2014-08-12 - NUCLEAR EK FROM 94.229.64[.]231 - INTL.ECHRISTIANCARE[.]CO
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 78.47.203[.]83 - primo.rothstaffing[.]info - Malvertising Redirect
- 94.229.64[.]231 - intl.echristiancare[.]co - Nuclear EK
- 109.86.76[.]58 - icepower[.]su - Post-infection callback (Zemot)
- 178.158.135[.]20 - priple-red[.]su - Post-infection callback (Zemot)
MALVERTISING REDIRECT:
- 2014-08-12 02:34:34 UTC - 78.47.203[.]83 - primo.rothstaffing[.]info - GET /js/scroll.js?ver=4.42.9767
NUCLEAR EK:
- 2014-08-12 02:34:35 UTC - 94.229.64[.]231:80 - intl.echristiancare[.]co - GET /797aa6e4k7pc.html
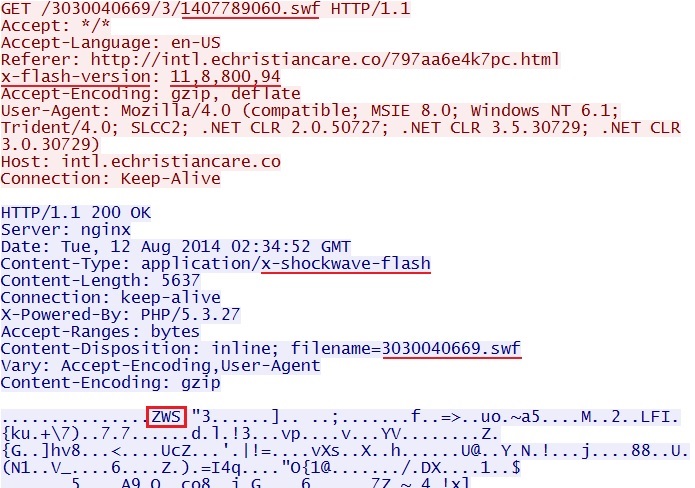
- 2014-08-12 02:34:40 UTC - 94.229.64[.]231:80 - intl.echristiancare[.]co - GET /3030040669/3/1407789060.swf
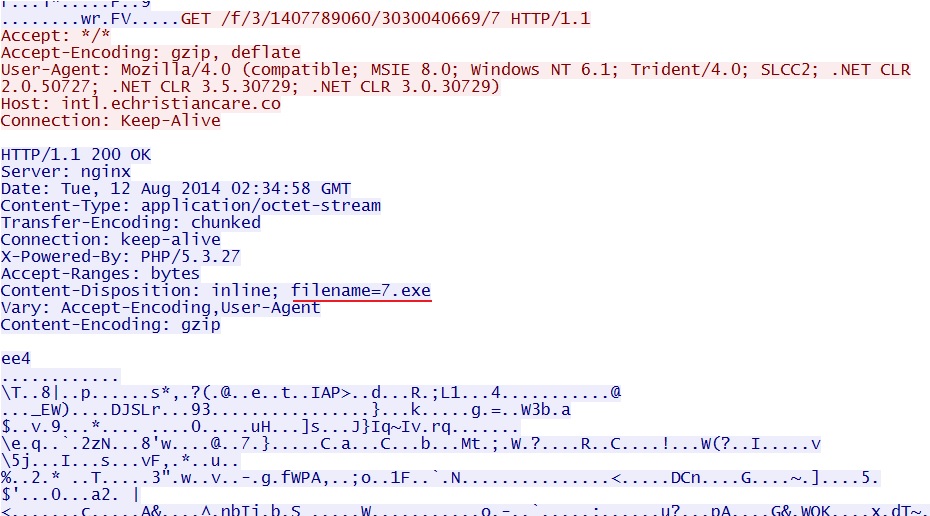
- 2014-08-12 02:34:46 UTC - 94.229.64[.]231:80 - intl.echristiancare[.]co - GET /f/3/1407789060/3030040669/7
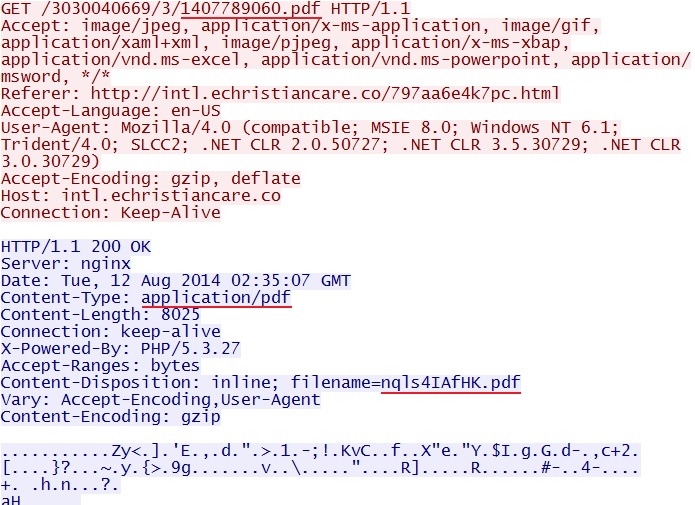
- 2014-08-12 02:34:55 UTC - 94.229.64[.]231:80 - intl.echristiancare[.]co - GET /3030040669/3/1407789060.pdf
- 2014-08-12 02:34:56 UTC - 94.229.64[.]231:80 - intl.echristiancare[.]co - GET /3030040669/3/1407789060.htm
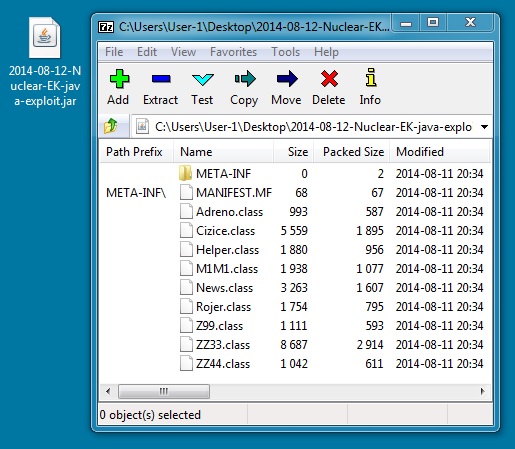
- 2014-08-12 02:35:28 UTC - 94.229.64[.]231:80 - intl.echristiancare[.]co - GET /3030040669/3/1407789060.jar
POST-INFECTION TRAFFIC:
- 2014-08-12 02:34:50 UTC - 109.86.76[.]58:80 - icepower[.]su - GET /b/shoe/1480 [repeats 9 more times]
- 2014-08-12 02:35:21 UTC - 178.158.135[.]20:80 - priple-red[.]su - GET /mod_articles-qaz12.9/jquery/ [repeats 31 more times]
- 2014-08-12 02:38:20 UTC - 178.158.135[.]20:80 - priple-red[.]su - GET /mod_articles-qaz12.9/ajax/ [continues to repeat]
