24 UTC - 31.202.203[.]170:80 - vision-vaper[.]su - GET /b/letr/9B249347C576AE4B0A6453DC
- 22:34:24 UTC - 27.254.40[.]105:8080 - 27.254.40[.]105:8080 - POST /b/opt/EF99E025F45142AE3B43BF39
- 22:34:27 UTC - 27.254.40[.]105:8080 - 27.254.40[.]105:8080 - GET /b/letr/9A86C04018FD00DCD7EFFD4B
- 22:34:28 UTC - 198.154.224[.]48:8080 - 198.154.224[.]48:8080 - POST /b/opt/B764AB7C4FD57C1B80C7818C
- 22:34:28 UTC - 198.154.224[.]48:8080 - 198.154.224[.]48:8080 - POST /b/opt/B102BD367ED3BF9EB1C14209
- 22:34:46 UTC - 198.154.224[.]48:8080 - 198.154.224[.]48:8080 - POST /b/req/2BBEC34074027586BB108811
- 22:34:46 UTC - 198.154.224[.]48:8080 - 198.154.224[.]48:8080 - GET /b/eve/485ce027874e1db06bb3b717
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT:
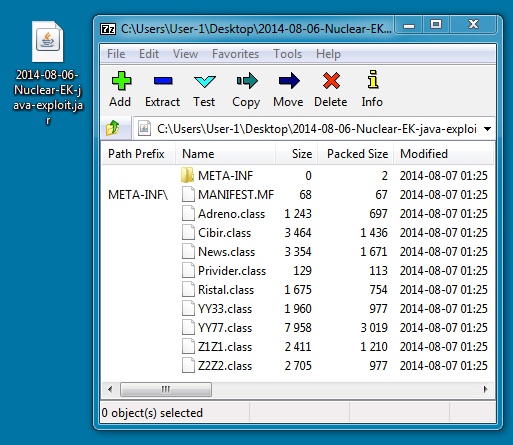
File name: 2014-08-06-Nuclear-EK-java-exploit.jar
File size: 12,221 bytes
MD5 hash: 25b3f029c3327cdec54fc719d37403ba
Detection ratio: 0 / 51
First submission: 2014-08-06 23:41:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/0f5fafc68f2ba70d7289a57dfe49a6a8154906e29024c9fdd3b28390b39bb96a/analysis/
MALWARE PAYLOAD:
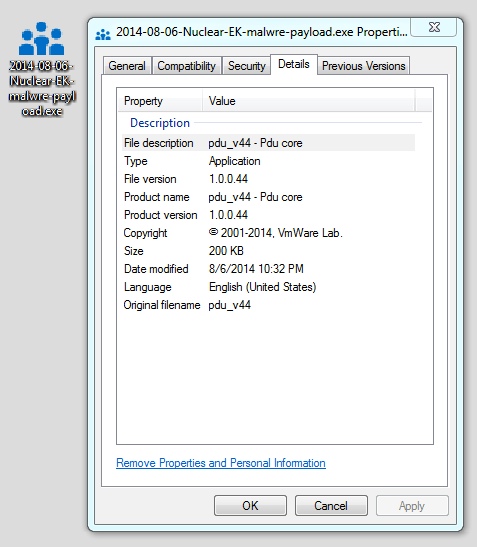
File name: 2014-08-06-Nuclear-EK-malwre-payload.exe
File size: 204,800 bytes
MD5 hash: 609cc899a3ed8f23c54981137bb80cf3
Detection ratio: 0 / 54
First submission: 2014-08-06 23:41:54 UTC
VirusTotal link: hhttps://www.virustotal.com/en/file/2499b98617f7e76514be57fa9fb15a48d2adc5e0beac6d68f845a719cd32b1be/analysis/
FOLLOW-UP MALWARE:
File name: UpdateFlashPlayer_90bb0736.exe
File size: 167,936 bytes
MD5 hash: b20ebff04cf7a6c7cc24873183e1ca2f
Detection ratio: 21 / 54
First submission: 2014-08-06 18:18:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/9ae4a4ea4ae284251996f62916dde00663c81ef5549f81b8ca732e6daa23b598/analysis/
ALERTS
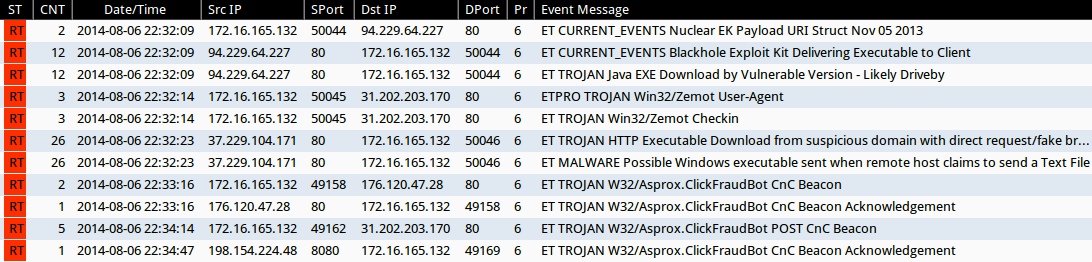
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 22:32:09 UTC - 94.229.64[.]227:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 22:32:09 UTC - 94.229.64[.]227:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:2013962)
- 22:32:09 UTC - 94.229.64[.]227:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby (sid:2013036)
- 22:32:14 UTC - 31.202.203[.]170:80 - ETPRO TROJAN Win32/Zemot User-Agent (sid:2808499)
- 22:32:14 UTC - 31.202.203[.]170:80 - ET TROJAN Win32/Zemot Checkin (sid:2018643 or sid:2018644)
- 22:32:23 UTC - 37.229.104[.]171:80 - ET TROJAN HTTP Executable Download from suspicious domain with direct request/fake browser (multiple families) (sid:2018572)
