2014-08-11 - PORN-RELATED SUBDOMAINS OF SOURCEFORGE[.]NET LEAD TO FLASHPACK EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This past Friday, a reader notified me of stat-count.dnsdynamic[.]com redirecting to FlashPack EK. The redirect by stat-count.dnsdynamic[.]com can be generated by visiting porn-themed pages from sub domains of sourceforge[.]net.
- You can find these porn-themed pages with the following Google search:
site:sourceforge[.]net nude tube fake
- URLs from the search results follow a specific pattern:
[random characters].sourceforge[.]net/[random characters][2-digit number].html
or:
[random characters].sourceforge[.]net/[2-digit number].html
- However you get there, stat-count.dnsdynamic[.]com is compromised and redirecting to FlashPack EK. The EK sends a Glupteba payload as seen in Operation Windigo.
- For more information about Operation Windigo, ESET published a report avaialable here.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 184.82.76[.]4 - stat-count.dnsdynamic[.]com - Compromised website
- 77.78.104[.]9 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - FlashPack EK
- 79.136.118[.]200 - no domain name - Post-infection Glupteba traffic
COMPROMISED WEBSITE:
- 13:32:48 UTC - 184.82.76[.]4:80 - stat-count.dnsdynamic[.]com - GET /ad/sourceforge/ad_104/165184313/?http%3A%2F%2F
www.google.com%2Furl%3Furl%3Dhttp%3A%2F%2Fehaqihy.sourceforge[.]net%2Futroazoagih126.html%26rct%3Dj%26frm%3D1%26q%3D%26esrc
%3Ds%26sa%3DU%26ei%3D3cXoU_aNGImU8QHyrIGIBg%26ved%3D0CCsQFjAF%26usg%3DAFQjCNHXDIFf7R4_gZMwov3GFsN8JtZ_jA
FLASHPACK EK:
- 13:32:48 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /index.php?l=anM9MSZyZ2ducXZoYj
1vY2JpbXF1dXQmdGltZT0xNDA4MTExMTMyMjUwMzk0MTc5MCZzcmM9MjIwJnN1cmw9YW50aWRvci5uZXQmc3BvcnQ9ODAma2V5PTQ3NzRBNUE5
JnN1cmk9L2FkL3NvdXJjZWZvcmdlL2FkXzEwNC8xNjUxODQzMTMvJTNmaHR0cCUyNTNBJTI1MkYlMjUyRnd3dy5nb29nbGUuY29tJTI1MkZ1cmwlMjUz
RnVybCUyNTNEaHR0cCUyNTNBJTI1MkYlMjUyRmVoYXFpaHkuc291cmNlZm9yZ2UubmV0JTI1MkZ1dHJvYXpvYWdpaDEyNi5odG1sJTI1MjZyY3QlMjUz
RGolMjUyNmZybSUyNTNEMSUyNTI2cSUyNTNEJTI1MjZlc3JjJTI1M0RzJTI1MjZzYSUyNTNEVSUyNTI2ZWklMjUzRDNjWG9VX2FOR0ltVThRSHlySUdJQ
mclMjUyNnZlZCUyNTNEMENDc1FGakFGJTI1MjZ1c2clMjUzREFGUWpDTkhYRElGZjdSNF9nWk13b3YzR0ZzTjhKdFpfakE= - 13:32:49 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r522053ee12e4444b542451e29c08717ba.consejeros[.]com[.]bo -
GET /index2.php - 13:32:50 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/gmetax.php
- 13:32:51 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/lspinq/f2cf6.js
- 13:32:51 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/qherey.js
- 13:32:52 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/owei.php
- 13:32:52 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/mfoundz.php
- 13:32:52 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/qfrankn.php
- 13:32:52 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/gyetg.php
- 13:32:52 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/rstayedy.php
- 13:32:52 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/lspinq/b9b1b.js
- 13:32:52 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/lspinq/3879aa.js
- 13:32:52 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/lspinq/033bd7.js
- 13:32:52 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/lspinq/90cc0fa9.js
- 13:32:52 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/lspinq/5357bd1.js
- 13:32:53 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/lodpchangeb.php
- 13:32:58 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/lspinq/a156d81.swf
- 13:32:59 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/lspinq/1fc0bb.swf
- 13:32:59 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/lspinq/b29d5.swf
- 13:33:01 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/lodqhundredsn.php?id=4
- 13:34:12 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/lodtgravityd.php
- 13:34:28 UTC - 77.78.104[.]96:80 - xh2cqhmv5u4ifvht8j99d7r.consejeros[.]com[.]bo - GET /kafecodes/kholdq/lspinq/260cb1ce.jar
NOTE: a .jar file was sent in reply to the last HTTP GET request; however, I could not extract it from the PCAP.