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-08-12-Nuclear-EK-flash-exploit.swf
File size: 5,614 bytes
MD5 hash: a1465ece32fa3106aa88fd666ebf8c78
Detection ratio: 3 / 47
First submission: 2014-08-08 07:20:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/e165b73eb2f84f5fd5e85e4aecdfea947e51a0556d70f08924e8f1c28fd1079a/analysis/
JAVA EXPLOIT
File name: 2014-08-12-Nuclear-EK-java-exploit.jar
File size: 12,396 bytes
MD5 hash: a93f603a95282b80d8afd3f23c4d4889
Detection ratio: 3 / 50
First submission: 2014-08-12 14:21:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/367e0eb7dba190f23666e2bc89baf5d2f79460a98cf19a5155f7c4b7f1f5c864/analysis/
PDF EXPLOIT
File name: 2014-08-12-Nuclear-EK-pdf-exploit.pdf
File size: 9,770 bytes
MD5 hash: 19ed55ef17a49451d8052d0b51c66239
Detection ratio: 2 / 54
First submission: 2014-08-12 14:22:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/7ae6cce3edf2f690fbbba2c4da2b6674abb386ff5d3c639b9214fb51fac62879/analysis/
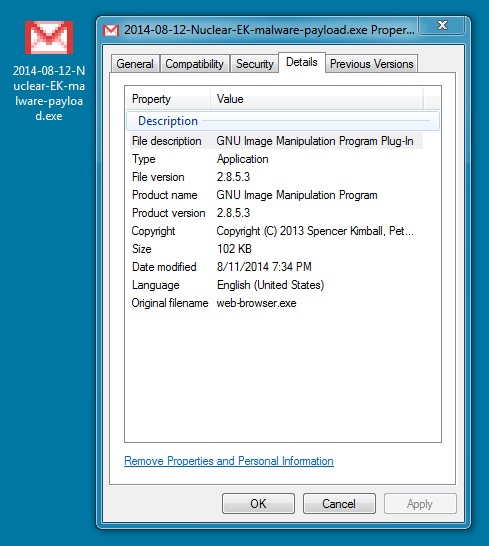
MALWARE PAYLOAD
File name: 2014-08-12-Nuclear-EK-malware-payload.exe
File size: 104,960 bytes
MD5 hash: 8bce8a59f9e789befb9d178c9a03fb66
Detection ratio: 1 / 53
First submission: 2014-08-12 14:22:30 UTC
VirusTotal link: https://www.virustotal.com/en/file/355546c6bb8fde63f5cfdd663996df3222aa154f06d33fe4b81c2d5085166ee1/analysis/
ALERTS

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 02:34:34 UTC - 78.47.203[.]83:80 - ET CURRENT_EVENTS Malvertising Redirection to Exploit Kit Aug 07 2014 (sid:2018909)
- 02:34:35 UTC - 94.229.64[.]231:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing May 23 2014 (sid:2018595)
- 02:34:40 UTC - 94.229.64[.]231:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2018362)