- 22:32:23 UTC - 37.229.104[.]171:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 22:33:16 UTC - 176.120.47[.]28:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- 22:33:16 UTC - 176.120.47[.]28:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 22:34:14 UTC - 31.202.203[.]170:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
- 22:34:47 UTC - 198.154.224[.]48:8080 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 22:32:08 UTC - 94.229.64[.]227:80 - [1:30219:2] EXPLOIT-KIT Nuclear exploit kit outbound jar request
- 22:32:08 UTC - 94.229.64[.]227:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt
- 22:32:09 UTC - 94.229.64[.]227:80 - [1:30220:2] EXPLOIT-KIT Nuclear exploit kit outbound payload request
- 22:32:09 UTC - 94.229.64[.]227:80 - [1:25042:3] EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit
- 22:32:09 UTC - 94.229.64[.]227:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 22:32:09 UTC - 94.229.64[.]227:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
- 22:32:09 UTC - 94.229.64[.]227 - [139:1:1] (spp_sdf) SDF Combination Alert
- 22:32:11 UTC - 94.229.64[.]227:80 - [1:30220:2] EXPLOIT-KIT Nuclear exploit kit outbound payload request
- 22:32:12 UTC - 94.229.64[.]227:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
- 22:32:23 UTC - 37.229.104[.]171:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 22:32:25 UTC - 37.229.104[.]171 - [139:1:1] (spp_sdf) SDF Combination Alert
- 22:32:30 UTC - 37.229.104[.]171:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 22:32:31 UTC - 37.229.104[.]171 - [139:1:1] (spp_sdf) SDF Combination Alert
- 22:33:15 UTC - 188.230.15[.]191 - [139:1:1] (spp_sdf) SDF Combination Alert
- 22:33:16 UTC - 176.120.47[.]28:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 22:34:14 UTC - 172.16.165.132:4912 - 31.202.203[.]170:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 22:34:24 UTC - 31.202.203[.]170:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 22:34:24 UTC - 27.254.40[.]105:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 22:34:27 UTC - 27.254.40[.]105:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 22:34:28 UTC - 198.154.224[.]48:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 22:34:28 UTC - 198.154.224[.]48:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 22:34:46 UTC - 198.154.224[.]48:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 22:34:46 UTC - 198.154.224[.]48:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
Click here to return to the main page.