POST-INFECTION TRAFFIC:
- 13:33:02 UTC - 79.136.118[.]200:42737 - GET /stat?uid=100&downlink=1111&uplink=1111&id=00117C21&statpass=bpass&version=
20140810&features=30&guid=f9f5c432-daef-4ae3-b975-87434aeb7a12&comment=20140810&p=0&s= - 13:33:03 UTC - 79.136.118[.]200:34618 - Glupteba callback traffic
- 13:35:06 UTC - 174.143.144[.]69:25 - GET / HTTP/1.1
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT 1 OF 3
File name: 1fc0bb.swf
File size: 31,561 bytes
MD5 hash: addf1b50218673c6656f516915a84f26
Detection ratio: 0 / 52
First submission: 2014-08-11 13:39:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/45fd4a3d15fc76b930caa50c5c46fb6c6c896a1fb8e07e75dbbf8b9804fd8617/analysis/
FLASH EXPLOIT 2 OF 3
File name: a156d81.swf
File size: 8,396 bytes
MD5 hash: 4bcff12446b61f6c7ba7ba0fdcf9b33e
Detection ratio: 1 / 43
First submission: 2014-08-11 13:39:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/cd01023dd60906ae0ab41be212b6d5b657b44f4bed55fd7cf5d9d5897f4d5520/analysis/
FLASH EXPLOIT 3 OF 3
File name: b29d5.swf
File size: 9,563 bytes
MD5 hash: e752688cabd3647591790729b5f13128
Detection ratio: 1 / 53
First submission: 2014-08-11 13:39:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/392645985008ba54fb3d1bb6161f728e95b7bb2762699d680fcbe70be02578f1/analysis/
MALWARE PAYLOAD
File name: 2014-08-11-FlashPack-EK-malware-payload.exe
File size: 75,139 bytes
MD5 hash: e51be47fdf68be5b2b283ea07c3c6394
Detection ratio: 3 / 53
First submission: 2014-08-11 13:40:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/501ee698d66b20cb9a93f340577410cfde7167cff75b676d9343e36f19b0e7b3/analysis/
ALERTS
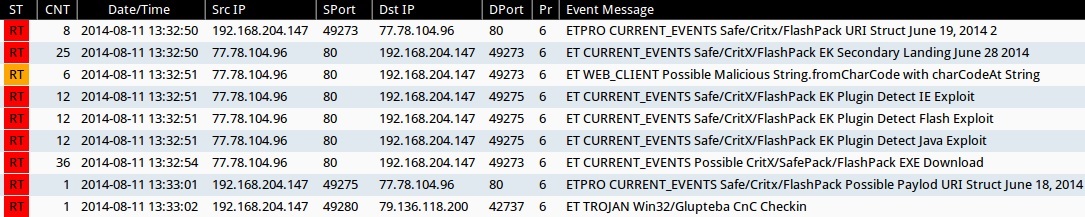
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 13:32:50 UTC - 77.78.104[.]96:80 - ETPRO CURRENT_EVENTS Safe/Critx/FlashPack URI Struct June 19, 2014 2 (sid:2808213)
- 13:32:50 UTC - 77.78.104[.]96:80 - 192.168.204.147:- ET CURRENT_EVENTS Safe/CritX/FlashPack EK Secondary Landing June 28 2014 (sid:2018794)
- 13:32:51 UTC - 77.78.104[.]96:80 - ET WEB_CLIENT Possible Malicious String.fromCharCode with charCodeAt String (sid:2012205)
- 13:32:51 UTC - 77.78.104[.]96:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack EK Plugin Detect IE Exploit (sid:2018795)
- 13:32:51 UTC - 77.78.104[.]96:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack EK Plugin Detect Flash Exploit (sid:2018797)
- 13:32:51 UTC - 77.78.104[.]96:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack EK Plugin Detect Java Exploit (sid:2018796)
- 13:32:54 UTC - 77.78.104[.]96:80 - ET CURRENT_EVENTS Possible CritX/SafePack/FlashPack EXE Download (sid:2017297)
- 13:33:01 UTC - 77.78.104[.]96:80 - ETPRO CURRENT_EVENTS Safe/Critx/FlashPack Possible Paylod URI Struct June 18, 2014 (sid:2808209)