- 02:34:46 UTC - 94.229.64[.]231:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 02:34:46 UTC - 94.229.64[.]231:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:2013962)
- 02:34:50 UTC - 109.86.76[.]58:80 - ETPRO TROJAN Win32/Zemot User-Agent (sid:2808499)
- 02:34:50 UTC - 109.86.76[.]58:80 - ET TROJAN Win32/Zemot Checkin (sid:2018643 and sid:2018644)
- 02:34:55 UTC - 94.229.64[.]231:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering PDF Exploit to Client (sid:2013960)
- 02:35:28 UTC - 94.229.64[.]231:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013 (sid:2017666)
- 02:35:29 UTC - 94.229.64[.]231:80 - ETPRO EXPLOIT Multiple Vendor Malformed ZIP Archive Antivirus Detection Bypass (sid:2800029)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 02:34:34 UTC - 192.168.204.2:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority (x7)
- 02:34:46 UTC - 94.229.64[.]231:80 - [1:30220:2] EXPLOIT-KIT Nuclear exploit kit outbound payload request
- 02:34:46 UTC - 94.229.64[.]231:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 02:34:46 UTC - 94.229.64[.]231:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 02:34:46 UTC - 94.229.64[.]231:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
- 02:34:46 UTC - 94.229.64[.]231:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 02:34:49 UTC - [local host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query (x4)
- 02:35:28 UTC - 94.229.64[.]231:80 - [1:30219:2] EXPLOIT-KIT Nuclear exploit kit outbound jar request
- 02:35:29 UTC - 94.229.64[.]231:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt
SCREENSHOTS FROM THE TRAFFIC
Nuclear EK landing page, with the malvertisement referer:
Nuclear EK sends the malware payload:
Click here to return to the main page.