- 13:33:02 UTC - 79.136.118[.]200:42737 - ET TROJAN Win32/Glupteba CnC Checkin (sid:2013293)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 13:32:51 UTC - 77.78.104[.]96:80 - [1:23878:8] BROWSER-PLUGINS Oracle JRE Deployment Toolkit ActiveX clsid access attempt
- 13:32:54 UTC - 77.78.104[.]96:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 13:32:54 UTC - 77.78.104[.]96:80 - [1:24791:3] EXPLOIT-KIT CritX exploit kit Portable Executable download
- 13:32:54 UTC - 77.78.104[.]96:80 - [1:29167:1] EXPLOIT-KIT CritX exploit kit payload download attempt
- 13:32:54 UTC - 77.78.104[.]96:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 13:32:54 UTC - 77.78.104[.]96:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 13:33:01 UTC - 77.78.104[.]96:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 13:33:01 UTC - 77.78.104[.]96:80 - [1:24791:3] EXPLOIT-KIT CritX exploit kit Portable Executable download
- 13:33:01 UTC - 77.78.104[.]96:80 - [1:29167:1] EXPLOIT-KIT CritX exploit kit payload download attempt
- 13:33:01 UTC - 77.78.104[.]96:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 13:33:01 UTC - 77.78.104[.]96:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 13:33:02 UTC - 79.136.118[.]200:42737 - [1:30977:1] MALWARE-CNC Win.Trojan.Jaik variant outbound connection
- 13:33:03 UTC - 79.136.118[.]200:34618 - [1:31603:1] MALWARE-CNC Win.Trojan.Glupteba C&C server HELLO request to client
- 13:33:03 UTC - 79.136.118[.]200:34618 - [1:31607:1] MALWARE-CNC Win.Trojan.Glupteba client response/authenticate to C&C server
- 13:33:03 UTC - 79.136.118[.]200:34618 - [1:31604:1] MALWARE-CNC Win.Trojan.Glupteba C&C server READD command to client
- 13:33:03 UTC - 79.136.118[.]200:34618 - [1:31604:1] MALWARE-CNC Win.Trojan.Glupteba C&C server READD command to client
- 13:34:13 UTC - 77.78.104[.]96:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 13:34:13 UTC - 77.78.104[.]96:80 - [1:24791:3] EXPLOIT-KIT CritX exploit kit Portable Executable download
- 13:34:13 UTC - 77.78.104[.]96:80 - [1:29167:1] EXPLOIT-KIT CritX exploit kit payload download attempt
- 13:34:13 UTC - 77.78.104[.]96:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 13:34:13 UTC - 77.78.104[.]96:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 13:35:04 UTC - 79.136.118[.]200:34618 - [1:31603:1] MALWARE-CNC Win.Trojan.Glupteba C&C server HELLO request to client
- 13:35:04 UTC - 79.136.118[.]200:34618 - [1:31605:1] MALWARE-CNC Win.Trojan.Glupteba C&C server READY command to client
- 13:35:06 UTC - 79.136.118[.]200:34618 - [1:31603:1] MALWARE-CNC Win.Trojan.Glupteba C&C server HELLO request to client
- 13:35:06 UTC - 79.136.118[.]200:34618 - [1:31605:1] MALWARE-CNC Win.Trojan.Glupteba C&C server READY command to client
Click here to return to the main page.